OpenVPN JumpCloud Server Certificate not showing up
-
anyone able to assist on this, i haven't had to mess with certs much and i am probably doing something wrong. im having some trouble with getting a jumpcloud server cert showing up under OpenVPN server settings field "Server certificate"
I am running pfsense 2.5.0
I am following instructions here: https://support.jumpcloud.com/support/s/article/jumpcloud-ldaps-ssl-certificate1#Command
the KB article above indicates the following command outputs only the JumpCloud LDAP Server certificate
echo -n | openssl s_client -connect ldap.jumpcloud.com:636 | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > /tmp/jumpcloud.ldap.pemi run that command from my ubuntu vm, and then go to System > Cert Manager > Certificates > add/sign
import existing certificate
paste in the certificate data that was generated from the command above
save
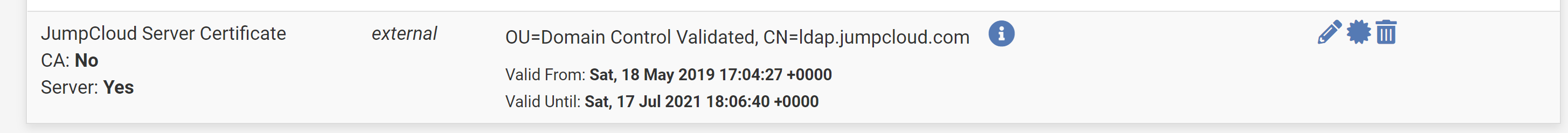
I see the cert added as a Server cert.
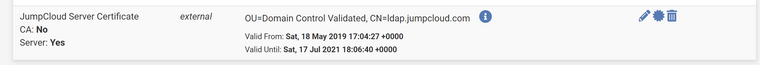
Now i go to add an OpenVPN server and its not listed under Server certificate.
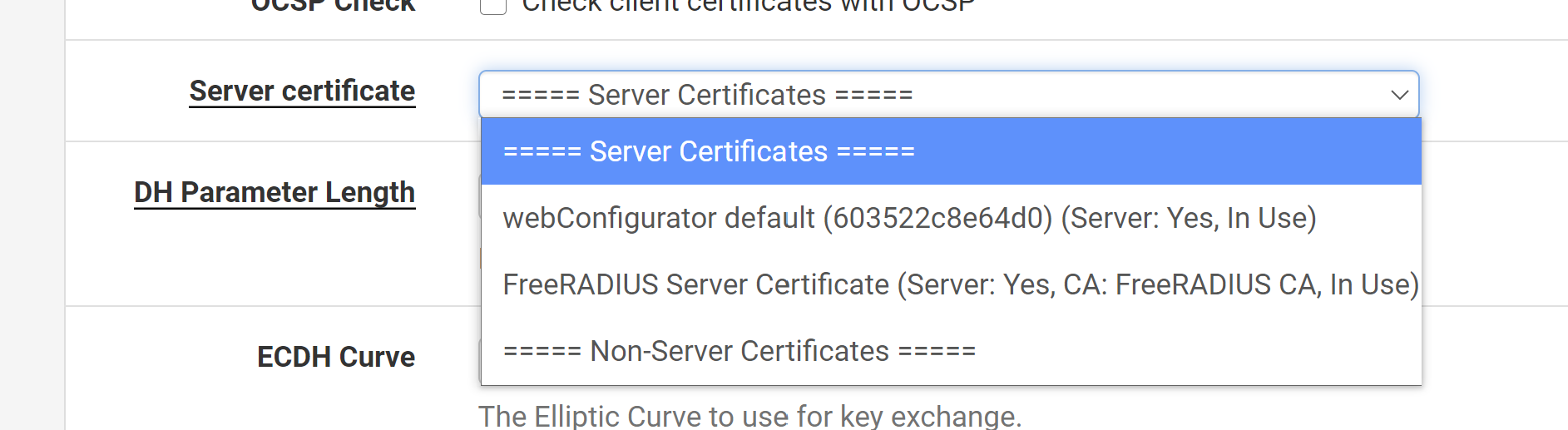
Much appreciated
-
so after a bit of playing around i ended up figuring out how to get it working. i'm not the best with certs but here is a video for how to configure:
steps:
- list itemBefore anything, follow the instructions on JumpCloud for setting up LDAP and binding a user to LDAP: https://support.jumpcloud.com/support/s/article/using-jumpclouds-ldap-as-a-service1
- The following command outputs the certificate authority to the /tmp/ directory as jumpcloud.chain.pem.
echo -n | openssl s_client -connect ldap.jumpcloud.com:636 -showcerts | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > /tmp/jumpcloud.chain.pem-
Skip the first certificate of the chain.
-
Add the next 3 certificates in the chain individually as Certificate Authorities in pfSense using the following settings:
-
System > Cert. Manager > CAs tab > Add
-
Descriptive name: JumpCloud CA (add a 1, 2, and 3 after each certificate)
-
Method: Import an Existing Ceritifcate Authority
-
Trust Store: check this box
-
Randomize Serial: check this box
-
Certificate Data: paste the single certificate here
-
Save
- The following command outputs only the JumpCloud LDAP Server certificate to the /tmp/ directory as jumpcloud.ldap.pem
echo -n | openssl s_client -connectldap.jumpcloud.com:636 | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > /tmp/jumpcloud.ldap.pem- Add the Server Certificate to pfSense.
-
System > Cert. Manager > Certificates tab > Add/Sign
-
Method: Import an Existing Certificate
-
Descriptive name: JumpCloud Server Certificate
-
Certificate data: paste the certificate here
-
Save
If you don't have a JumpCloud account set up and bound to LDAP, you'll need to do that first.
You can use your account or create a new user. There only needs to be one bound account but there can be multiple.
In JumpCloud:
-
Users > Select the user you'd like bound to LDAP > User Security Settings and Permissions > check the Enable as LDAP Bind DN box and Save user
-
LDAP > Add a new LDAP server > Add the user groups or users
-
Create the LDAP Server in pfSense
NOTE: you can get YOUR_ORG_ID from JumpCloud's Settings page
- System > User Manager > Authentication Servers tab > Add
-
LDAP Server Settings:
-
Type: LDAP
-
Hostname or IP Address: ldap.jumpcloud.com
-
Port Value: 636 (SSL)
-
Transport: SSL - Encrypted
-
Peer Certificate Authority: JumpCloud LDAPS SSL Client Certificate
-
Protocol Version: 3
-
Search Scope - Level: Entire Subtree
-
Search Scope - Base DN: ou=Users,o=YOUR_ORG_ID,dc=jumpcloud,dc=com
-
Authentication Containers: ou=Users,o=YOUR_ORG_ID,dc=jumpcloud,dc=com
-
Extended Query: &(objectClass=inetOrgPerson)(uid=*)
-
Bind Credentials - User DN: uid= ldap-binding user,ou=Users,o=YOUR_ORG_ID,dc=jumpcloud,dc=com
-
Bind Credentials - Password: ldap-binding-user's-password
-
User Naming Attribute: uid
-
Group Naming Attribute: cn
-
Group Member Attribute: memberOf
-
Group Object Class: groupOfNames
-
Save
- Test the authentication in pfSense
-
Diagnostics > Authentication > LDAP
-
put in your user name and password and click Test
-
You should see a green box indicating success
Setting up OpenVPN:
-
Type of Server: LDAP
-
LDAP servers: Choose the JumpCloud LDAP server you created in the previous steps
-
Certificate Authority: choose the OpenVPN authority you created earlier
-
Certificate: Choose the OpenVPN certificate you created earlier
-
Change any other settings to your liking and you're all set.