Wireguard Remote Access configuration. No access to Internet
-
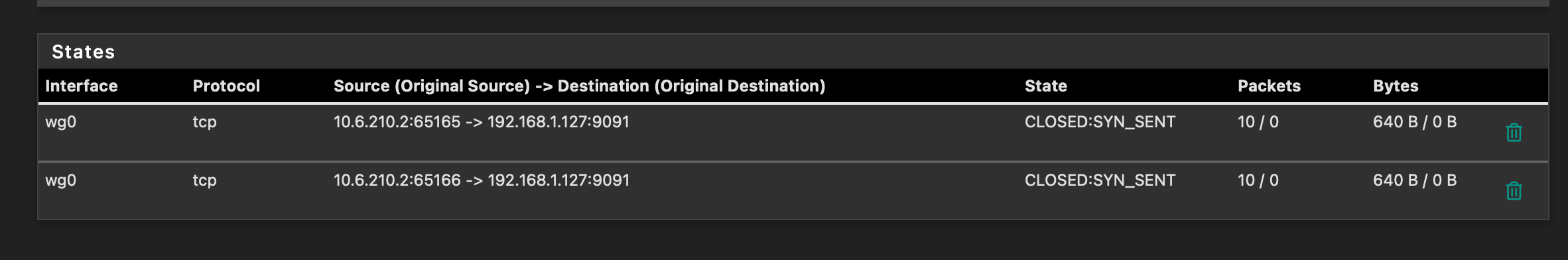
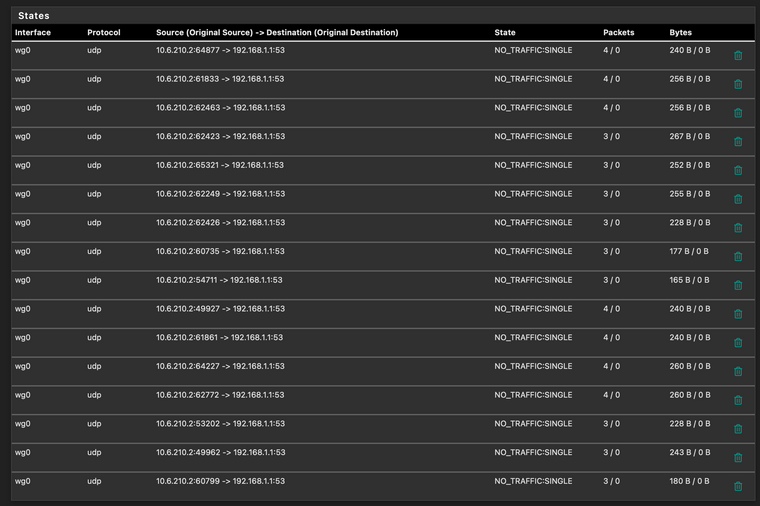
I have followed the instruction from here, however I cannot access Internet, though local network is accessible. I'm able to ping from/to LAN<->Wireguard networks. Looking at the Rule's states, looks like DNS requests is not going through, also not able to open transmission interface.
I have tried to switch off DNS rebind check, Static route filtering, but none of this resolves the issues, Would appreciate any hint on how to resolve this. Thanks.
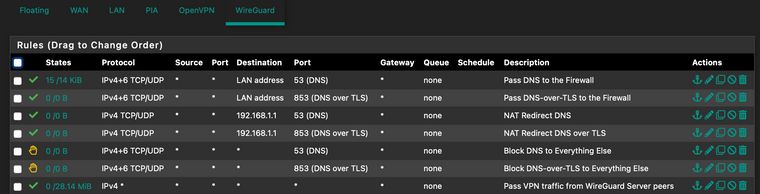
Fiirewall rules:
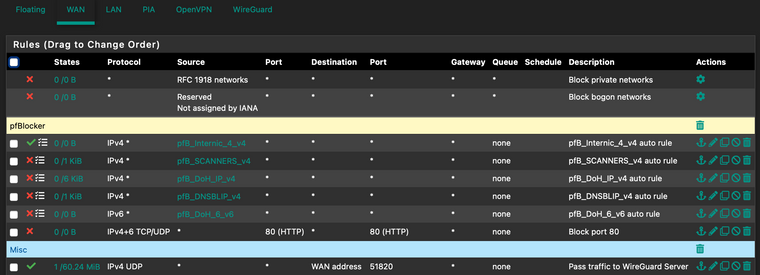
Wireguard config:
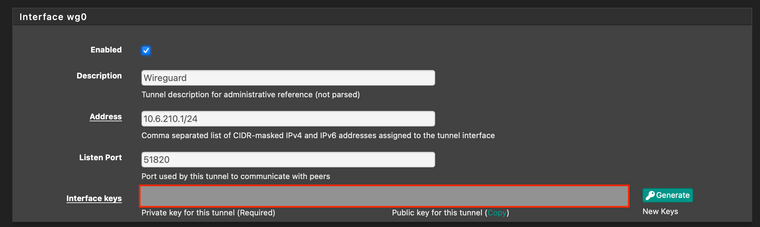
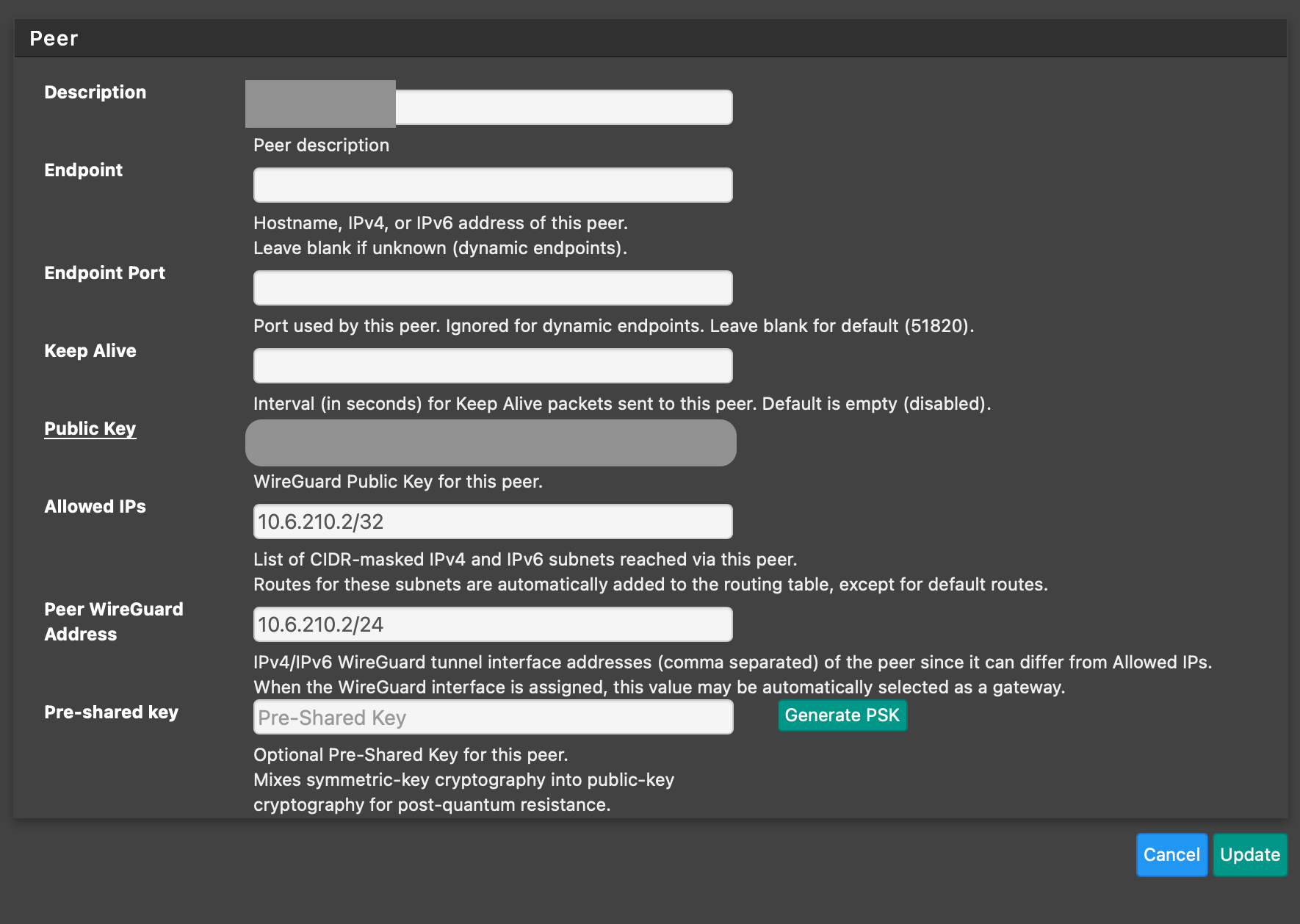
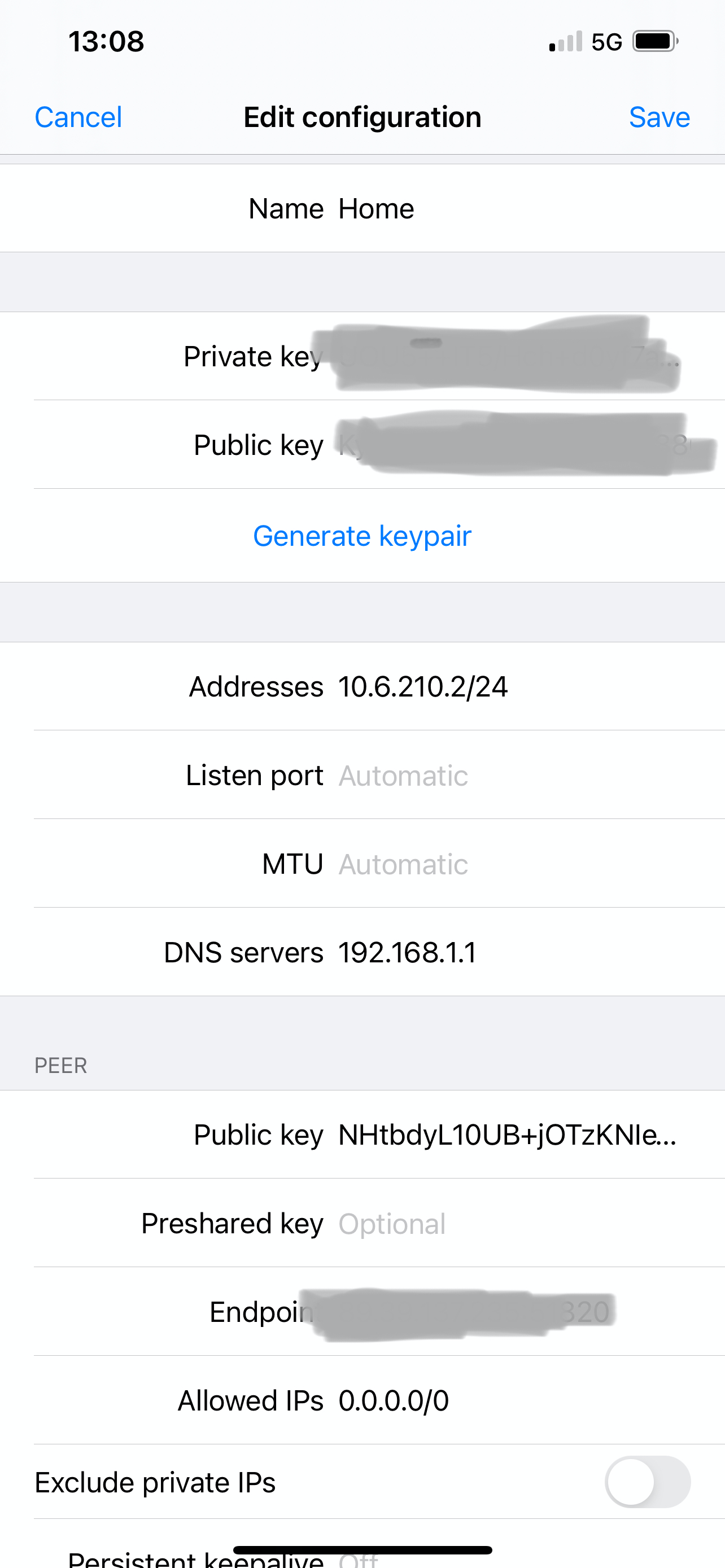
-
@universex nice name !
You need a few things -
-
first assign an interface as per here - lets call it WG https://docs.netgate.com/pfsense/en/latest/vpn/wireguard/assign.html
-
Move rules from your existing Wireguard group to this new interface - WG. Its important not to have any rules in the Wireguard group. https://docs.netgate.com/pfsense/en/latest/vpn/wireguard/rules.html. Rules on the WireGuard group tab are matched first, so ensure rules on the group tab are removed, disabled, or do not match traffic which requires reply-to.
-
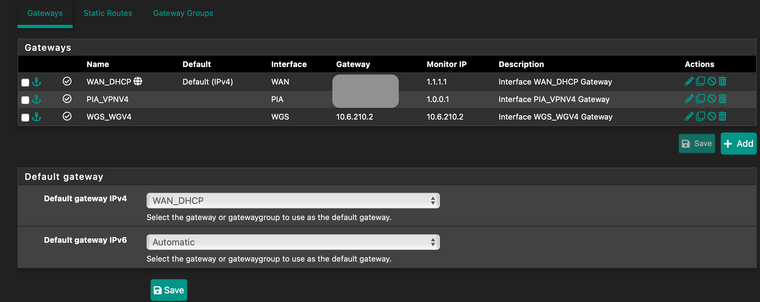
Goto System > Routing > Gateways // Select Default IPv4 GW as WAN_DHCP > don't leave it on auto
-
Lastly set a NAT rule to NAT pfsense LAN to the WG interface IP.
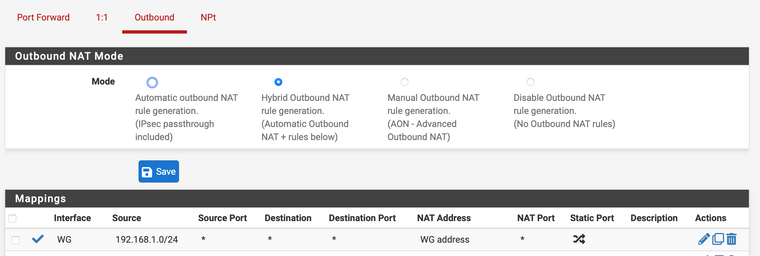
-
-
@ab5g thanks for the reply.
I've done everything as advised, however still not working. Getting the same errors.
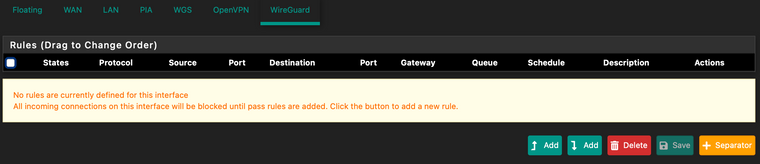
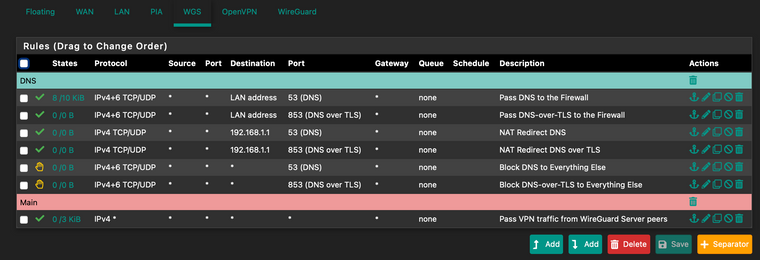
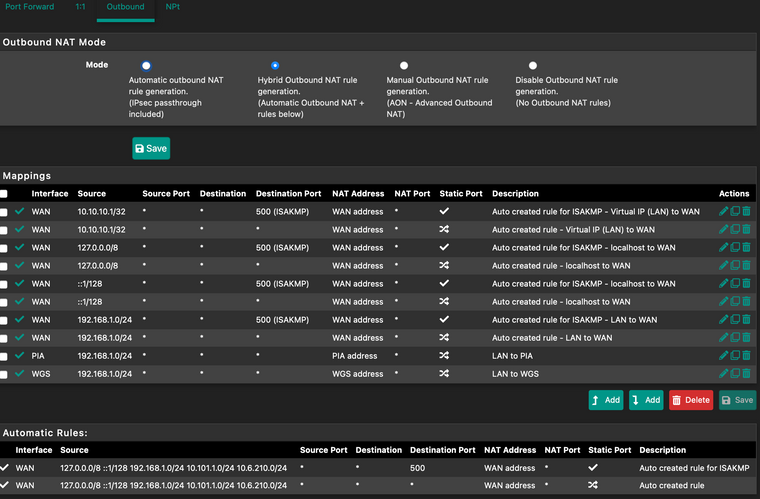
-
Your settings look good to me... and I didn't add a NAT rule and it's working fine for me. I don't believe outbound NAT is necessary on the WG interface for a simple remote access VPN. I think NAT becomes an issue if you're trying to connect two networks to each other, or if you're using a VPN provider for internet access, since you have multiple devices whose traffic is going over the VPN as if it were a WAN connection.
I did assign an interface, but had gotten it working before I assigned the interface. It worked fine before and after doing it though.
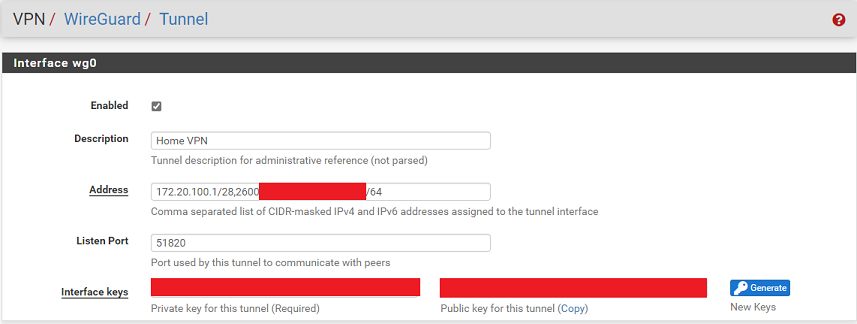
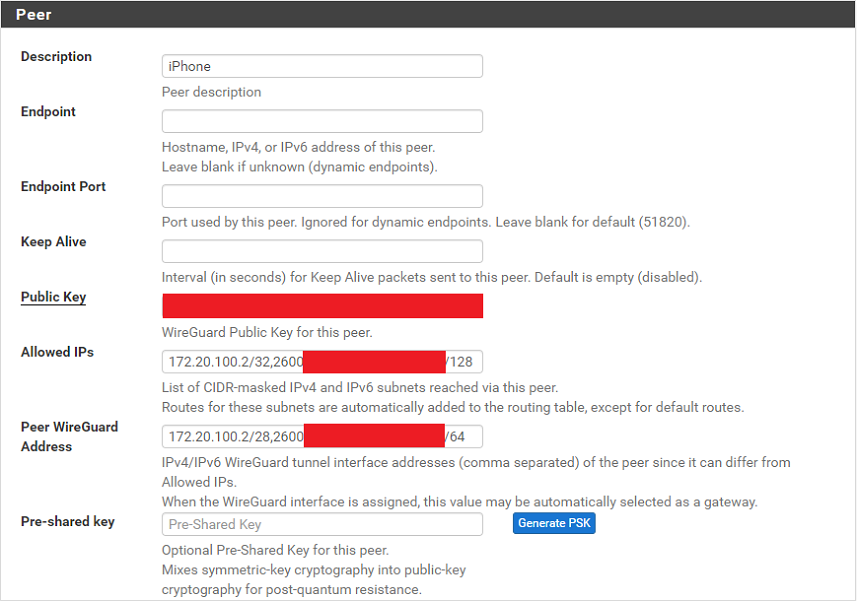
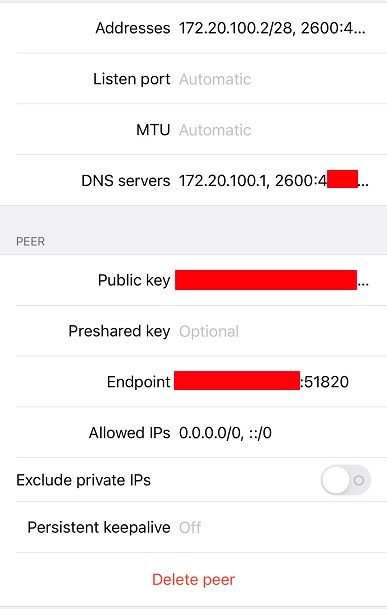
My setting screenshots are below (I used a smaller /28 rather than /24 for IPv4). I didn't include firewall rules for the WG interface... the only one I have is an "Allow All", as well as the rule on WAN for port 51820.
Also, you might want to restart Unbound if you're using that for DNS... I found that needed to be done in order for it to recognize DNS requests from my remote device. Or check your Unbound settings if you limit the interfaces that Unbound can accept connections from.
-
@universex You settings look ok.
Please restart the wireguard tunnel by going to VPN>WireGuard>Tunnel - edit and then save. If that doesn't work try a tcpdump on
- the wireguard interface like tcpdump -I wg0 host <destination you are pinging>
- Next run the same tcpdump on WAN interface to see packets are going to the WAN interface.
-
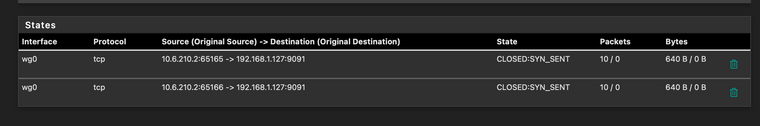
Thanks @virgiliomi, setting DNS to 10.6.210.1 has resolved the issue. Though I'm still seeing CLOSED:SYN_SENT against Transmission, but this I guess something else.