Phone not accessing the internet after rule to avoid the router VPN
-
Is this standard on cablemodems to use VLAN 1 for their management interface when in bridge mode?
On my Telus modem, I can set bridge mode on port 1 and the remaining three LAN ports are normal. I just connect one of those to my managed switch on an untagged port separate VLAN to access.
Previous Shaw modems I had when I enabled Bridge mode I think I had to access the default subnet somehow during bootup, reset the modem using pin, or contact Shaw to take it out.
-
@dma_pf Now that the problem with the connection going down is solved, I have come back to this. I have managed to put the ISProuter in bridge mode and now the pfSense router is connecting to the ISP directly.
It is expected, but I feel the connection is more snapy, there is less lag between asking for a webpage and it opening. Not having a second NAT from a underpower router will do that I guess.
Also, you were completely right and now the phone is connecting fine, the firewall rule to have the static IP of my phone routed through the WAN instead of the VPN_WAN is working. It was indeed the double NAT that was giving trouble as you suggested.
Now that the ISP Router firewall is down I am getting a lot of activity blocked by the pfSense firewall in the WAN interface, but that was to be expected too. Most of it from China from what I have sampled, also to be expected.
In case there is another "noobie" that it is reading, what I had to do after I had set up the ISPRouter in bridge mode is in pfSense go to Status->Interfaces, then in WAN release the DHCP lease (this is the one that I had with the ISPRouter, usually address 192.168.X.X) and then adquire the lease again (now with the ISP directly, the IP is completely different, not 192.X.X.X). This worked, but pfSense was confused about the routing, it was giving me error 65, which websearching told me it was lack of routing. So I went to System -> Routing, I changed the "Default gateway IPv4" from Automatic to WAN_DHCP, Save and Apply. Apparently that made pfSense get a sense of the routing again and everything was working fine. I switched it back to automatic, save and apply, and everything was working well still. So apparently pfSense needed a trigger to reshape the routing or something.
Now, the only issue is that I can still not access the ISPRouter from behind the pfSense Router. It is not the biggest deal, since I do not need to touch it anymore and I can access it by connecting a ethernet cable to it directly from the laptop, but I would like to have access from the pfSense LAN network. I think I followed @dma_pf advice but still not connecting. Here is the relevant configuration (feel free to ask for anything):
I created the VLAN interface and gave it a static address in the range of the ISPRouter address:

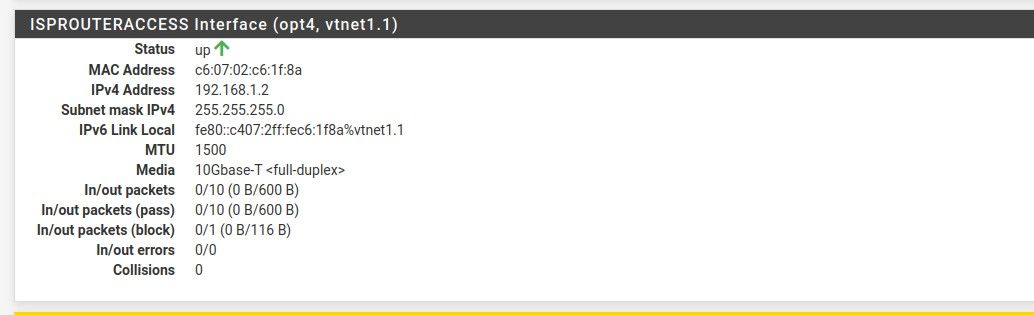
Then I created the rule in the NAT:

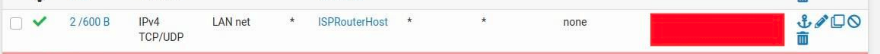
The problem with this is that the firewall was blocking access to 192.168.1.1 (as it should by the rules I had), so I created a new rule to allow access (the last rule before the default reject rules):

With all of this the connection is still not going through. It times out. For the record, the IP of the ISP Router is included in the Local_Network alias, so the two previous rules that deny it do not affect it. More evidence to this is that when the last pass rule was not present, the traffic to the ISPRouterHost was being catch by the Default reject rule, so the other rules were not being triggered (as expected). Plus, I added the rule to the logs and it is getting triggered when trying to access the ISPRouter IP.
Do I need to create a gateway and set it up in the firewall rule or with the NAT rule should be enough? I have not been able to find anything relevant in the logs, what can I do to debug and see what is happening?
-
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
Do I need to create a gateway and set it up in the firewall rule or with the NAT rule should be enough? I have not been able to find anything relevant in the logs, what can I do to debug and see what is happening?
You don't have to set up a new gateway. But you do need to let the new ISPROUTERACCESS interface route out of pfsense to get to the router. Move this rule to the ISPROUTERACCESS tab in Firewall/Rules and change "LAN net" to "ANY" :
-
@dma_pf Still not working. This is what I did.
I moved the rule to ISPROUTERACCESS in the firewall and set destination to Any. The rule is logged. The problem here is that the origin is LAN and the Default reject rule of the LAN gets triggered, blocking the request from my LAN computer to the ISPRouter IP. The firewall rule at ISPROUTERACCESS never gets triggered.
I tried to duplicate the rule and have it both in LAN and ISPROUTERACCESS and still does not work. Only the rule in LAN gets triggered and the connection times out.
Maybe I misunderstood what you were suggesting.
-
@dicmo I looked over our discussion here, and also the configuration on the off-site pfsense where we have this working, more carefully. I do note that we have a rule set up in both the LAN and the router access interfaces.
The differences that I noted between our set up and yours are:
-
In the Routing/Gateways "Default Gateway IPv4" setting we have it set as WAN_DHCP and you have it as Automatic.
-
The LAN firewall rule on our pfsense looks like this:

-
The router access interface firewall rule looks like this:

In looking back at it more carefully, I'm not sure that the router access interface firewall rule is needed. I can't confirm that because have not tested without the rule and am not in a position to do so currently. But I do see that there isn't any traffic hitting the router access interface rule (0/0), whereas there is on the LAN rule (0/1.03).
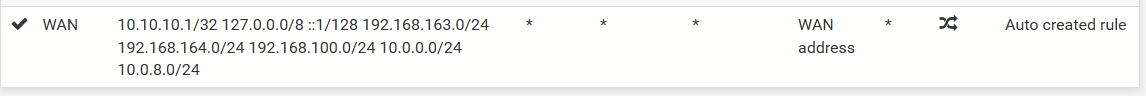
- I also noticed that in our NAT rules (which are in Hybrid Mode) there are 2 NAT rules that mention our modem's GUI network (192.168.100.0/24). The first one is a manual rule that looks like this:

The second one is automatic rule like this:
One last thought. Is the Web GUI on the router secured with a self-signed certificate? If so you may need to access it with https://192.168.0.1 if your browser does not automatically redirect to https in typing the IP address in the browser.
Good luck....I hope that helps!
-
-
@brians said in Phone not accessing the internet after rule to avoid the router VPN:
Is this standard on cablemodems to use VLAN 1 for their management interface when in bridge mode?
In my experience, when the router/modem is in bridge mode, this is the only way to access the GUI when you are trying to access the GUI from a network behind pfsense.
-
@dma_pf I tried all the same configuration you have and I can not connect. I even tried setting a gateway associated to the VLAN interface and route the traffic there. Rebooting. Nothing seems to work and I do not have the knowledge to really understand what is going on and fix it, so I think I will leave it, at least for now. I do not need to access the ISP router for anything now that it is in bridge mode and if I need to at some point I can access it by just connecting it to my laptop with an ethernet cable, so I do not think I will dedicate more time to this when I have a bunch of other stuff to set up. If anyone knows what is happening or has any suggestion, I will gladly try, but other than that, it is good how it is.
Once more, thanks a lot for the help, here and in the other post. I am not sure I would have succeeded setting everything up without your help and the help of this forum in general.
-
@dicmo I'm sorry we didn't get that last bit working. At this point I'm out of ideas but am fairly certain that this is not a pfsense issue. My gut sense says it's some setting in the router itself that is denying access to the GUI on the bridged port. But I'm glad you have a workaround if you need it. If you do figure it out some day please post the solution. I's love to know what it was.
I appreciate your thanks. It was a lot of fun getting you to where you are now. Seven years ago or so when I started using pfsense I really had no idea of networking. I've pretty much learned all of what I know through this forum. It's really a great community and I take pleasure in giving back to it when I can.