Deny opt1/wifi to LAN
-
Hello community,
I'm a new pfSense user so most probably I'm missing some basic knowledge. I recently migrated from endian firewall to pfSense and so far is working perfect.Now I'm "playing" with firewall rules and what I have to do is deny OPT1 (that I use as WiFi network) to LAN, to do that I use the followind rule on OPT1/WIFI interface:
Action: Reject
Interface: WIFI
Protocol: Any
Source: 192.168.2.0/24 (the whole WIFI Network)
Destination: 192.168.10.0/24 (the whole LAN Network)That works perfect. Now I have to enable WIFI interface to internet, and here is the problem:
This is the rule I created after the above one:
Action: Pass
Interface: WIFI
Protocol: Any
Source: WIFI Net
Destination: WAN NetThis rules doesn't work and I haven't internet connection on WIFI interface. To make it works I have to chenge as:
Destination: AnyWIFI to LAN is still blocked but I don't like rules with "ANY", I would like to configure a specific rule but I don't understand which interface I have to use instead of "ANY".
Could someone advice me?
Thank you
Lucas -
@lucas-rey said in Deny opt1/wifi to LAN:
Destination: WAN Net
Firewall rules are read top down, put your block 1st then pass after.
Destination: WAN Net ??
Destination: any
-
Added to that :
The source of the two rules should / could be identical.
edit : no related to your question, just what you showed.
-
@lucas-rey said in Deny opt1/wifi to LAN:
I don't like rules with "ANY", I
Well then you would have to create an alias that contains every IP on the public internet you would like to allow :) Shouldn't take too long to compile that ;)
Or since that is pretty freaking close to any ;) You could use that...
Wan Net is just that - the network attached to your wan.. It sure doesn't include say 8.8.8.8 or the IP address for amazon.com, or netgate.com, etc. etc..
-
Here's what I do:-
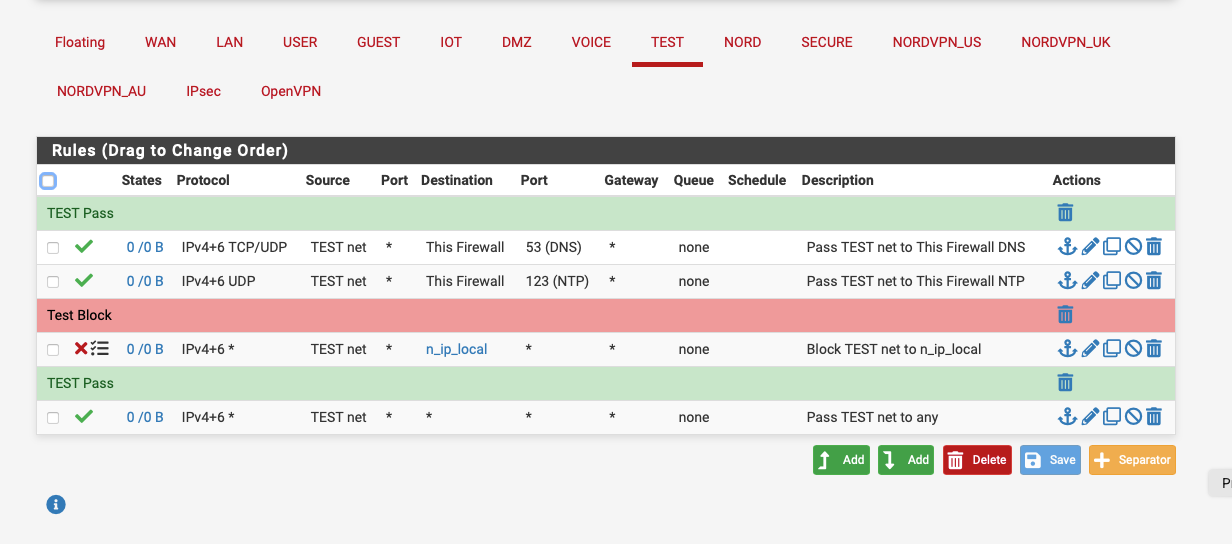
n_ip_local contains all my local subnets, and I have internet access only from this subnet.
-
@nogbadthebad said in Deny opt1/wifi to LAN:
n_ip_local contains all my local subnets
You could be specific - or you could for say just create a rfc1918 alias.. Since it would be assumed that your other vlan/networks would be using rfc1918 space. So if you want an alias that blocks all access to any local network/vlan you might have now, or in the future you could just create a alias that includes all the rfc1918 space
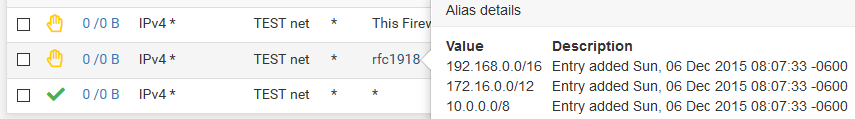
When wanting to block stuff - the this firewall is a good built in alias to use, because it would also include your wan IP.. Which is normally if your blocking a vlan from going to your local stuff - you prob want to block it from access pfsense gui via the wan IP..
-
Thank you all for replies, I'm getting confused with WAN Net because in Endian Firewall there was an interface called RED and it's used for internet access. Now I undestand how the WAN Net interface works on pfSense.
So I just added the blocking rule as 1st one (and yes I can use WIFI Net instead of network address), and then allow WIFI to connect using the "any" as destination.@johnpoz Do you have the whole ip list to share?

However, do I need to allow also WIFI to WIFI to make WiFi devices communicates each other? Or it's already implemented as default?
-
@lucas-rey said in Deny opt1/wifi to LAN:
do I need to allow also WIFI to WIFI to make WiFi devices communicates each other? Or it's already implemented as default?
Its implemented in the sense that devices on the same network don't talk to pfsense to talk to each other.. The "router" or gateway, to get off a network is not used to talk to another device on the same network - only to talk to some IP on a different network.
Pfsense has zero to do with devices talking to each other on the same network.. You could turn pfsense off and they could still talk to each other.
-
@johnpoz Thank you, also there, again, I'm geting confused by Endian Firewall logic, it implements a so called Zone Firewall where I had to allow communication between zone/interface.
However, pfSense is much better then Endian Firewall in terms of performance, so I can now take advantage of my new 1Gbit connection! :)
-
Pfsense is not a zone firewall.. But yes in a zone type firewall you would allow traffic from stay trusted to untrusted, or internet or whatever other zones you might of setup.
-
It sounds like you're setting up a guest WiFi. Here are my rules for mine:
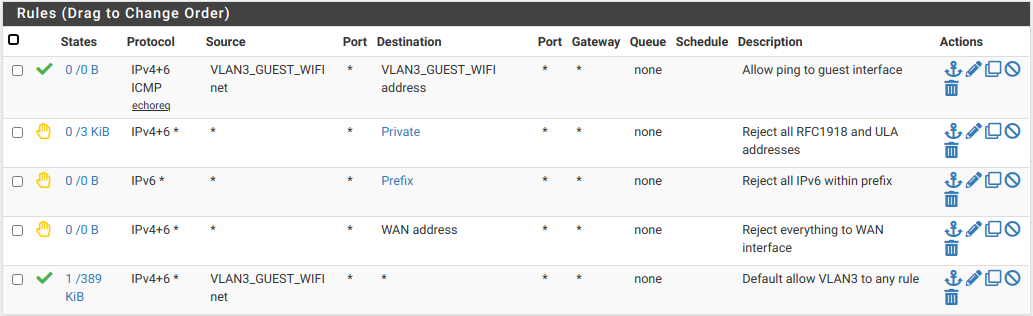
Private and prefix are aliases.