Only internet traffic rule suggestion
-
I have several networks. Two of which are a guest network and an IOT network. These networks should ONLY have access to the internet and nothing else. Instead of creating one block rule per network on the Guest and ITO section. Is there an easier way to do this? It is working, but I end up with several rules on each section. Maybe there is a way to consolidate this into one rule.
-
-
Thanks that works.
-
@mrjoli021
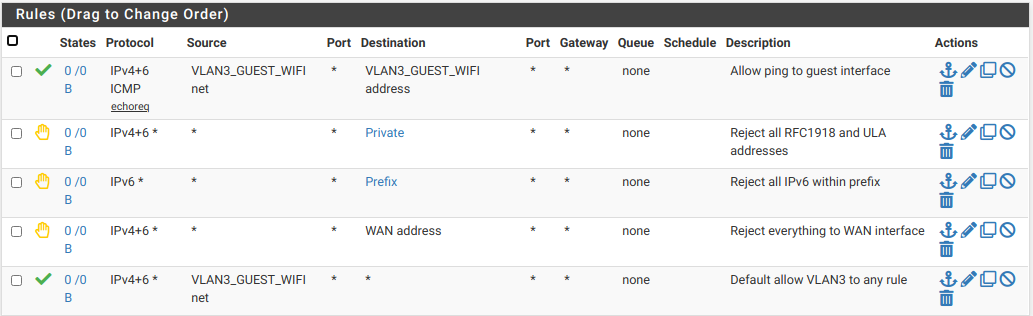
You can do it with only one flaoting rule if you want. If it should be applied before rules on the interface tabs check the "Quick" option.To be on the safe side, I use to add an alias which includes all RFC1918 (private) networks and use this as destination in the firewall rule.
So to only permit internet access to a subnet, in the pass rule I check "invert" at destination and enter the RFC1918 alias. So this rule allows access to any destination, but RFC1918 networks. And it still matches after adding a new network segment.
However, you may also use it in a block or reject rule. Rejecting access is basically useful to let the client know that he is rejected and there is no sense for further try. For IoT threre is no need, I think.Edit:
Quick option for floating rules -
-
In my rules I also allowed for my IPv6 prefix. I have a /56 prefix and one rule blocks it, as well as all ULA addresses, which where included in my Private alias.