VPN rules Hierarchy
-
I'm hoping that someone can provide a little guidance for me on how to setup my firewall and make sure that it is secure. I've had pfSense setup for about 3 years but recently when trying to diagnose another issue I was told that my firewall wasn't doing what I thought it was doing.
Here is the rule on my IoT vLAN:
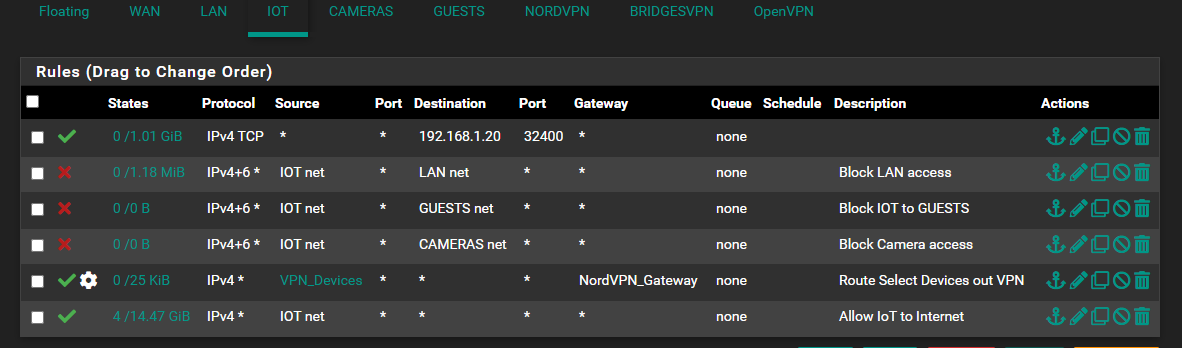
My understanding of this is that I am blocking access from my IoT lan to any other vLAN, the only exception to this is my Plex server which operates at .20 address. It should allow access to the Internet and allow any devices in my VPN_Device alias to hit the VPN gateway.
Is this the most efficient way to do this? Is my order incorrect?
-
How your rules read:
-
Allow Any TCPv4 traffic, from any device, to 192.168.1.20, at port 32400, exit using default gateway
-
Block all IPv4/6 traffic, from devices on IOT net, to LAN net, at all ports
-
Block all IPv4/6 traffic, from devices on IOT net, to GUEST net, at all ports
-
Block all IPv4/6 traffic, from devices on IOT net, to CAMERAS net, at all ports
-
Allow all IPv4 traffic, from VPN_Devices, to All, exit using NordVPN gateway
-
Allow all IPv4 traffic, from IOT net, to All, exit using default gateway
Others may see things I do not see.
The biggest thing I see is no block rule after your policy routing rule. If the NordVPN gateway goes down for any reason (i.e. maintenance, intermittent connection, password/key changes on website before updating pfsense, etc...); the NordVPN_Gateway rule will be skipped and all traffic from the VPN_Devices will use the last rule to exit out of your default gateway. (This assumes devices in the VPN_Device alias are on in the IOT net.) This block rule will look like this:
- Reject/Block any IPv4, from VPN_Devices, to All, exit using default gateway
The next thing is EVERYTHING on the IOT network can access 192.168.1.20 (plex server?) at port 32400. Maybe that is not a big deal. But likely everything does not need access to 192.168.1.20:32400.
Lastly, IOT_Devices can reach the openVPN, NordVPN, and BridgesVPN nets. Get rid of the x3 block rules and instead use x1 block rule with an alias which holds all RFC1918 networks (10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16) to block IOT devices from reaching all RFC1918 local networks. This would include the nets openVPN, NordVPN, and BridgesVPN are using.
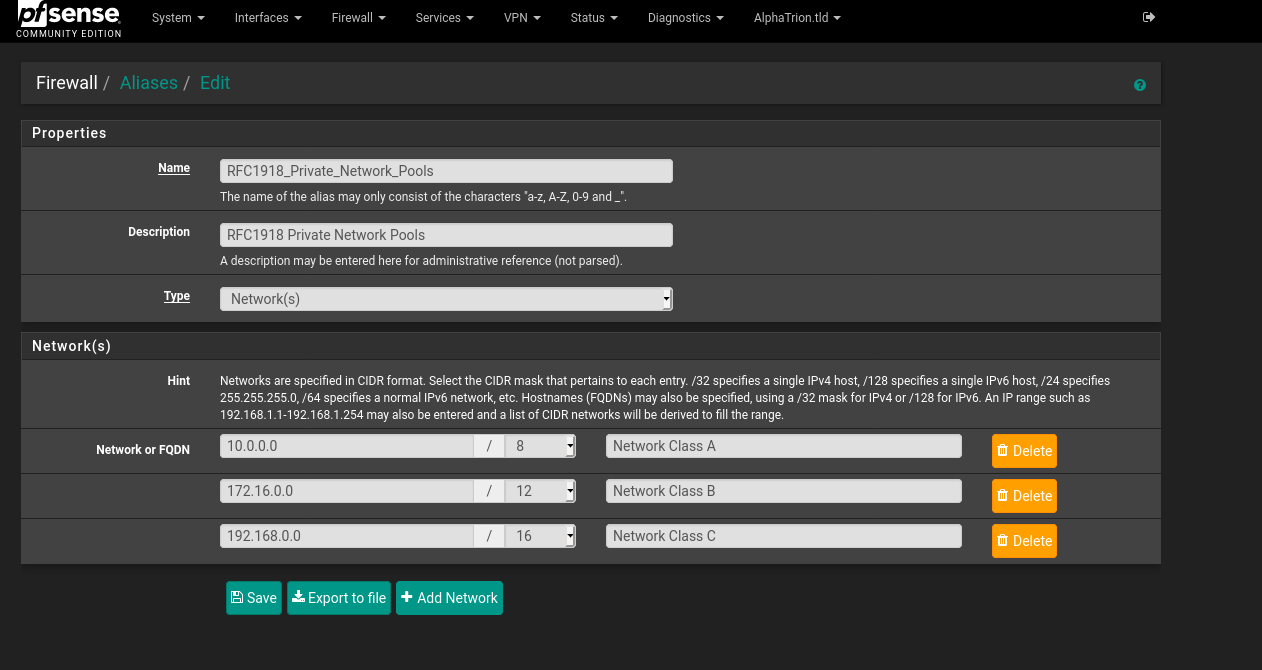
-
-
@vmac Just noticed. Any device using IPv6 will exit using the default gateway. The only rule affecting IPv6 are the rules preventing LAN, GUEST, and CAMERAS net access. On the LAN interfaces there is a default allow all rule at the bottom (hidden). So if a VPN_Device is using IPv6 instead of IPv4 it will not exiting using NordVPN. It will exit using the default gateway.