Alert TOR navigation and TOR .exe
-
Hi, I am new on this.
I have been playing with Suricata, i have investigated only the alerts, by example with ICMP.
I would like to be able to alert about TOR traffic, but only when the executable is started and a .onion is accessed.#alert tls any any -> any any (msg:"Traffic TOR detected"; tls_sni; flowbits: set,traffic/id/tor; flowbits:set,traffic/label/search; sid:9;)
#alert tcp any any -> any any (msg:"TOR exe"; pcre:"/www.[a-z0-9]{12,21}.(onion)/i"; sid:99;)
#alert tls any any -> any any (tls.sni; content:".onion"; startswith; nocase; endswith; msg:"Navegation TOR"; priority:1; flow:to_server, established; sid:1258; rev:1;)
#alert tcp any any -> any any (msg:"Content TOR 1"; content:".onion"; sid:147;)
#alert tcp $EXTERNAL_NET [9000:9300] -> $HOME_NET any (msg:"NF - POLICY - TOR browser starting up"; flow:from_server,established; pcre:"/www.[a-z0-9]{12,21}.(com|net)/i"; reference:url,networkforensic.dk; metadata:10122017; classtype:policy-violation; sid:5021501; rev:3;)
#alert dns $HOME_NET any -> any any (msg:"Trafic TOR detected"; dns_query; content:".onion"; nocase; isdataat:!1,relative; classtype:coin-mining; sid:3017030; rev:1;)None have worked for me.
I have seen rules, but they are all from the IP list. Any ideas?
Thank you very much, any help will be appreciated. -
@doloreshaz3 Isn't all TOR traffic encrypted hence you only see rules with IP lists or DNS lookups.
All the ET rules are Exit Node TCP Traffic group and Known Tor Relay/Router (Not Exit) Node TCP Traffic group.
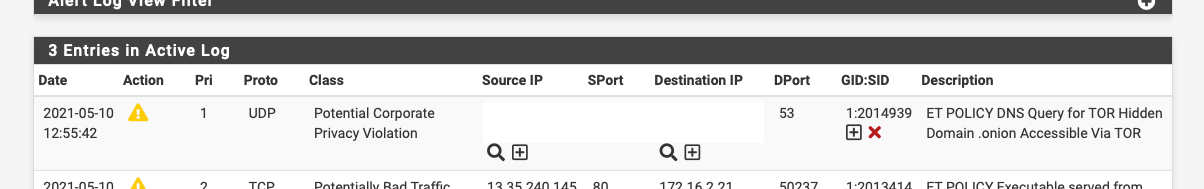
There is an ET POLICY rule for *.onion lookups:-
-
alert udp $HOME_NET any -> any 53 (msg:"ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR"; content:"|01|"; offset:2; depth:1; content:"|00 01 00 00 00 00 00|"; distance:1; within:7; content:"|05|onion|00|"; fast_pattern; distance:0; reference:url,en.wikipedia.org/wiki/.onion; classtype:policy-violation; sid:2014939; rev:2; metadata:created_at 2012_06_22, updated_at 2020_09_17;)
-
@nogbadthebad Thats was i think, because the .onion is encrypted too.
Thank you very much for your help, appreciated.