Tagged traffic on SG-2100 802.1q port
-
Hi
I just bought a Netgate SG-2100. I’ve set up 802.1q mode on the integrated switch.LAN port 2 is connected to an AP that sends tagged (VLAN ID 2) and non-tagged traffic.
I can't figure out why TCP dump on tagged interface shows nothing? Need Help TCP dump on non-tagged interface on the same physical port is OK.
AP is configured to correctly send traffic on VLAN ID 2.
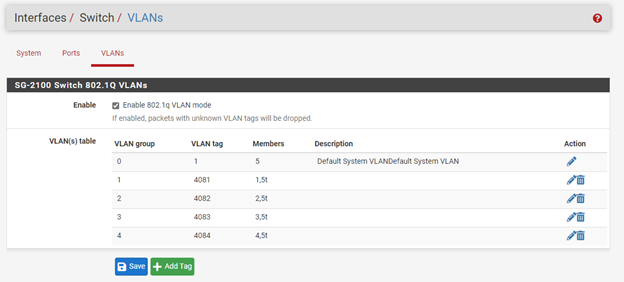
Integrated Switch configuration:
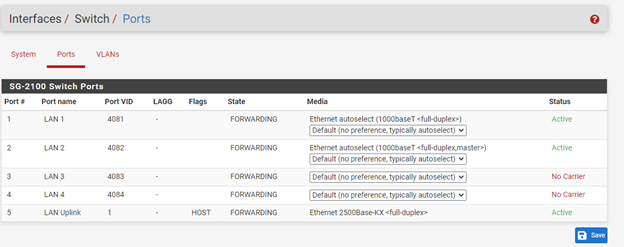
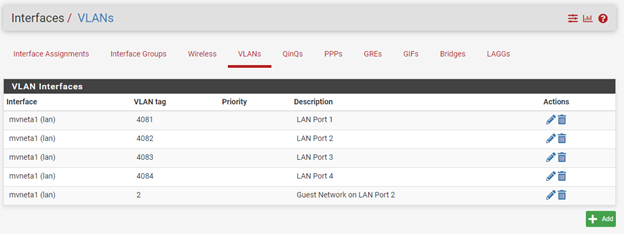
Interface VLAN configurations:
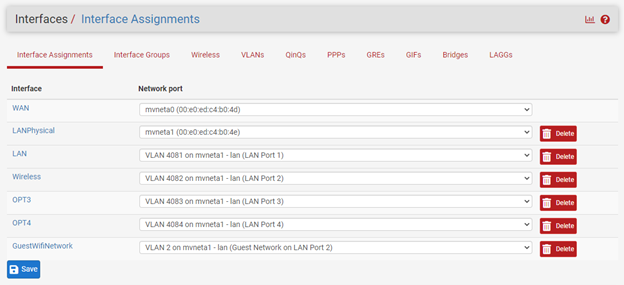
Interface configs:
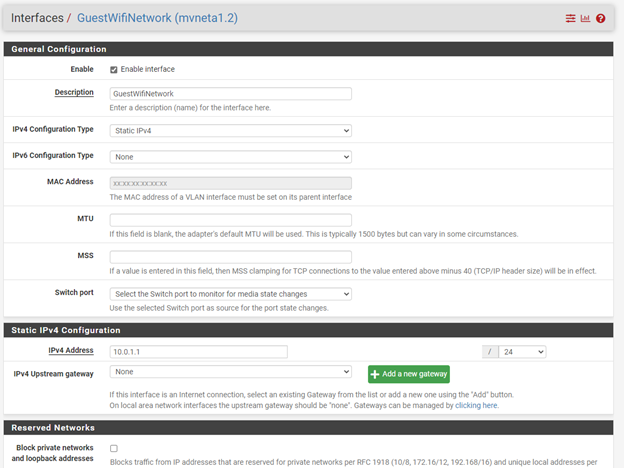
Firewall configs:
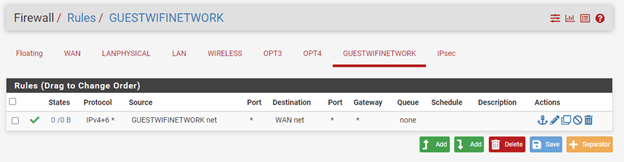
DHCP configs:
DNS configs:
Am I missing anything?
-
@smk You have not added VLAN tag 2 to the SG-2100 switch. It needs to be on ports 2 and 5 tagged (2t,5t). With that set, untagged traffic will be on VLAN 4082, Wireless on pfSense, and VLAN tag 2 traffic will be on GuestWifiNetwork.
-
Thanks @Derelict
Its gotten better, clients are getting DHCP assignments after making this change:
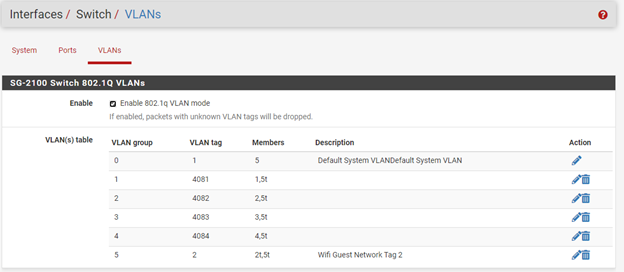
But clients are still not able to reach out to the internet. Am I missing anything else?
-
-
Hi @Derelict
Yes, the firewall rule is permissive:
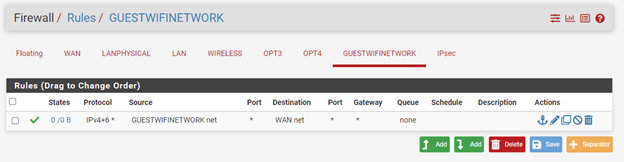
And Firewall NAT settings are auto:
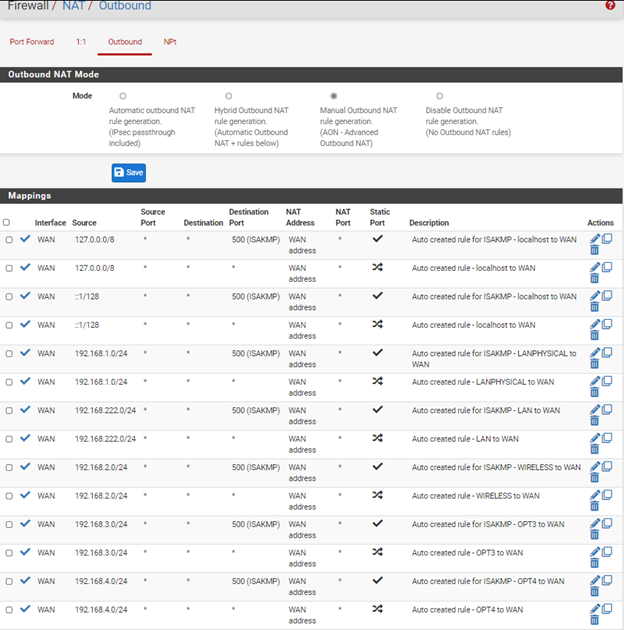
Is that right?
-
@smk WAN net is not the internet. any is the internet.
-
@smk And those are not automatic NAT rules. Those are manual NAT rules. They will reflect the configuration at the time you set manual NAT mode, not anything that has been added since.
10.0.1.0/24 is not listed as a source there so that is missing too.
-
-
@Derelict: Everything works with 1 exception: clients on the AP are not able to talk to one another.
Firewall allows traffic to the internet:

NAT rules are setup:
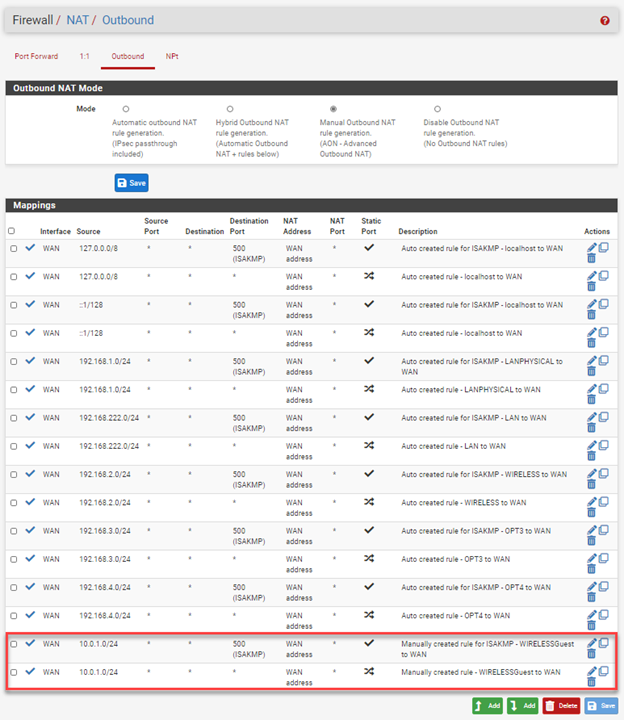
Am I missing anything that would allow clients on the 10.0.1/24 network to talk to one another?
-
@smk said in Tagged traffic on SG-2100 802.1q port:
clients on the AP are not able to talk to one another
That would normally not go through the router, but from one device to the other. Some APs have a "guest mode" or similar option to prevent wireless clients from talking to each other (only to the Internet).
-
Thank you @teamits
Guest mode was already disabled on the AP:
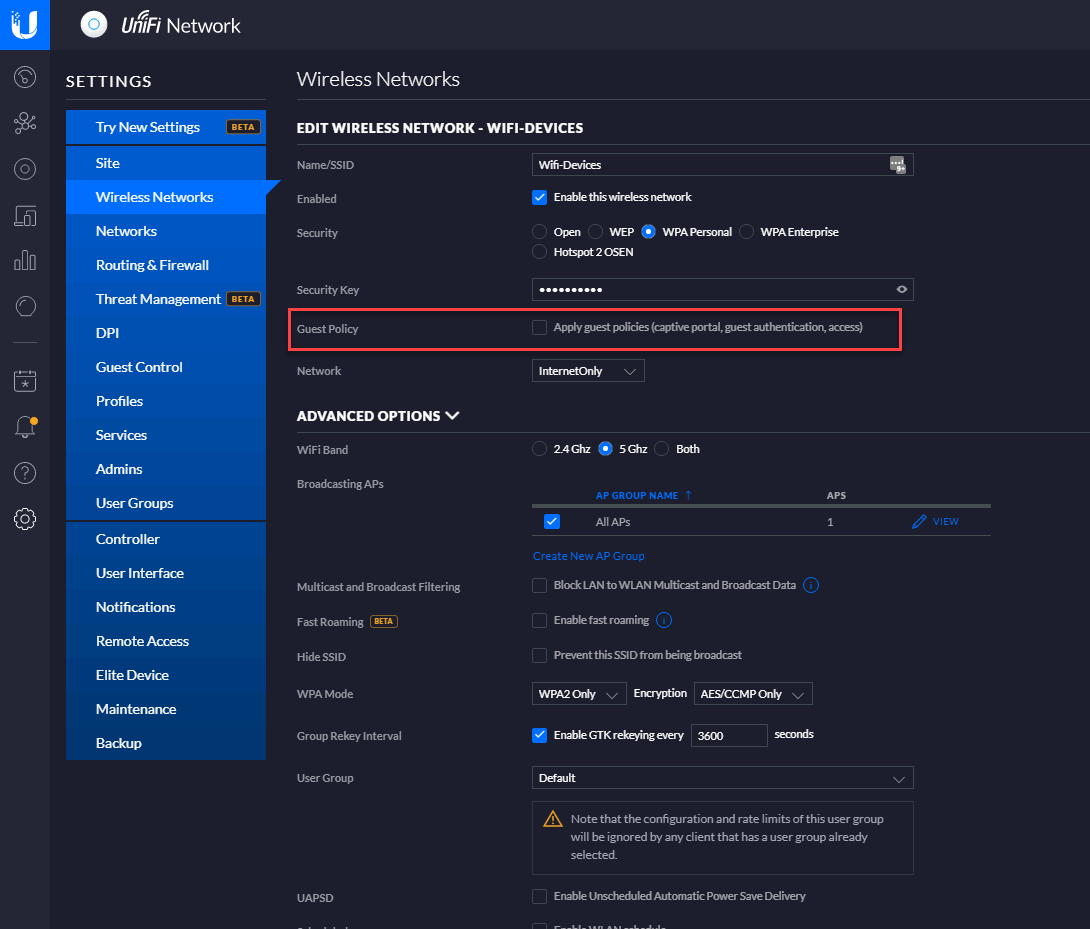
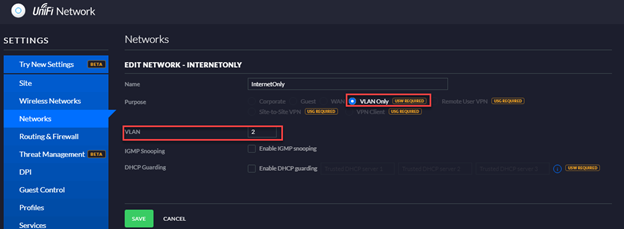
Am I missing any configuration that would prevent members to communicate with each other?
-
@smk I don't know what it looks like or where it is on Ubiquiti. This is what it looks like on Ruckus Unleashed:
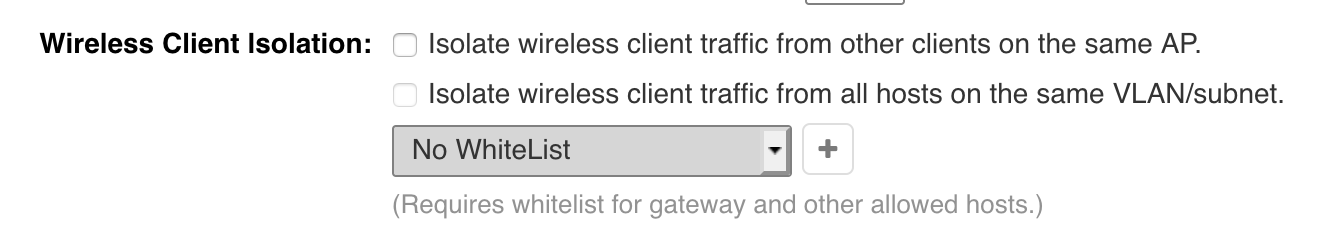
-
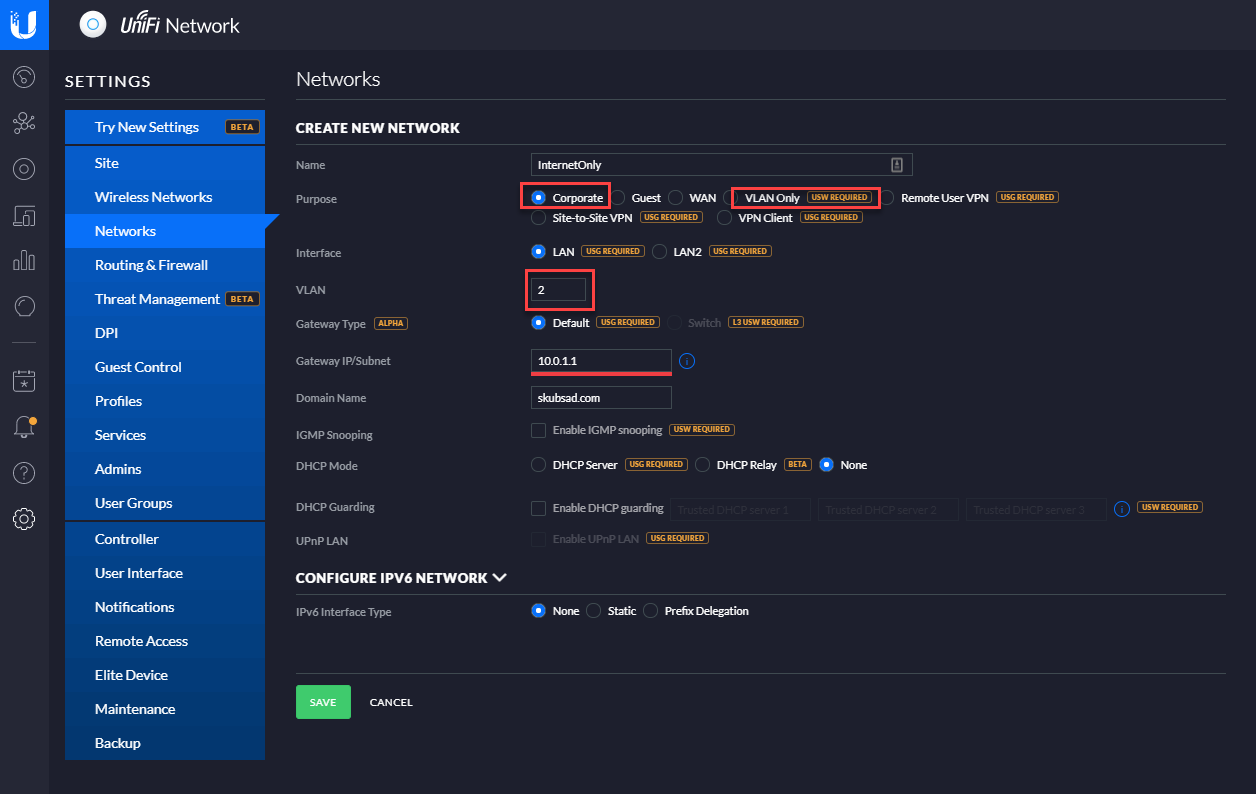
@Derelict & @teamits : you were both right. Sorry, my bad: it was bad Ubiquity configuration.
If anyone falls in the same trap, the solution is to set "Corporate" + "VLAN". Not "VLAN Only" + "VLAN":
Thank you both very much!