OpenVPN Server Behind NAT being blocked by Firewall Rule
-
Hi all,
I am trying to set up an OpenVPN server behind another router. Setup looks something like this:
[Internet] <-> [Router] <-> [PFSense]The [Router] has the VPN port port-forwarded, so a connection can be established from outside the network.
I have tested the VPN connection from the [Router] network into the [PFSense] network and it is working fine (has internet access and internal network access).
When I access the VPN server from the internet, I am able to establish a connection. However, all outbound traffic is being blocked by a firewall rule for an interface that is setup for a client VPN connection.
The OpenVPN log says this:
client/123.123.123.123:12345 write TCPv4_SERVER: Permission denied (code=13)I checked the firewall log to see why this is occuring:
Apr 21 16:29:11 ► CLIENT_VPN Default deny rule IPv4 (1000000104) 192.168.0.100:1194 123.123.123.123:12345 TCP:FPAIn this case,
192.168.0.100:1194would be the WAN address for my pfsense box and123.123.123.123:12345would be the client trying to access the VPN. TheCLIENT_VPNis a client VPN connection that is being used for other outbound traffic. I would have expected the OpenVPN Server to use the default gateway, which isWAN.I reviewed my firewall rules and tried to set up some rules to force all outbound traffic to use the
WANgateway and also set up the Outbound NAT for the OpenVPN Server: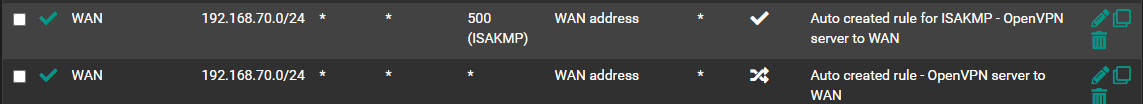
I tried to set up policy based routing documented here:
https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/assign.htmlHowever, my attempt to force the OpenVPN to use the
WANinterface didn't work. Any help on this would be appreciated.Thanks,
-D -
@preimmortal said in OpenVPN Server Behind NAT being blocked by Firewall Rule:
I checked the firewall log to see why this is occuring:
Apr 21 16:29:11 ► CLIENT_VPN Default deny rule IPv4 (1000000104) 192.168.0.100:1194 123.123.123.123:12345 TCP:FPA
In this case, 192.168.0.100:1194 would be the WAN address for my pfsense box and 123.123.123.123:12345 would be the client trying to access the VPN. The CLIENT_VPN is a client VPN connection that is being used for other outbound traffic. I would have expected the OpenVPN Server to use the default gateway, which is WANBasically respond packets are routed accordingly to the routing table if the incoming interface of the requests is unclear.
I suspect that the other client connection set the default route, presumably pushed by the server.I reviewed my firewall rules and tried to set up some rules to force all outbound traffic to use the WAN gateway and also set up the Outbound NAT for the OpenVPN Server:
Outbound NAT rules have no affect on respond packets.
I tried to set up policy based routing documented here:
Not clear what you aim to achieve with that in this case.
Simply ensure that there is a firewall rule on the WAN interface allowing the OpenVPN access on port 1194, ensure that there is no floating rule or interface group rule matching this traffic.