HAProxy basic configuration issue
-
Using pfSense, I have a LetsEncrypt certificate and can accesss pfSense using the FQDN without the security flags. I want to do the same for internal servers only, but can't get that to work. I have DNS Resolver set to register DHCP leases and DHCP static mappings. (But is that necessary with a properly configured HAProxy?) Some servers have static addresses.
HAProxy is enabled, max connections are set to 100, and max SSL D-H size is set to 2048. Otherwise, everything on Settings page is default.
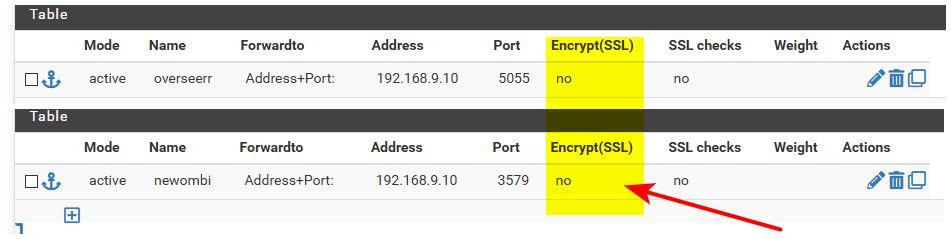
Backend health check method is set to none. Here's a picture of other backend settings: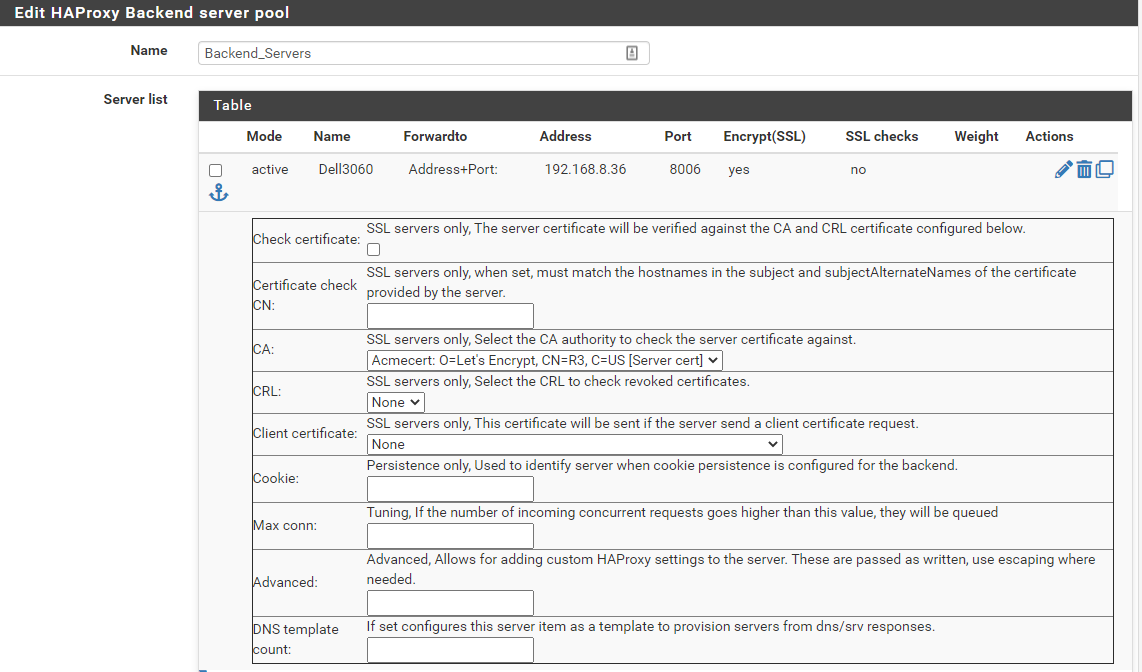
On the Frontend, both "Add ACL" boxes are checked under SSL Offloading; Certificate. Here are pictures of the top: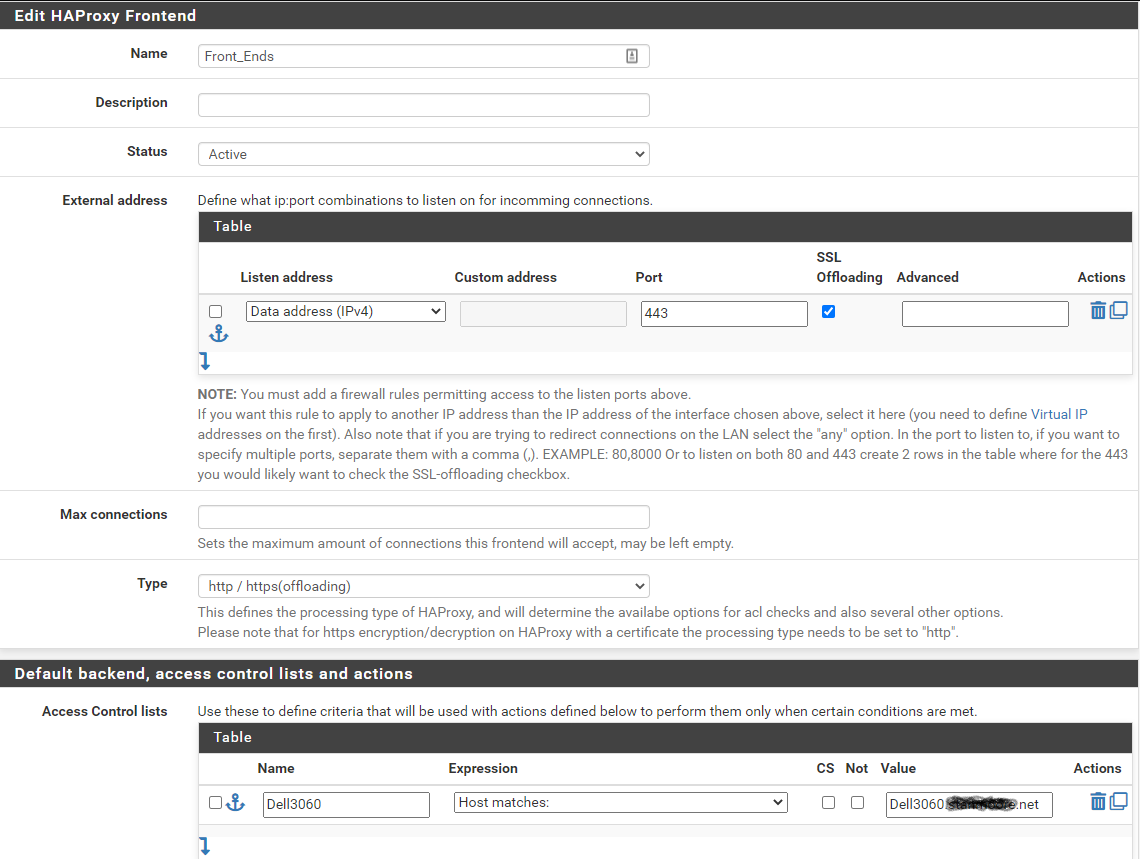
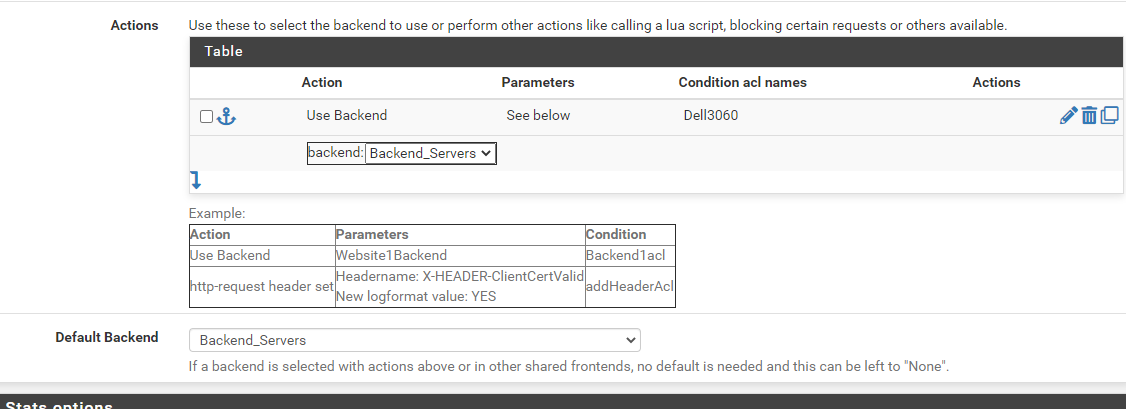
The "Listen address" is the interface of the subnet my computers are on.
When I try to use this, I just get a browser message that the site can't be reached. I've looked through and watched quite a bit of stuff on the internet, but I suspect there's just something basic that I'm not getting. Any help would be appreciated. -
@stan said in HAProxy basic configuration issue:
The "Listen address" is the interface of the subnet my computers are on.
So you want front end to listen on your lan side IP of pfsense on 443, then you want to send traffic to your sever, also via https on port 8006. And what cert is the server using? That pfsense is going to trust.
Im confused with what your trying to accomplish here? So you have a host override set so this fqdn your acme cert CN is - resolving to your pfsense lan side IP?
-
johnpoz,
My objective is just to gain access to internal servers using a FQDN and the LetsEncrypt certificate, so that my Chrome browser will memorize the user name and password. I can access them with their IP addresses, but have to go through the process of overriding the security warnings and then sign in.
I'd prefer using 443 on the front end and having that converted to 8006, but would be happy if it worked using 8006 on the frontend.
As to "what cert is the server using", I thought that I could, through the proxy process, have it use the same cert that is in my pfSense.
I had previously tried a host override and it didn't change anything. I just set it up again, and that still doesn't help. I assume that setting DNS Resolver to register DHCP leases and static mappings would accomplish the same thing, at least of servers without static addresses.
BTW, thanks for the very rapid response. -
You can offload your ssl to haproxy... But this looks to me like your trying to do ssl to your server on port 8006, where this would just be http..
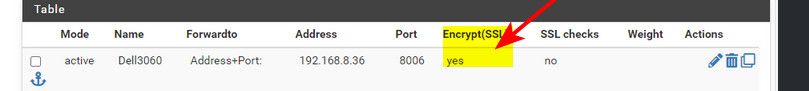
And you would listen on your wan IP, ie public IP - because this is where your fqdn that your acme cert points to right?
I do this for 2 different fqdn.. Using the acme cert.. But the traffic to the backend is just http.
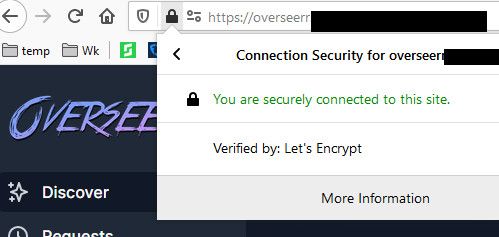
So sure in my browser I can just hit the acme fqdn in my browser and it looks to the browser a ssl site..
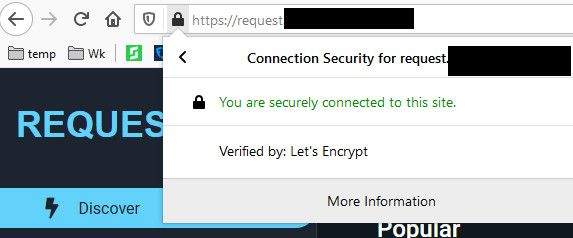
-
johnpoz,
The server does use SSL. When I access it by IP address, I use HTTPS. I just tried using HTTP, and that doesn't work.
Do you think my listening address is correct? It's the interface for the subnet that my computer is on. I've tried "any (IPv4)" in the past, and that didn't work, either. -
@stan said in HAProxy basic configuration issue:
I use HTTPS.
And what cert do you have installed there?
The IP your listening on would have to be the IP the fqdn your using points too. If your using some acme fqdn.. That for sure is not going to point to some rfc1918 IP unless you setup an override.
-
johnpoz,
The certificate on the server is just a self-signed certificate. That's why Chrome doesn't accept it as secure.
My LetsEncrypt certificate doesn't point anywhere. It's created with a DNS challenge, not a HTTP, etc. challenge. I don't have any port forwards in my firewall.
I do have an override set up for the server. Still, no dice.
Is there a setting somewhere else in pfSense that I need to worry about?
-
@stan said in HAProxy basic configuration issue:
My LetsEncrypt certificate doesn't point anywhere.
Yeah it does.. its what CN.. something.domain.tld - there is no way that you can get a acme unless the dns is valid publicly..
So yeah the acme resolves to something..
-
johnpoz,
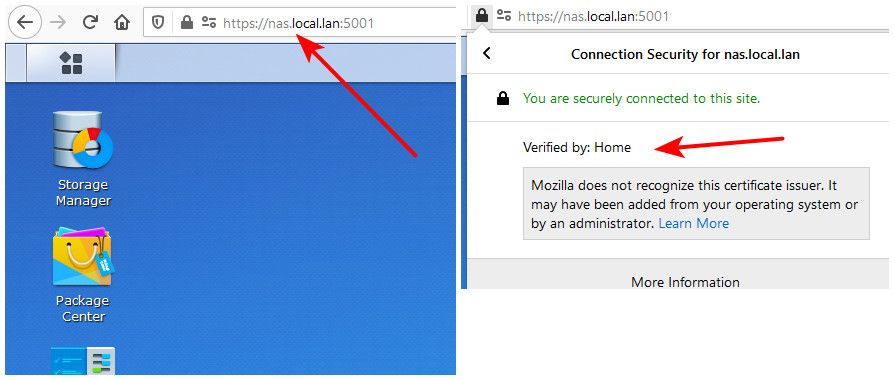
OK. Here's my ACME certificate.
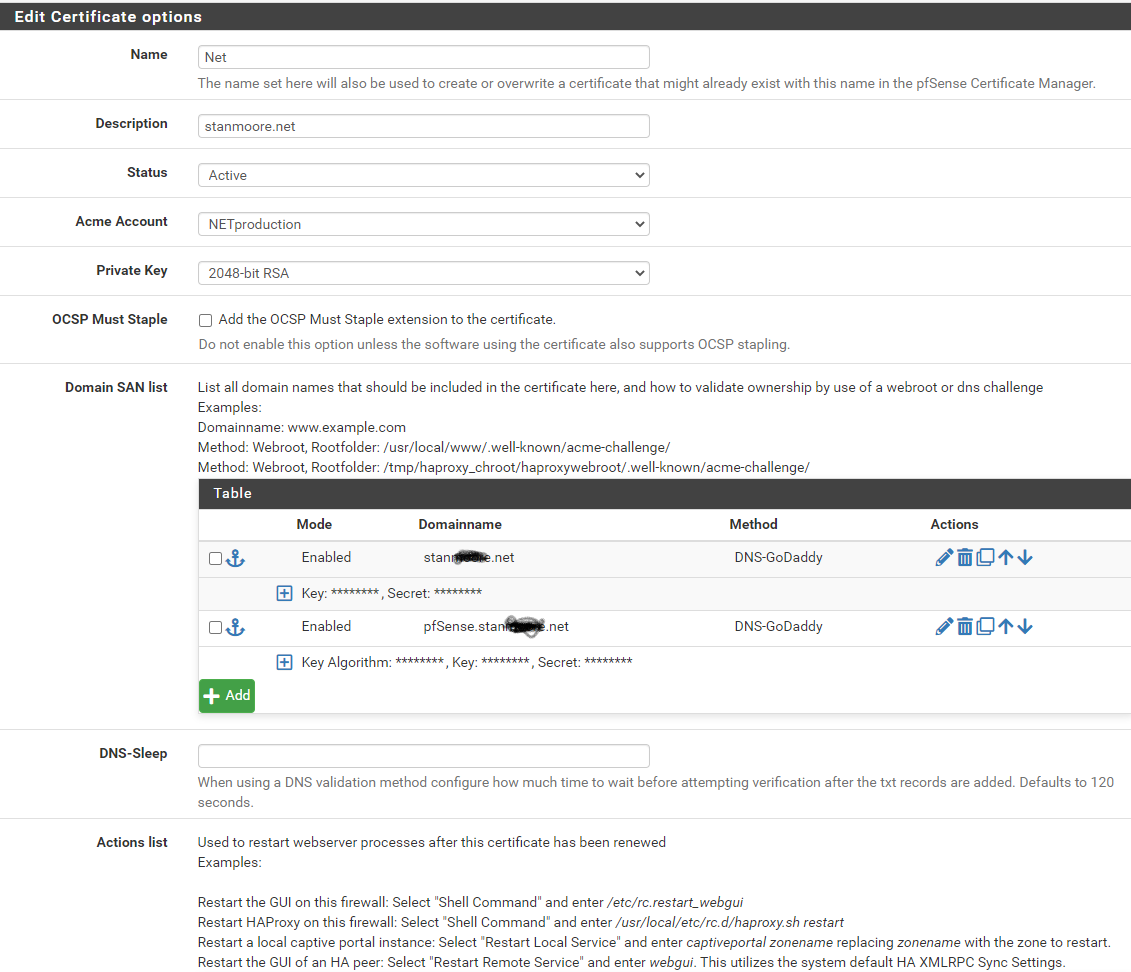
My pfSense address is xxx.xxx.8.1. I tried setting the listen address to the 8.1 interface and it still didn't work. Maybe you can tell something from this picture. -
My point
@stan ;; QUESTION SECTION: ;stanmore.net. IN A ;; ANSWER SECTION: stanmore.net. 86400 IN A 213.138.113.108$ dig pfsense.stanmore.net ; <<>> DiG 9.16.13 <<>> pfsense.stanmore.net ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 34405 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;pfsense.stanmore.net. IN A ;; ANSWER SECTION: pfsense.stanmore.net. 86400 IN A 213.138.113.108Is your LAN port your listening on that IP??
Oh you have 2 oo's -- that does not resolve.. How would you get there? So again you point that fqdn to your lan IP?? Your client has to resolve that fqdn to the IP your listening on..
And why would pfsense trust a self signed cert??
If all you want to do is get to some local server locally via a valid trust cert.. Why would you not just put that cert on the server.. You can sign a cert with a CA you create right in pfsense.. And use whatever domain you want, etc..
-
johnpoz, Thanks again for your attention to this. My A record just says "Parked" and when I open to edit, there is no IP address shown. I assume that 213.138.113.108 is just some address that GoDaddy uses for parked A records. It is not the external address either from my ISP or from my VPN provider.
I don't follow your comment: "Oh you have 2 oo's--that does not resolve". Maybe it doesn't matter.
Yes, "all I want to do is get to some local server locally via a valid trust cert." I haven't seen before the technique of creating a self-signed certificate in pfSense and placing that on the browser. I'll have to study your guide further to see if I can figure it out. I already have the LetsEncrypt cert on pfSense and was hoping just to use that.
One other fact that is probably important that I can't figure out is that I can't get to the FQDN address of the servers at all; it's not just a matter of the cert not being accepted by the browser. I do have DNSResolver registering DHCP leases and static mappings, so I thought the Resolver would pull up the server, but that's not happening. -
The two 00's - is your domain stanmore or stanmoore?
You leave your description open, and then you try and hide it in the domain name? So not sure.
if your server is 192.168.8.36
Then create a host override in pfsense to point whatever.domain.tld to this IP..
Create a CA, then create a cert with this CA. Trust the CA in your browser - and then use that cert on your server. Done.. NO proxy needs to be involved. Makes no sense to use the proxy unless you want outside people to get in, and to be honest you wan to offload the ssl to the proxy and not do it on the server.
I have a few guides around here about doing just that - let me see if can dig one up and link to it.
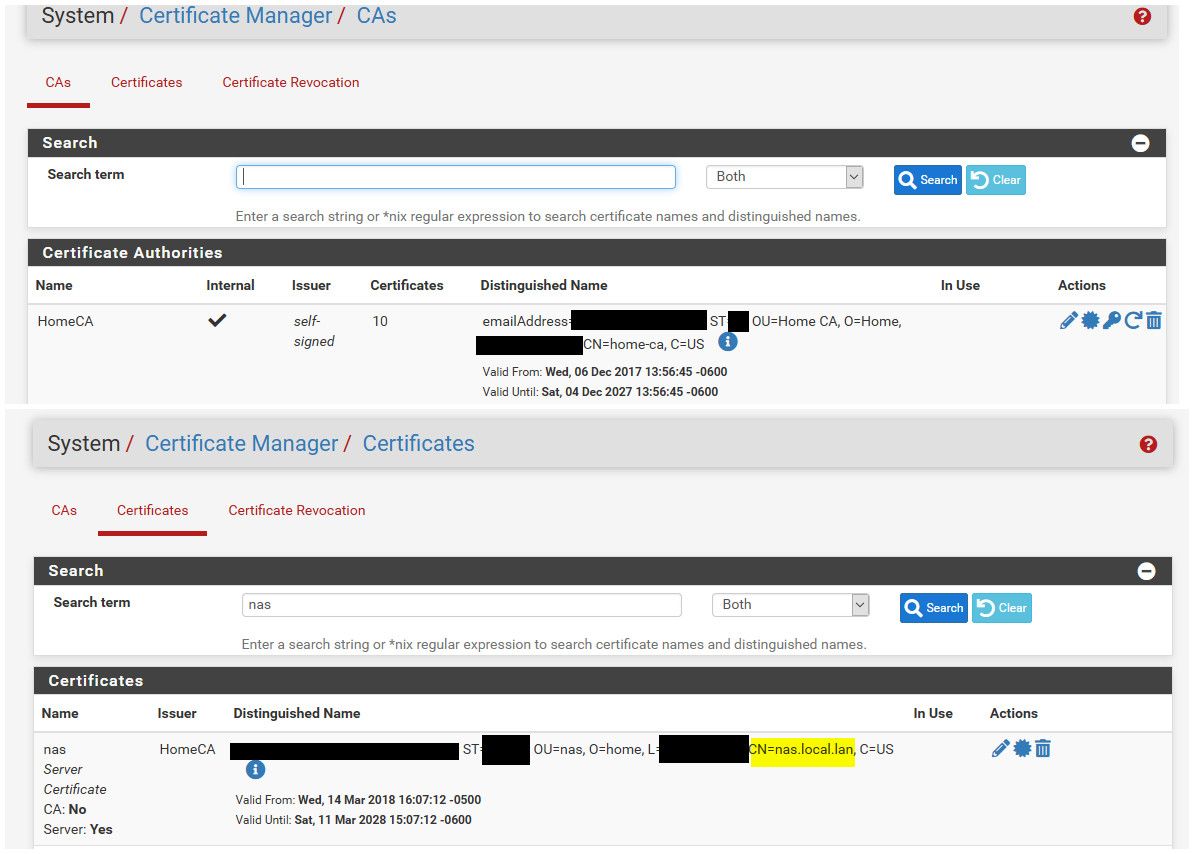
Here - walk through I did back in 2019
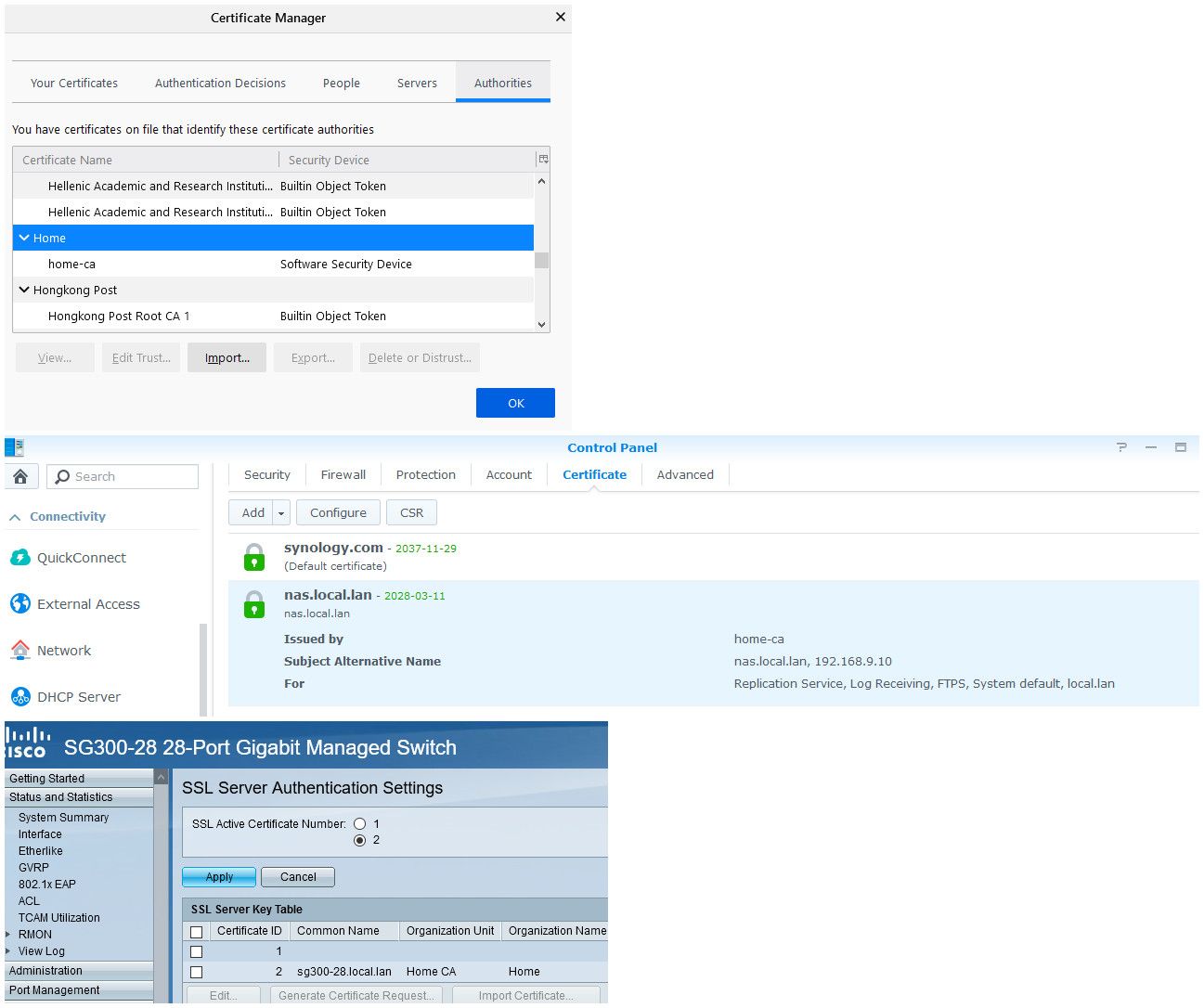
https://forum.netgate.com/post/831783edit: To finish that off.. Here is CA trusted by my browser.. And here are 2 devices using certs I signed with my trusted CA. Switch and Nas.
Keep in mind that browsers have backed off on how long a cert could be good for - not that long ago you could make then for like 10 years and be done with it. But now browsers can have issue certs valid longer than say 1 year
https://blog.mozilla.org/security/2020/07/09/reducing-tls-certificate-lifespans-to-398-days/
So for your certs you can only do them for that long - or your browser will complain - some of mine where done before those changes went into effect..
Other advantage of just doing it this way - is you can add in IPs into the certs via SAN, and then either name or IP works and your cert is trusted.
switch via name or ip
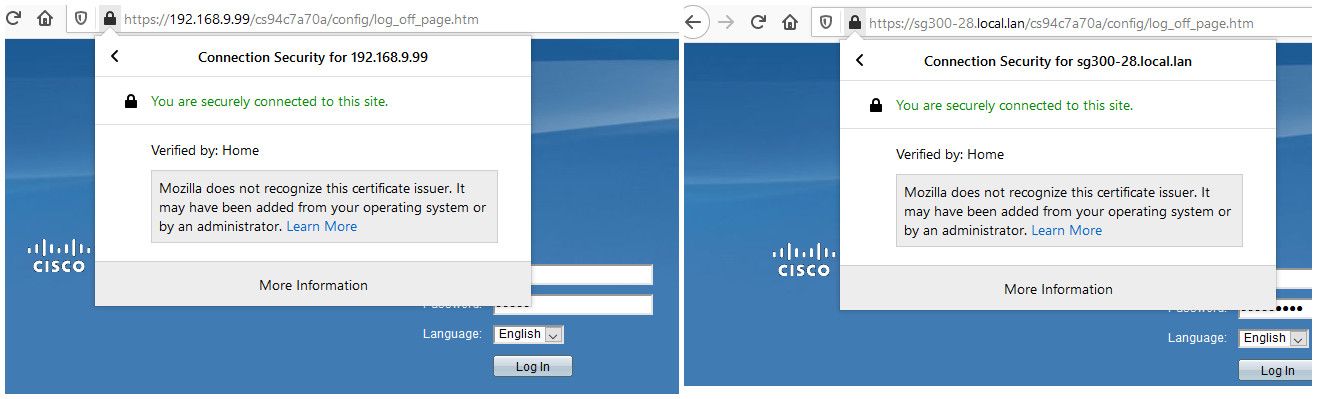
Notice in the cert for my nas above - its lists subject alternative names for nas.local.lan and 192.168.9.10