Sporadic dns issue related to DNSSEC
-
Hi.
I'm using the dns resolver and have found a site that won't resolve:
www.broadcom.comAfter some research and stumbling I finally found a temporary(?) solution in disabling DNSSEC which allows broadcom.com to resolve.
Is there any way for me to activate DNSSEC and still resolve broadcom.com, and does anyone else experience this problem?
-
@stoffix said in Sporadic dns issue related to DNSSEC:
www.broadcom.com
I am not having any issues resolving this with dnssec
$ dig www.broadcom.com ; <<>> DiG 9.16.12 <<>> www.broadcom.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19099 ;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.broadcom.com. IN A ;; ANSWER SECTION: www.broadcom.com. 3600 IN CNAME cdn.broadcom.com. cdn.broadcom.com. 3600 IN CNAME www.broadcom.com.cdn.cloudflare.net. www.broadcom.com.cdn.cloudflare.net. 3600 IN A 104.18.4.158 www.broadcom.com.cdn.cloudflare.net. 3600 IN A 104.18.5.158 ;; Query time: 219 msec ;; SERVER: 192.168.3.10#53(192.168.3.10) ;; WHEN: Sat Mar 27 09:15:22 Central Daylight Time 2021 ;; MSG SIZE rcvd: 144While I show some issues with that here
https://dnsviz.net/d/www.broadcom.com/dnssec/broadcom-dd.lldns.net/A: The server responded with no OPT record, rather than with RCODE FORMERR. (208.111.184.11, 208.111.184.12, 2607:f4e8:ac:1::11, 2607:f4e8:ac:1::12, UDP_-_EDNS0_4096_D_K) broadcom.com/DS (alg 8, id 61210): DNSSEC specification prohibits signing with DS records that use digest algorithm 1 (SHA-1). broadcom.com/DS (alg 8, id 61210): DNSSEC specification prohibits signing with DS records that use digest algorithm 1 (SHA-1). broadcom.com/DS (alg 8, id 61210): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset. broadcom.com/DS (alg 8, id 61210): DS records with digest type 1 (SHA-1) are ignored when DS records with digest type 2 (SHA-256) exist in the same RRset.It shows fine here
https://dnssec-debugger.verisignlabs.com/www.broadcom.com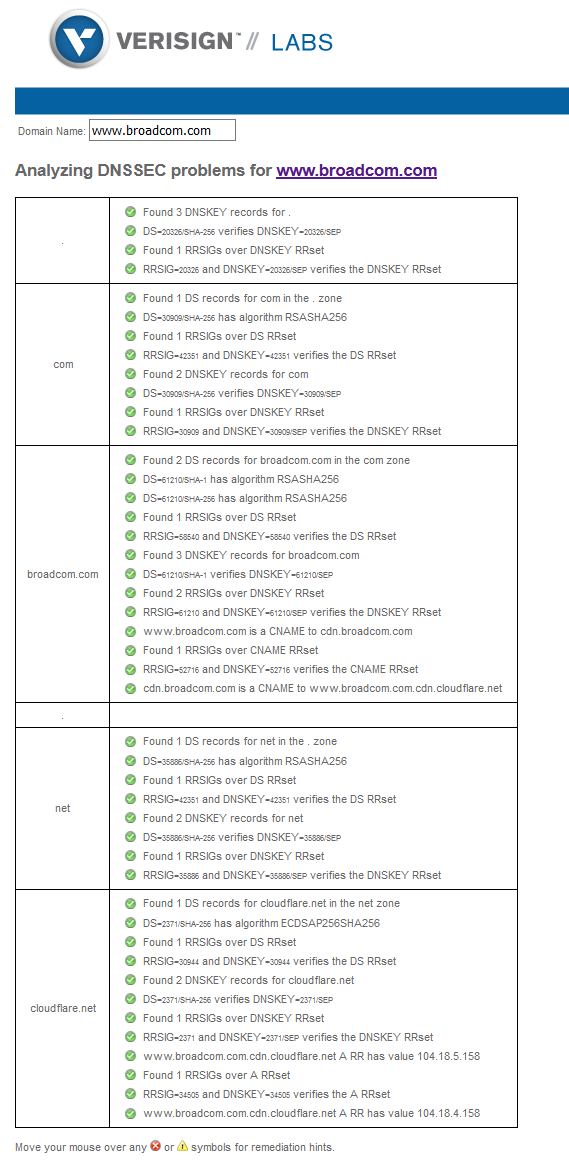
You are resolving right? And not forwarding to somewhere and trying to do dnssec?
If you have a domain that dnssec is failing - and you still want to get there you can set that domain as non secure..
in the unbound options set say
server: domain-insecure: "broadcom.com" -
@johnpoz
Yes, I'm resolving. Part of my stumbling was because I had set up dns servers in the general settings, and when pfsense couldn't resolve it would use one of those. It made me quite puzzled when broadcom.com wouldn't work on my clients, but a ping from pfsense worked.I have now removed all of the listed dns servers, and dns query forwarding is not enabled in the dns resolver settings. The result is that with DNSSEC enabled it behaves similar on pfsense and the clients (doesn't resolve.)
Your workaround does work though.
Here's my output from dig:
Without workaround:$ dig www.broadcom.com ; <<>> DiG 9.16.11 <<>> www.broadcom.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 688 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.broadcom.com. IN A ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Sat Mar 27 16:52:18 CET 2021 ;; MSG SIZE rcvd: 45With your workarond:
$ dig www.broadcom.com ; <<>> DiG 9.16.11 <<>> www.broadcom.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 57753 ;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.broadcom.com. IN A ;; ANSWER SECTION: www.broadcom.com. 286 IN CNAME cdn.broadcom.com. cdn.broadcom.com. 3586 IN CNAME www.broadcom.com.cdn.cloudflare.net. www.broadcom.com.cdn.cloudflare.net. 286 IN A 104.18.5.158 www.broadcom.com.cdn.cloudflare.net. 286 IN A 104.18.4.158 ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Sat Mar 27 16:54:45 CET 2021 ;; MSG SIZE rcvd: 144It's weird that it works for you, and not for me.
Could it somehow be my internet provider which causes this? -
Where exactly are you doing that query on?
;; SERVER: 127.0.0.1#53(127.0.0.1)Do a trace, lets see what could be different
[21.02-RELEASE][admin@sg4860.local.lan]/root: dig www.broadcom.com +trace ; <<>> DiG 9.16.11 <<>> www.broadcom.com +trace ;; global options: +cmd . 65086 IN NS d.root-servers.net. . 65086 IN NS e.root-servers.net. . 65086 IN NS f.root-servers.net. . 65086 IN NS g.root-servers.net. . 65086 IN NS h.root-servers.net. . 65086 IN NS i.root-servers.net. . 65086 IN NS j.root-servers.net. . 65086 IN NS k.root-servers.net. . 65086 IN NS l.root-servers.net. . 65086 IN NS m.root-servers.net. . 65086 IN NS a.root-servers.net. . 65086 IN NS b.root-servers.net. . 65086 IN NS c.root-servers.net. . 65086 IN RRSIG NS 8 0 518400 20210409050000 20210327040000 42351 . LwjAYGeasi3q7UYqLXslXrMJBKiMWWZW2ppD92Mc6pDutvKpj+ksGlW2 nCGUEskeX4GFAgRz7QqrWMWf3s3kLwbKhne4GjXKi3anemKvFB1v6R0e 3uYafVARr+o5duvIsHOjUDG+1yKAoPkPnrfquf40i/0oJut28cUE3qOI uDjJqeniwSN5maMRKjdYnO2cBUFpBisoQJ6wOcB8Fx4Tl0VN0mQpojT6 XsXnGbIdB59DRXKGO3G6xYjKnct9tz/SsolcObg6DoqBTCGgyockj0+M gPftkSR7/6cfS9fjOtRf3n2lOl86KAcTgrjvK5Fsj9PYlARUpR7+IZ74 JYvjVA== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766 com. 86400 IN RRSIG DS 8 1 86400 20210409050000 20210327040000 42351 . jIZPzD+VW2ARP9cEAuFEiKSclcucwl1gqH8wf3mPA0dIFncp0JsOLeho TfIFeJ11ae6BJqid+6dbpdY2grbJhhHKBOw9/LY4xe/17KeGjswB/nTi Cst2rLPPojsZV5RZShEFurwUSFcYOIrFd8I+B6GGx6I46NWDLvI8MEzi PJa8Ud4YG3lKVHJX+8AGKnhoiTbSVwk5AT6gcjYoYYw1hv0zPmz39r0N /Is4pTYF3wugbprigWn3Gg4VFnQSMcWtKVB89+gvFw1+4Uzj1/hT0YGt R7+H0Nxg4IDrxnrqu72wj6RCfhuXapinEXKx410OPo+6HY2hI0Io2WhR TxKhzQ== ;; Received 1176 bytes from 199.7.91.13#53(d.root-servers.net) in 29 ms broadcom.com. 172800 IN NS pdns1.cscdns.net. broadcom.com. 172800 IN NS pdns2.cscdns.net. broadcom.com. 86400 IN DS 61210 8 1 6F0A9DF17ED6E1F31F2F184A038AF07D2D7DDF97 broadcom.com. 86400 IN DS 61210 8 2 7A97793031AC4256DAEE3DCAC603519C4BE1283690CDA1636A5DC6CB 27F2F188 broadcom.com. 86400 IN RRSIG DS 8 2 86400 20210402044422 20210326033422 58540 com. PYny3W5dKW0diYul/Rv1lUv6s60MdPIan2Fa2+DWFqBtYmAseik7/aPH dhTJoAxU3I1JtTT5uNEwpcAYrhL3giFj2ajJ9XQN95uXjlYpMdbm7Yhq w6YSi6myqLAGnxJP+EUV8DTf9xEDUF8hN9PeFIJ8Qa26Hw4iZWMs93p0 dP8GP7PxpwHMG0sQviG3+LkPTrT6GJPHCXSyz2b94bwLeg== ;; Received 374 bytes from 2001:503:a83e::2:30#53(a.gtld-servers.net) in 30 ms www.broadcom.com. 300 IN CNAME cdn.broadcom.com. cdn.broadcom.com. 3600 IN CNAME www.broadcom.com.cdn.cloudflare.net. cdn.broadcom.com. 3600 IN RRSIG CNAME 8 3 3600 20210330234650 20210326232722 52716 broadcom.com. R2YL5JokRpaA7sm6Jzxg59usNC78QAN6TA/+NkqTuzmmwUlXJKsRMDsJ Dy5meHUkFOrN0E2JuJlwTaM/PLLey47/mmWlrBOpED25OiDLzOfMXjcz MxrHxYM0abw2XQRHqaJX1lIeu+j0DpPfEtsHCpUCITTOj+hxuvQXYJlB 3WZa0PWoZsdELGD4wB+d67EheNrjmItWVVyQUr11eWwj9mKoZkocjmx3 SHmXHQmA1fmclTUTE3z5LIH6zoSK44kRfxp+KxXZB4w6lG9aQyPKgYNv H85H/1a7+Jh8pLK0XRAmHEKypzoveJbcEBWjxyDptMuIkP0wzVoDtxrz +z6lSg== www.broadcom.com. 300 IN RRSIG CNAME 8 3 300 20210331011713 20210327001855 52716 broadcom.com. i5kxCoQX6qrGJdL9wBaShvIMNSVHIWu8Cj3QCd9JVuDn8vFFLNazSxA4 1pDRaTNrRjZkLNVN0zN1xwHDJB3dVuc3wh+wc75JCp8oNLvPyyMFGXiB V8/3HJ7VPd6gxPKy3gjDlFv6A0+tLLJ3NgL8L3iN89p7T01WT/mmHj+y r04e3e60PlORB+6TJcEbPbIw6I3IY5e/j4s274PxIC6vmV6l+aS1bCfn 8dSBi2pywIEGpO4Ym+XoB7rXK3LQ5o+EgnBr3yDhxUmiUX0/DnoC8/xR IjwlhD/GCCndnN+qTj3SUZtTfdYp33i0xSfEH4SMXTrEVimgiApak4Jb OF9cGw== ;; Received 716 bytes from 2610:a1:1023::100#53(pdns2.cscdns.net) in 37 ms [21.02-RELEASE][admin@sg4860.local.lan]/root: -
I'm doing the query on the pfsense router where I have this issue.
[2.5.0-RELEASE][root@slottet.doff1]/root: dig www.broadcom.com +trace ; <<>> DiG 9.16.11 <<>> www.broadcom.com +trace ;; global options: +cmd . 86370 IN NS a.root-servers.net. . 86370 IN NS i.root-servers.net. . 86370 IN NS c.root-servers.net. . 86370 IN NS j.root-servers.net. . 86370 IN NS h.root-servers.net. . 86370 IN NS d.root-servers.net. . 86370 IN NS g.root-servers.net. . 86370 IN NS b.root-servers.net. . 86370 IN NS m.root-servers.net. . 86370 IN NS e.root-servers.net. . 86370 IN NS k.root-servers.net. . 86370 IN NS l.root-servers.net. . 86370 IN NS f.root-servers.net. . 86370 IN RRSIG NS 8 0 518400 20210409050000 20210327040000 42351 . LwjAYGeasi3q7UYqLXslXrMJBKiMWWZW2ppD92Mc6pDutvKpj+ksGlW2 nCGUEskeX4GFAgRz7QqrWMWf3s3kLwbKhne4GjXKi3anemKvFB1v6R0e 3uYafVARr+o5duvIsHOjUDG+1yKAoPkPnrfquf40i/0oJut28cUE3qOI uDjJqeniwSN5maMRKjdYnO2cBUFpBisoQJ6wOcB8Fx4Tl0VN0mQpojT6 XsXnGbIdB59DRXKGO3G6xYjKnct9tz/SsolcObg6DoqBTCGgyockj0+M gPftkSR7/6cfS9fjOtRf3n2lOl86KAcTgrjvK5Fsj9PYlARUpR7+IZ74 JYvjVA== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766 com. 86400 IN RRSIG DS 8 1 86400 20210409050000 20210327040000 42351 . jIZPzD+VW2ARP9cEAuFEiKSclcucwl1gqH8wf3mPA0dIFncp0JsOLeho TfIFeJ11ae6BJqid+6dbpdY2grbJhhHKBOw9/LY4xe/17KeGjswB/nTi Cst2rLPPojsZV5RZShEFurwUSFcYOIrFd8I+B6GGx6I46NWDLvI8MEzi PJa8Ud4YG3lKVHJX+8AGKnhoiTbSVwk5AT6gcjYoYYw1hv0zPmz39r0N /Is4pTYF3wugbprigWn3Gg4VFnQSMcWtKVB89+gvFw1+4Uzj1/hT0YGt R7+H0Nxg4IDrxnrqu72wj6RCfhuXapinEXKx410OPo+6HY2hI0Io2WhR TxKhzQ== ;; Received 1204 bytes from 192.112.36.4#53(g.root-servers.net) in 83 ms broadcom.com. 172800 IN NS pdns1.cscdns.net. broadcom.com. 172800 IN NS pdns2.cscdns.net. broadcom.com. 86400 IN DS 61210 8 1 6F0A9DF17ED6E1F31F2F184A038AF07D2D7DDF97 broadcom.com. 86400 IN DS 61210 8 2 7A97793031AC4256DAEE3DCAC603519C4BE1283690CDA1636A5DC6CB 27F2F188 broadcom.com. 86400 IN RRSIG DS 8 2 86400 20210402044422 20210326033422 58540 com. PYny3W5dKW0diYul/Rv1lUv6s60MdPIan2Fa2+DWFqBtYmAseik7/aPH dhTJoAxU3I1JtTT5uNEwpcAYrhL3giFj2ajJ9XQN95uXjlYpMdbm7Yhq w6YSi6myqLAGnxJP+EUV8DTf9xEDUF8hN9PeFIJ8Qa26Hw4iZWMs93p0 dP8GP7PxpwHMG0sQviG3+LkPTrT6GJPHCXSyz2b94bwLeg== ;; Received 374 bytes from 192.31.80.30#53(d.gtld-servers.net) in 115 ms www.broadcom.com. 300 IN CNAME cdn.broadcom.com. cdn.broadcom.com. 3600 IN CNAME www.broadcom.com.cdn.cloudflare.net. cdn.broadcom.com. 3600 IN RRSIG CNAME 8 3 3600 20210330234650 20210326232722 52716 broadcom.com. R2YL5JokRpaA7sm6Jzxg59usNC78QAN6TA/+NkqTuzmmwUlXJKsRMDsJ Dy5meHUkFOrN0E2JuJlwTaM/PLLey47/mmWlrBOpED25OiDLzOfMXjcz MxrHxYM0abw2XQRHqaJX1lIeu+j0DpPfEtsHCpUCITTOj+hxuvQXYJlB 3WZa0PWoZsdELGD4wB+d67EheNrjmItWVVyQUr11eWwj9mKoZkocjmx3 SHmXHQmA1fmclTUTE3z5LIH6zoSK44kRfxp+KxXZB4w6lG9aQyPKgYNv H85H/1a7+Jh8pLK0XRAmHEKypzoveJbcEBWjxyDptMuIkP0wzVoDtxrz +z6lSg== www.broadcom.com. 300 IN RRSIG CNAME 8 3 300 20210331011713 20210327001855 52716 broadcom.com. i5kxCoQX6qrGJdL9wBaShvIMNSVHIWu8Cj3QCd9JVuDn8vFFLNazSxA4 1pDRaTNrRjZkLNVN0zN1xwHDJB3dVuc3wh+wc75JCp8oNLvPyyMFGXiB V8/3HJ7VPd6gxPKy3gjDlFv6A0+tLLJ3NgL8L3iN89p7T01WT/mmHj+y r04e3e60PlORB+6TJcEbPbIw6I3IY5e/j4s274PxIC6vmV6l+aS1bCfn 8dSBi2pywIEGpO4Ym+XoB7rXK3LQ5o+EgnBr3yDhxUmiUX0/DnoC8/xR IjwlhD/GCCndnN+qTj3SUZtTfdYp33i0xSfEH4SMXTrEVimgiApak4Jb OF9cGw== ;; Received 716 bytes from 156.154.130.100#53(pdns1.cscdns.net) in 54 ms [2.5.0-RELEASE][root@slottet.doff1]/root:I have to admit I'm not good at interpeting this, but it seems one difference is you get an ipv6 address, while I don't. (My internet provider still doesn't offer ipv6)
Could that be part of an explanation? -
I wouldn't think so - since the ipv6 points to the same place..
Did you update your unbound to 1.13.1 - this I believes requires a pkg update from cmd line on pfsense currently
Nothing I can see shows why that should fail dnssec validation.
[21.02-RELEASE][admin@sg4860.local.lan]/root: unbound -V Version 1.13.1 -
I just tried updating unbound as you said, and then I restarted the service afterwards to be sure.
[2.5.0-RELEASE][root@slottet.doff1]/root: unbound -V Version 1.13.1It doesn't seem to make any difference though:
[2.5.0-RELEASE][root@slottet.doff1]/root: dig www.broadcom.com +trace ; <<>> DiG 9.16.12 <<>> www.broadcom.com +trace ;; global options: +cmd . 86328 IN NS d.root-servers.net. . 86328 IN NS g.root-servers.net. . 86328 IN NS a.root-servers.net. . 86328 IN NS i.root-servers.net. . 86328 IN NS k.root-servers.net. . 86328 IN NS h.root-servers.net. . 86328 IN NS b.root-servers.net. . 86328 IN NS j.root-servers.net. . 86328 IN NS l.root-servers.net. . 86328 IN NS c.root-servers.net. . 86328 IN NS f.root-servers.net. . 86328 IN NS m.root-servers.net. . 86328 IN NS e.root-servers.net. . 86328 IN RRSIG NS 8 0 518400 20210409050000 20210327040000 42351 . LwjAYGeasi3q7UYqLXslXrMJBKiMWWZW2ppD92Mc6pDutvKpj+ksGlW2 nCGUEskeX4GFAgRz7QqrWMWf3s3kLwbKhne4GjXKi3anemKvFB1v6R0e 3uYafVARr+o5duvIsHOjUDG+1yKAoPkPnrfquf40i/0oJut28cUE3qOI uDjJqeniwSN5maMRKjdYnO2cBUFpBisoQJ6wOcB8Fx4Tl0VN0mQpojT6 XsXnGbIdB59DRXKGO3G6xYjKnct9tz/SsolcObg6DoqBTCGgyockj0+M gPftkSR7/6cfS9fjOtRf3n2lOl86KAcTgrjvK5Fsj9PYlARUpR7+IZ74 JYvjVA== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms com. 172800 IN NS a.gtld-servers.net. com. 172800 IN NS b.gtld-servers.net. com. 172800 IN NS c.gtld-servers.net. com. 172800 IN NS d.gtld-servers.net. com. 172800 IN NS e.gtld-servers.net. com. 172800 IN NS f.gtld-servers.net. com. 172800 IN NS g.gtld-servers.net. com. 172800 IN NS h.gtld-servers.net. com. 172800 IN NS i.gtld-servers.net. com. 172800 IN NS j.gtld-servers.net. com. 172800 IN NS k.gtld-servers.net. com. 172800 IN NS l.gtld-servers.net. com. 172800 IN NS m.gtld-servers.net. com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766 com. 86400 IN RRSIG DS 8 1 86400 20210409050000 20210327040000 42351 . jIZPzD+VW2ARP9cEAuFEiKSclcucwl1gqH8wf3mPA0dIFncp0JsOLeho TfIFeJ11ae6BJqid+6dbpdY2grbJhhHKBOw9/LY4xe/17KeGjswB/nTi Cst2rLPPojsZV5RZShEFurwUSFcYOIrFd8I+B6GGx6I46NWDLvI8MEzi PJa8Ud4YG3lKVHJX+8AGKnhoiTbSVwk5AT6gcjYoYYw1hv0zPmz39r0N /Is4pTYF3wugbprigWn3Gg4VFnQSMcWtKVB89+gvFw1+4Uzj1/hT0YGt R7+H0Nxg4IDrxnrqu72wj6RCfhuXapinEXKx410OPo+6HY2hI0Io2WhR TxKhzQ== ;; Received 1176 bytes from 199.7.91.13#53(d.root-servers.net) in 54 ms broadcom.com. 172800 IN NS pdns1.cscdns.net. broadcom.com. 172800 IN NS pdns2.cscdns.net. broadcom.com. 86400 IN DS 61210 8 1 6F0A9DF17ED6E1F31F2F184A038AF07D2D7DDF97 broadcom.com. 86400 IN DS 61210 8 2 7A97793031AC4256DAEE3DCAC603519C4BE1283690CDA1636A5DC6CB 27F2F188 broadcom.com. 86400 IN RRSIG DS 8 2 86400 20210402044422 20210326033422 58540 com. PYny3W5dKW0diYul/Rv1lUv6s60MdPIan2Fa2+DWFqBtYmAseik7/aPH dhTJoAxU3I1JtTT5uNEwpcAYrhL3giFj2ajJ9XQN95uXjlYpMdbm7Yhq w6YSi6myqLAGnxJP+EUV8DTf9xEDUF8hN9PeFIJ8Qa26Hw4iZWMs93p0 dP8GP7PxpwHMG0sQviG3+LkPTrT6GJPHCXSyz2b94bwLeg== ;; Received 374 bytes from 192.31.80.30#53(d.gtld-servers.net) in 124 ms www.broadcom.com. 300 IN CNAME cdn.broadcom.com. cdn.broadcom.com. 3600 IN CNAME www.broadcom.com.cdn.cloudflare.net. cdn.broadcom.com. 3600 IN RRSIG CNAME 8 3 3600 20210330234650 20210326232722 52716 broadcom.com. R2YL5JokRpaA7sm6Jzxg59usNC78QAN6TA/+NkqTuzmmwUlXJKsRMDsJ Dy5meHUkFOrN0E2JuJlwTaM/PLLey47/mmWlrBOpED25OiDLzOfMXjcz MxrHxYM0abw2XQRHqaJX1lIeu+j0DpPfEtsHCpUCITTOj+hxuvQXYJlB 3WZa0PWoZsdELGD4wB+d67EheNrjmItWVVyQUr11eWwj9mKoZkocjmx3 SHmXHQmA1fmclTUTE3z5LIH6zoSK44kRfxp+KxXZB4w6lG9aQyPKgYNv H85H/1a7+Jh8pLK0XRAmHEKypzoveJbcEBWjxyDptMuIkP0wzVoDtxrz +z6lSg== www.broadcom.com. 300 IN RRSIG CNAME 8 3 300 20210331011713 20210327001855 52716 broadcom.com. i5kxCoQX6qrGJdL9wBaShvIMNSVHIWu8Cj3QCd9JVuDn8vFFLNazSxA4 1pDRaTNrRjZkLNVN0zN1xwHDJB3dVuc3wh+wc75JCp8oNLvPyyMFGXiB V8/3HJ7VPd6gxPKy3gjDlFv6A0+tLLJ3NgL8L3iN89p7T01WT/mmHj+y r04e3e60PlORB+6TJcEbPbIw6I3IY5e/j4s274PxIC6vmV6l+aS1bCfn 8dSBi2pywIEGpO4Ym+XoB7rXK3LQ5o+EgnBr3yDhxUmiUX0/DnoC8/xR IjwlhD/GCCndnN+qTj3SUZtTfdYp33i0xSfEH4SMXTrEVimgiApak4Jb OF9cGw== ;; Received 716 bytes from 156.154.130.100#53(pdns1.cscdns.net) in 59 ms [2.5.0-RELEASE][root@slottet.doff1]/root:[2.5.0-RELEASE][root@slottet.doff1]/root: dig www.broadcom.com ; <<>> DiG 9.16.12 <<>> www.broadcom.com ;; global options: +cmd ;; connection timed out; no servers could be reached -
@stoffix said in Sporadic dns issue related to DNSSEC:
;; connection timed out; no servers could be reached
Well that for sure is not a dnssec problem..
That is just unbound not running..If you can not talk to loopback on pfsense.
-
Using your workaround, and adding
server: domain-insecure: "broadcom.com"to the unbound option set I get:
[2.5.0-RELEASE][root@slottet.doff1]/root: dig www.broadcom.com ; <<>> DiG 9.16.12 <<>> www.broadcom.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 32110 ;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.broadcom.com. IN A ;; ANSWER SECTION: www.broadcom.com. 300 IN CNAME cdn.broadcom.com. cdn.broadcom.com. 3600 IN CNAME www.broadcom.com.cdn.cloudflare.net. www.broadcom.com.cdn.cloudflare.net. 300 IN A 104.18.5.158 www.broadcom.com.cdn.cloudflare.net. 300 IN A 104.18.4.158 ;; Query time: 585 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Sat Mar 27 22:18:20 CET 2021 ;; MSG SIZE rcvd: 144 [2.5.0-RELEASE][root@slottet.doff1]/root:So it does somehow seem related, doesn't it?
Although I have no clue as to what to look for next to find out about this issue. -
Not sure what to tell you.. It resolves just fine dnssec here.. Maybe your isp is doing something odd with interception?
see the ad, means it passed validation
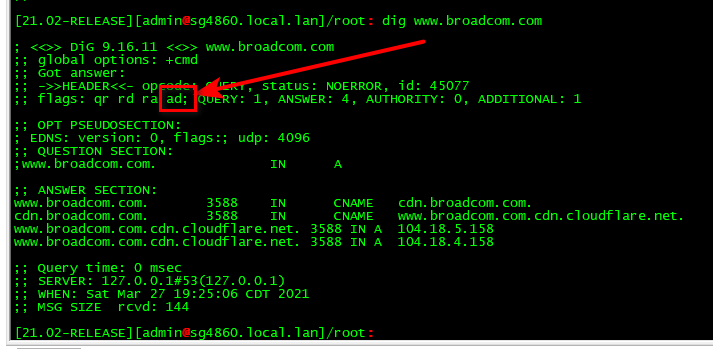
While I see some not so great stuff with the one dnssec test, its not something that should fail validation. And as you see from the other site that tests dnssec - all is good.
Turn up logging in unbound, and see if that points to anything.. You can also setup logging in the option box..
log-queries: yes log-replies: yesAre you on the broadcom ISP I take it - ask them!
Here I asked google, which it does dnssec - and it passes.. see the ad in that query
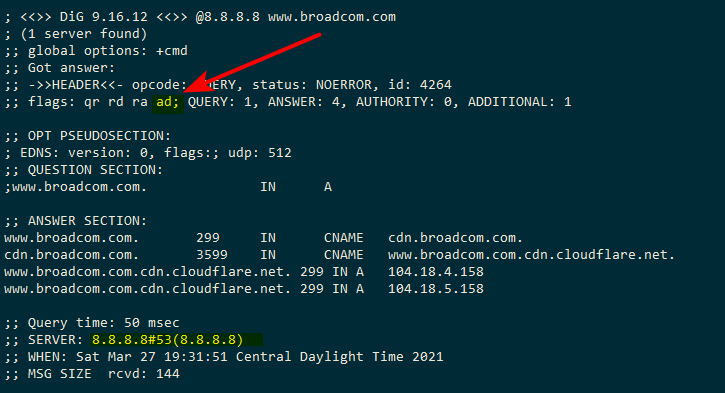
-
Yeah, maybe its my isp doing something weird which usually passes, but fails this one.
I tried turning up logging and adding this to the option box (nothing else in it)
server: log-queries: yes log-replies: yesSometimes I get the timeout:
[2.5.0-RELEASE][root@slottet.doff1]/root: dig www.broadcom.com ; <<>> DiG 9.16.12 <<>> www.broadcom.com ;; global options: +cmd ;; connection timed out; no servers could be reached [2.5.0-RELEASE][root@slottet.doff1]/root:With these entries in the log:
Mar 29 01:37:21 unbound 56883 [56883:1] debug: cache memory msg=128389 rrset=291198 infra=165730 val=59994 Mar 29 01:37:21 unbound 56883 [56883:1] debug: udp request from ip4 127.0.0.1 port 44131 (len 16) Mar 29 01:37:21 unbound 56883 [56883:1] debug: answer from the cache failed Mar 29 01:37:21 unbound 56883 [56883:1] debug: Cache reply: unchecked entry needs validation Mar 29 01:37:21 unbound 56883 [56883:1] info: 127.0.0.1 www.broadcom.com. A IN Mar 29 01:37:16 unbound 56883 [56883:1] debug: cache memory msg=128389 rrset=291198 infra=165730 val=59994 Mar 29 01:37:16 unbound 56883 [56883:1] debug: udp request from ip4 127.0.0.1 port 44131 (len 16) Mar 29 01:37:16 unbound 56883 [56883:1] debug: answer from the cache failed Mar 29 01:37:16 unbound 56883 [56883:1] debug: Cache reply: unchecked entry needs validation Mar 29 01:37:16 unbound 56883 [56883:1] info: 127.0.0.1 www.broadcom.com. A IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns1.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns2.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: DelegationPoint<broadcom.com.>: 2 names (0 missing), 4 addrs (4 result, 0 avail) cacheNS Mar 29 01:37:11 unbound 56883 [56883:0] debug: processQueryTargets: targetqueries 0, currentqueries 0 sentcount 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: processQueryTargets: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state QUERY TARGETS STATE Mar 29 01:37:11 unbound 56883 [56883:0] info: error sending query to auth server ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: Need to send query but have no outgoing interfaces of that family Mar 29 01:37:11 unbound 56883 [56883:0] debug: inserted new pending reply id=112e Mar 29 01:37:11 unbound 56883 [56883:0] debug: serviced query UDP timeout=376 msec Mar 29 01:37:11 unbound 56883 [56883:0] debug: EDNS lookup known=0 vs=0 Mar 29 01:37:11 unbound 56883 [56883:0] debug: dnssec status: expected Mar 29 01:37:11 unbound 56883 [56883:0] debug: sending to target: <broadcom.com.> 2610:a1:1022::100#53 Mar 29 01:37:11 unbound 56883 [56883:0] info: sending query: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: selrtt 376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=120000 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=96256 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: attempt to get extra 3 targets Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns1.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns2.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: DelegationPoint<broadcom.com.>: 2 names (0 missing), 4 addrs (4 result, 0 avail) cacheNS Mar 29 01:37:11 unbound 56883 [56883:0] debug: processQueryTargets: targetqueries 0, currentqueries 0 sentcount 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: processQueryTargets: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state QUERY TARGETS STATE Mar 29 01:37:11 unbound 56883 [56883:0] info: error sending query to auth server ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: Need to send query but have no outgoing interfaces of that family Mar 29 01:37:11 unbound 56883 [56883:0] debug: inserted new pending reply id=a626 Mar 29 01:37:11 unbound 56883 [56883:0] debug: serviced query UDP timeout=376 msec Mar 29 01:37:11 unbound 56883 [56883:0] debug: EDNS lookup known=0 vs=0 Mar 29 01:37:11 unbound 56883 [56883:0] debug: dnssec status: expected Mar 29 01:37:11 unbound 56883 [56883:0] debug: sending to target: <broadcom.com.> 2610:a1:1022::100#53 Mar 29 01:37:11 unbound 56883 [56883:0] info: sending query: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: selrtt 376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=120000 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=96256 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: attempt to get extra 3 targets Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns1.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns2.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: DelegationPoint<broadcom.com.>: 2 names (0 missing), 4 addrs (4 result, 0 avail) cacheNS Mar 29 01:37:11 unbound 56883 [56883:0] debug: processQueryTargets: targetqueries 0, currentqueries 0 sentcount 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: processQueryTargets: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state QUERY TARGETS STATE Mar 29 01:37:11 unbound 56883 [56883:0] info: error sending query to auth server ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: Need to send query but have no outgoing interfaces of that family Mar 29 01:37:11 unbound 56883 [56883:0] debug: inserted new pending reply id=e59a Mar 29 01:37:11 unbound 56883 [56883:0] debug: serviced query UDP timeout=376 msec Mar 29 01:37:11 unbound 56883 [56883:0] debug: EDNS lookup known=0 vs=0 Mar 29 01:37:11 unbound 56883 [56883:0] debug: dnssec status: expected Mar 29 01:37:11 unbound 56883 [56883:0] debug: sending to target: <broadcom.com.> 2610:a1:1022::100#53 Mar 29 01:37:11 unbound 56883 [56883:0] info: sending query: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: selrtt 376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=120000 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=96256 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: attempt to get extra 3 targets Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns1.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns2.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: DelegationPoint<broadcom.com.>: 2 names (0 missing), 4 addrs (4 result, 0 avail) cacheNS Mar 29 01:37:11 unbound 56883 [56883:0] debug: processQueryTargets: targetqueries 0, currentqueries 0 sentcount 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: processQueryTargets: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state QUERY TARGETS STATE Mar 29 01:37:11 unbound 56883 [56883:0] info: error sending query to auth server ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: Need to send query but have no outgoing interfaces of that family Mar 29 01:37:11 unbound 56883 [56883:0] debug: inserted new pending reply id=42eb Mar 29 01:37:11 unbound 56883 [56883:0] debug: serviced query UDP timeout=376 msec Mar 29 01:37:11 unbound 56883 [56883:0] debug: EDNS lookup known=0 vs=0 Mar 29 01:37:11 unbound 56883 [56883:0] debug: dnssec status: expected Mar 29 01:37:11 unbound 56883 [56883:0] debug: sending to target: <broadcom.com.> 2610:a1:1023::100#53 Mar 29 01:37:11 unbound 56883 [56883:0] info: sending query: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: selrtt 376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=120000 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=96256 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: attempt to get extra 3 targets Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns1.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns2.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: DelegationPoint<broadcom.com.>: 2 names (0 missing), 4 addrs (4 result, 0 avail) cacheNS Mar 29 01:37:11 unbound 56883 [56883:0] debug: processQueryTargets: targetqueries 0, currentqueries 0 sentcount 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: processQueryTargets: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state QUERY TARGETS STATE Mar 29 01:37:11 unbound 56883 [56883:0] info: error sending query to auth server ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: Need to send query but have no outgoing interfaces of that family Mar 29 01:37:11 unbound 56883 [56883:0] debug: inserted new pending reply id=7061 Mar 29 01:37:11 unbound 56883 [56883:0] debug: serviced query UDP timeout=376 msec Mar 29 01:37:11 unbound 56883 [56883:0] debug: EDNS lookup known=0 vs=0 Mar 29 01:37:11 unbound 56883 [56883:0] debug: dnssec status: expected Mar 29 01:37:11 unbound 56883 [56883:0] debug: sending to target: <broadcom.com.> 2610:a1:1023::100#53 Mar 29 01:37:11 unbound 56883 [56883:0] info: sending query: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: selrtt 376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=120000 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=96256 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: attempt to get extra 3 targets Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns1.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns2.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: DelegationPoint<broadcom.com.>: 2 names (0 missing), 4 addrs (4 result, 0 avail) cacheNS Mar 29 01:37:11 unbound 56883 [56883:0] debug: processQueryTargets: targetqueries 0, currentqueries 0 sentcount 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: processQueryTargets: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state QUERY TARGETS STATE Mar 29 01:37:11 unbound 56883 [56883:0] info: error sending query to auth server ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: Need to send query but have no outgoing interfaces of that family Mar 29 01:37:11 unbound 56883 [56883:0] debug: inserted new pending reply id=2225 Mar 29 01:37:11 unbound 56883 [56883:0] debug: serviced query UDP timeout=376 msec Mar 29 01:37:11 unbound 56883 [56883:0] debug: EDNS lookup known=0 vs=0 Mar 29 01:37:11 unbound 56883 [56883:0] debug: dnssec status: expected Mar 29 01:37:11 unbound 56883 [56883:0] debug: sending to target: <broadcom.com.> 2610:a1:1023::100#53 Mar 29 01:37:11 unbound 56883 [56883:0] info: sending query: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: selrtt 376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=120000 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=376 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: rtt=96256 Mar 29 01:37:11 unbound 56883 [56883:0] debug: servselect ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: attempt to get extra 3 targets Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns1.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns2.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: DelegationPoint<broadcom.com.>: 2 names (0 missing), 4 addrs (0 result, 4 avail) cacheNS Mar 29 01:37:11 unbound 56883 [56883:0] debug: processQueryTargets: targetqueries 0, currentqueries 0 sentcount 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: processQueryTargets: broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state QUERY TARGETS STATE Mar 29 01:37:11 unbound 56883 [56883:0] info: resolving (init part 3): broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state INIT REQUEST STATE (stage 3) Mar 29 01:37:11 unbound 56883 [56883:0] info: resolving (init part 2): broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state INIT REQUEST STATE (stage 2) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.131.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1023::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip4 156.154.130.100 port 53 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns1.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: pdns2.cscdns.net. * A AAAA Mar 29 01:37:11 unbound 56883 [56883:0] info: DelegationPoint<broadcom.com.>: 2 names (0 missing), 4 addrs (0 result, 4 avail) cacheNS Mar 29 01:37:11 unbound 56883 [56883:0] debug: cache delegation returns delegpt Mar 29 01:37:11 unbound 56883 [56883:0] debug: request has dependency depth of 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: resolving broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state INIT REQUEST STATE Mar 29 01:37:11 unbound 56883 [56883:0] debug: process_request: new external request event Mar 29 01:37:11 unbound 56883 [56883:0] debug: iterator[module 1] operate: extstate:module_state_initial event:module_event_pass Mar 29 01:37:11 unbound 56883 [56883:0] debug: mesh_run: validator module exit state is module_wait_module Mar 29 01:37:11 unbound 56883 [56883:0] debug: validator: pass to next module Mar 29 01:37:11 unbound 56883 [56883:0] info: validator operate: query broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: validator[module 0] operate: extstate:module_state_initial event:module_event_pass Mar 29 01:37:11 unbound 56883 [56883:0] debug: mesh_run: validator module exit state is module_wait_subquery Mar 29 01:37:11 unbound 56883 [56883:0] info: generate request broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] info: DS RRset broadcom.com. DS IN Mar 29 01:37:11 unbound 56883 [56883:0] info: next keyname broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: striplab 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: target keyname broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] info: current keyname com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] info: validator: FindKey www.broadcom.com. A IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: val handle processing q with state VAL_FINDKEY_STATE Mar 29 01:37:11 unbound 56883 [56883:0] info: validated DS broadcom.com. DS IN Mar 29 01:37:11 unbound 56883 [56883:0] info: verify rrset cached broadcom.com. DS IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: Process cached DS response Mar 29 01:37:11 unbound 56883 [56883:0] debug: No DS RRset Mar 29 01:37:11 unbound 56883 [56883:0] info: next keyname broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: striplab 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: target keyname broadcom.com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] info: current keyname com. DNSKEY IN Mar 29 01:37:11 unbound 56883 [56883:0] info: validator: FindKey www.broadcom.com. A IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: val handle processing q with state VAL_FINDKEY_STATE Mar 29 01:37:11 unbound 56883 [56883:0] info: chased extract ;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 0 ;; flags: qr ra ; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: www.broadcom.com. IN A ;; ANSWER SECTION: www.broadcom.com. 118 IN CNAME cdn.broadcom.com. www.broadcom.com. 118 IN RRSIG CNAME 8 3 300 20210401002028 20210328001713 52716 broadcom.com. jOYNUiqp5tpM7Wy8obuKKFVa4YSWFWM7kebthvnTIMwe2ASP7jPQLKMDOIdedQIB146zzeo1eJulF01ZR8Sr6iT8BfN2BIbXK4ymtAZyyGRvy4NmxLpZbqfWmCm0+TZqbtCfvVYKOm8ZRkupu4sShCddi6u0RZa1WRomDHeOcmbZYxPxsP9jBT3Q1+TxWTbAA970nds4xyR5Sk9TQg4IwYTA3dcun/B7uzAMrzZ354OvdHO3peenDi21ypt4WlRzWqWh/jGwd3v0eXhrxR7wjOTM3mW8dfIG9VwrYHrGmvOvKnweDyf34oyAdb4t3SlggMXsuSkdivPlFOeoh6Bfrw== ;{id = 52716} cdn.broadcom.com. 3418 IN CNAME www.broadcom.com.cdn.cloudflare.net. cdn.broadcom.com. 3418 IN RRSIG CNAME 8 3 3600 20210401224511 20210328223250 52716 broadcom.com. F3QWF0hmxtfBm99RXGkG/Sf9MYrNi8qK3oR5f+FZCsOtD/rzFjR7YMJW56y7lH8tFzLnpLKTtTasXfcdKBlUKmbvMJHUEagh6cQqoXpUpBBlk4fCr7JvI/7Sxgm0vxrLDv8m6njtfLsRYG63EG8arnRf4De2VhIaomDrJOmaTpYZMMTSetcHd+F3wjNRHx4H0YVz+i1z571mlrfY59J9xzQZwhcK4YhZbrERRyRTwDxOy3lmeCJPJ42u2qM0Gi90mtU6mRbq5uxgDLiSLVuceL9E7Ot28Y4Yz+H9LOshlOMFRH8KTzWBWMU5YlgUj0TOC90yk0FbUqxhA0JCRCbyJg== ;{id = 52716} ;; AUTHORITY SECTION: ;; ADDITIONAL SECTION: ;; MSG SIZE rcvd: 701 Mar 29 01:37:11 unbound 56883 [56883:0] info: signer is broadcom.com. TYPE0 CLASS0 Mar 29 01:37:11 unbound 56883 [56883:0] debug: validator classification cname Mar 29 01:37:11 unbound 56883 [56883:0] debug: val handle processing q with state VAL_INIT_STATE Mar 29 01:37:11 unbound 56883 [56883:0] debug: validator: nextmodule returned Mar 29 01:37:11 unbound 56883 [56883:0] info: validator operate: query www.broadcom.com. A IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: validator[module 0] operate: extstate:module_wait_module event:module_event_moddone Mar 29 01:37:11 unbound 56883 [56883:0] debug: mesh_run: iterator module exit state is module_finished Mar 29 01:37:11 unbound 56883 [56883:0] debug: prepending 2 rrsets Mar 29 01:37:11 unbound 56883 [56883:0] info: finishing processing for www.broadcom.com. A IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state FINISHED RESPONSE STATE Mar 29 01:37:11 unbound 56883 [56883:0] debug: returning answer from cache. Mar 29 01:37:11 unbound 56883 [56883:0] debug: msg ttl is 118, prefetch ttl 88 Mar 29 01:37:11 unbound 56883 [56883:0] info: msg from cache lookup ;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 0 ;; flags: qr ra ; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: www.broadcom.com.cdn.cloudflare.net. IN A ;; ANSWER SECTION: www.broadcom.com.cdn.cloudflare.net. 118 IN A 104.18.5.158 www.broadcom.com.cdn.cloudflare.net. 118 IN A 104.18.4.158 www.broadcom.com.cdn.cloudflare.net. 118 IN RRSIG A 13 6 300 20210330003409 20210327223409 34505 cloudflare.net. FyGO+ud5OlsfNVK9CKTpOPUQhUzOBLnWWCI+ZWS5kJ9TiRXg3m4Q9N1uOTAVFiOZRkpN+iDk4GO2mFOqLcN6vQ== ;{id = 34505} ;; AUTHORITY SECTION: ;; ADDITIONAL SECTION: ;; MSG SIZE rcvd: 195 Mar 29 01:37:11 unbound 56883 [56883:0] debug: request has dependency depth of 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: resolving www.broadcom.com. A IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state INIT REQUEST STATE Mar 29 01:37:11 unbound 56883 [56883:0] debug: returning CNAME response from cache Mar 29 01:37:11 unbound 56883 [56883:0] debug: msg ttl is 3418, prefetch ttl 3077 Mar 29 01:37:11 unbound 56883 [56883:0] info: msg from cache lookup ;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 0 ;; flags: qr ; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: cdn.broadcom.com. IN A ;; ANSWER SECTION: cdn.broadcom.com. 3418 IN CNAME www.broadcom.com.cdn.cloudflare.net. cdn.broadcom.com. 3418 IN RRSIG CNAME 8 3 3600 20210401224511 20210328223250 52716 broadcom.com. F3QWF0hmxtfBm99RXGkG/Sf9MYrNi8qK3oR5f+FZCsOtD/rzFjR7YMJW56y7lH8tFzLnpLKTtTasXfcdKBlUKmbvMJHUEagh6cQqoXpUpBBlk4fCr7JvI/7Sxgm0vxrLDv8m6njtfLsRYG63EG8arnRf4De2VhIaomDrJOmaTpYZMMTSetcHd+F3wjNRHx4H0YVz+i1z571mlrfY59J9xzQZwhcK4YhZbrERRyRTwDxOy3lmeCJPJ42u2qM0Gi90mtU6mRbq5uxgDLiSLVuceL9E7Ot28Y4Yz+H9LOshlOMFRH8KTzWBWMU5YlgUj0TOC90yk0FbUqxhA0JCRCbyJg== ;{id = 52716} ;; AUTHORITY SECTION: ;; ADDITIONAL SECTION: ;; MSG SIZE rcvd: 383 Mar 29 01:37:11 unbound 56883 [56883:0] debug: request has dependency depth of 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: resolving www.broadcom.com. A IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state INIT REQUEST STATE Mar 29 01:37:11 unbound 56883 [56883:0] debug: returning CNAME response from cache Mar 29 01:37:11 unbound 56883 [56883:0] debug: msg ttl is 118, prefetch ttl 107 Mar 29 01:37:11 unbound 56883 [56883:0] info: msg from cache lookup ;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 0 ;; flags: qr ; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: www.broadcom.com. IN A ;; ANSWER SECTION: www.broadcom.com. 118 IN CNAME cdn.broadcom.com. www.broadcom.com. 118 IN RRSIG CNAME 8 3 300 20210401002028 20210328001713 52716 broadcom.com. jOYNUiqp5tpM7Wy8obuKKFVa4YSWFWM7kebthvnTIMwe2ASP7jPQLKMDOIdedQIB146zzeo1eJulF01ZR8Sr6iT8BfN2BIbXK4ymtAZyyGRvy4NmxLpZbqfWmCm0+TZqbtCfvVYKOm8ZRkupu4sShCddi6u0RZa1WRomDHeOcmbZYxPxsP9jBT3Q1+TxWTbAA970nds4xyR5Sk9TQg4IwYTA3dcun/B7uzAMrzZ354OvdHO3peenDi21ypt4WlRzWqWh/jGwd3v0eXhrxR7wjOTM3mW8dfIG9VwrYHrGmvOvKnweDyf34oyAdb4t3SlggMXsuSkdivPlFOeoh6Bfrw== ;{id = 52716} ;; AUTHORITY SECTION: ;; ADDITIONAL SECTION: ;; MSG SIZE rcvd: 352 Mar 29 01:37:11 unbound 56883 [56883:0] debug: request has dependency depth of 0 Mar 29 01:37:11 unbound 56883 [56883:0] info: resolving www.broadcom.com. A IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: iter_handle processing q with state INIT REQUEST STATE Mar 29 01:37:11 unbound 56883 [56883:0] debug: process_request: new external request event Mar 29 01:37:11 unbound 56883 [56883:0] debug: iterator[module 1] operate: extstate:module_state_initial event:module_event_pass Mar 29 01:37:11 unbound 56883 [56883:0] debug: mesh_run: validator module exit state is module_wait_module Mar 29 01:37:11 unbound 56883 [56883:0] debug: validator: pass to next module Mar 29 01:37:11 unbound 56883 [56883:0] info: validator operate: query www.broadcom.com. A IN Mar 29 01:37:11 unbound 56883 [56883:0] debug: validator[module 0] operate: extstate:module_state_initial event:module_event_new Mar 29 01:37:11 unbound 56883 [56883:0] debug: mesh_run: start Mar 29 01:37:11 unbound 56883 [56883:0] debug: udp request from ip4 127.0.0.1 port 44131 (len 16) Mar 29 01:37:11 unbound 56883 [56883:0] debug: answer from the cache failed Mar 29 01:37:11 unbound 56883 [56883:0] info: 127.0.0.1 www.broadcom.com. A INI see the lines repeated several times:
Mar 29 01:37:11 unbound 56883 [56883:0] info: error sending query to auth server ip6 2610:a1:1022::100 port 53 (len 28) Mar 29 01:37:11 unbound 56883 [56883:0] debug: Need to send query but have no outgoing interfaces of that familyCould the issue somehow be ipv6 related? Since my isp doesn't deliver ipv6?
Other times I get this result:[2.5.0-RELEASE][root@slottet.doff1]/root: dig www.broadcom.com ; <<>> DiG 9.16.12 <<>> www.broadcom.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 64916 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.broadcom.com. IN A ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Mon Mar 29 01:35:15 CEST 2021 ;; MSG SIZE rcvd: 45 [2.5.0-RELEASE][root@slottet.doff1]/root:It's missing the 'ad' flag!
With this in the log:Mar 29 01:35:16 unbound 56883 [56883:1] debug: close fd 43 Mar 29 01:35:16 unbound 56883 [56883:1] debug: comm_point_close of 43: event_del Mar 29 01:35:16 unbound 56883 [56883:1] debug: tcp took too long, dropped Mar 29 01:35:15 unbound 56883 [56883:0] info: 127.0.0.1 www.broadcom.com. A IN SERVFAIL 0.000000 1 45 Mar 29 01:35:15 unbound 56883 [56883:0] info: 127.0.0.1 www.broadcom.com. A INI find this quite puzzling!
For reference checking with google I get the same result as you:[2.5.0-RELEASE][root@slottet.doff1]/root: dig @8.8.8.8 www.broadcom.com ; <<>> DiG 9.16.12 <<>> @8.8.8.8 www.broadcom.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 49208 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ;; QUESTION SECTION: ;www.broadcom.com. IN A ;; ANSWER SECTION: www.broadcom.com. 299 IN CNAME cdn.broadcom.com. cdn.broadcom.com. 3599 IN CNAME www.broadcom.com.cdn.cloudflare.net. www.broadcom.com.cdn.cloudflare.net. 299 IN A 104.18.4.158 www.broadcom.com.cdn.cloudflare.net. 299 IN A 104.18.5.158 ;; Query time: 58 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Mon Mar 29 02:02:18 CEST 2021 ;; MSG SIZE rcvd: 144 [2.5.0-RELEASE][root@slottet.doff1]/root:I can't find anything in the log for this, but i guess it's because google resolved the address, and not my resolver.
Could this be an ipv6 related issue? maybe a configuration fault on my side?
-
@stoffix said in Sporadic dns issue related to DNSSEC:
Could this be an ipv6 related issue? maybe a configuration fault on my side?
If you have no IPv6 - why would it even try to talk to an IPv6 server?
You could try setting
do-ip6: noIn your options box.. But it shouldn't even try if you don't have ipv6 on your wan..
Mar 29 01:37:11 unbound 56883 [56883:0] debug: Need to send query but have no outgoing interfaces of that family
That makes no sense to me - unless all you got back for some NS was an AAAA
-
First things first : I just generated a new 'DNSSEC' report, as the latest on dnsviz.net was 3 months old :
https://dnsviz.net/d/broadcom.com/YGFlsg/dnssec/
which doesn't show a nice clean result.
@stoffix said in Sporadic dns issue related to DNSSEC:
;; connection timed out; no servers could be reached
unbound getting restarted by an incoming DHCP lease ?
Check the resolver log : how many time it restarts per day ? hour ? minute ?
Just to be sure, uncheck :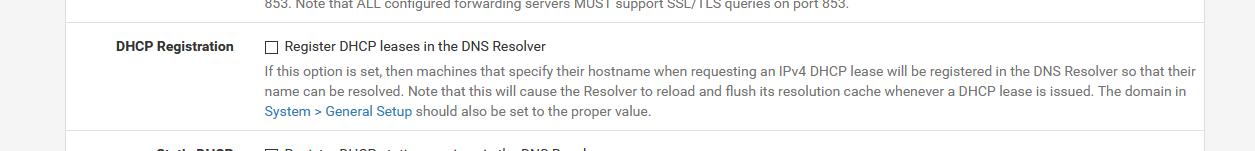
Btw : I did a new test on dnsviz.net, 2 minutes later.
https://dnsviz.net/d/broadcom.com/YGFoPg/dnssec/
This time : no red 'fatal' error messages - just 4 warnings. Looks like they are in the middle of some KSK shift. -
@gertjan said in Sporadic dns issue related to DNSSEC:
atest on dnsviz.net was 3 months old :
No because I updated it when I did it - so not sure how that was possible.
But yeah failure to talk to someone is not a dnssec failure..
-
@gertjan
dhcp registration was on, i've turned it off last night.
At the moment the log fills so quicly i can't see how often it restarted, but it's off now anyway. Thanks.my options box now reads:
server: log-queries: yes log-replies: yes do-ip6: noMy wan is a pppoe, and I don't have a public ipv6 address. I checked the interface status page and for my wan it shows a link-local ipv6, maybe that's why the resolver was trying ipv6 as well?
For now dig only seems to show a timeout checking www.broadcom.com
I got some more detailed logs from the resolver in the attatched file: log.txt
It's too large to write it in the post.Some entries looks interesting:
Mar 29 14:57:01 unbound 99799 [99799:1] debug: Cache reply: unchecked entry needs validation Mar 29 14:56:56 unbound 99799 [99799:1] info: mesh_run: end 2 recursion states (1 with reply, 0 detached), 1 waiting replies, 239 recursion replies sent, 0 replies dropped, 0 states jostled out Mar 29 14:56:56 unbound 99799 [99799:1] debug: mesh_run: iterator module exit state is module_wait_reply Mar 29 14:56:56 unbound 99799 [99799:1] debug: timeout udp Mar 29 14:57:00 unbound 99799 [99799:1] debug: query response was timeout Mar 29 14:57:11 unbound 99799 [99799:1] debug: out of query targets -- returning SERVFAIL Mar 29 14:57:42 unbound 99799 [99799:1] info: Missing DNSKEY RRset in response to DNSKEY query. Mar 29 14:57:42 unbound 99799 [99799:1] debug: not validating response, is valrec(validation recursion lookup)And the responses I see in the log doesn't show the 'ad' flag either.
If I should guess it looks like unbound is unable to validate (dnssec) www.broadcom.com by not getting some query responsens, and therefore timeouts while waiting for said responses. It looks like unbound keeps trying for a little while after dig gives up -not that it makes a difference.Could there be an ipv4 specific issue somewhere?
Or maye a "geographical" issue? (I'm located in northern Norway) -
@stoffix said in Sporadic dns issue related to DNSSEC:
Or maye a "geographical" issue?
Possible - when you resolve you have to talk to the authoritative nameservers for a domain or tld, etc. So yeah its possible that isp peering issues, or just geographic issues related to latency could cause pain in resolving.
So if unbound has issues talking to specific NS returned, then it should try not to talk to those and choose more the NS with better response times, etc. But if your cache was clearing all the time because of unbound restarts.. Then it wouldn't know which ns it was having issues with, etc.
Now that you have unbound not restarting all the time, see if you settle down for resolving that fqdn.. You can always look up details of how a specific fqdn would be looked up.
[21.02-RELEASE][admin@sg4860.local.lan]/: unbound-control -c /var/unbound/unbound.conf lookup www.broadcom.com The following name servers are used for lookup of www.broadcom.com. ;rrset 7932 13 0 2 0 com. 7932 IN NS a.gtld-servers.net. com. 7932 IN NS b.gtld-servers.net. com. 7932 IN NS c.gtld-servers.net. com. 7932 IN NS d.gtld-servers.net. com. 7932 IN NS e.gtld-servers.net. com. 7932 IN NS f.gtld-servers.net. com. 7932 IN NS g.gtld-servers.net. com. 7932 IN NS h.gtld-servers.net. com. 7932 IN NS i.gtld-servers.net. com. 7932 IN NS j.gtld-servers.net. com. 7932 IN NS k.gtld-servers.net. com. 7932 IN NS l.gtld-servers.net. com. 7932 IN NS m.gtld-servers.net. ;rrset 7932 1 1 11 5 com. 7932 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CFC41A5766 com. 7932 IN RRSIG DS 8 1 86400 20210410050000 20210328040000 42351 . jHnh+pTanx1cXVQCLOzD1VMZ/aDZYQWIN6mGvldH233rd5wBXvrHFA7la5osDjKb12bETey69jObKgCeEIKx5eq3ILxlKRBMcKdrl/GFjjobuFZHxvSlUbjzUhy0YIUx5d9mNBrpDdiCoOx8870VbKCub22VN5SE2td0Iz3Sbz4RP382hFq2xylU6TrEnIYduXDA6pr7uFs8ItjXmZKgMkFSZbDAERIpjBbUYYoWReREol9PoQOm/0Pku9ohOvVzubNtRtVqAcQ2YC0iPQjy/cY4At7GfDYm20bBI26M9j2MHKmXWbkjBUp822YN2NPc30YZfcJiMLazJuPQmCQQuA== ;{id = 42351} ;rrset 7932 1 0 1 0 m.gtld-servers.net. 7932 IN A 192.55.83.30 ;rrset 7932 1 0 1 0 m.gtld-servers.net. 7932 IN AAAA 2001:501:b1f9::30 ;rrset 7932 1 0 1 0 l.gtld-servers.net. 7932 IN A 192.41.162.30 ;rrset 7932 1 0 1 0 l.gtld-servers.net. 7932 IN AAAA 2001:500:d937::30 ;rrset 7932 1 0 1 0 k.gtld-servers.net. 7932 IN A 192.52.178.30 ;rrset 7932 1 0 1 0 k.gtld-servers.net. 7932 IN AAAA 2001:503:d2d::30 ;rrset 7932 1 0 1 0 j.gtld-servers.net. 7932 IN A 192.48.79.30 ;rrset 7932 1 0 1 0 j.gtld-servers.net. 7932 IN AAAA 2001:502:7094::30 ;rrset 7932 1 0 1 0 i.gtld-servers.net. 7932 IN A 192.43.172.30 ;rrset 7932 1 0 1 0 i.gtld-servers.net. 7932 IN AAAA 2001:503:39c1::30 ;rrset 7932 1 0 1 0 h.gtld-servers.net. 7932 IN A 192.54.112.30 ;rrset 7932 1 0 1 0 h.gtld-servers.net. 7932 IN AAAA 2001:502:8cc::30 ;rrset 7932 1 0 1 0 g.gtld-servers.net. 7932 IN A 192.42.93.30 ;rrset 7932 1 0 1 0 g.gtld-servers.net. 7932 IN AAAA 2001:503:eea3::30 ;rrset 7932 1 0 1 0 f.gtld-servers.net. 7932 IN A 192.35.51.30 ;rrset 7932 1 0 1 0 f.gtld-servers.net. 7932 IN AAAA 2001:503:d414::30 ;rrset 7932 1 0 1 0 e.gtld-servers.net. 7932 IN A 192.12.94.30 ;rrset 7932 1 0 1 0 e.gtld-servers.net. 7932 IN AAAA 2001:502:1ca1::30 ;rrset 7932 1 0 1 0 d.gtld-servers.net. 7932 IN A 192.31.80.30 ;rrset 7932 1 0 1 0 d.gtld-servers.net. 7932 IN AAAA 2001:500:856e::30 ;rrset 7932 1 0 1 0 c.gtld-servers.net. 7932 IN A 192.26.92.30 ;rrset 7932 1 0 1 0 c.gtld-servers.net. 7932 IN AAAA 2001:503:83eb::30 ;rrset 7932 1 0 1 0 b.gtld-servers.net. 7932 IN A 192.33.14.30 ;rrset 7932 1 0 1 0 b.gtld-servers.net. 7932 IN AAAA 2001:503:231d::2:30 ;rrset 7932 1 0 1 0 a.gtld-servers.net. 7932 IN A 192.5.6.30 ;rrset 7932 1 0 1 0 a.gtld-servers.net. 7932 IN AAAA 2001:503:a83e::2:30 Delegation with 13 names, of which 0 can be examined to query further addresses. It provides 26 IP addresses. 2001:503:a83e::2:30 not in infra cache. 192.5.6.30 expired, rto 3390592 msec, tA 0 tAAAA 0 tother 0. 2001:503:231d::2:30 not in infra cache. 192.33.14.30 expired, rto 3390592 msec, tA 0 tAAAA 0 tother 0. 2001:503:83eb::30 not in infra cache. 192.26.92.30 expired, rto 3390592 msec, tA 0 tAAAA 0 tother 0. 2001:500:856e::30 not in infra cache. 192.31.80.30 rto 320 msec, ttl 717, ping 4 var 79 rtt 320, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 2001:502:1ca1::30 not in infra cache. 192.12.94.30 not in infra cache. 2001:503:d414::30 not in infra cache. 192.35.51.30 not in infra cache. 2001:503:eea3::30 not in infra cache. 192.42.93.30 not in infra cache. 2001:502:8cc::30 not in infra cache. 192.54.112.30 not in infra cache. 2001:503:39c1::30 not in infra cache. 192.43.172.30 not in infra cache. 2001:502:7094::30 not in infra cache. 192.48.79.30 not in infra cache. 2001:503:d2d::30 not in infra cache. 192.52.178.30 not in infra cache. 2001:500:d937::30 not in infra cache. 192.41.162.30 not in infra cache. 2001:501:b1f9::30 not in infra cache. 192.55.83.30 not in infra cache. [21.02-RELEASE][admin@sg4860.local.lan]/:Keeping in mind that you have more than those to contend with because the cname points to cloudflare as well.
[21.02-RELEASE][admin@sg4860.local.lan]/: unbound-control -c /var/unbound/unbound.conf lookup www.broadcom.com.cdn.cloudflare.net The following name servers are used for lookup of www.broadcom.com.cdn.cloudflare.net. ;rrset 14314 5 0 2 0 cloudflare.net. 14314 IN NS ns1.cloudflare.net. cloudflare.net. 14314 IN NS ns2.cloudflare.net. cloudflare.net. 14314 IN NS ns3.cloudflare.net. cloudflare.net. 14314 IN NS ns4.cloudflare.net. cloudflare.net. 14314 IN NS ns5.cloudflare.net. ;rrset 14314 1 1 11 5 cloudflare.net. 14314 IN DS 2371 13 2 90F710A107DA51ED78125D30A68704CF3C0308AFD01BFCD7057D4BD03B62C68B cloudflare.net. 14314 IN RRSIG DS 8 2 86400 20210404052352 20210328041352 30944 net. JmDnk7yeQJZDVl5Fz1Ijo9tw7egwoRYaGP9kkwogFOkGUreJvF3LFocfKCnpAolV3692TrYCWoUVglgTm5Ye2KSAoEl8D7J58UTbczpeyncrNMjXe6E1WZBe02smwe6njOeRDM3mJBNt1AUVWNqMK4OMETYGyGPhs4QYUVFnzXK9ynxp+Be9YwMQJjyEfYO30uy6nL/hF9SYRrHTbf4QIQ== ;{id = 30944} ;rrset 14314 1 0 1 0 ns5.cloudflare.net. 14314 IN A 198.41.223.31 ;rrset 14314 1 0 1 0 ns5.cloudflare.net. 14314 IN AAAA 2400:cb00:2049:1::c629:df1f ;rrset 14314 1 0 1 0 ns4.cloudflare.net. 14314 IN A 198.41.223.131 ;rrset 14314 1 0 1 0 ns4.cloudflare.net. 14314 IN AAAA 2400:cb00:2049:1::c629:df83 ;rrset 14314 1 0 1 0 ns3.cloudflare.net. 14314 IN A 198.41.222.31 ;rrset 14314 1 0 1 0 ns3.cloudflare.net. 14314 IN AAAA 2400:cb00:2049:1::c629:de1f ;rrset 14314 1 0 1 0 ns2.cloudflare.net. 14314 IN A 198.41.222.131 ;rrset 14314 1 0 1 0 ns2.cloudflare.net. 14314 IN AAAA 2400:cb00:2049:1::c629:de83 ;rrset 14314 1 0 1 0 ns1.cloudflare.net. 14314 IN A 173.245.59.31 ;rrset 14314 1 0 1 0 ns1.cloudflare.net. 14314 IN AAAA 2400:cb00:2049:1::adf5:3b1f Delegation with 5 names, of which 0 can be examined to query further addresses. It provides 10 IP addresses. 2400:cb00:2049:1::adf5:3b1f not in infra cache. 173.245.59.31 expired, rto 3390592 msec, tA 0 tAAAA 0 tother 0. 2400:cb00:2049:1::c629:de83 not in infra cache. 198.41.222.131 expired, rto 3390592 msec, tA 0 tAAAA 0 tother 0. 2400:cb00:2049:1::c629:de1f not in infra cache. 198.41.222.31 expired, rto 3390592 msec, tA 0 tAAAA 0 tother 0. 2400:cb00:2049:1::c629:df83 not in infra cache. 198.41.223.131 expired, rto 3390592 msec, tA 0 tAAAA 0 tother 0. 2400:cb00:2049:1::c629:df1f not in infra cache. 198.41.223.31 expired, rto 3390592 msec, tA 0 tAAAA 0 tother 0. [21.02-RELEASE][admin@sg4860.local.lan]/:BTW - you might notice I have no ipv6 ns in the infra cache, because I have no-ip6 set as well.. Was playing with that from another thread a couple days back.. And hadn't yet removed it..
-
It's interesting that you have no-ip6 set as well, since we shouldn't percieve any difference then.
When I look up the cloudflare fqdn It's almost letter by letter the same as yours:
[2.5.0-RELEASE][root@slottet.doff1]/root: unbound-control -c /var/unbound/unbound.conf lookup www.broadcom.com.cdn.cloudflare.net The following name servers are used for lookup of www.broadcom.com.cdn.cloudflare.net. ;rrset 82086 5 0 2 0 cloudflare.net. 82086 IN NS ns1.cloudflare.net. cloudflare.net. 82086 IN NS ns2.cloudflare.net. cloudflare.net. 82086 IN NS ns3.cloudflare.net. cloudflare.net. 82086 IN NS ns4.cloudflare.net. cloudflare.net. 82086 IN NS ns5.cloudflare.net. ;rrset 82086 1 1 11 5 cloudflare.net. 82086 IN DS 2371 13 2 90F710A107DA51ED78125D30A68704CF3C0308AFD01BFCD7057D4BD03B62C68B cloudflare.net. 82086 IN RRSIG DS 8 2 86400 20210404052352 20210328041352 30944 net. JmDnk7yeQJZDVl5Fz1Ijo9tw7egwoRYaGP9kkwogFOkGUreJvF3LFocfKCnpAolV3692TrYCWo UVglgTm5Ye2KSAoEl8D7J58UTbczpeyncrNMjXe6E1WZBe02smwe6njOeRDM3mJBNt1AUVWNqMK4OMETYGyGPhs4QYUVFnzXK9ynxp+Be9YwMQJjyEfYO30uy6nL/hF9SYRrHTbf4QIQ== ;{id = 30944} ;rrset 82086 1 0 1 0 ns5.cloudflare.net. 82086 IN A 198.41.223.31 ;rrset 82086 1 0 1 0 ns5.cloudflare.net. 82086 IN AAAA 2400:cb00:2049:1::c629:df1f ;rrset 82086 1 0 1 0 ns4.cloudflare.net. 82086 IN A 198.41.223.131 ;rrset 82086 1 0 1 0 ns4.cloudflare.net. 82086 IN AAAA 2400:cb00:2049:1::c629:df83 ;rrset 82086 1 0 1 0 ns3.cloudflare.net. 82086 IN A 198.41.222.31 ;rrset 82086 1 0 1 0 ns3.cloudflare.net. 82086 IN AAAA 2400:cb00:2049:1::c629:de1f ;rrset 82086 1 0 1 0 ns2.cloudflare.net. 82086 IN A 198.41.222.131 ;rrset 82086 1 0 1 0 ns2.cloudflare.net. 82086 IN AAAA 2400:cb00:2049:1::c629:de83 ;rrset 82086 1 0 1 0 ns1.cloudflare.net. 82086 IN A 173.245.59.31 ;rrset 82086 1 0 1 0 ns1.cloudflare.net. 82086 IN AAAA 2400:cb00:2049:1::adf5:3b1f Delegation with 5 names, of which 0 can be examined to query further addresses. It provides 10 IP addresses. 2400:cb00:2049:1::adf5:3b1f not in infra cache. 173.245.59.31 not in infra cache. 2400:cb00:2049:1::c629:de83 not in infra cache. 198.41.222.131 expired, rto 3390592 msec, tA 0 tAAAA 0 tother 0. 2400:cb00:2049:1::c629:de1f not in infra cache. 198.41.222.31 rto 233 msec, ttl 553, ping 9 var 56 rtt 233, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 2400:cb00:2049:1::c629:df83 not in infra cache. 198.41.223.131 rto 315 msec, ttl 553, ping 3 var 78 rtt 315, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 2400:cb00:2049:1::c629:df1f not in infra cache. 198.41.223.31 rto 271 msec, ttl 553, ping 7 var 66 rtt 271, tA 0, tAAAA 0, tother 0, EDNS 0 probed. [2.5.0-RELEASE][root@slottet.doff1]/root:For broadcom.com I only get two nameservers, and they're different than yours:
[2.5.0-RELEASE][root@slottet.doff1]/root: unbound-control -c /var/unbound/unbound.conf lookup www.broadcom.com The following name servers are used for lookup of www.broadcom.com. ;rrset 86355 2 0 2 0 broadcom.com. 86355 IN NS pdns1.cscdns.net. broadcom.com. 86355 IN NS pdns2.cscdns.net. ;rrset 86355 2 1 11 5 broadcom.com. 86355 IN DS 61210 8 1 6F0A9DF17ED6E1F31F2F184A038AF07D2D7DDF97 broadcom.com. 86355 IN DS 61210 8 2 7A97793031AC4256DAEE3DCAC603519C4BE1283690CDA1636A5DC6CB27F2F188 broadcom.com. 86355 IN RRSIG DS 8 2 86400 20210402044422 20210326033422 58540 com. PYny3W5dKW0diYul/Rv1lUv6s60MdPIan2Fa2+DWFqBtYmAseik7/aPHdhTJoAxU3I1JtTT5uNEwpcAYrhL3giFj2ajJ9XQN95uXjlYpMdbm7Yhqw6YSi6myqLAGnxJP+EUV8DTf9xEDUF8hN9PeFIJ8Qa26Hw4iZWMs93p0dP8GP7PxpwHMG0sQviG3+LkPTrT6GJPHCXSyz2b94bwLeg== ;{id = 58540} ;rrset 14355 1 0 8 0 pdns2.cscdns.net. 14355 IN A 156.154.131.100 ;rrset 14355 1 0 8 0 pdns1.cscdns.net. 14355 IN A 156.154.130.100 Delegation with 2 names, of which 2 can be examined to query further addresses. It provides 2 IP addresses. 156.154.130.100 rto 119000 msec, ttl 855, ping 13 var 79 rtt 329, tA 0, tAAAA 0, tother 3, probedelay 21, EDNS 0 probed. 156.154.131.100 rto 119000 msec, ttl 856, ping 0 var 94 rtt 376, tA 0, tAAAA 0, tother 3, probedelay 12, EDNS 0 assumed. [2.5.0-RELEASE][root@slottet.doff1]/root:With DNSSEC disabled I get this:
[2.5.0-RELEASE][root@slottet.doff1]/root: dig www.broadcom.com ; <<>> DiG 9.16.12 <<>> www.broadcom.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 47615 ;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.broadcom.com. IN A ;; ANSWER SECTION: www.broadcom.com. 94 IN CNAME cdn.broadcom.com. cdn.broadcom.com. 3394 IN CNAME www.broadcom.com.cdn.cloudflare.net. www.broadcom.com.cdn.cloudflare.net. 94 IN A 104.18.5.158 www.broadcom.com.cdn.cloudflare.net. 94 IN A 104.18.4.158 ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Mon Mar 29 17:16:39 CEST 2021 ;; MSG SIZE rcvd: 144[2.5.0-RELEASE][root@slottet.doff1]/root: unbound-control -c /var/unbound/unbound.conf lookup www.broadcom.com The following name servers are used for lookup of www.broadcom.com. ;rrset 85586 2 0 2 0 broadcom.com. 85586 IN NS pdns1.cscdns.net. broadcom.com. 85586 IN NS pdns2.cscdns.net. ;rrset 85586 2 1 2 0 broadcom.com. 85586 IN DS 61210 8 1 6F0A9DF17ED6E1F31F2F184A038AF07D2D7DDF97 broadcom.com. 85586 IN DS 61210 8 2 7A97793031AC4256DAEE3DCAC603519C4BE1283690CDA1636A5DC6CB27F2F188 broadcom.com. 85586 IN RRSIG DS 8 2 86400 20210402044422 20210326033422 58540 com. PYny3W5dKW0diYul/Rv1lUv6s60MdPIan2Fa2+DWFqBtYmAseik7/aPHdhTJoAxU3I1JtTT5uNEwpcAYrhL3giFj2ajJ9XQN95uXjlYpMdbm7Yhqw6YSi6myqLAGnxJP+EUV8DTf9xEDUF8hN9PeFIJ8Qa26Hw4iZWMs93p0dP8GP7PxpwHMG0sQviG3+LkPTrT6GJPHCXSyz2b94bwLeg== ;{id = 58540} ;rrset 13587 1 0 8 0 pdns2.cscdns.net. 13587 IN A 156.154.131.100 ;rrset 13587 1 0 8 0 pdns1.cscdns.net. 13587 IN A 156.154.130.100 Delegation with 2 names, of which 2 can be examined to query further addresses. It provides 2 IP addresses. 156.154.130.100 rto 307 msec, ttl 87, ping 11 var 74 rtt 307, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 156.154.131.100 not in infra cache. [2.5.0-RELEASE][root@slottet.doff1]/root:The only differences I notice betwenn dnssec support enabled/disabled is some of the rrset digits are different.
Could it be an issue with "my" nameservers? -
Ah you had them cached, mine didn't so it just listed the NS it knew about that it would need to talk to to look that up.. Once I actually did a query for it, then the actual ns would be listed.
[21.02-RELEASE][admin@sg4860.local.lan]/: unbound-control -c /var/unbound/unbound.conf lookup www.broadcom.com The following name servers are used for lookup of www.broadcom.com. ;rrset 86396 2 0 2 0 broadcom.com. 86396 IN NS pdns1.cscdns.net. broadcom.com. 86396 IN NS pdns2.cscdns.net. ;rrset 86396 2 1 11 5 broadcom.com. 86396 IN DS 61210 8 1 6F0A9DF17ED6E1F31F2F184A038AF07D2D7DDF97 broadcom.com. 86396 IN DS 61210 8 2 7A97793031AC4256DAEE3DCAC603519C4BE1283690CDA1636A5DC6CB27F2F188 broadcom.com. 86396 IN RRSIG DS 8 2 86400 20210402044422 20210326033422 58540 com. PYny3W5dKW0diYul/Rv1lUv6s60MdPIan2Fa2+DWFqBtYmAseik7/aPHdhTJoAxU3I1JtTT5uNEwpcAYrhL3giFj2ajJ9XQN95uXjlYpMdbm7Yhqw6YSi6myqLAGnxJP+EUV8DTf9xEDUF8hN9PeFIJ8Qa26Hw4iZWMs93p0dP8GP7PxpwHMG0sQviG3+LkPTrT6GJPHCXSyz2b94bwLeg== ;{id = 58540} ;rrset 14396 1 0 8 0 pdns2.cscdns.net. 14396 IN A 156.154.131.100 ;rrset 14396 1 0 8 0 pdns1.cscdns.net. 14396 IN A 156.154.130.100 Delegation with 2 names, of which 2 can be examined to query further addresses. It provides 2 IP addresses. 156.154.130.100 rto 191 msec, ttl 896, ping 3 var 47 rtt 191, tA 0, tAAAA 0, tother 0, EDNS 0 probed. 156.154.131.100 not in infra cache. [21.02-RELEASE][admin@sg4860.local.lan]/:Your "tother 3" could point to time outs for other records, ie your dnssec stuff..
-
I (spending way too much time) found out "tother 3" means timeout other and 3 is the maximum value.
I guess there's not much more to do/find out about this. If the problem escalates I'll just have to turn off DNSSEC, at least now I know where to look.
Thank you for all your help!
-
tA and tAAAA and tother should all be zeros.. If they are not - then your having problems talking to that NS.. either network issues, or it just sucks as a NS and isn't answering.