OpenVPN Client Blocks All Traffic
-
Good afternoon,
I have setup an OpenVPN client with ProtonVPN. It connects and gets an IP. However, all traffic on my network no longer works. I have been able to get a since computer to work by forwarding it manually in the rules.
I am guessing that I have something else not setup correctly in my firewall as I have followed directions pretty closely.
I have an interface setup for it, I have looked at the rules and have very basic ones set (I have two groups, though, ProtonVPN (name I created) and OpenVPN).
Since I have pfsense in production for my home, I am unable to robustly test it as people are on the internet quite often. I am using seven interfaces: three physical ports, three vLANs, and one VPN.
My goal was to just get one computer (from just one interface) routed through the VPN for now and I have setup an alias to get that started. I am not trying to get all traffic to go through it.
Does anyone know of any great tutorials that will help me figure out what I am missing? I have walked through Tom Lawrence's YT video a couple of time and tried the ProtonVPN tutorial. I am on the latest version, 2.5.1.
Thank you!
-
@notahacker said in OpenVPN Client Blocks All Traffic:
I am guessing that I have something else not setup correctly in my firewall as I have followed directions pretty closely.
More detail about your setup would help to check out.
Basically activating a VPN client does nothing with your existing rules, but only routing.
Most VPN provider push the default rule to you, so that any upstream traffic goes out to the vpn.
To avoid this go in to the client settings and check "Don't pull routes".If that was the case your internet traffic should word again even when the client is connected. If you only want to direct partial traffic over the vpn this is the configuration to use anyway and route the vpn traffic by policy routing rules.
For routing the traffic over the vpn, I guess, you're missing the correct outbound NAT rule.
-
I am not sure what information would be the most helpful. I am running pfsense on a protectli vault FW6E. I setup the Certificates using the downloaded file from ProntonVPN. I did not have "Don't pull routes" checked, but I can try that at some later point.
The custom options that the VPN said I should add are:
tun-mtu 1500; tun-mtu-extra 32; mssfix 1450; persist-key; persist-tun; reneg-sec 0; remote-cert-tls server; pull;I believe the rest was pretty much the standard setup.
I tried adding the Outbound NAT rule to one interface, but it did not work. It is possible I did not restart the openvpn service, though.
The most frustrating part is that the internet for all devices goes down as soon as I start the VPN. This makes it so that I am not able to work on it during regular hours (roommate loves their gaming/YT!).
My Firewall Rules are just blocking bogon networks and allowing all traffic under PROTONVPN and OpenVPN does not have anything at this time.
Thank you so much for your reply.
-
@notahacker said in OpenVPN Client Blocks All Traffic:
The custom options that the VPN said I should add are:
Where did you get this suggested from???
Normally there are no advanced options to set as long as you don't have a true reason for each.
Won't discuss each now, but at least remove the "pull"! This one blocks "Don't pull".@notahacker said in OpenVPN Client Blocks All Traffic:
I tried adding the Outbound NAT rule to one interface, but it did not work
As you mentioned you have assigned an interface to the client instance (don't know if you did correctly, since missing detailed infos). You have to add the outbound NAT rule to this interface.
-
@viragomann said in OpenVPN Client Blocks All Traffic:
Where did you get this suggested from???
I used the tutorial on the ProtonVPN site. A lot of it I understood, but I did not look very far into understanding what the custom options were doing. I will remove the "pull".
@viragomann said in OpenVPN Client Blocks All Traffic:
As you mentioned you have assigned an interface to the client instance (don't know if you did correctly, since missing detailed infos). You have to add the outbound NAT rule to this interface.
Here is my interface:
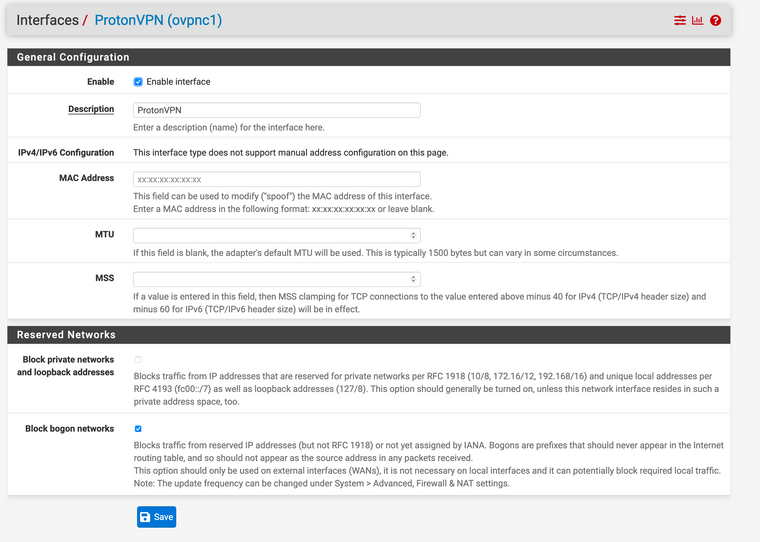
Here is my outbound NAT:
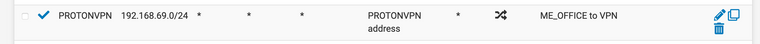
Unfortunately, I am not quite sure what detailed information would be the most useful to troubleshoot this situation.
Thanks.
-
Well, it looks like I was able to get it to work. Seems the "pull" within the custom options was the issue. Now I just need to figure out how to get a DNS server working for the one computer I am routing through the VPN. I can ping IPs and it is noticeably longer than when pinging without the VPN. However, sites will not load. Locally, I am using a PiHole for DNS.
I believe there must be a custom option I can include for a DNS server, I just have not found that yet.
Thank you for the "pull" catch!!
-
@notahacker
The policy routing rule directs any matching traffic to the VPN server.
So this will also include DNS, however, your computer might been configured to use the PiHole for name resolution.So if you want to use your PiHole on this machine you have to add an additional firewall rule without a stated gateway above of the policy routing to allow the DNS access.
However, this will result in DNS leaks, cause with this the DNS goes out the WAN interface.
You can only avoid DNS leaks by directing DNS requests from the concerned computer over the VPN.