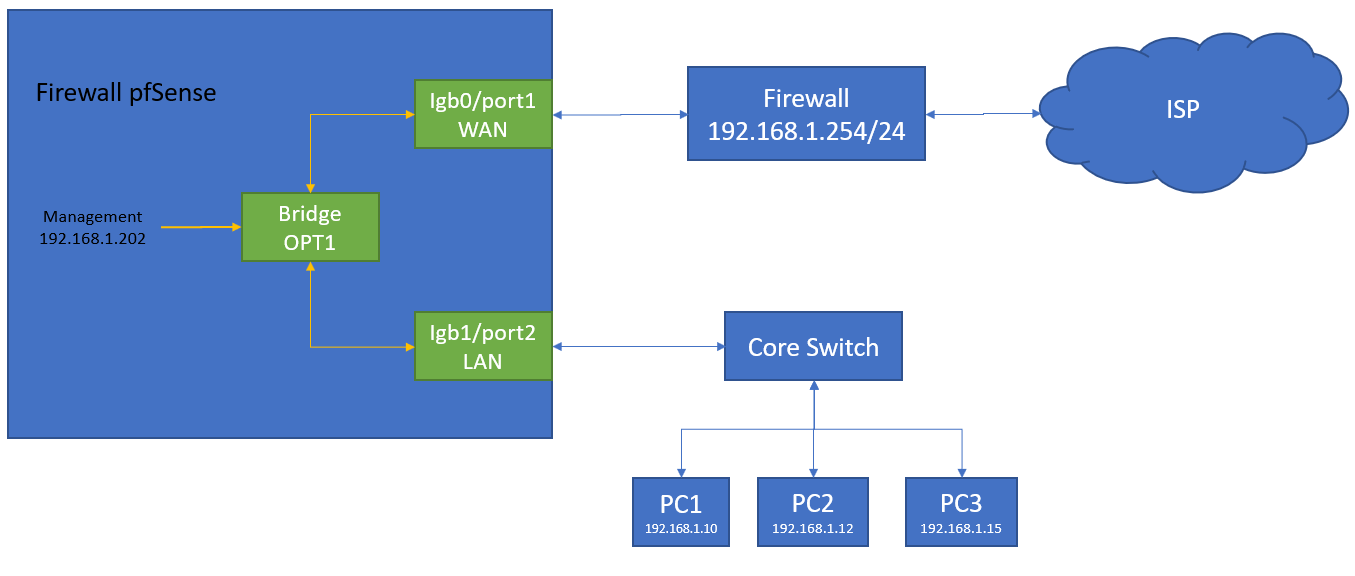
I am trying to configure pfsense inline mode (not route) with pfBlocker
-
@mind12 Thank you very much for your contribution, I had not reviewed my post, I was attending other projects, the device is physical, at the moment I have it working only with the IP blocking and with Suricata for traffic analysis.
I will try to do this test that you mention to me but the question is the following, the computers already receive DHCP through the main firewall, I understand that I must configure the administration IP (192.168.1.202/24) as part of the DNS servers that pfSense has?
-
@ocerna
For pfblocker (I assume) IP and suricata blocking all your LAN traffic need to flow through the pfsense firewall, have you cabled it that way?
For pfblocker DNSBL your clients need the pfsense IP as the primary DNS server.
Please dont forget to configure DNS resolver to listen on your bridged interface.First I would test with a client by assigning the pfsense IP as a primary DNS server manually.
-
-
@ocerna Arent you looking for a proxy instead?? Squid?
-
Looks ok to me. Seems a little overkill for such a small network.
I would use only the pfsense as the firewall with all the functions implemented. -
@mind12
I think I did not express myself well.The diagram shown is just a small example, this will be used in a network with more than 10 computers.
@Cool_Corona
And as you can see, what we are trying to implement is a transparent Bridge, which is intercepting malicious traffic with Suricata and blocking IP (IP Block) and domains (DNSBL) from pfBlocker. -
It is still an overkill to me. Why do you insist on the other firewall?
You would get much easier less administrative burden with one firewall. -
@mind12 Hello.
Well, perform the tests according to your recommendations and these were the following steps:
1- Assign a static IP to one of the network equipment and as the first DNS server 192.168.1.202 which is the management IP of the pfSense, as secondary configure the network gateway 192.168.1.254, the equipment manages to have internet but DNSBL fails to block malicious DNS.
2- Assign a static IP to one of the computers on the network and as the first DNS server 192.168.1.202, without configuring a secondary DNS, with this configuration it is not possible to have Internet browsing.
Something that I have noticed since I have tried to make DNSBL work in bridge mode is that being configured in BRIDGE, there is no communication with the virtual IP that is configured in DNSBL in my case it is 10.10.10.1, pfSense from your console if it manages to block The bad DNS and it also has communication with the virtual IP, I think that if we manage to make the bridge network computers communicate with this virtual IP, the DNS blocking would be effective again.
-
@ocerna Hi,
10.10.10.1 is for the DNSBL blocking site, if your clients can't reach that the page wont load but the DNS resoulution of the tested site should point to that address.
On windows you can test it with cmd and the command
nslookup www.example.com BridgeIP
If the answer is timing out the DNS resolver is not listening on your bridge interface or one of your firewall rule is blocking access to it. If you test a malicious domain the answer should be 10.10.10.1.Based on your topology diagram your clients are in the same network as your PF bridge IP so I would assign an unused IP from the same subnet to DNSBL.
However pfBlocker won't let you change it unless you comment out this section (must do it after every pfBlocker update):(I don't know why @BBcan177 implemented it this way, I guess to protect people creating IP conflict.)
Here: /usr/local/www/pfblockerng/pfblockerng_dnsbl.php
This section: $ip_validate
The other option is adding a route to your 2nd firewall to the DNSBL IP but that would cause assymetric routing (PF would answer directly to your clients but the packet came from the 2nd firewall). This also proves that using one firewall would be easier. -
@mind12 Hello,
I have reviewed each of the recommended steps:
1- DNS resolver is listening for all interfaces, if I configure that it only listens for the Bridge interfaces, it presents us with the same result.2- Modify the validation code for the virtual IP, add an IP of the example segment 192.168.1.203 and the same result still does not block domains, for verification use nslookup and it continues to show the original IP of the domain which was used as test, in few words is not blocking.
3- Well my opinion about this is that apparently there is a link between the DHCP service and the DNSBL to work with it, but as I said this is only my opinion.
Previously I was looking for more information and I was with that unknown that if I wanted to make a bridge interface with DNS blocking, I would have to configure one of the interfaces that comprise the Bridge for this case the LAN will activate the DHCP service.