Preventing to access pfSense login page on IoT VLAN
-
@kom Unable to ping anything. Computer is not able to acquire a DHCP address, while the DHCP server is active on the test VLAN
-
@keesdek Post a screen of your rules for that interface.
-
-
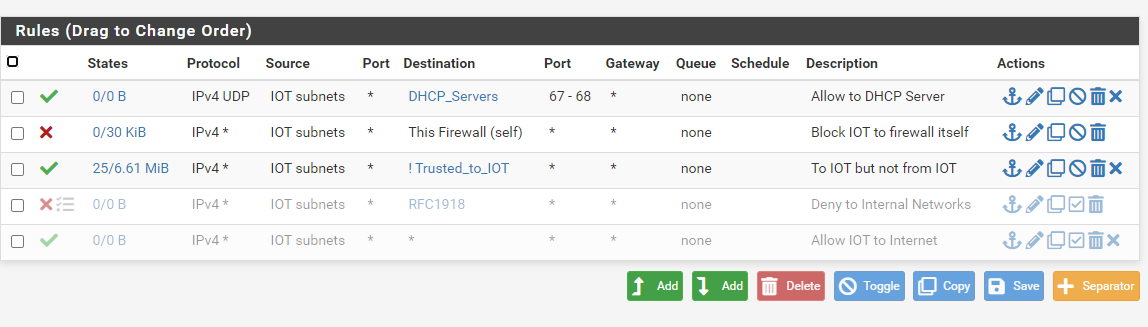
@keesdek Rules are processed top-down first match (except floating rules which are last-match unless you have the Quick option selected.) All your rules are out of order since the top rule allows everything. That rule should be last, not first. Your problem isn't your rules.
-
@kom Thanks again for your help!
I tried 'johnpoz' (above) order first, but since it didn't work then, I started changing the order... -
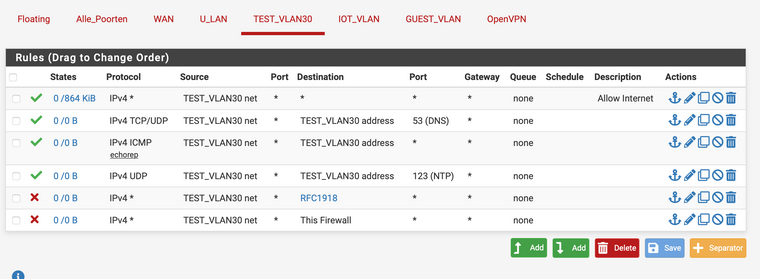
@keesdek Can you confirm that your test client is on test_vlan30?
-
@kom Yes, the test client is on test_vlan30. And in the mean time my computer has acquired an IP address. But still no internet
-
@keesdek In the meantime? Getting an address via DHCP should be almost instantaneous. What is this client? PC, phone? Physical, virtual? Windows, Mac, Linux? Any hardware like a switch between client and pfSense? What do your outbound NAT rules look like?
-
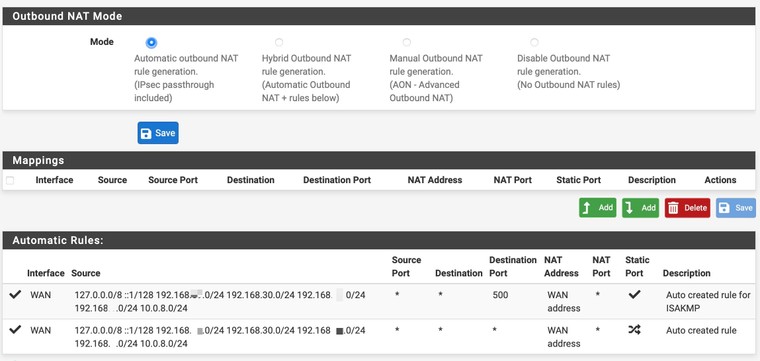
@kom Well... initially I configured the test_vlan30 interface incorrectly. But that is fixed. Attached a screenshot of the outbound NAT rules
-
@keesdek What is this client? PC, phone? Physical, virtual? Windows, Mac, Linux? Any hardware like a switch between client and pfSense?
-
@kom Client is a Mac, connected via UniFy switch and wireless access point
-
@keesdek So lots in between to cause problems. I'm not a Mac guy. Can you confirm that it gets an IP address in the correct range, has the correct mask, gateway and DNS?
-
@kom I can confirm all
-
@keesdek Delete all your rules on that interface except an allow all rule. Get basic connectivity working before you start to restrict things. Once that is done, can you ping the interface from the Mac?
-
@kom Did that and am able to ping the interface. In the webbrowser the pfSense web gui opens as well. And I have internet connection as well
-
@keesdek Well, looks like it works now. Here is what I did. After deleting all the rules except the allow rule, I started turning the rules on again from the bottom up. When I leave the top rule turned off, it works! On the test network I can connect to the internet, but am not able to open the pfSense web gui
Thank you very much for your help KOM and others!!
Still a lot to learn on my side
-
@keesdek said in Preventing to access pfSense login page on IoT VLAN:
eave the top rule turned off,
Then there is no way you would have internet.. Again rules are evaluated top down.. If you have not any rule - how would you have internet? You wouldn't not through this interface you wouldn't..
Also whatever you dhcp issue - has nothing to do with rules.. You could have zero rules, you could have explicit rules blocking dhcp and it would still work.. once you enable dhcp on interface - hidden rules are created that allow dhcp to work..
So you saying dhcp wasn't working had nothing to do with any rules you created that is for sure.
-
@johnpoz The dhcp issue was due to the fact that I misconfigured the test_vlan interface...
-
@johnpoz Brilliantly useful. This is EXACTLY what I wasted time trying to blindly do on my own via google and youtube. THANK YOU
-
Hey all... I was just reading through firewalling posts and wanted an opinion on this topic where rules I have setup are concerned. In my case, I needed other trusted networks to be able to initiate traffic to IOT devices but not the other way round. Further, I do not use pfsense as a dhcp server because it acts as a dhcp relay. My setup is a bit different where I am using a L3 switch for trusted networks where the routing between them is done on the switch. Untrusted vlans such as GUEST and IOT are sent up to pfsense via a separate trunked interface where I have the firewall governing where the traffic on those vlans can and cannot go. I wanted to know if what I am doing on IOT from a rule perspective is the best method. You will notice some of the original rules I have disabled in favor of the newer rules. What you see below functions as I described for the IOT network. Thoughts?