Client device running OpenVPN not connecting to LAN
-
Hi all,
I'm having an issue with access to local LAN resources for an OpenVPN connected device. I don't think this is a 'typical' problem so I'm struggling to find anything online which helps (or perhaps I'm not using the right keywords!).
The situation: I have a device on my network which is connecting to an external OpenVPN server. The VPN connection is successful, and I am able to access REMOTE LAN resources/internet with no issues. However, when the VPN is connected, I lose access to any LOCAL LAN devices.
Example:
OpenVPN Client turned OFF:
10.20.0.2 (VLAN20) can connect to 10.30.0.2 (VLAN30).
OpenVPN Client turned ON:
10.20.0.2 (VLAN20) cannot connect to 10.30.0.2 (VLAN30).Interestingly, when the client is turned ON, 10.20.0.2 can still access things on the LAN for which a state exists - however killing the state and attempting to re-establish is unsuccessful.
Here are my firewall rules for VLAN20:
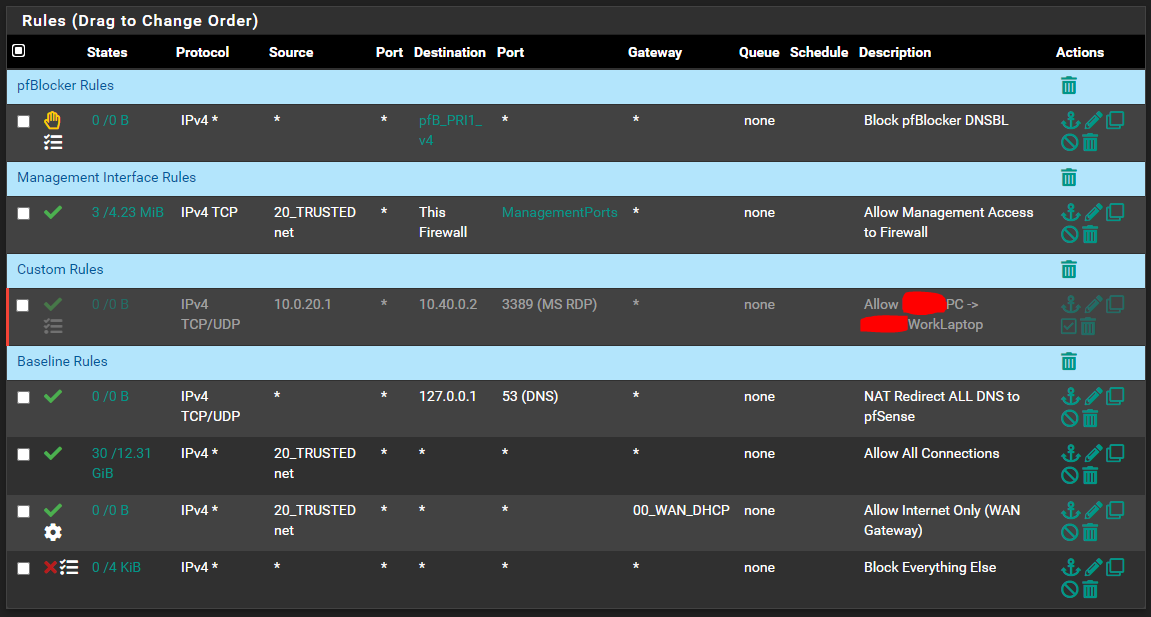
Even with the logged blocked rule at the end, no blocked entries appear in the firewall... so I'm quite confused as to what may be going on here!

Thank you for taking the time to read this/offer any suggestions

Additional Information:
VLAN20 (OpenVPN Client Device 10.20.0.2) serves on 10.20.0.1/24 -
@theskelly
Check the clients routing table. I guess, the VPN server pushes routes which overlap your LAN. So that traffic destined to internal IP are directed to the VPN server.
Which remote networks does the client need to access? -
@viragomann I like your thinking, however there shouldn't be any overlap... The remote network is a 192.168.0.1/24 network, and my local network connecting to the VPN is 10.20.0.1/24.
The VPN assigns addresses on 10.8.0.0/24 which does not overlap with any network segments on either side of the VPN connection...
-
@theskelly
It doesn't depend on the true remote networks, but on the routes which are added to the client when the connection is established. Therefor I requested you to check the routing table. -
Ah, my apologies for the misunderstanding.
The vpn server config contains the following:
server 10.8.0.0 255.255.255.0 push "route 192.168.0.0 255.255.255.0" push "redirect-gateway def1 bypass-dhcp"My understanding of this is that the first line specifies the IP range in which the VPN Server dishes out IP's to clients.
The second line allows the clients to route to the specified network on the server side.
The third line forces traffic through the VPN tunnel (by redirecting the default gateway).is another 'push route' required to specify local access?
Here is the routing table for my connected windows machine:
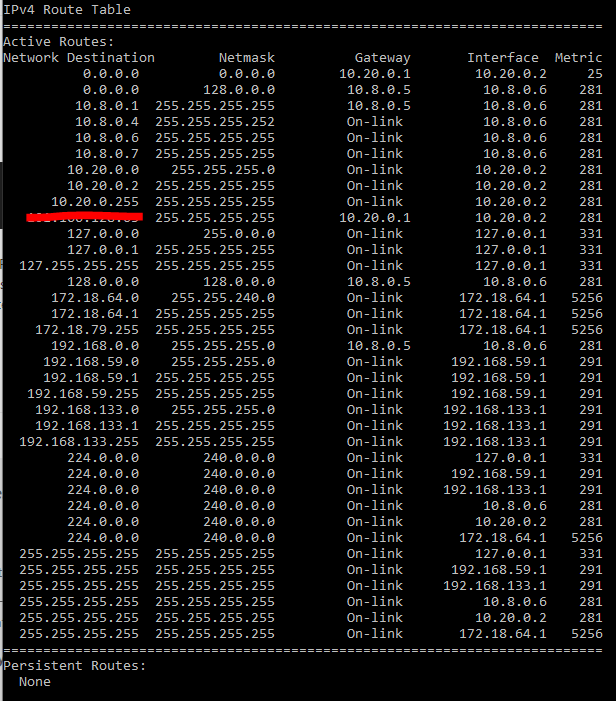
-
@theskelly said in Client device running OpenVPN not connecting to LAN:
My understanding of this is that the first line specifies the IP range in which the VPN Server dishes out IP's to clients.
Correct.
@theskelly said in Client device running OpenVPN not connecting to LAN:
The second line allows the clients to route to the specified network on the server side.
The third line forces traffic through the VPN tunnel (by redirecting the default gateway).Both lines instruct the clients to add a route after the connection is established. The first one pushes the route for 192.168.0.0/24, the second pushes the default route to the clients.
So the second line might be responsible for your routing problem. It directs the whole traffic from the client over the VPN. So yeah, this of course is overlapping your local networks and the client may send packets to the VPN server instead of the local router. -
@viragomann thank you! You're on the money with that one. Disabling the redirect of the default gateway allows me to retain connectivity to the client LAN.
However the drawback of this is that now, internet-bound traffic does not tunnel through the VPN. I assume the happy medium here is to re-enable the gateway redirect and also add in a route to allow traffic to find its way to the client LAN. Would another 'push route' be used to achieve this? (I've seen a few things about 'iroute' online which is just confusing me!
 )
) -
@theskelly
No iroute is for routing traffic to a specific client in OpenVPN.If you need to direct the internet traffic over the vpn you have to set the default route, which prevents you from accessing other network segments, as you experienced already.
That's why you should set up a vpn for internet access on the router instead. If you still want to run it on the client device, you can play around with routing metrics and static routes.Try the following:
Add the redirect gateway line to the server settings again and also add the linepush "route-metric 512"Restart the server and try again with these settings.
If it doesn't work add a static route for the local networks to the client. How to do that depends on your OS.
-
@viragomann thanks for the guidance! Unfortunately the metric 512 line didn't work. I'm not so keen on configuring routes for each client - so perhaps I'll make pfsense the client instead.
Thank you again!

-
@theskelly said in Client device running OpenVPN not connecting to LAN:
so perhaps I'll make pfsense the client instead.
Ttat's a very good decission.
