[SOLVED] DNS Zone Transfer
-
Hi,
I trying to configure secondary dns zone on windows server. How do I make PfSense DNS Server allow that transfer? I am using pfsense as Master dns server.
Thanks.
-
@manjotsc
Just a guess: There is an unbound manual : https://man.openbsd.org/unbound.conf
There is a custom option field in the pfsense gui.
Looking into that manual shows some Zone transfer commands.
If you can find the right for you, just enter that into the custom options and restart unbound afterwards. -
@manjotsc said in DNS Zone Tranfer:
How do I make PfSense DNS Server allow that transfer? I am using pfsense as Master dns server.
unbound as an authoritative name server for a domain ?
Or, for that matter : pfSense as a authoritative name server for a domain ??Compare https://en.wikipedia.org/wiki/BIND with https://en.wikipedia.org/wiki/Unbound_(DNS_server) and https://en.wikipedia.org/wiki/Comparison_of_DNS_server_software
So, it can be done. Stop using unbound - or dnsmasq (the forwarder).
You'll be needing bind - the pfSense package. Which is, if I recall, isn't usable right now, see recent forum messages for details.My personal advise : setting up bind using a GUI, the pfSense GUI ? That seems a very hard thing to do if you never have dealt (seriously) with bind before.
-
@manjotsc said in DNS Zone Tranfer:
Hi,
I trying to configure secondary dns zone on windows server. How do I make PfSense DNS Server allow that transfer? I am using pfsense as Master dns server.
Thanks.
Using non-Microsoft DNS servers as a secondary DNS zone target can be fraught with difficulties. Mostly this comes from the way Active Directory insists on doing certain things. While it can be done with
bind, as @Gertjan mentioned, it can be a frustrating experience to get working correctly.If you really want a secondary DNS for AD, I would suggest biting the bullet and standing up another Windows server. It can be a virtual machine (just not on the same physical host as your current Windows server if you want real redundancy).
-
@bmeeks said in DNS Zone Tranfer:
While it can be done with bind, as @Gertjan mentioned, it can be a frustrating experience to get working correctly.
IMHO : Understanding bind help you tackle THE question : How does Internet work. More precise :
That's not frustrating. I saw that ones as totally mandatory, if I wanted to have that impression that I might have understood something about this "DNS" thing.Edit : using 'bind' on a pfSense is making it yourself really hard.
bind is not GUI friendly - in the past - and it won't be so in the future.
An authoritative domain (name) server shouldn't be run on a firewall (as any server for that matter).Again : just my 2 cents.
-
-
@manjotsc said in DNS Zone Tranfer:
@gertjan @pete35 @bmeeks Let's say if bind is not the best way to go. Is is possible to make unbound listen on 192.168.40.4 on port 53 and on 1.1.1.1 at port 853?
The official
unbounddocumentation is here: https://nlnetlabs.nl/documentation/unbound/unbound.conf/.It appears you can configure
unboundto listen on multiple interfaces, and with a different listening port on each interface. However, I'm not sure you can do that within the pfSense GUI. You might can pull something like that off using the Custom Options section, but I'm doubtful because the settings you need there are also put into the configuration file by the GUI code (interfaces and port). You could wind up with duplicate settings in the configuration file andunboundmay not like that.The GUI lets you choose multiple interfaces to listen on, but when you choose a port (either 53 or 853), it uses that port for all interfaces.
What exactly are you trying to accomplish? Are you after redundancy for your Windows DNS server, or something else? I'm having trouble understanding how zone transfers figure into listening on different ports (and, I assume, using TLS on the 853 port).
-
@bmeeks The problem I am running into is that, I have windows computer that needs to be pointed to windows server dns, but on the rest of devices I am using pfsense as main dns because of pfblockerng. I want use pfsense dns on all devices so they can resolve the domain I have in windows server.
-
It seems that unbound can consult (local) zone information , even do XFERs.
See https://nlnetlabs.nl/documentation/unbound/unbound.conf/ -
@manjotsc said in DNS Zone Tranfer:
@bmeeks The problem I am running into is that, I have windows computer that needs to be pointed to windows server dns, but on the rest of devices I am using pfsense as main dns because of pfblockerng. I want use pfsense dns on all devices so they can resolve the domain I have in windows server.
Then I would do this.
- Set up
unboundand pfBlockerNG-devel/DNSBL as normal. - Within
unbound, set up a Domain Override for your local Windows AD domain. Don't forget to also include a reverse pointer look-up zone as part of the override. This domain override tellsunboundto ask your Windows DNS server for any lookups from that zone. This would normally be when resolving hosts or IPs from logs or maybe the ARP Table display in pfSense. - On your Windows AD DNS server, configure it for forwarding and point it to your pfSense box (where
unboundis running) as the forwarding server. - Point all of your internal hosts to the Windows DNS server for DNS.
This setup is actually what I use for my personal system. This way Windows clients can get all the AD stuff they need, but all queries for non-local stuff will be forwarded to
unboundon pfSense which will resolve via the DNS roots. And if you askunboundfor anything relating to your Windows AD, thenunboundwill forward those queries to the Windows AD DNS server because of the configured domain override. - Set up
-
@bmeeks This what I had as config, the problem with this is, if a create a static mapping in pfsense for example test.manjot.net, but since devices are pointed to windows server, it will not resolve test.manjot.net unless i manully create that record on windows server.
-
@manjotsc said in DNS Zone Tranfer:
@bmeeks This what I had as config, the problem with this is, if a create a static mapping in pfsense for example test.manjot.net, but since devices are pointed to windows server, it will not resolve test.manjot.net unless i manully create that record on windows server.
What is the issue of creating the static mapping over in Windows? Really, for a Windows AD domain, you want your DHCP and DNS all handled by Windows anyway (usually all on a domain controller box).
In terms of effort, logging in and creating the mapping in Windows versus doing the same on pfSense seems the same. Maybe I'm missing something critical in what you want to do.
-
@bmeeks I looking for some automation between pfsense and windows server to sync DNS A records from pfsense static mapping.
-
@manjotsc Again, why not just put the static DNS mapping on the windows DNS server? Why the insistence on using pfSense for DNS? You already have fully-functional DNS servers on Windows.
-
While
unboundcan do a lot of things on its own, doing all of them within the pfSense GUI is not so easy. Here is the official documentation forunbound: https://www.nlnetlabs.nl/documentation/unbound/.What most of us replying to this thread are saying is that things will be easier for you to just use the Windows AD environment completely for DHCP and DNS with it forwarding to
unboundfor external lookups so you can take advantage of the DNSBL feature of pfBlockerNG-devel. And put any static mappings in Windows. With the domain override properly configured inunboundwithin the pfSense GUI, any statically-mapped host will resolve just fine from either a Windows machine or the pfSense machine (or any other local host pointing to the Windows DNS server). -
@manjotsc said in DNS Zone Tranfer:
I have windows computer that needs to be pointed to windows server dns, but on the rest of devices I am using pfsense as main dns because of pfblockerng
Huh? As others have stated just point ALL your devices to your AD dns.. Then have your AD dns forward to unbound on pfsense - there you go all your devices using pfblocker.. Done! 30 seconds of configuration..
-
@manjotsc: since we do not know your skill level with DNS, some assumptions were made in our responses.
Do you know the difference between resolving and forwarding DNS servers?
Do you know what a domain override entry is used for in say
unbound?I'm wondering if some of our replies have not been fully understood. Not saying this to impune your ability, just honestly asking. Folks post here with many different skill sets, and sometimes answers can be tweaked for better understanding.
-
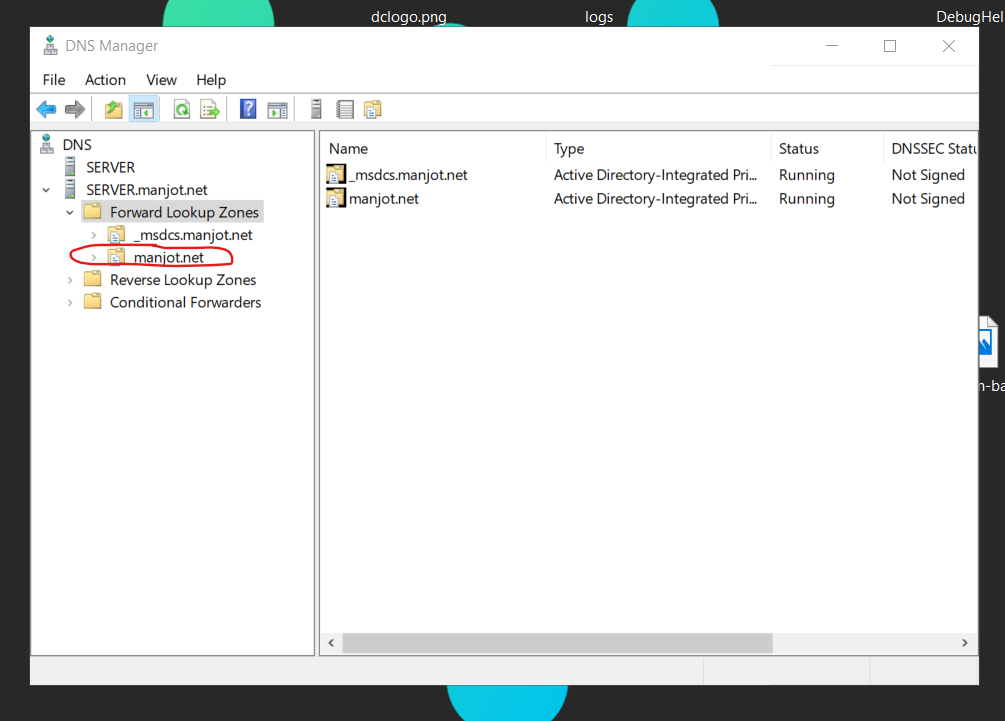
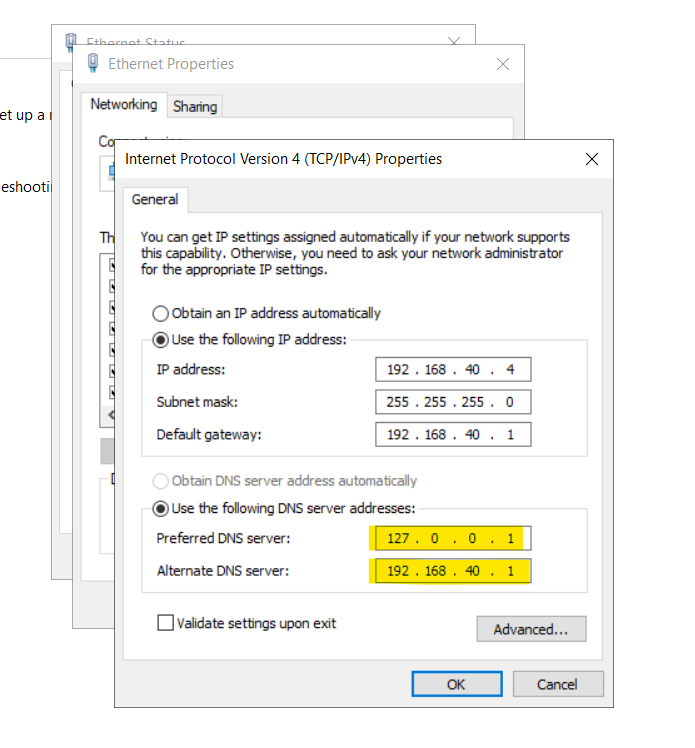
@johnpoz @bmeeks @Derelict @Gertjan Ok I got, I over looked the things a bit, my under standing was that windows server would never forward same domain request to forwarders dns servers. I had to do was delete the manjot.net under Forward DNS Zones and set the primary dns to 127.0.01 and secondary dns to pfsense 192.168.40.1.
Deleted manjot.net
Set DNS Servers on Domain Controller
-
@manjotsc said in DNS Zone Tranfer:
@johnpoz @bmeeks @Derelict @Gertjan Ok I got, I over looked the things a bit, my under standing was that windows server would never forward same domain request to forwarders dns servers. I had to do was delete the manjot.net under Forward DNS Zones and set the primary dns to 127.0.01 and secondary dns to pfsense 192.168.40.1.
Deleted manjot.net

Set DNS Servers on Domain Controller

Deleting that forward lookup zone is correct. It should never have been there.
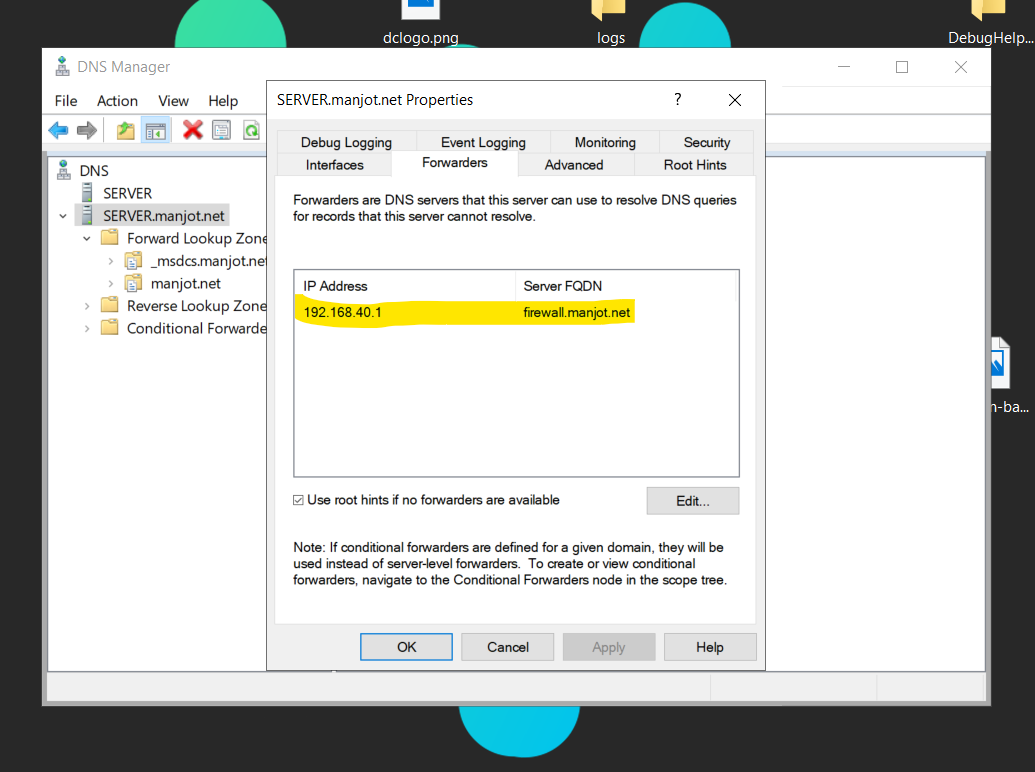
However, I'm not sure your DNS Server IP settings are correct. If that 192.168.40.1 IP is your pfSense box, don't do that! Instead, go back to DNS Manager, right-click on the server in the left-hand pane, choose Properties, and enter the pfSense box as the IP of the Forwarding server.
I'm not sure that you fully understand what a Forwarder is. Do a quick search on Google for the diferrence between a Forwarder and a Resolver in DNS. Also check out this link for configuring a Forwarder in Windows DNS: https://technogecko.net/msft/how-to-add-dns-forwarders-in-windows-server-dns/. You should put the IP address of your pfSense box in the Forwarder IP.
-