WireGuard lives!
-
@psp Thanks for the update!
-
Waiting anxiously for tutorial and easy installation option. However don’t rush it, we all know how that goes
 .
. -
I'm wondering if it's a simple matter to just scp the 4 package files over and then run pkg on each one to install them, then reboot?
-
Yup that is it.. I like to install them in the order of dependency.
wireguard-kmod, bash, wireguard-tools and then pkg-Wireguard. With the latest kmod we are seeing some KPs and other wierdness. So remeber this is experimental. don't run on prod and backup before you make any chagnes.
-
I cant get it to work.
I am not even sure if its connecting and i am not sure how the NAT should be configured so that all traffic goes via wireguard as it no longer makes a gateway.
Kind Regards,
Chris -
@chrisjmuk so you’ll need to create your own gateway entry manually, and then policy route over it as usual
-
@theonemcdonald i know how to create the gateway and set the rule in the firewall to go to the specific gateway, or am i missing something else?
-
@chrisjmuk What VPN provider are you using?
-
Mullvad VPN - used before on pfSense 1.5.1 Dev
These are my settings - i have removed the keys on purpose and will change.
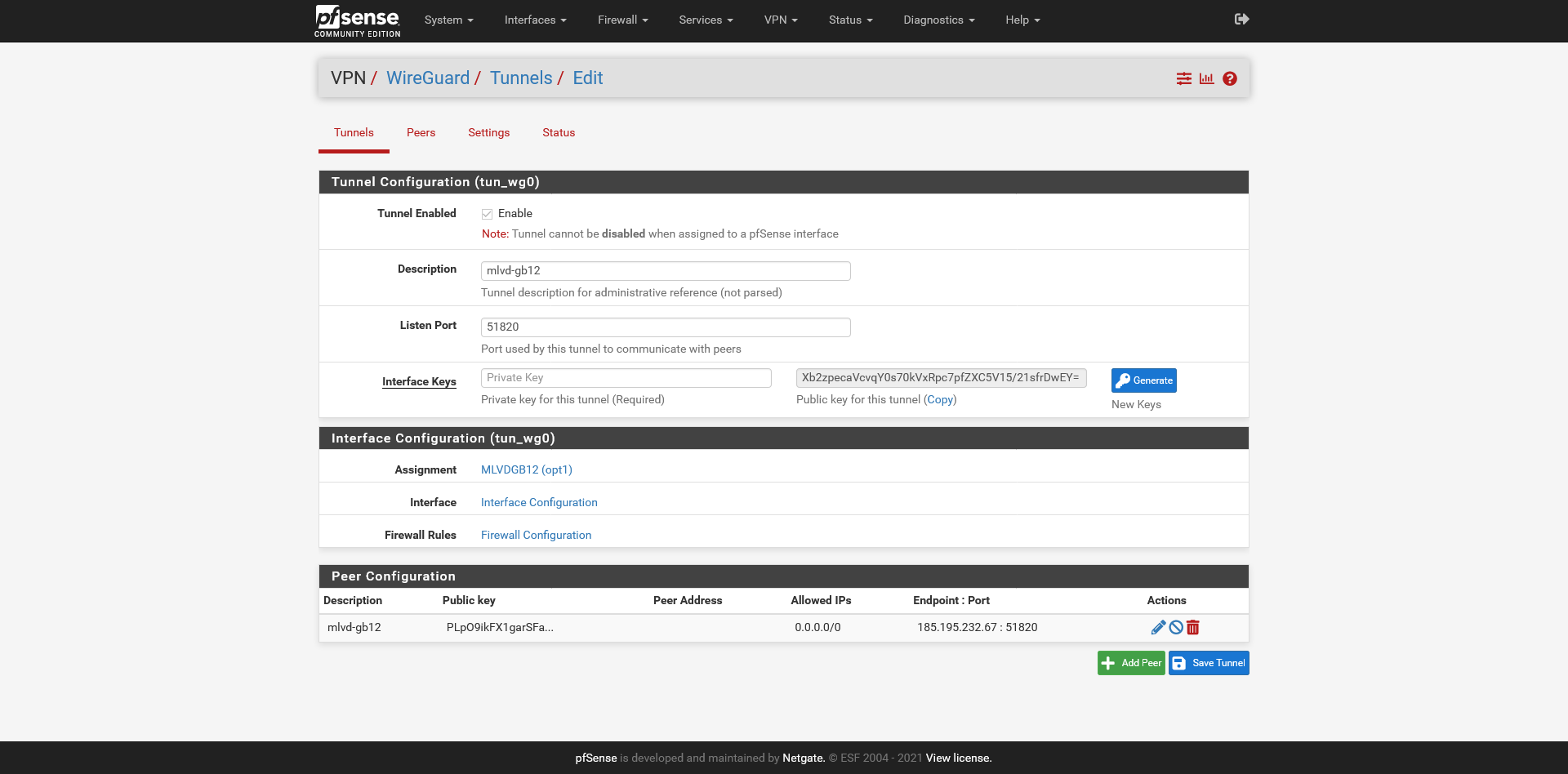
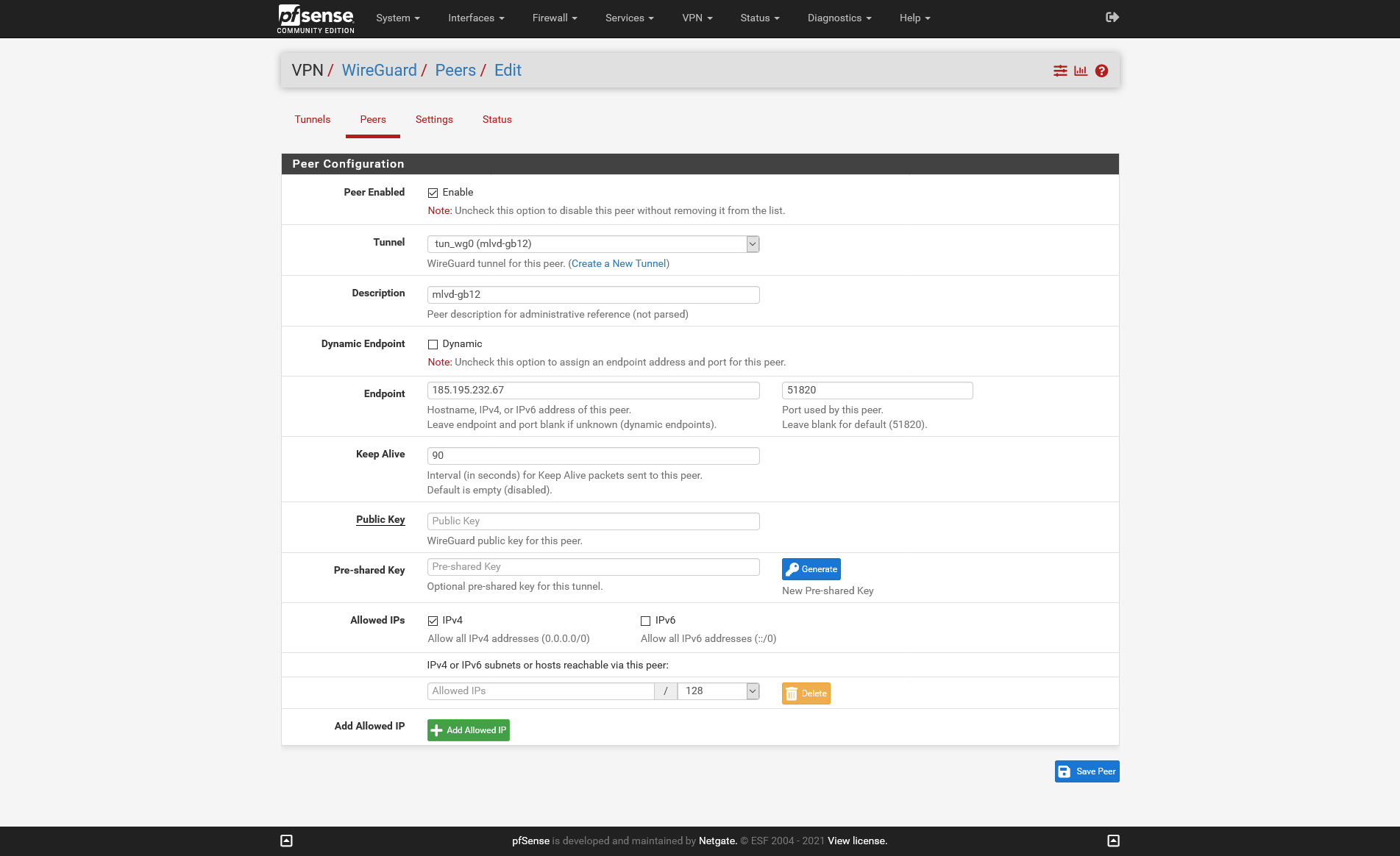
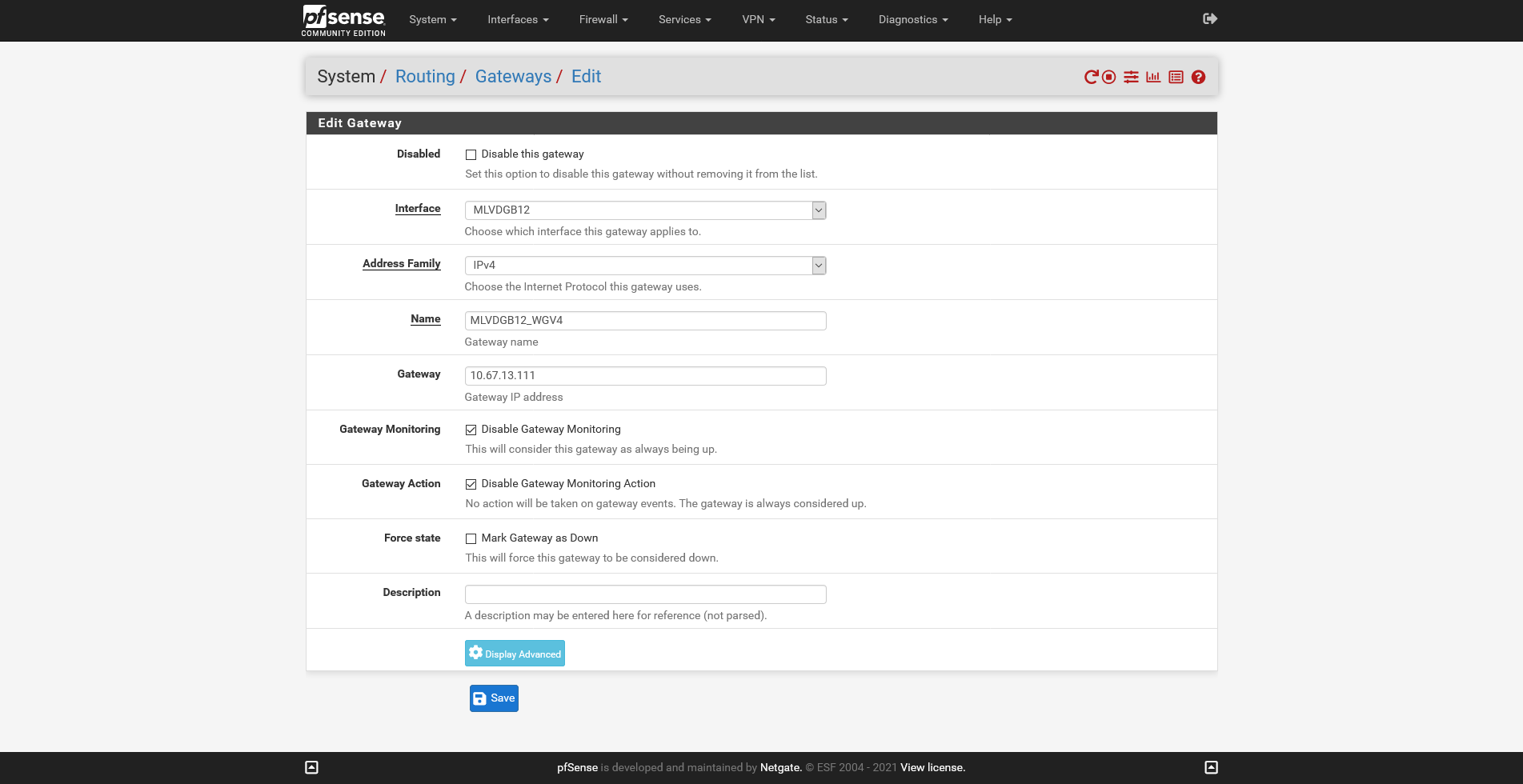
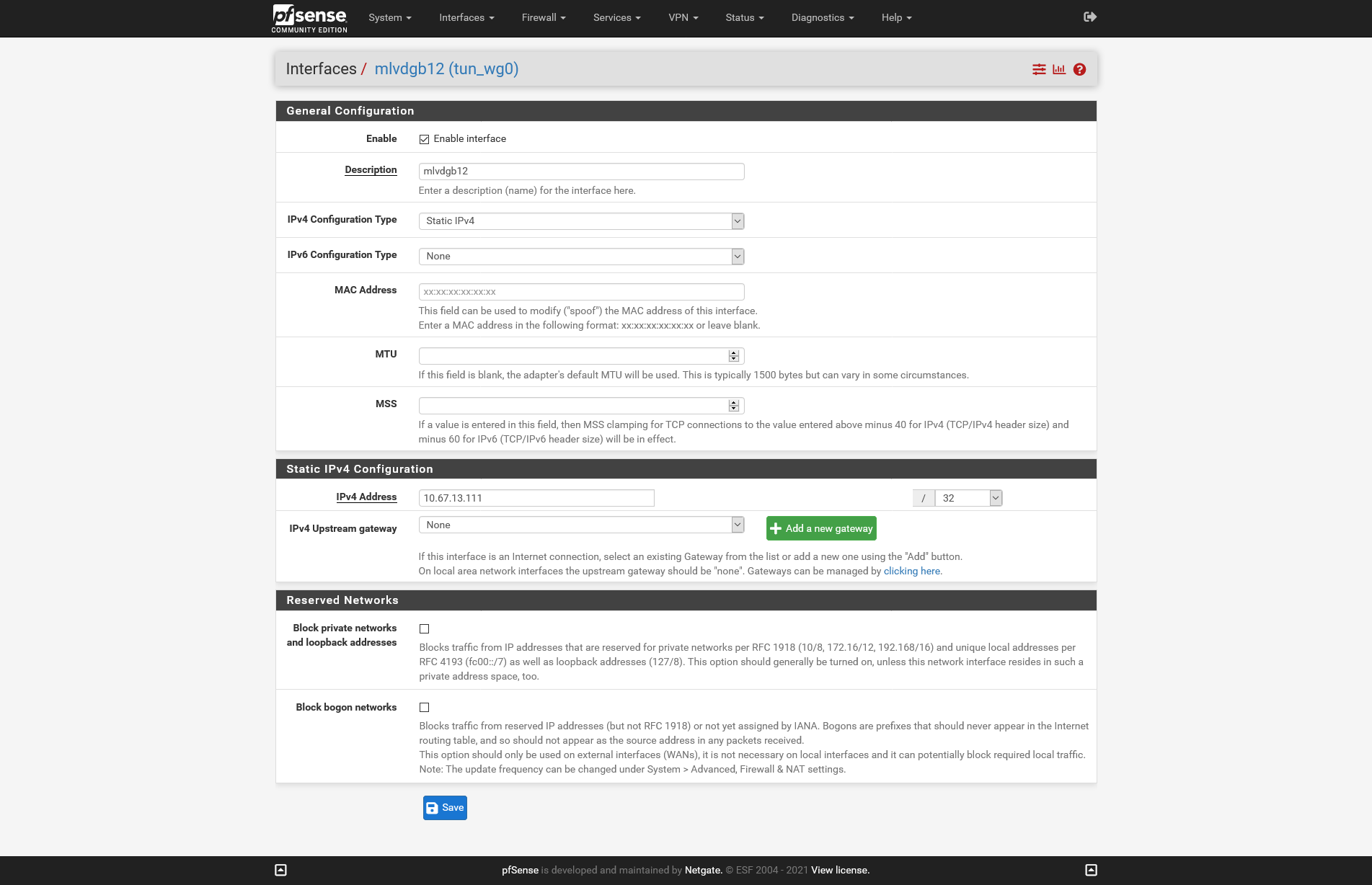
-
@chrisjmuk I will get a mullvad subscription to test
-
@theonemcdonald its free for 24 hours.
also getting this error
Crash report begins. Anonymous machine information: amd64 12.2-STABLE FreeBSD 12.2-STABLE devel-12-n226623-ba553ae641b5 pfSense Crash report details: PHP Errors: [05-May-2021 14:07:00 Etc/UTC] PHP Warning: Invalid argument supplied for foreach() in /usr/local/www/wg/vpn_wg_peers_edit.php on line 259 No FreeBSD crash data found. -
@chrisjmuk This has been fixed, will be in the next release.
-
For anyone having issues with Mullad,
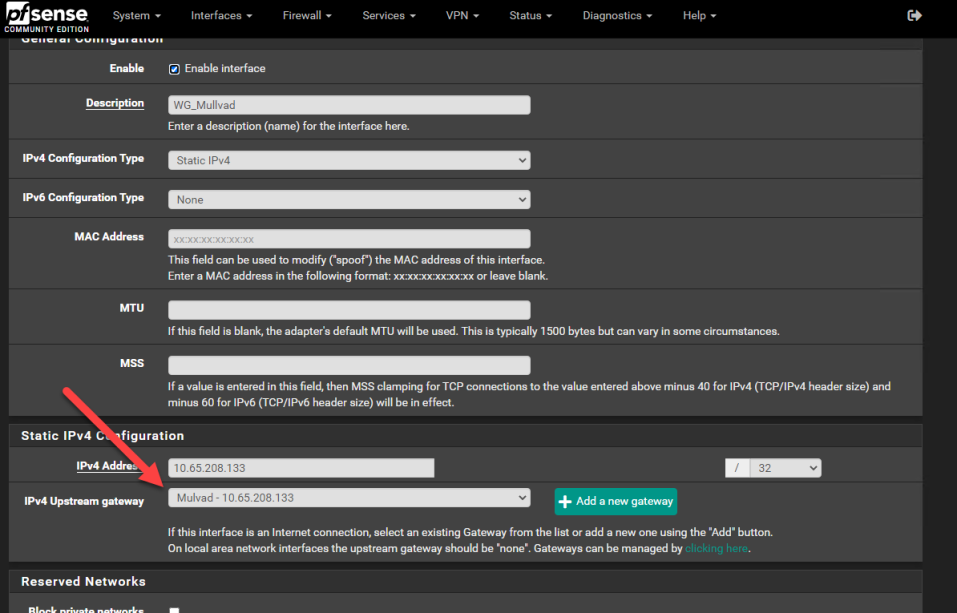
Make sure your gateway is the same as your interface address
-
@theonemcdonald still no luck unfortuantly on my side. are you able to give me a quick message?
-
@chrisjmuk I just get got it setup and working fine.
Here is what I did.
- download zip file for the config from mullvad
- create tunnels and peers. (the conf in the zip file contains the tunnel private key, and public key for peer, the pfsense ui will generate the tunnel public key automatically)
- create interface MULL_WG with Interface Address 10.x.x.x/32, create a gateway at the same time for that same IP.
- create outbound NAT, set interface to MULL_WG and source / dest to any
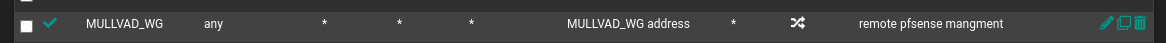
- firewall rules to do policy based routing.
-
@vajonam Thank you, that done the trick - all working now, i will set my self as a regular sponsor for your github.
-
Hi! I setup pfSense 2.6 on my Hyper-V lab and was able to get setup a Wireguard tunnel with TorGuard. Looks promising! I did notice a little more cpu load then I expected when running speedtests but I was able to utilize my 100Mbit internet connection.
WGTUN Interface (opt1, tun_wg0) Status up IPv4 Address 10.13.XX.XX Subnet mask IPv4 255.255.255.0 Gateway IPv4 10.13.XX.XX MTU 1500 In/out packets 509239/443583 (536.63 MiB/360.12 MiB) In/out packets (pass) 509239/443583 (536.63 MiB/360.12 MiB) In/out packets (block) 0/0 (0 B/0 B) In/out errors 0/0 Collisions 0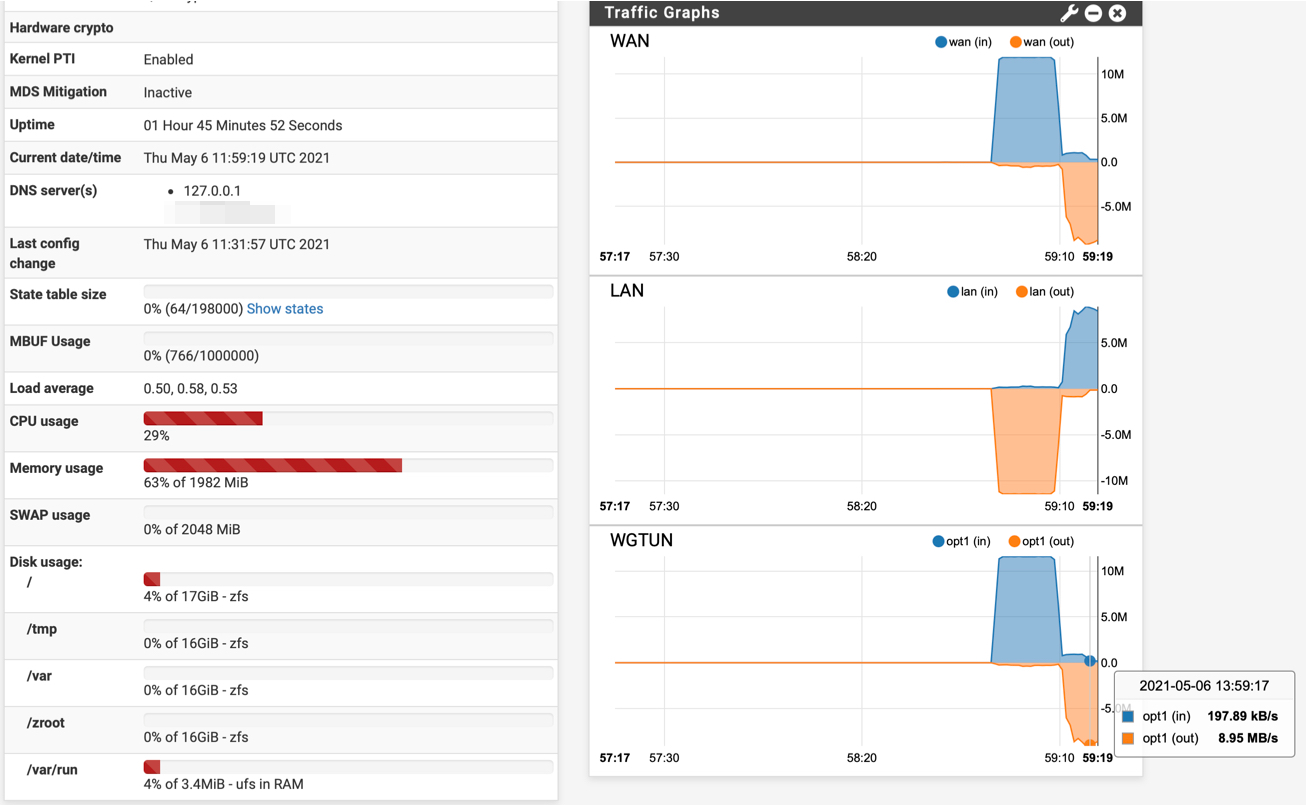
-
@vjizzle There is still optimization gains to be realized yet in the kernel module...primarily around the crypto. We will track all ongoing development on all fronts to keep this fresh and current. Stay tuned
-
@theonemcdonald Hi! Just to clarify, will this be available in pfSense 2.5.1 Package Manager ?
-
@emikaadeo said in WireGuard lives!:
@theonemcdonald Hi! Just to clarify, will this be available in pfSense 2.5.1 Package Manager ?
Not currently as it's not recommended for stable. So if you want to run it on 2.5.x, download the packages from GitHub and install it manually.