Wireguard and interfaces
-
@kom can you post a screenshot?
-
@vbman213
Here I have just created a tunnel. Note that Rules now has a WireGuard tab.
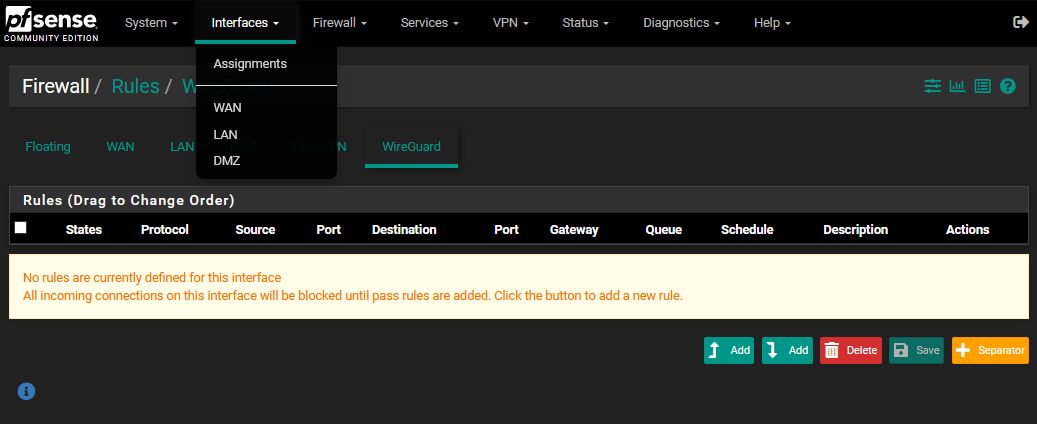
Here I am assigning the wg0 tunnel to OPT1
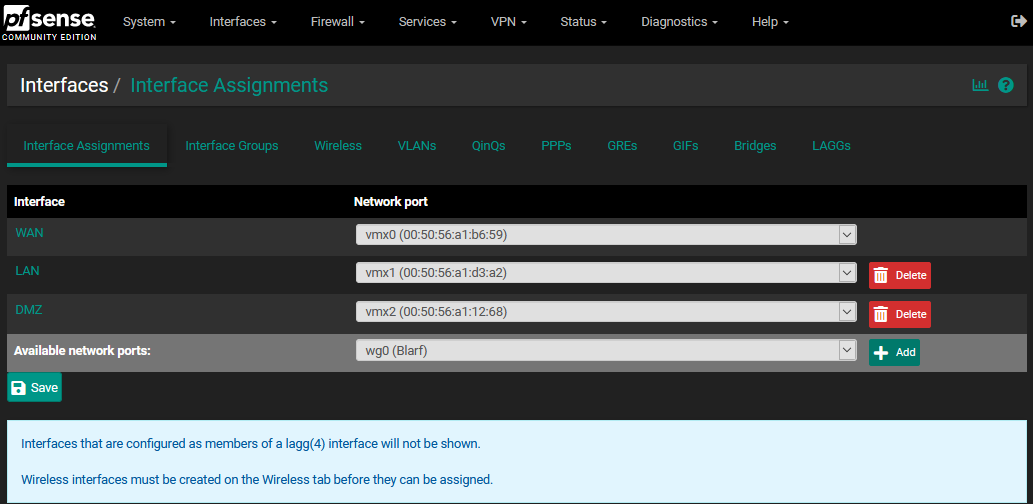
Here I have enabled the OPT1 interface and renamed it to WIREGUARD
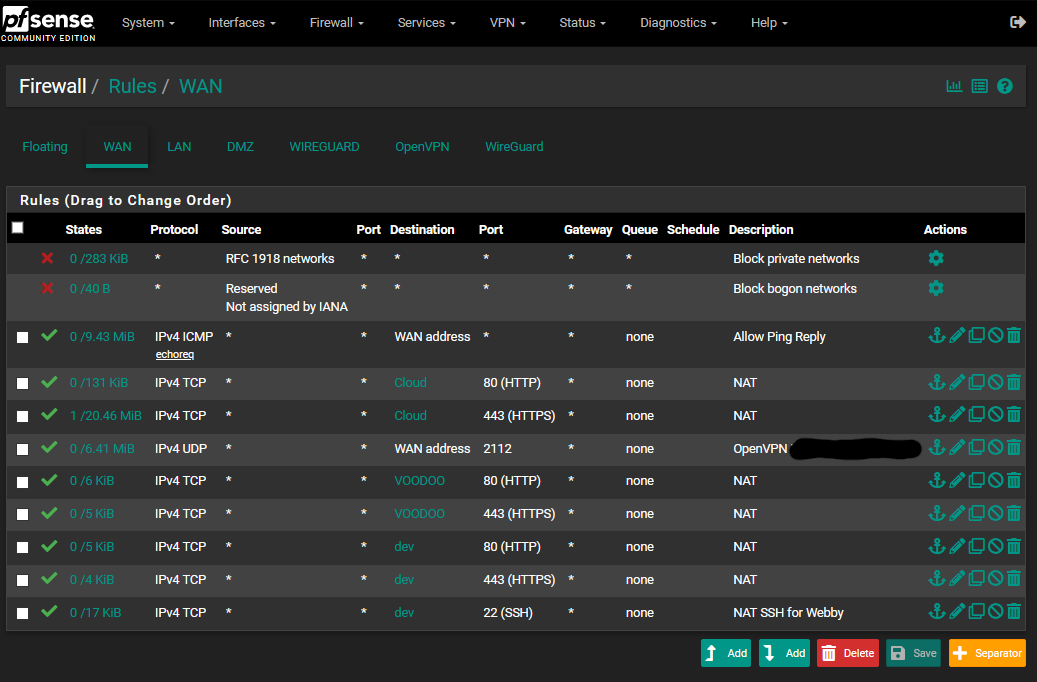
I now have two Wireguard tabs under Rules
-
@kom said in Wireguard and interfaces:
I now have two Wireguard tabs under Rules
One is for WireGuard, generally. Like the OpenVPN and IPSec tabs.
The other is for the interface you created. To avoid confusion, I'd call the interface something else. Like roadwg. -
@dotdash Strange that I haven't seen these dual-tabs in any of the guides or videos I've seen. Oh well, whatever. It doesn't matter now since I couldn't get the Wireguard site to site link working and we already have a good OpenVPN config.
-
@kom said in Wireguard and interfaces:
I end up with two WireGuard tabs in Rules.
Is this normal?Yes this would be expected. See this post: https://forum.netgate.com/topic/161601/purpose-of-wireguard-tab-and-wg0
This might help you in setting up the road warrior tunnel: https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-ra.html text
-
I never assigned an interface for OpenVPN
What if you don't assign one for Wireguard? What will you miss out ?
Thx
-
@chudak generally if you’re running a routed site to site tunnel, you’d want to assign interfaces on both ends so you can do gateway monitoring across the tunnel, policy based routing, etc. if you’re setting up WireGuard for remote access, it really doesn’t make much sense to define an interface.
-
@rcmcdonald91
Thank you !
-
@chudak I think I read somewhere here that the default Wireguard tab allows you to define rules that are global across all defined wg tunnels, where the interfaces allow you to define rules for just that specific tunnel that's linked to the interface.
-
I finally got it working. I wanted a road warrior config between my home pfSense and work. It took me awhile to realize that, while you don't need to define an interface on the work (server) side, you do on the home (client) side plus the usual firewall rule and outbound NAT rule to direct the traffic out the wireguard interface.