IPv6 Firewall Rules
-
Hi All,
Hopefully a simple one. Just getting my setup fully IPv6 enabled, now that I finally have my head around it + subnetting etc.
So I have around 40x VLANS on pfSense.
For each interface, I used to do the following
RULE 1 - Allow X Traffic to other VLANS where required
RULE 2 - BLOCK ALL Traffic to Private IPv4 Address Range
RULE 3 - Allow ANY Outbound (Limited to certain ports if required)This works perfectly. Simple, secure, and stopped VLANS being able to talk to other VLANS unless required.
With IPv6 though, how can I achieve the same result? As there is no longer a Private IPv6 Range / Subnet, as they are all publicly routable IPv6 Addresses.
Thanks, Scott
-
@smaxwell2 said in IPv6 Firewall Rules:
So I have around 40x VLANS on pfSense.
For each interface, I used to do the following
RULE 1 - Allow X Traffic to other VLANS where required
RULE 2 - BLOCK ALL Traffic to Private IPv4 Address Range
RULE 3 - Allow ANY Outbound (Limited to certain ports if required)
This works perfectly. Simple, secure, and stopped VLANS being able to talk to other VLANS unless required.
With IPv6 though, how can I achieve the same result? As there is no longer a Private IPv6 Range / Subnet, as they are all publicly routable IPv6 Addresses.
Thanks, ScottCreate aliases with all your subnets and block on each interface, add an allow for services the firewall provides and put it above the block rule.
Then add a pass any any at the bottom.
If you have the 40 vlan interfaces on pfSense maybe use floating rules.
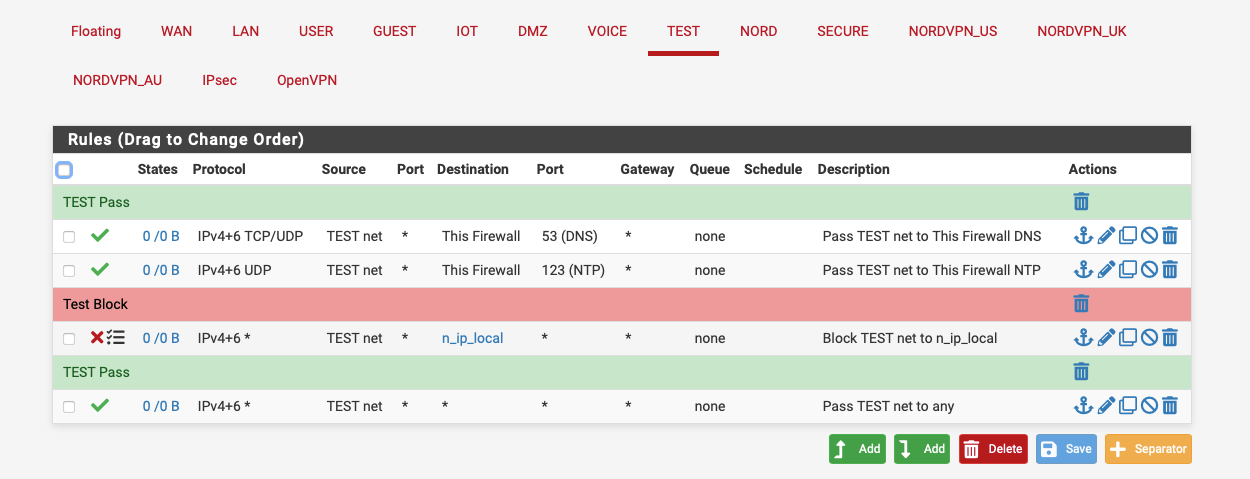
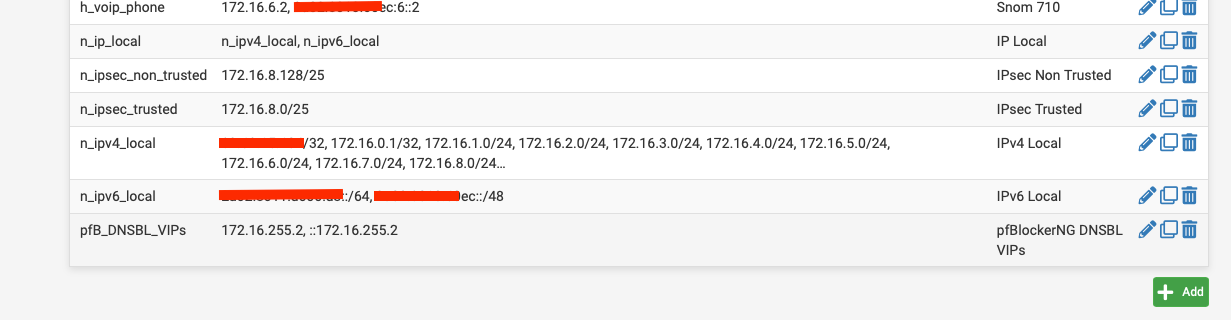
The /48 is the full allocation from my ISP.
-
@nogbadthebad This makes perfect sense !
Great :) Thanks very much - knew I was thinking about this the wrong way.
I'll just create 1 x Alias with my /48 (which will include all my /60s and /64s)
Then do exactly as you said :)
Thanks again
-
@smaxwell2 said in IPv6 Firewall Rules:
So I have around 40x VLANS on pfSense.
40???? Why so many? Are you trying to do something that might be better done another way?