Firewall Blocking 445 from one vlan to another
-
I've had this setup for several years and the config has not changed much but with 2.5 and 2.5.1 my firewall began blocking smb between vlans.
Setup
Pfsense
3550 Cisco
4 Vlans 10, 20,30, and 40
Unraid server on vlan 10
work station on vlan 30
Aliases Local_Subnet 192.168.0.0/16
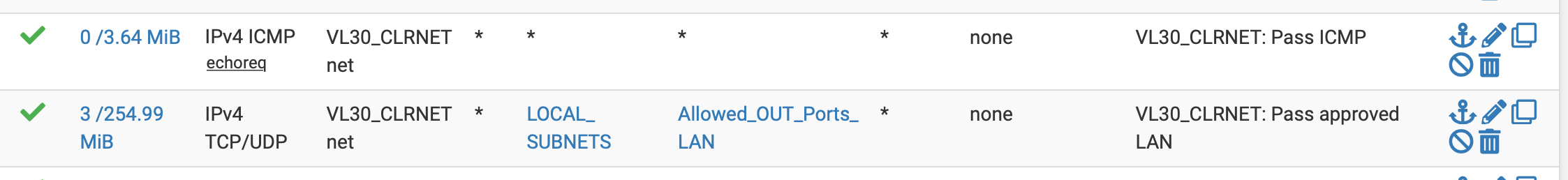
Aliases Ports; Allowed_OUT_Ports_LAN (egress)Rules for the two vlans
vlan 10
vlan30
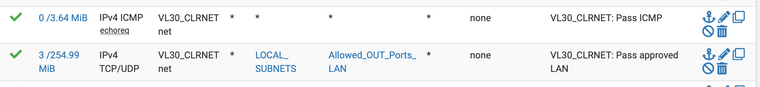
the allowed ports (short list)
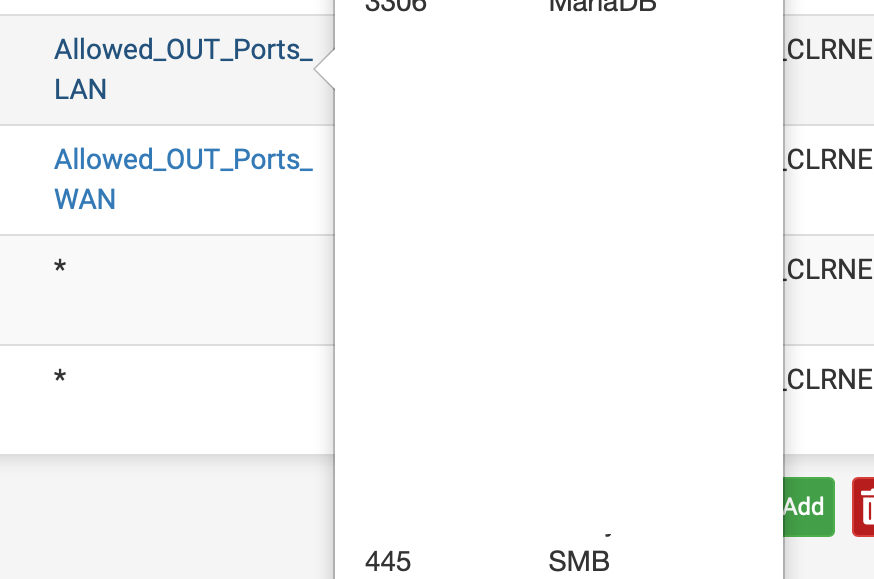
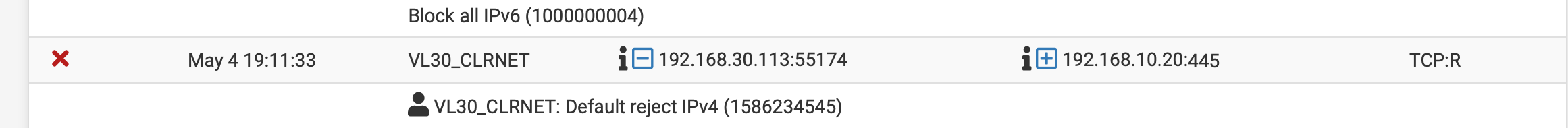
Prior 2.5 I was able to connect to share read/write no issues. From vlan30 to the server on vlan10. After 2.5 notice that my timemachine share would not copy the image. Did more testing and found that i could not write any share. However if the workstation is on vlan 10 no issues. I checked the logs and below is the screenshot of pfsense blocking from vlan 30 to vlan 10.
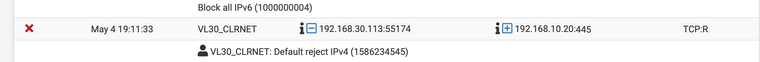
I cannot decipher why it's getting block since it define at the rules for both vlans.
any help would be appreciated.
-
That is a RST (RESET), that is the one saying - F off ;) I'm done with this connection after no act from a FIN, etc. If the state is closed then yeah extra of those would be blocked.
If pfsense was blocking the attempt at communication you would see S (SYN) blocked.. Anything other than S blocked points to the server doesn't want to talk to the client, or the client has finished the communication and never got a fin,ack to its fin. Or its taking a shortcut to closing the connection and saying this conversation is OVER..
If your seeing anything other S blocked - then the state has been closed already, etc. And that is why pfsense is blocking the traffic. Or the state was never opened in the first place in the case of a SA (syn,ack) for example because the firewall never saw the syn to open a state.
That is 30.113 sending a RST to 10.20
-
@johnpoz thank you for that explanation. I have not seen and SYN in the logs. my unraid server has had a few updates that are funky in my setup. I will go down that rabbit hole. Thank you again
-
What you might want to do is a sniff, packet capture which you can do on pfsense directly via the diagnostic menu. You can then open those packet capture in wireshark and get some details of what is going on.