(Stupid?) Log question
-
I just recently started using pfBlocker and I'm still trying to figure our this cool piece of software so this might be a silly question. I have DoH blocked under an alias deny and associated firewall rules. I was looking through the logs and I found an entry on the wan interface where the source IP is 8.8.8.8:53 and the destination is <my WAN IP>:<random high UDP port>. At first I thought maybe it was a configuration error triggering some type of asymmetric routing condition but I don't think that is the case. I have a pretty plain vanilla setup with a single wan gateway. (although I do both inbound and outbound filtering of allowed ports and services) Is Google DNS really pinging my WAN a dozen times every three hours (like clockwork)?
Edit: I use Unbound as a resolver for all network clients and I am not configured in any way to use Google DNS
-
@mdouglass108 First, are you using pfBlockerNG? If not, I recommend that version. Now, the answer, most likely it is one of your client that is configured to use Google, especially, if your client is Android related and the destination IP should identify the client.
-
- Yes, using pfBlockerNG-devel
- I have a few IoT type "smart devices" on their own separate vlan but DNS requests are NAT redirected to pfSense. ONLY requests going to pfSense are allowed. I concede that 1 or more of them are very likely to be hard coded to use 8.8.8.8
- No Android devices
- Blocker shows the source as 8.8.8.8 on port 53
- Blocker shows the destination as my WAN address on a random (and changing) high UDP port.
- So are you thinking somehow a host is leaking out to Google DNS and the reply is getting picked up and blocked by pfBlocker?
-
@mdouglass108 said in (Stupid?) Log question:
So are you thinking somehow a host is leaking out to Google DNS and the reply is getting picked up and blocked by pfBlocker?
No, it does that only to clients because the client made a DNS request and that client is not getting DNS request from pfSense else you would have the IP address of the device instead of your WAN IP as the destination. Do you force all clients to use pfSense DNS in your LAN firewall like this:
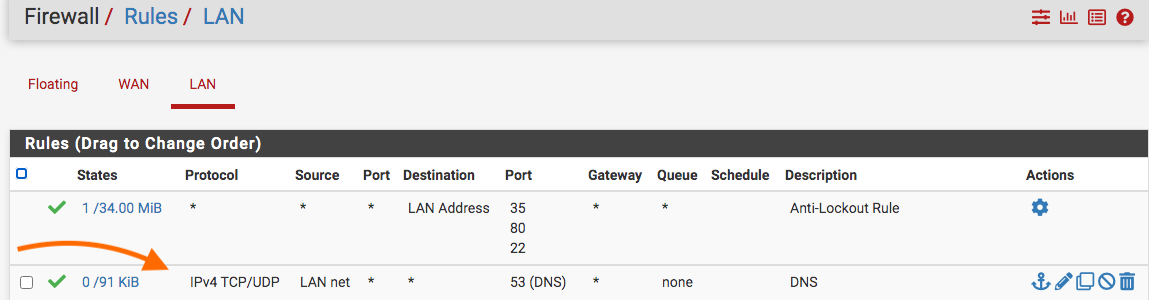
-
Not quite.
The DNS rule is as follows for each interface:
Action = Pass
Protocol = IPv4 TCP/UDP
Source = LAN Net
Source Port = any
Destination = LAN Interface address (i.e 192.168.10.1)
Destination Port = 53
Gateway = anyAll permitted traffic is specifically passed on a rule by rule basis. Each interface has approximately 6-7 rules total. At the end of the rule set there is an explicit block all rule.
The NAT rule redirecting DNS requests is as follows:
Protocol = TCP/UDP
Source = LAN Net
Source Port = Any
Destination = !LAN Address (NOT Lan)
Destination Port = 53
NAT IP = LAN Interface address (i.e. 192.168.10.1)
NAT Ports = 53Unbound is configured to listen for requests on LAN (and all other interfaces)
-
Also, when I filter the pfBlocker logs for a destination of 8.8.8.8 there is nothing........other than the entry for the test I just did to confirm that outbound blocking was working. So it certainly appears that it's not originating from inside my network. Otherwise pfBlocker would be rejecting and logging that request.
This is more of a curiosity than anything else. Why are packets from 8.8.8.8 hitting my WAN every 3 hours or so? I assume that Google uses a range of IP addresses that actually reply to DNS queries directed at 8.8.8.8. If I WERE using Google DNS at 8.8.8.8 and logging that traffic would the reply show it from 8.8.8.8 or some other address in their assigned range. This goes beyond my shallow pool (or pond) of understanding of how large CDNs function behind the scenes.
-
@mdouglass108 It should be in the DNSBL log. May I suggest turning off all devices, then turn them on one by one to find the culprit
-
I'm not running DNSBL yet (still trying to figure out pfBlocker). I'm using IP list to block DOH, specifically Alias Deny with the list TheGreatWall_DoH_IP.
The list of of likely clients to unplug is a lot shorter than the list of ALL clients to unplug so I'll start with those first. The fact that there is no outbound log entries in pfBlocker seems to suggest it could be something like this post from another forum:
https://community.spiceworks.com/topic/527938-strange-inbound-udp-packets
I really appreciate you taking time out of your day to respond but since this is more of a curiosity than an operational issue I'll mark this thread as closed. Near as I can tell everything is working correctly on my network. Blocked things are getting blocked and allowed traffic is getting passed. If I find anything interesting or noteworthy I'll post it here but for now I think I'm done.
Thank you.
Cheers!