Simple OpenVPN setup... but I must be doing something wrong way ?
-
Hello there,
I have SG-3100, latest 21.02.2-RELEASE (arm) firmware.
Configuration is : WAN (static public IP), LAN (192.168.0.0/24) and OPT1 (192.168.2.0/24)
OPT1 is practicably also configured as LAN interface.So, where is the challenge? I have one NAS device that I would like put in a separate network (let's say 10.10.20.0/24) and to allow remote users to access this NAS who would be alone in this network (NAS IP for example 10.10.20.250 ) as I do not want remote users to have access neither to LAN or OPT1 networks.
NAS will be plugged into LAN interface on the SG-3100.Tunnel network is set to 10.100.100.0/24 while LAN I would like to connect to on SG-3100 is 10.10.20.0/24
Under VIP (Virtual IPs) I have added 10.10.20.0/24 as a virtual network as "Other" type of virtual IP, and all that for LAN interface.I have configured OpenVPN on SG-3100, and I my Windows 10 PC and SG-3100 are connected (OpenVPN icon is green), but I am not able to ping NAS from my PC.
I am new to pfSense and Netgate, so I guess it must be some sort of a newbie issue, anyway, I was unable to resolve it myself and have decided to ask here for help,
Any advice is more than appreciated!
-
@freeman-0 I'm not familiar with your method. I'm not sure why you need a VIP. I had no problem configuring a road-warrior OpenVPN config just by following the wizard. From there you can then create firewall rules on the OpenVPN interface to control traffic to your various networks.
-
OpenVPN works just fine (and export of clients etc.) if you want to give your "road warriors" :) an access to you LAN (in my case I have LAN 192.168.0.0/24 and OPT1 192.168.2.0/24).
Been there done that - it works fine.
However, in the same LAN and OPT1 I do have some servers that I do not want to be "exposed" to the remote users. Just as added layer of security.
So, I've decided to put that server (NAS) for the remote users into a separate "virtual" LAN, and to configure OpenVPN to give remote users IP addresses only from that LAN (in my case for example 10.10.20.0/24). That way, remote user, when connected, can "see" only this NAS and no other servers.
I hope I made it a bit more clear this way?
-
@freeman-0 said in Simple OpenVPN setup... but I must be doing something wrong way ?:
So, where is the challenge?
Probably this one : not being able to find the step-by-*step manual : Goto Youtube, locate the Netgate Channel, take a look at the OpenVPN (server) road warrior setup video's.
There is a new style one, and two older one that learn you what's needed to know. -
Actually I have watched a couple of OpenVPN on pfsense videos on YT (made by Netgate, but also Lawrence Systems and others) prior registering to this forum - but couldn't find any answer to my problem.
-
@freeman-0 said in Simple OpenVPN setup... but I must be doing something wrong way ?:
but couldn't find any answer to my problem.
These sources are not aware of the (your) problem.
That's why, initially, you should not create problems.
First, set up a OpenVPN server access on a clean ( !! ) pfSense system.
See that it works.
Play with it.
Get acquainted.Now you can go forward, introduce your own specific setup.
Always test after each setup change.
At the moment it fails, you know what to undo - you know what doesn't work. -
Did that with cisco, for many years. Now I am kind of old and life is to short to spend it playing with something that, at the end, maybe can not do what I want.
But thank you for your advice, anyway. -
@freeman-0 Your NAS is on a separate vlan? Or did you just drop a 10.10 server in the middle of a 192.168 network?
Regardless of which network your NAS is on, the procedure for setting up OpenVPN is the same. I still don't know why you need a VIP. Folks usually use their WAN as the OpenVPN address.
-
@kom said in Simple OpenVPN setup... but I must be doing something wrong way ?:
I still don't know why yo need a VIP
Same here - looks like he wants to run his NAS just on a different L3 than what everything else in the vlan is on.. Which is and always will be borked.. Put your nas on its own vlan if you want to isolate it from the rest of your network.
-
Sorry for not so prompt reply I was quite busy.
Here is a diagram of the current setup where it is also indicated what I want to achieve: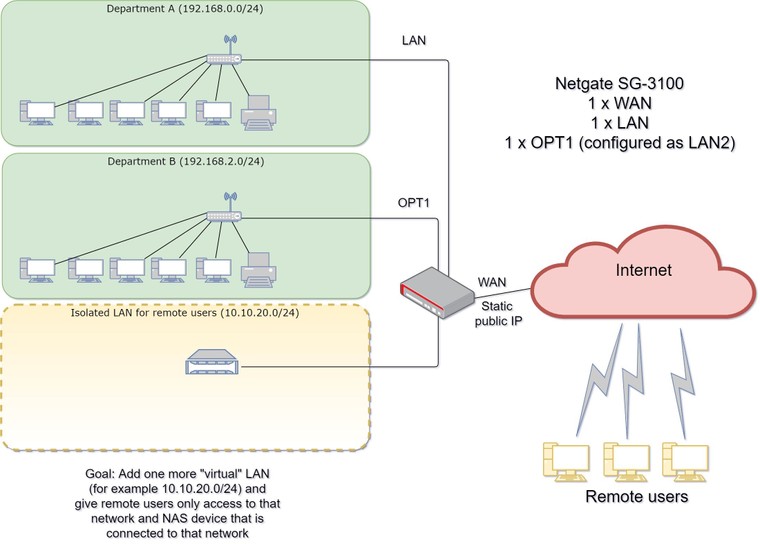
Hope this clarifies it a bit?
-
@freeman-0 How is the isolated LAN connected to pfSense? Your diagram doesn't specify, it just hangs off of pfSense somehow.
-
@freeman-0 I think your not getting the point of vlans maybe. I have the same setup and works perfectly fine.
Setup seperate vlan for you nas, setup vlans for your other 2 networks, setup Road warrior vpn. You now have 4 independent 'networks'. None can talk to each other without correct firewall rules.
Now setup firewall rules allowing access to whatever your vpn should be allowed to see. Simples...
Make sure your switch supports vlans and pfsense is your main dhcp for everything.
Don't over complex your network. Keep it simple.. If you need more help I can run you through the setup in more detail but from what I can understand your setup seems really simple.
I have 6 vlans, 2 inbound vpns and 2 outbound vpns. I have various rules blocking specific clients from accessing other clients networks etc. The key is keep the config simple then add the complexity later once you get the basics working.
-
Switches on site are a bit older and do not support 802.1Q
One drop tagged packets and other one simply ignore tagging and broadcasting traffic to all ports (a situation you generally want to avoid by using VLANS).
I guess they will be replaced at one stage as managed (and with VLAN support) switches are cheap nowadays, but for the time being this is what I have available.@kom - One switch is connected to LAN port on SG-3100, and then other computer/devices from Department A are connected to that switch. Other switch is connected to a OPT1 port on SG-3100 and then other computer/devices from Department B are connected to that switch.
Ideally I would like to connect NAS for remote users directly to one of free LAN ports on SG-3100 and keep it in the same wiring closet (with our modem, PBX etc.).
-
This post is deleted! -
@freeman-0 i reckon that should still work. it won't be as flexible as vlans but you will have to dedicate the ports on the firewall to vlans and all connections on those switches will be in those "vlans". You can then dedicate 1 port to just be for the nas on a separate vlan. Again, not sure if this would actually work (but it works in my head!!)
Ideally to get to do what you want is you want a proper switch to support vlan tagging. Then you can easily segregate ports out and get interfaces to support vlans etc.
-
@freeman-0 said in Simple OpenVPN setup... but I must be doing something wrong way ?:
One drop tagged packets and other one simply ignore tagging and broadcasting traffic to all ports
What switches are these exactly? @JKnott would say BS ;) Since all switches should pass vlan frames ;)
So I would be curious to know what switches these are.. Get another switch to put your nas on. Even if dumb you can do your vlan isolation physically. If you have no more ports in pfsense then put it between.. You can run dumb switches downstream of a smart switch that understands vlans with no issues.. As long as all devices will be in the same vlan..
But if you have a 3100.. You have enough ports to create 5 different physical networks without having to tag. Your drawing shows need of 3 only.
-
@johnpoz That really depends on the switches and their age etc.
i would for him to test my 3 unmanaged switches and prove me wrong.. all 3 of them (1 netgear and 2 tplink) drop vlan tags.
It depends on the manufacturer if they ignore or drop the additional vlan packets. Most allow but quite a few that drop them.
From my research and speaking with network professionals who do vlans day in day out - Some switches will drop the vlan frames as garbled, some switches will pass them on as they are, and some switches will strip the VLAN tags.
-
I am with you - running tags on a dumb switch is not good idea.. But @JKnott has been pretty sure that what your saying just doesn't happen ;)
My point is even if they pass them, since they do not understand them there is no isolation. Be it they pass them or not - its not good idea ever.
But love to poke the bear :) now and then.. So if you have found somewhat current switch that causing issues with tags over a dumb switch.. That would be a good poke of the bear ;)
I get what your trying to do - but running multiple L3 over the same L2 is not a good solution to your problem. If you do not have open port you can leverage on your 3100 for vlan/network to isolate your nas on its own L2.
The correct solution would be to get a $30-40 smart switch to do the isolation and then run your dumb switches downstream of that. Multiple L3 on the same L2 is never a good solution - can be be a temp work around to get around an issue - sure.. But actual solution is to isolation of your networks, be it via physical isolation with dumb switches or combination of smart and dumb to provide your isolation. So that you run only a single L3 on each L2.
-
@johnpoz Those are some "Digitus" brand switches. 24 port , unmanaged... Looks pretty generic. I have no idea why that particular brand was bought... probably it was cheapest at that time. :(

Person who was IT support here before me was trying to make network segments via VLAN's and gave up, eventually. Before Netgate SG3100 they used to have one TP Link router (19" , 2xLAN, 1xDMZ, 2xWAN) quite outdated in terms of CPU power and couldn't handle volume of VPN traffic ... so it was replaced with SG-3100.
-
That is only 10/100? ugghh.. Yeah time for an uplift ;)
Smart switches can be had for very reasonable prices these days.. But if budget is a constraint, and you need more ports for different networks/vlans than you can provide with your 3100. A simple 5 or 8 or even low cost 16 could be purchased and then run your downstream dumb switches off that.. Until such time that budget allows for upgrade of all the switches to provide for full flexibility of what vlan is where, etc.
I show a
D-Link Ethernet Switch, 8 Port Smart Managed Gigabit Desktop EEE Network Internet (DGS-1100-08V2)
for $35 on amazon right now..16 port model $109, and 24 port $129..