Impossible Network Traffic?
-
Hi all,
I have an interface on VLAN40 of my network as a guest network (40_GUEST), with a static IPv4 configuration of 10.40.0.1/24. The DHCP server serves up IPs in this range from 10.40.0.100-10.40.0.254.
There are no active DHCP leases, and there are 5x assigned static mappings (10.40.0.2-10.40.0.6).I noticed in my firewall logs some strange traffic on this interface, with a source IP address that cannot exist on that interface given the above. Destination is some public IP somewhere:
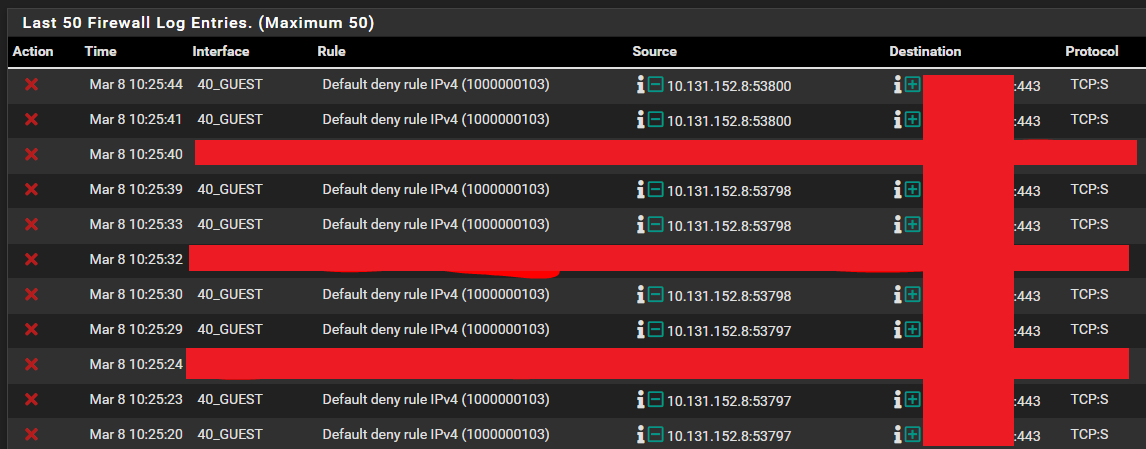
Any ideas what could be happening here? How can 10.131.152.8 exist?
Thanks in advance for any advice or suggestions!

-
@theskelly Anyone can set any IP address they want and direct traffic to the pfSense MAC address sourced from that address. That will show up exactly like that in the firewall logs (they are logging that the rules are doing their job).
I would run a packet capture on that interface to gather the MAC address that is sending the traffic then get into your switching infrastructure to see what port that MAC address is on, and follow the cable to the source. You might also just be able to do an OUI Lookup and the MAC address might tell you what device it is.
Diagnostics > Packet Capture
https://docs.netgate.com/pfsense/en/latest/diagnostics/packetcapture/index.html
-
@derelict Thank you!
The entries seem to appear in bursts randomly throughout the day... - so next time I see it happening I'll try the packet capture method and see what I can find

-
If available, enable and configure DHCP snooping. Don't forget to enable the static entries to bypass (generally prefer to trust a MAC over a port, in case something else ends up on the port). This combined with ip arp inspection can significantly reduce noise and coerce clients to operate correctly. If that network exists anywhere in your environment, you might have something acting as a logical bridge between VLANs.
You might opt to end the rule set for the interface as (especially for 'untrusted' segments):
pass from <interface network> to <appropriate destination/s>
block log from any to anyMay seem a bit strict but ensures that only accepted sources transit the firewall's interface, inbound. Making sure that any earlier rules don't allow bypass.