Interest in a WG manager for PIA?
-
I've adapted a wg interface controller I wrote to manage wg based PIA gateways on a linux vm since pfSense didn't have support for wg at the time I started using wg with PIA. I then policy routed my PIA traffic from pfSense thru the linux vm as needed. Now that pfSense supports wg, I've started working on adapting my controller to work with pfSense. This allows me to eliminate the linux vm gateway and simplify my routing setup. Pretty much have a proof of concept working quite nicely. Is there any interest in this type of controller in the community? I'm at the point now where it works pretty much good enough for me so I can either wrap this up and call it a day or if there's interest I can cleanup the code, put some docs together, etc.
What do you get with this controller? The ability to create and maintain multiple wg tunnels with PIA on pfSense. Each tunnel can then be setup as a gateway in pfSense for policy based routing, etc. The controller also will manage port forwarding on each interface, if desired. So you can enable port forwarding on one or more interfaces and the controller grabs a port, authorizes it and keeps the port forward active as needed. The controller then monitors all of the interfaces and if it detects that any of them are down, it will recreate them.
Controller UI:
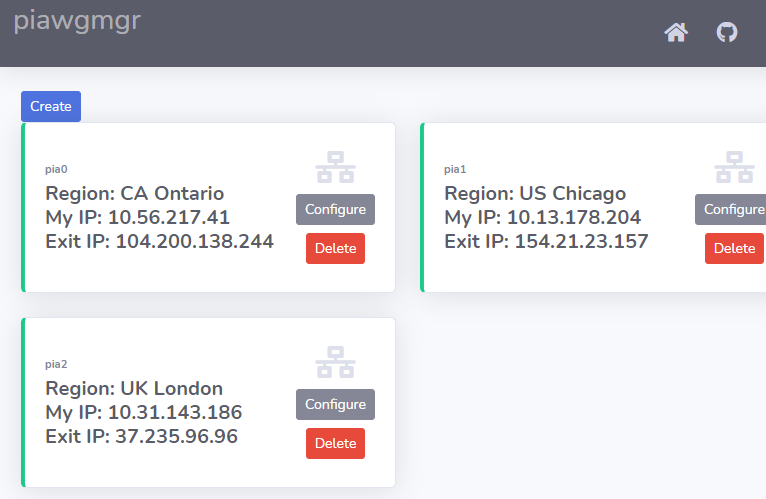
The controller then takes your interface settings and creates and maintains the wg interfaces in pfSense:
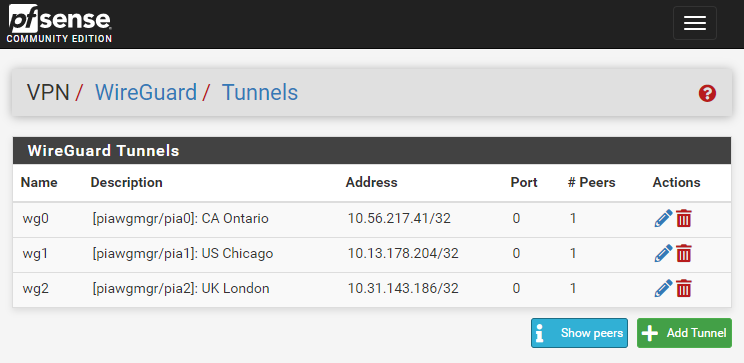
Then once those interfaces are created in pfSense, you're free to assign pfSense interfaces, create gateways and policy route to your heart's content. :D
The controller would be packaged as a docker container and just needs to run from anywhere that it can talk to pfSense over ssh.
-
@slugger I don't know that I understand this sufficiently to say if it would be helpful to me. I do know that I would like to use WG with PIA from my pfSense 2.5 instance. I tried playing with the Linux setup script from github today and I found the configuration file at
/etc/wireguard/pia.confthat it created. This seems to contain interface and peer information in it, I am just not sure how to add this in pfSense.I think a guide to help others setup PIA on pfSense once you have the pia.conf file would be helpful. I also don't understand how I would route all my traffic through WG once it is setup.
-
@ryanm Using PIA's scripts, the final step would be to take the wireguard config file generated and create a WG interface in pfSense. And it would work fine. Create the wg tunnel in pfSense using the settings from that file, assign that tunnel as an interface in pfSense, then use that interface as a gateway for policy routing as usual in pfSense.
The issue that I'm trying to solve in that setup is removing the manual need to create the wg interface. Once the PIA interface goes down, you'd have to do all those manual steps again to recreate the wg interface. The keys always change anytime your tunnel is dropped for whatever reason (intermittent connection loss, etc.). That's where my app comes in. It monitors the tunnels it creates with PIA and keeps (re)creating them as needed.
I'm close. Functionally my app works, I've been running it happily on my LAN for awhile. It's changed a bit since those posts above. I've scrapped the webui thing I was doing on a previous iteration and now it's just a simple config file that you setup with the app that just runs in the background somewhere on your LAN. I plan the docs to be a kind of "typical" setup that will show you how to setup a tunnel that you can route all your traffic through.
-
@Slugger Just started looking at this today. Here is someone's detailed effort for OPNsense, which might be helpful.
https://github.com/FingerlessGlov3s/OPNsensePIAWireguard
Probably will initially do WG from Docker container, but ultimately thru pfSense for selective policy.
-
@js138 Slightly different thing going on over there on OPNSense. Here, we need to get the WireGuard config into the
config.xmlfile so you can do everything else needed (create the gateway, setup the outbound NAT, etc.).I'm getting there. My installation/setup tutorial is coming along nicely. Mind you it is taking me way longer to write these docs than it does to set this up from a fresh pfSense installation. :)
Anyways, a few more evenings of docs and should be good to go. I did find a bug tonight while writing some more docs so feel free to have a look at the docs and let me know if any of it makes sense but I wouldn't go running the docker quite yet. :)
-
@slugger I went through the tutorial pages on Gitlab. I am trying to do something a bit different I think, but I do think I have it somewhat working.
I was able to get to a point where I think I have my WG tunnel and peer defined, and I think the interface, gateway, and outbound rule are there.
I was also able to route traffic through my WG tunnel from a specific host by adding the LAN rule.
However, when I used OVPN, I never had to set the gateway for my LAN to route through it. How can I set my traffic to route by default through WG if it is up, otherwise through my WAN (or OVPN then WAN)? Is there a way to set a gateway preference?
-
@ryanm
System > Routing > Gatewaysand you can select a default gateway there, but I don't recommend setting a VPN connection as the system default gateway. I'm not sure what happens when the selected gateway becomes unavailable. I assume it just picks another one to replace it, but not sure, never tested it. Actually I don't even think it would do that, that doesn't seem right to me.Whereas if you set the gateway via firewall rule, it is documented that if that gateway becomes unavailable it will switch it back to the system default gateway. I've only ever used vpn connections for policy based routing.
-
@slugger Hmm, it is just weird because I didn't seem to need that rule when using OpenVPN. Regardless, I have added the rule to LAN and it seems to be routing my traffic over WG.
-
Given this announcement, I've paused my project and am reassessing things. Likely switching back to my previous Linux vm wireguard gateway setup I had going on. Definitely recommend not proceeding with using my app to config wg on pfsense.
-
M menethoran referenced this topic on
-
M mcury referenced this topic on
-
M mcury referenced this topic on