Site to site clients of client side cannot reach server (solved)
-
I am sorry I have to bother to ask this but after weeks I can't figure this out.
I have a site to site setup, site A is the server (pfsense 2.5.1), site B is the client (pfsense+21.02.2).
All clients behind Site A (server) can reach Site B firewall and clients behind Site B.
Site B firewall can reach Site A server and site A clients.
Using pfsense+ firewall ping webgui:
If I ping Site A from Site B's LAN interface and IOT interfaces it works.
If I ping Site A from Site B's openvpn mobile clients interface it does not work.
I have identical firewall rules for LAN, IOT, and openvpn clients.
Does anyone know why the openvpn mobile client interface is treated differently? I think I need a client specific overide but I don't really know why.
If I packet capture ping attempts from the Site B firewall to the Site A firewall on the openvpn client interface, no packets enter the tunnel:
10:27:07.790622 IP 10.8.1.1 > 172.20.0.1: ICMP echo request, id 12100, seq 0, length 64 10:27:08.793535 IP 10.8.1.1 > 172.20.0.1: ICMP echo request, id 12100, seq 1, length 64 10:27:09.812040 IP 10.8.1.1 > 172.20.0.1: ICMP echo request, id 12100, seq 2, length 64Both ends of the tunnel do not receive the request packets from 10.8.1.1
Here are the rules on the openvpn mobile client interface.
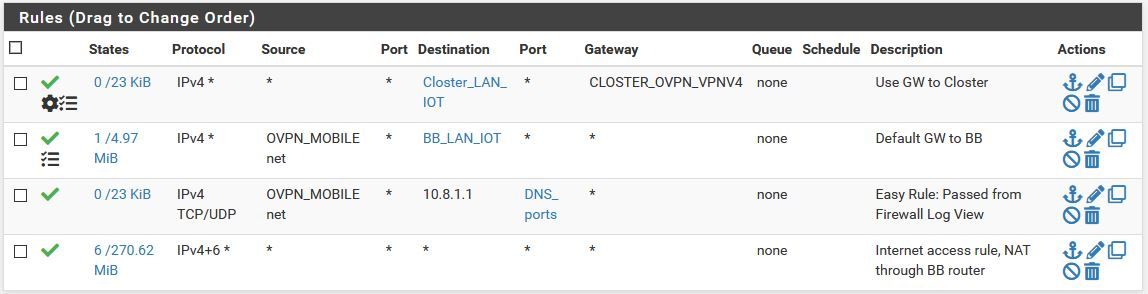
There are no firewall log entries for the ICMP packets. DNS requests across the tunnel are logged.
Any help appreciated.
Thank you,
Devan
-
Is your site B's OpenVPN Client network (lan) defined in the Site A routing table ?
If the SiteB OpenVPN Client Lan is not known at Site A , then Site A ansvers wont be routed to Site B.
/Bingo
-
Are you using OpenVPN between SiteA and SiteB too or ?
I'm using SSL/TLS /30 OpenVPN L2L tunnels.
I have a feeling that the below might just fit there.In a setup like mine , you would normally define the remote networks in the OpenVPN Server or Client definitions.
Here (on Site A definitions) , i would have had to enter the networks that can be "reached" on the remote end (Site B) , and that would have to include ANY networks on SiteB , including a OpenVPN "Dial-in" client network.
/Bingo
-
First, thank you.
I believe the routes are correct. Here are the relevant routes from Site A.
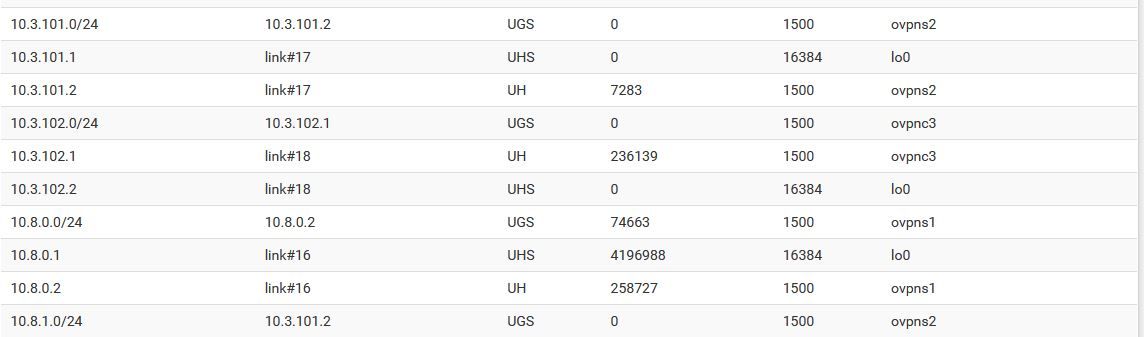
10.8.1.0/24 are the openvpn mobile clients connecting to Site B
10.3.101.0/24 is the openvpn tunnel over fiber optic (server)
10.3.102.0/24 is the openvpn tunnel over LTE behind NAT (client/failover)Here are relevant routes from Site B:
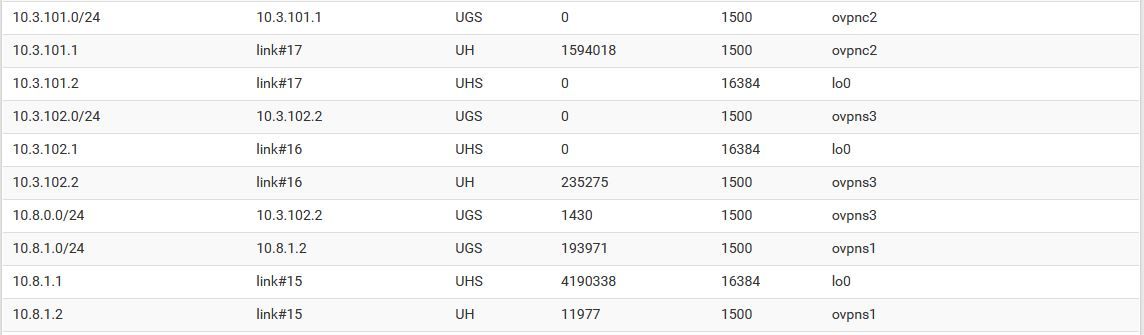

The 10.8.1.0/24 clients are listed in the remote networks available on the server setup for the OpenVPN tunnel.
Thank you,
Devan
-
I believe they are set correctly:
Site A OpenVPN server setting for site to site connection to Site B:
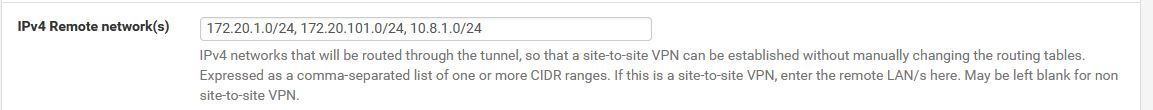
Related CSO entry on same firewall:
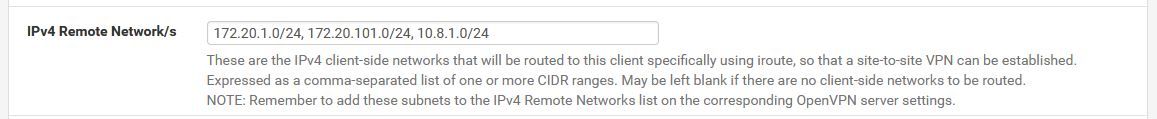
-
@ddbnj
I hope the 172.x.x.x net is in the SiteA routing table too , as it seems to reside there. But the CSO seems to indicate the 172 net is on Site B , where is it ?.But you are correct , the routing table seems to include the 10.8.1.0/24 on both ends.
Can you ping the "opposite" openvpn (L2L) interface from SiteB , and from a SiteB client ?
-
After many weeks and hours I figured it out.
@jimp posted in another thread titled OpenVPN fails with 2.50
Make sure your default gateway is set to your WAN gateway on System > Routing
Try setting the OpenVPN server Protocol value to "UDP IPv4 and IPv6 on all interfaces (multihome)"When I set Site A OpenVPN server protocol to multihome it works! I don't have any IPv6 interfaces so I never picked it. MultiWAN is a huge pain in the ass.
What a battle.
Thank you @bingo600 for helping me.
Devan
-
@ddbnj
Nice to have "helped" ... Or NOT
Glad i'm still on 2.4.5-p1 , and not chasing "ghosts"/Bingo