No alerts from pfsense/Suricata in Virtualbox
-
Hello there,
I am trying to setup a test-lab to make some comparisons between suricata and snort.
I did set up a Host-Only Network (172.16.100.0/24) via Virtualbox containing a Metasploitable-VM and a fresh Ubuntu-installation.
Also I created a Nat Network (10.0.100.0/24) containing a Kali-Linux VM.
Both networks are connected via pfsense which seems to work, since the VMs can Ping each other and all the VMs can connect to the internet.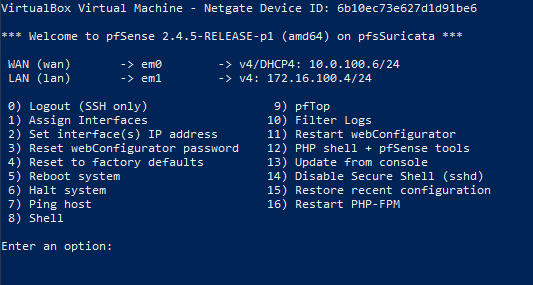
But shouldn't I get alerts when running nmap-scans from the Kali-VM against anything inside the Host-Only-Network?
Suricata is running on both, the WAN and LAN interface of pfsense.
Home_Net is on default:
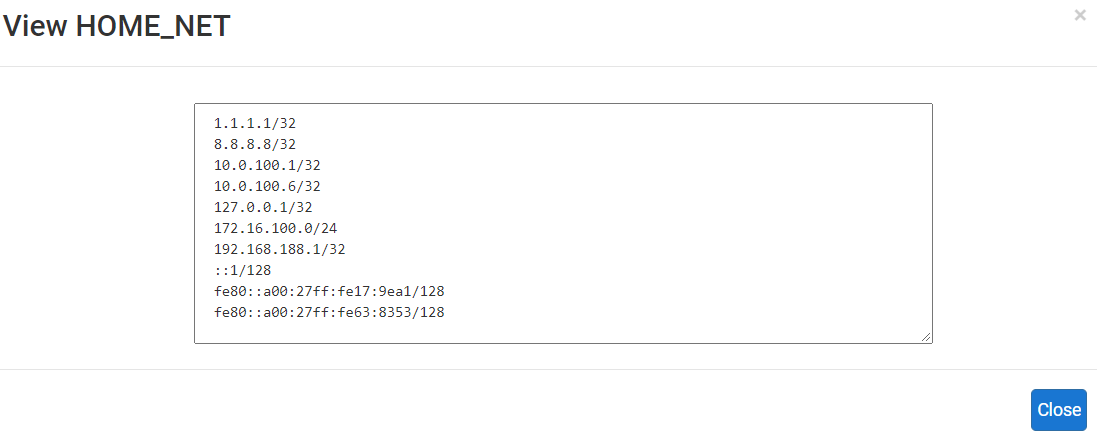
Nat-Network: 10.0.100.0/24
Host-Only-Network: 172.16.100.0/24
Kali-Ip: 10.0.100.5/32
Metasploitable-Ip: 172.16.100.11/32Any help would be greatly appreciated.
-
You don't mention what rules, if any, you have enabled. Do you actually have the correct rules in place on the interfaces to detect your scans?
I use a similar setup all the time when testing new releases of the Snort and Suricata packages before posting them. I usually use the ET-Scan rules category and run a simple
nmapSYN scan against a target like so:nmap -sS <target_ip>If you are not seeing alerts, and you have the proper rules deployed, then I would double-check my virtual switch setup to be sure you are not bypassing the firewall with the traffic. I use VMware Workstation instead of Virtualbox for my testing.
-
@bmeeks
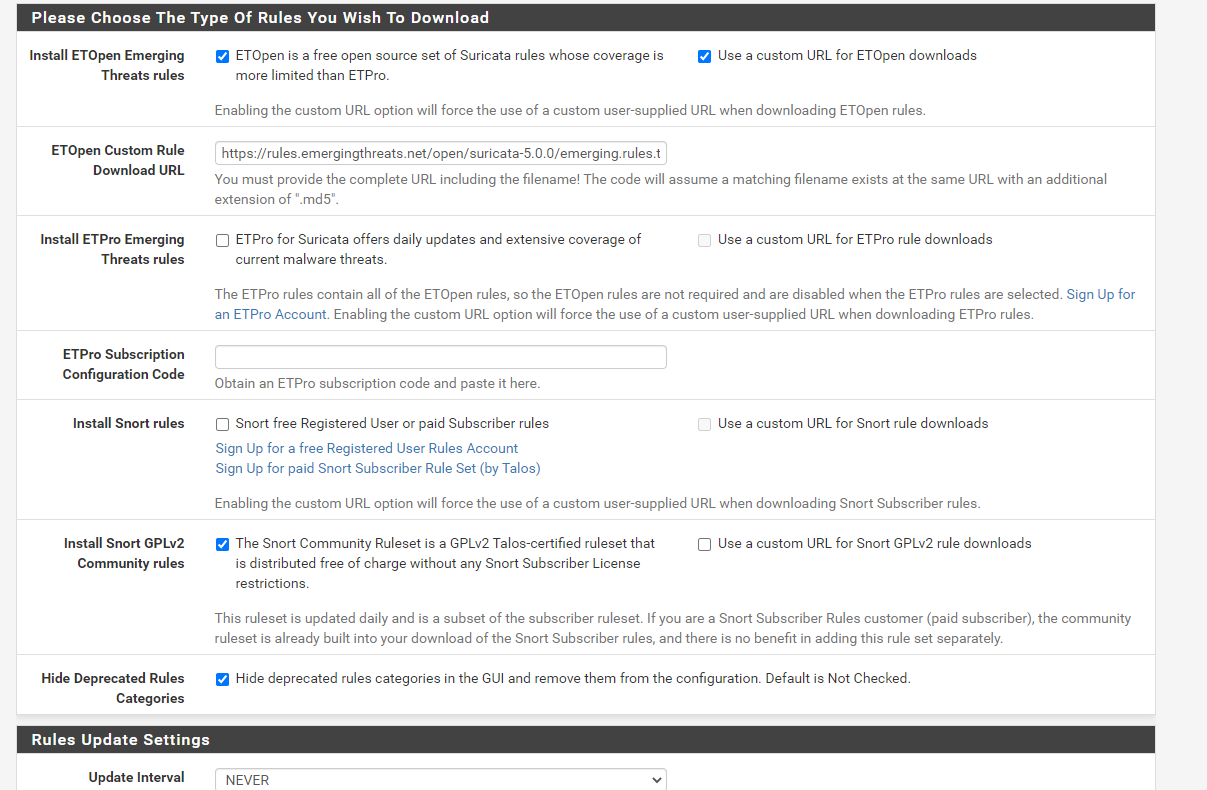
Sorry for not mentioning the rules.I downloaded ETOpen rules, and Enabled all Categories.
I do now and then get some alerts, but these seem to be known false alerts.
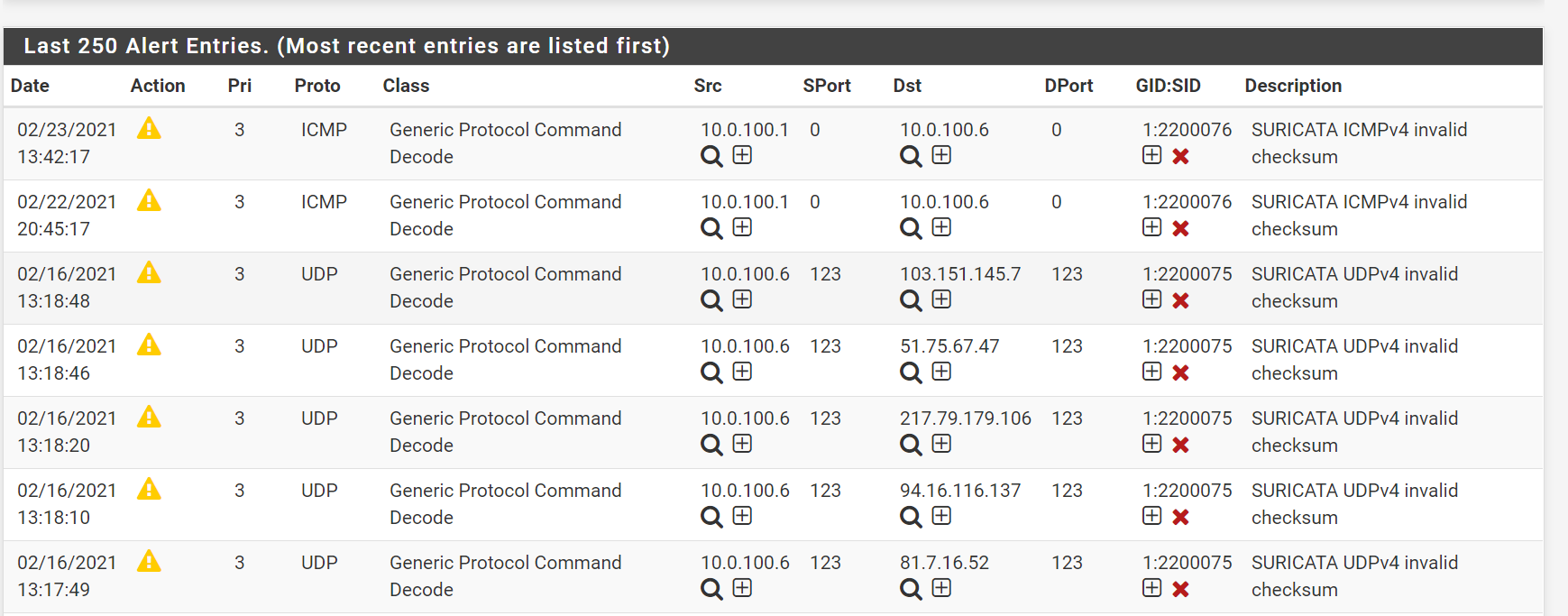
How could it happen that my traffic bypasses the firewall?
I thought it should not be possible to ping from my Nat-Network into the Host-Only-Network without pfsense connecting both networks. -
I'm not a Virtualbox user, so I can't say for sure what you should check to see about a bypass.
I can tell you absolutely that Suricata works and will trigger alerts when you have the correct configuration. I do this all the time.
By the way, you do not need to be using the "Custom URL" option for the ET Open rules. Just check the box to "Install ETOpen Emerging Threats Rules" and uncheck the "Use a Custom URL" box. It has nothing to do with your current problem, but you don't need that configuration. That option is there only for users that have a central internal server of their own where they want to distribute rules to internal clients. If you are downloading straight from emergingthreats.net, there is no need for a custom URL.
What is your experience level with an IDS? Have you used Snort and Suricata in the past? Have you gone to the CATEGORIES tab for your interfaces and selected the rules categories there and saved the changes? Your screenshot of the ALERTS tab indicates you are only using the default built-in rules.
-
@bmeeks
I unchecked the Custom URL box.
And yes, I went to "LAN Categories" and selected all rules and saved.
Then get the message "Suricata is 'live-loading' the new rule set on this interface."
It is my first IDS setup.
I found in "Diagnostics"-Tab that it is only 1 hop to the Metasploitable VM and also 1 hop to kali, which makes me confident both VMs are connected to pfsense.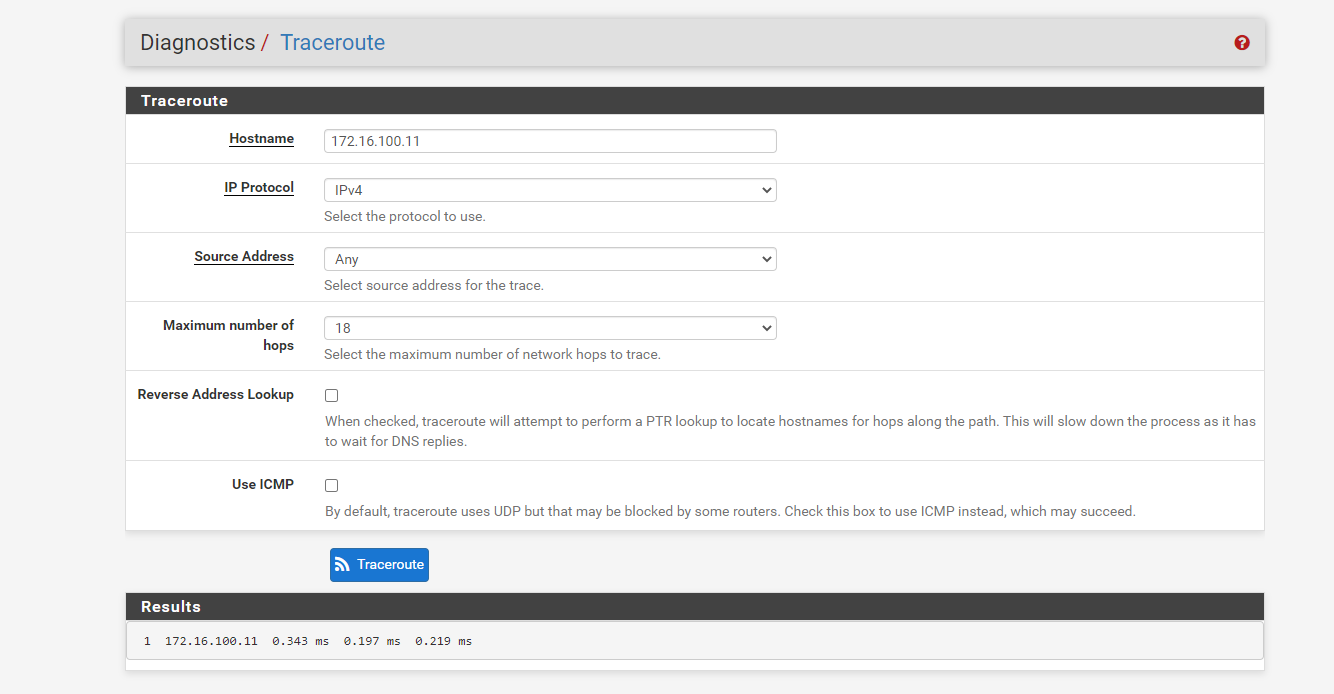
-
Running tracert from your firewall itself does not mean much. It is not telling you how the Kali Linux VM, for example, is reaching the hosts you are scanning.
You would want to run the tracert from the Kali Linux machine and see if the traffic is going "through" pfSense to reach the other hosts.
Run this exact command from a shell prompt on your Kali host and see what you get-
nmap -sS 172.16.100.11Then see if you have alerts in Suricata for scans against VNC ports and perhaps SQL Server and others from the Kali host to the host at 172.16.100.11.
-
Traceroute from kali to metasploitable does not look too good :(
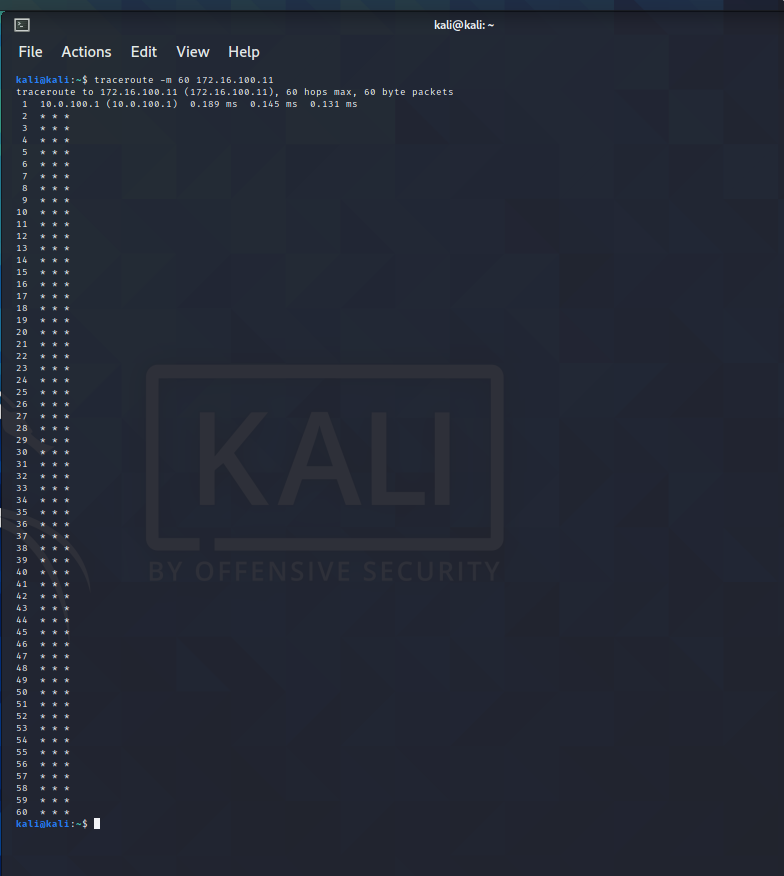
but with -I option:
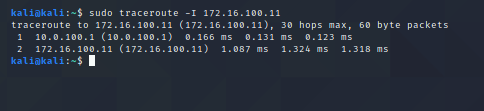
So does this actually tell me that the traffic is not going through pfsense (WAN = 10.0.100.6/24, but somehow directly via the Virtualbox gateway?
Changed default gateway to pfsense-WAN, seems to work now (except no internet anymore, but guess i can fix that somehow, too).
I do get alerts!!! :)
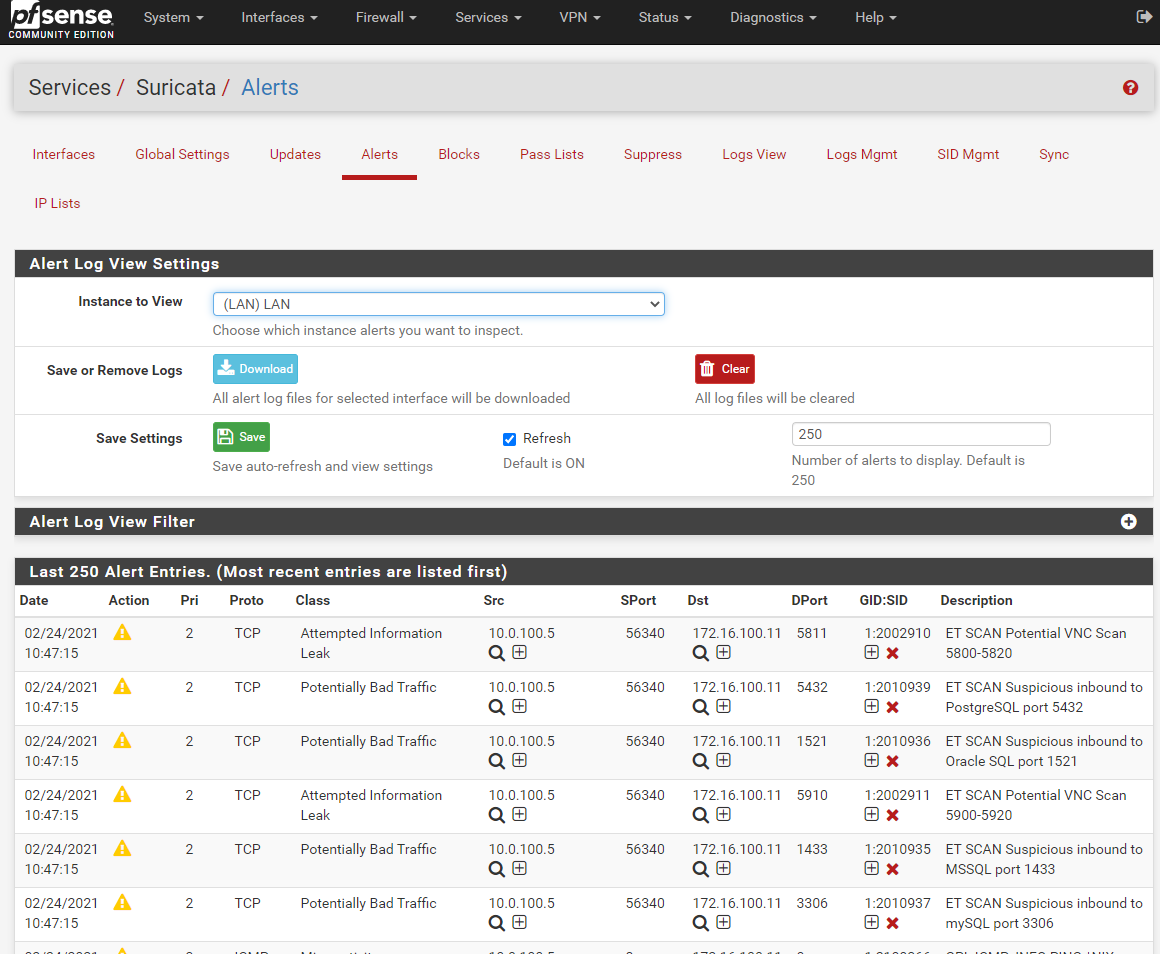
Thank you very much!
Let love rule! -
I'm not a Virtualbox user, so I can't help you there. Host networks in workstation-level hypervisors can be tricky. You really need the concept of virtual switches like you can use in ESXi and other hypervisors. That way you can keep things separate.