Default rule blocking some Outgoing DNS
-
I'm using DNS resolver in forwarding mode to Google and CloudFlare (SSL/TLS). It works, but see a lot of blocked packets by the default rule from my WAN address with TCP:F, P and A flags
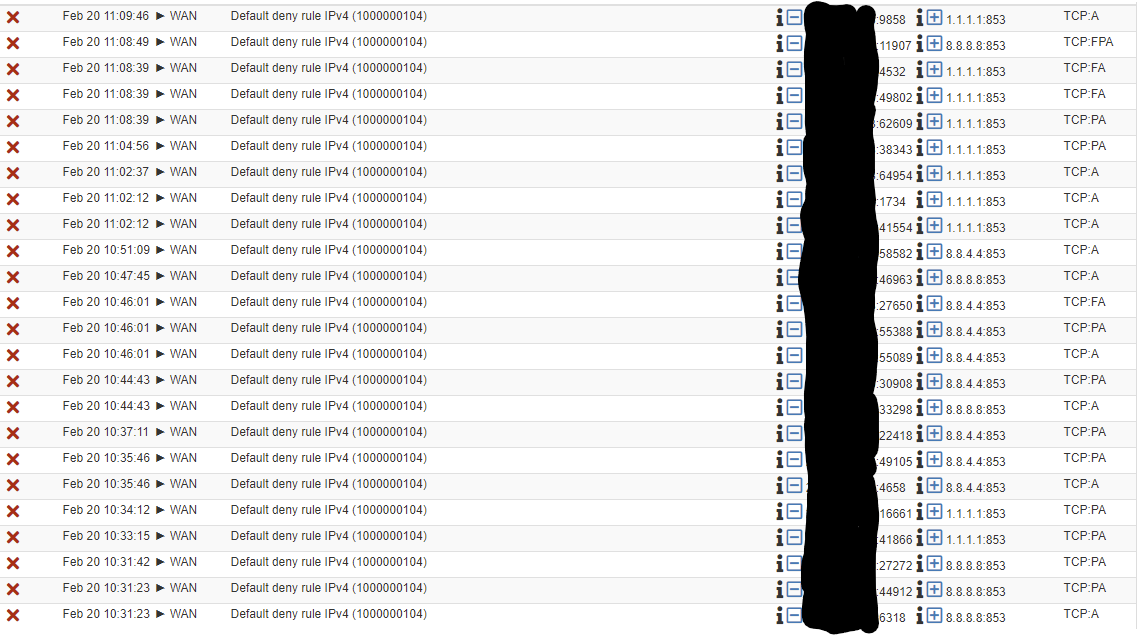
Is this normal?
For the record, I'm running 2.5.0, but it was also happening on 2.4.5-P1.
-
Seems weird. The default WAN deny rule should block traffic entering the WAN interface; not traffic leaving the WAN interface. What do your firewall rules look like for FLOATING and WAN?
-
"1000000104 " is the default interface final block all rule.
block out inet all tracker 1000000104 label "Default deny rule IPv4"remove the check here :
Can't tell why 8.8.8.8 and 1.1.1.1 is contacting your WAN 'out of state'.
-
@hieroglyph said in Default rule blocking some Outgoing DNS:
Seems weird. The default WAN deny rule should block traffic entering the WAN interface; not traffic leaving the WAN interface. What do your firewall rules look like for FLOATING and WAN?
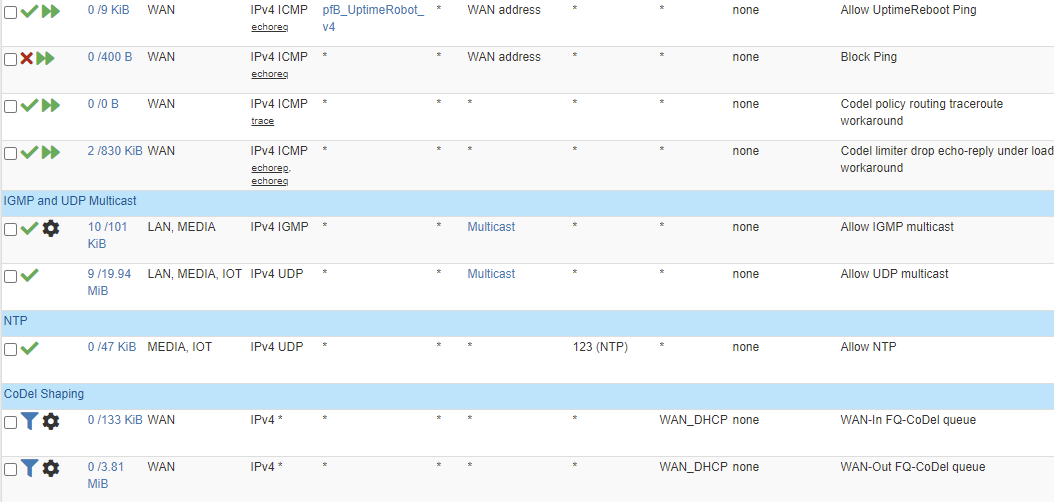
Here are my floating rules for WAN. Mostly they deal with the CODEL traffic shaping. I got them from the related thread and that part is working.
The DNS traffic out of state happens when I enabled forwarding for the DNS resolver, so pfSense connects to those public DNS directly from the WAN, but for some reason, some of the traffic back is flagged as out of state and gets dropped.
@gertjan said in Default rule blocking some Outgoing DNS:
"1000000104 " is the default interface final block all rule.
block out inet all tracker 1000000104 label "Default deny rule IPv4"remove the check here :

Can't tell why 8.8.8.8 and 1.1.1.1 is contacting your WAN 'out of state'.
I know that's the default deny rule, I check that on purpose, to see what gets blocked. Unchecking it will just stop the logging, but the traffic will still get blocked.
-
@pfnow Is the out of state traffic breaking DNS?
-
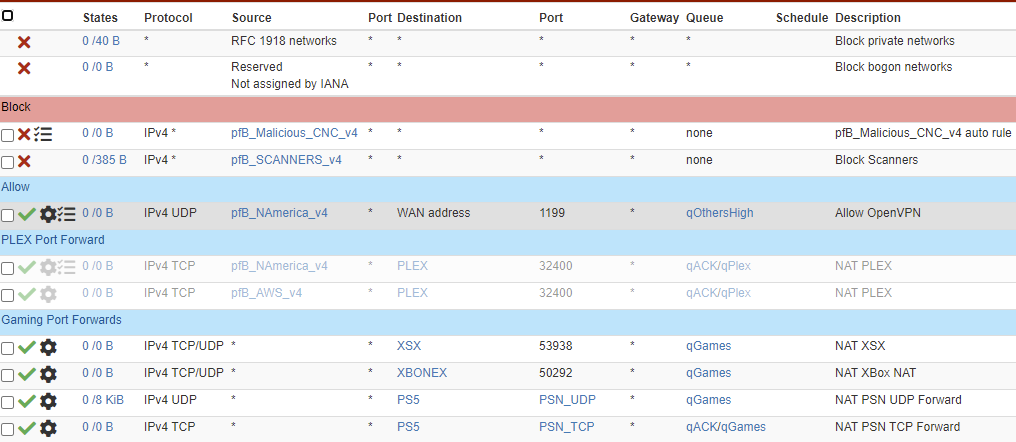
@pfnow Please show the FLOATING rules and WAN rules. Not just the WAN-FLOATING rules.
-
@hieroglyph no, DNS resolution seems to be working. I just found all the out of state blocking weird.
Here is the WAN FW tab
-
@pfnow Nothing looks crazy in your rules. So there is either something weird happening with the DNS resolver/resolver settings. Or you states are expiring fast.
Are 1.1.1.1, 8.8.8.8, and 8.8.4.4 the only three DNS servers you are using? If you are using other DNS servers are they also showing as being blocked by the default WAN rule?