Understanding OpenVPN interface firewall tabs
-
I have two functioning site to site VPNs, one using my FIOS line, one using LTE as backup.
I use policy routing and failover gateway groups to direct traffic and I thought I understood it but I am stuck on interpreting firewall rules.
My specific question is which packets does:
- The openvpn tab control?
- The BB_OVPN (FIOS) tab control?
- The VPN_LTE tab control?
For testing, I placed a block all rule at the top of my BB_OVPN tab rules and cleared all existing states. I then tried to ping across from a remote machine behind the firewall at the remote site to a local machine behind the local firewall at the local site and it worked. Packet capture shows the packets come from the BB_OVPN interface.
Do I have to put all rules controlling which traffic can reach machines on the local side on the openvpn tab and ignore the interface specific tabs?
Thanks for teaching,
Devan
-
@ddbnj
An interface which you have assigned to an OpenVPN instance controls only incoming traffic of this specific instance.The OpenVPN tab is an implicitly added interface group which includes all OpenVPN instances which are running on pfSenses, either servers or clients. Therefor I use the term instance here.
It appears in pfSense as soon as you fire up the first OpenVPN instance.Accordingly to Ordering of NAT and Firewall Processing, rules on an interface group tab have priority over such ones on the interface tabs.
So since you have assigned interfaces to your vpn servers, you may move all rules from the OpenVPN to the interface tabs.
-
Thank you for your explanation. What you describe is my current understanding as well but I'm not seeing that behavior in my setup. I'm probably missing something.
Here are some screen shots of the local end of the site to site tunnel:
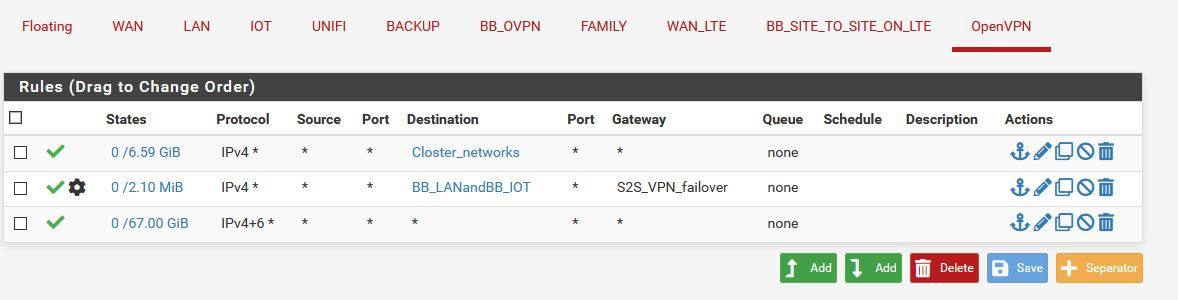
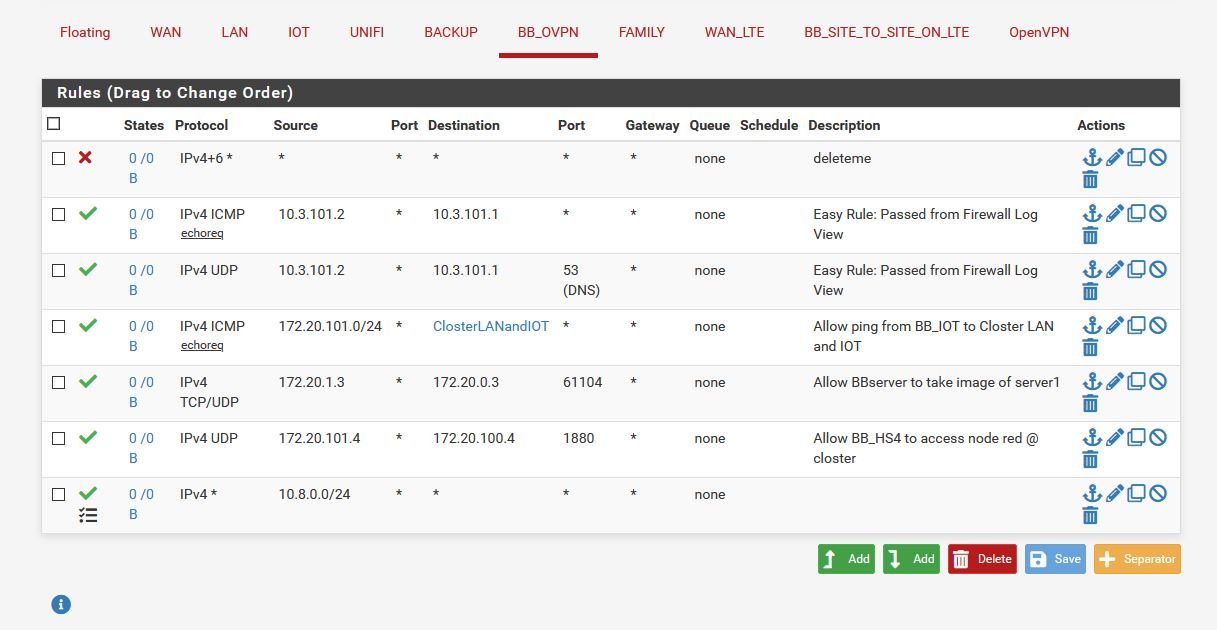
The block rule at the top was just for testing.
When I ping from a machine on the remote (172.20.101.4) to a local machine (172.20.0.3) this are the states created.
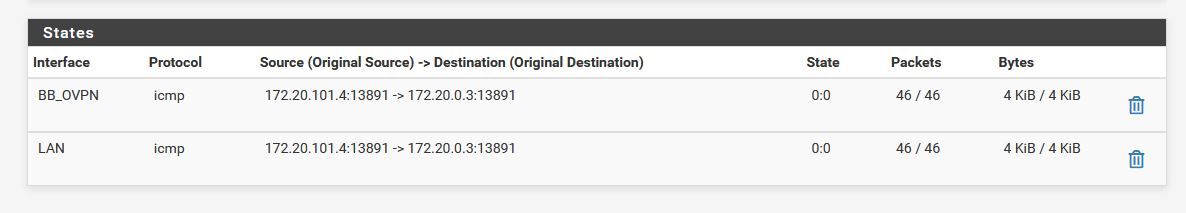
I'm not sure why my rules on the BB_OVPN are being bypassed. I started this investigation when I saw no states being reported on the firewall rules.
Any insight appreciated,
Devan
-
@ddbnj said in Understanding OpenVPN interface firewall tabs:
I'm not sure why my rules on the BB_OVPN are being bypassed.
Because there is a rule on the OpenVPN tab (the third one) allowing any to any, which is processed first.
-
Ahhh, so the rule hierarchy goes openvpn tab first. If no rules match the packet in openvpn, does the packet get dropped or does it now go to the interface tab?
-
@ddbnj
The OpenVPN is an interface group and groups a processed before interfaces as mentioned above.If no rule matches on the OpenVPN tab (and also none on the floating) it goes to the interface tab.
-
Thank you, the rules on the BB_OVPN tab are now being evaluated.
Last question. For site to site, is it best practice not to have any rules on the openvpn tab and instead place all rules on the respective interfaces?
-
@ddbnj
Basically it doesn't matter, where you add the rules, however if you have already assigned an interface, I'd prefere the interface tab. It's quite simpler.
For instance, if you add a block rule you can use any at source without affecting the other VPN instances.Furthermore if there is an incoming traffic from a public source on an OpenVPN interface (forwarded from the remote site) you have to care, that there is no rule on the OpenVPN tab mathing it. Otherwise responses are not routed back properly.