OpenVPN Site-To-Site Connected but only works one way
-
I am currently having some trouble getting a full site-to-site VPN working using OpenVPN. I am running the most recent version of PFsense on both machines (Both are Netgate devices). Site A is the OpenVPN server and has a public IP while Site B is acting as the client. They are using a shared key currently. I have both sides setup with the OpenVPN allowing all traffic through the VPN. I can successfully ping and connect to all devices behind Site A's LAN from both LANs at Site A and Site B. However, I am unable to ping Site B's LAN from any of devices on Site A's LAN. I am able to ping Site B's default gateway address and access the webgui for Site B from Site A. Traceroute does not show either of the the firewalls when attempting to trace to a Site B address but works perfectly when tracing the other direction. Is there a configuration setting I am missing?
TLDR: I can ping all of Site A from both sides of site-to-site VPN but can't seem to ping anything except gateway for Site B from Site A. Using Shared Key for OpenVPN Site-To-Site connection
/------------Configuration---------------------/
Both Firewalls:
OpenVPN Tab
Protocol: IPv4
Source: *
Port: *
Destination: *
Gateway: *OpenVPN Site A (Server):
Server Mode: Shared Key
Protocol: UDP4 on IPv4 only
Device mode : tun
IPv4 Tunnel: 172.16.0.0/24
Ipv4 Remote Networks: 192.168.105.0/24OpenVPN Site B (Client):
Server Mode: Shared Key
Protocol: UDP4 on IPv4 only
Device mode : tun
IPv4 Tunnel: 172.16.0.0/24
Ipv4 Remote Networks: 192.168.62.0/24WAN Static IP WAN with no static IP/Other LAN | | /----------------------/ /-----------------------/ / Site A /-------OpenVPN ----- / Site B / / OpenVPN Server / 172.16.0.0/24 / OpenVPN Client / / 192.168.62.0/24 / / 192.168.105.0/24 / /----------------------/ /-----------------------/ | | Site A LAN Site B LANPing/Traceroute results:
Site A-> Site A - Good
Site B -> Site A - Good
Site B -> Site B - Good
Site A -> Site B - Can ping 192.168.2.1 and access webgui, but not ping any other devices in Site B's LANSite B -> Site A
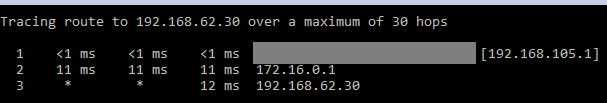
Site A-> Site B
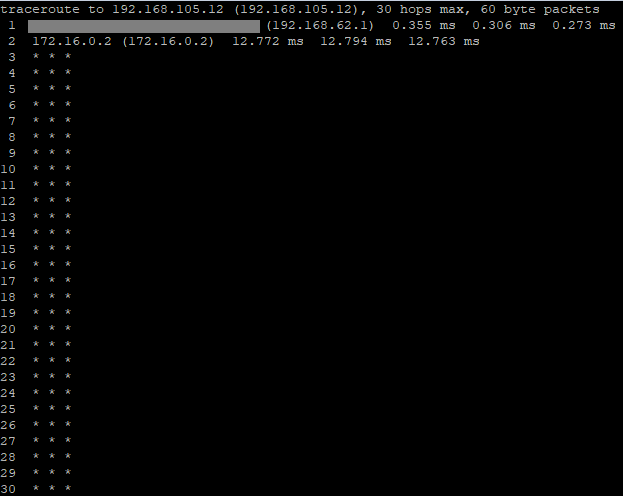
Site A-> Site B gateway
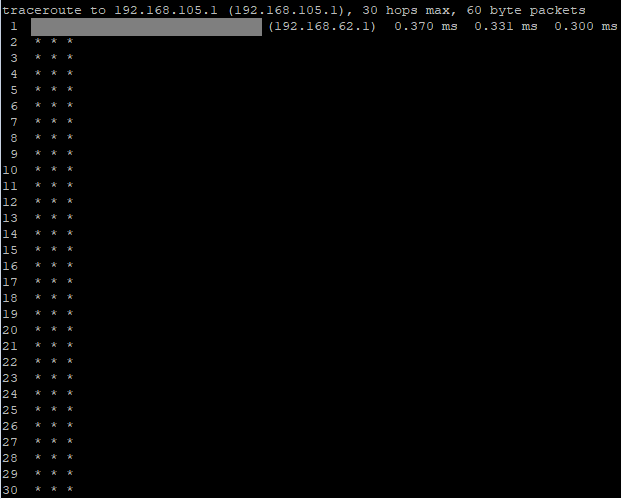
Ping Site A-> Site B Gateway
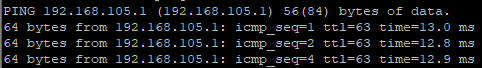
Any help would be appreciated. Thank you
-
Do you have any device like a printer you can try to ping via IP from Site A to Site B? If you only have Windows devices on the other end you are trying to ping the Windows Firewall sometimes blocks them because they are coming from a different subnet. I usually see this in Workgroup environments. You could try disabling the Firewall temporarily to test. This is why I suggest a printer. They usually don't block IPs from different subnets coming in.
Also, on site B try putting in the following rule under the WAN interface. You may already have it in there.
Action: Pass
Interface: Wan
Address Family: IPV4
Protocol: UDP
Source: any
Destination: WAN address
Destination Port Range: From: Whatever Port OpenVPN is using TO: Whatever Port OpenVPN is usingLast thing to try is go to Interfaces-->Wan. Take the checkmarks out at the bottom for Block private networks and loopback addresses and Block bogon networks just to see what happens.
-
@thatguy Disabling the Windows firewall worked. That has been driving me crazy for a few months, thank you. You mentioned that you have seen Windows devices do this. Is there a setting or anything simple/special I need to do to avoid this problem with the default firewall still enabled?
Edit: I forgot to mention that Windows Defender is already set to allow pings
-
I was looking for a client setup I have to tell you precisely what to do but I can't find one. This is probably because all of the clients I manage now are on Windows Domains and this is no longer an issue for me. But, I'll tell you where you need to go to setup the Windows Firewall Rule.
- Get to your Windows Defender Firewall. It's best to get to this through the Windows Control Panel.
- On the left click the link for Advanced Settings. From this screen you can create custom rules to allow for Inbound and Outbound Rules.
- If you right click on Inbound Rules or Outbound Rules you can click on New Rule... and a Wizard will come up to create a Rule. When you go through the wizard there will be a portion at the end where you can allow REMOTE subnets.
Unfortunately you'll have to do this for every Windows 10 machine you want access to across the VPN.