WireGuard lives!
-
I've been using wireguard on '2.5.1-RELEASE (amd64)' since v0.0.8 was released, upgrading every time a new release was added. Updated yesterday from v0.1.2_6 to v0.1.3. This where I stand at the moment:
- pfSense-pkg-WireGuard 0.1.3
wireguard-kmod 0.0.20210606
wireguard-tools-lite 1.0.20210424
One issue I've noticed since doing yesterday's update is shown as follows (Public key removed from the image, all else is as appears, sans the red eclipse ... of course!). This is from 2.5.1's menu: 'Status|Wireguard|Tunnels' and clicking on 'Show Peers' button. Possibly this is because I'm using 2.5.1? idk?
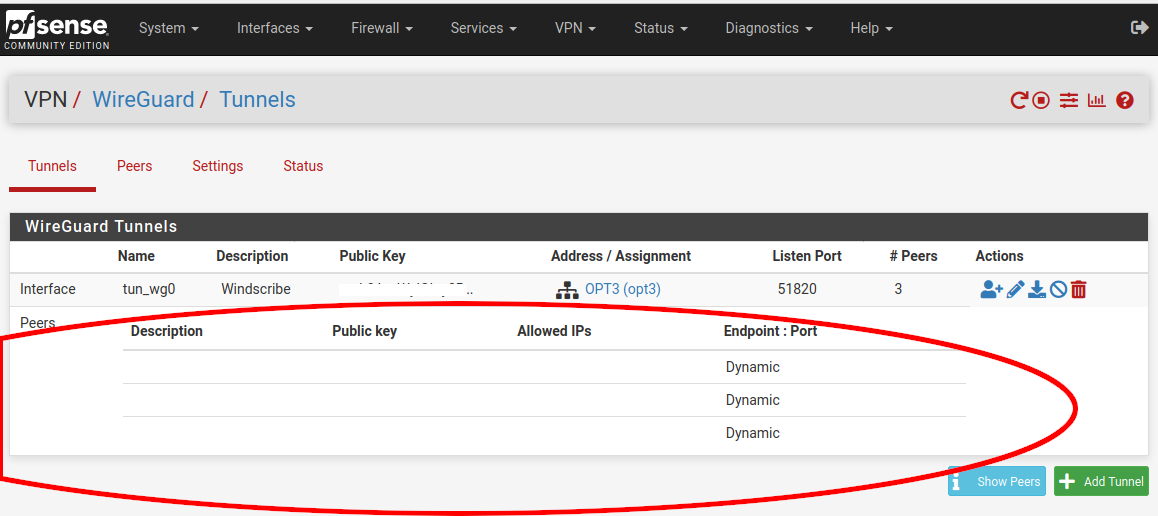
This seems cosmetic since my wireguard connect in pfsense continues to work without issues.
In the 'Status' window the 'Peers' show as expected (again, keys and endpoint:ports removed by me from this image).
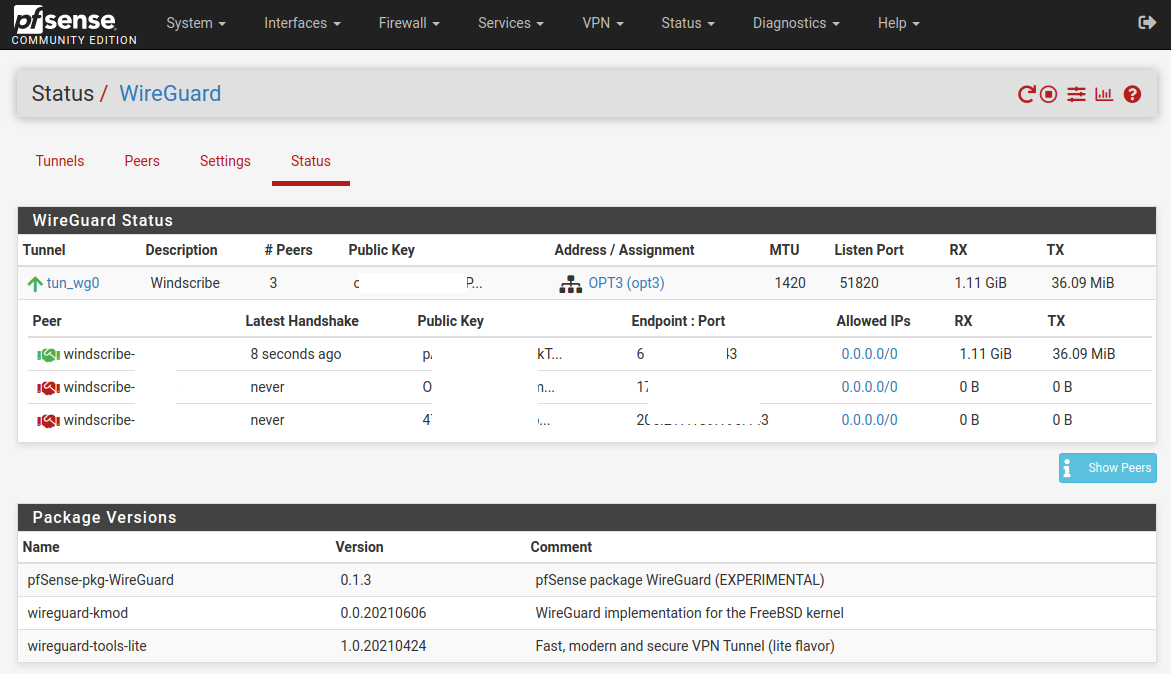
.
- pfSense-pkg-WireGuard 0.1.3
-
Hi! I am running wireguard on 2.5.2 rc. I have no tunnels configured because this system is running in a virtual machine on my homelab.
After upgrading to the latest version of wireguard I still see these errors:
Crash report begins. Anonymous machine information:
amd64
12.2-STABLE
FreeBSD 12.2-STABLE RELENG_2_5_2-n226661-b1c18988dca pfSenseCrash report details:
PHP Errors:
[24-Jun-2021 11:28:59 Europe/Amsterdam] PHP Warning: flock() expects parameter 1 to be resource, null given in /usr/local/pkg/wireguard/wg_service.inc on line 324
[24-Jun-2021 11:28:59 Europe/Amsterdam] PHP Warning: fclose() expects parameter 1 to be resource, null given in /usr/local/pkg/wireguard/wg_service.inc on line 327
[24-Jun-2021 11:29:19 Europe/Amsterdam] PHP Warning: flock() expects parameter 1 to be resource, null given in /usr/local/pkg/wireguard/wg_service.inc on line 324
[24-Jun-2021 11:29:19 Europe/Amsterdam] PHP Warning: fclose() expects parameter 1 to be resource, null given in /usr/local/pkg/wireguard/wg_service.inc on line 327No FreeBSD crash data found.
I hope this is all cosmetic but please let me know if I can help troubleshoot this.
-
@vjizzle Fix for this is included in the latest release which was accepted yesterday. It should be available very soon
-
@theonemcdonald i'm missing the routing overview inside the status view wt 0.1.3
-
And what is about to add routes to allowed networks automatically?
-
@dersch That was backed out until a more suitable overall solution for routes is built. Right now, you will need to either a) use a dynamic routing protocol or b) create static routes to direct traffic out a certain WG tunnel interface. This is being worked on
-
@theonemcdonald Is your repo still working? Got some issues with checking updates https://forum.netgate.com/post/989073
-
@emikaadeo the guys who maintain that are working on it. But the repo is indeed down atm. My recommendation would be to uninstall that custom repo and either a) side-load or b) get the code from Netgate's repo. Now that things are settling down a bit with the code and design, expect more frequent updates from the official Netgate repository.
-
@theonemcdonald said in WireGuard lives!:
@emikaadeo the guys who maintain that are working on it. But the repo is indeed down atm. My recommendation would be to uninstall that custom repo and either a) side-load or b) get the code from Netgate's repo. Now that things are settling down a bit with the code and design, expect more frequent updates from the official Netgate repository.
Is there another method to uninstall this custom repo since this one doesn't work?
https://github.com/theonemcdonald/pfSense-pkg-WireGuard/wiki/Installationcurl -s https://packages.mced.tech/install/remove_repo.sh | sh -
mv /etc/inc/pkg-utils.inc.orig /etc/inc/pkg-utils.inc rm /usr/local/etc/pkg/repos/*WireGuard.conf rm /usr/local/etc/ssl/wireguard.crt pkg update -
@theonemcdonald said in WireGuard lives!:
mv /etc/inc/pkg-utils.inc.orig /etc/inc/pkg-utils.inc rm /usr/local/etc/pkg/repos/*WireGuard.conf rm /usr/local/etc/ssl/wireguard.crt pkg updateWorks, Thanks!
-
@theonemcdonald thanks for your work on this.
-
Dear @theonemcdonald and all here,
Thanks for the package it works great. I am running 2.5.2 RC with no issues. Just a couple of questions. 1 - Will there be any work / development done so that the pfSense firewall can reboot and the WireGuard connection remains constant ? As it stands now - I have to set the default gateway to " Automatic " when rebooting. Just asking.
Two - Can anyone / somebody / anybody tell me how to install 2.6.0 development snapshot on a virtual machine. I get to a login after the installer runs - and that is where I get stuck. Further, the lan network does not seem to be able to dish out a connection from which to log into the webgui. Any assistance will be greatly appreciated.
Peace Unto All -
@ubernupe I reboot my development boxes multiple times per day and my WireGuard connections come right up. As for 2.6.0, there is a bug currently that is causing the installer to not work correctly. Install 2.5.1 and "upgrade" to 2.6.0 should avoid any bugs with the installer.
-
@theonemcdonald
Thanks for your swift and detailed reply. I appreciate the heads up about the bug in the 2.6.0 installer. I set up my firewall rules as you detailed for MULLVAD in earlier post found here :https://forum.netgate.com/topic/163133/wireguard-lives/22
So, am I doing anything which causes my firewall to be unable to sustain WireGuard connection on reboot ? I thank you for your hard work and dedication to this project.
Peace and Happy Fourth -
I'd like to install wireguard, however the version available in Package Manager is 0.1.5._3 instead of 1.6, plus the instructions on the Wiki in the Github page don't work as there doesn't appear to be a script at packages.mced.tech. I see the three pkg files under the release. Is it just a matter of installing them manually or is there an updated set of installation instructions I should use?
-
@slim0287 that repository is no longer active because the project is now sponsored and maintained in-house. v0.1.6 is available in 22.01/2.6RC branches. There is a UI dependency that makes v0.1.6 incompatible with older versions of pfSense. I’d recommend giving the release candidates a try, they are quite close to GA.
-
 C cmcdonald locked this topic on
C cmcdonald locked this topic on