Preventing to access pfSense login page on IoT VLAN
-
@johnpoz
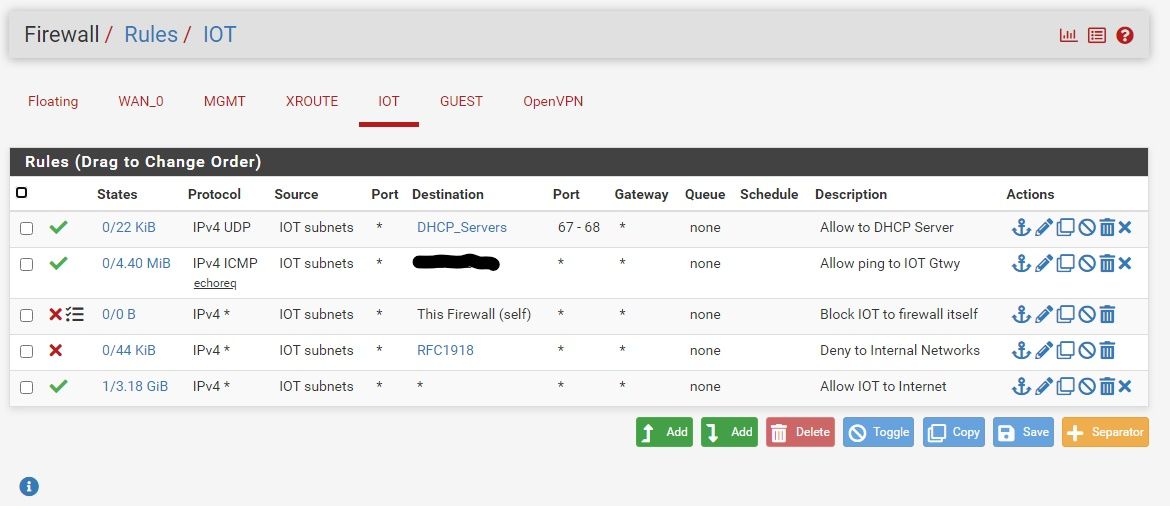
Well... Did some testing... Turns out that those inverted match rules were not doing what I thought. So I have the desired rules on my transit interface controlling what can talk to IOT and appropriate rules that block access from IOT (and GUEST) to internals as needed. Thanks for the heads up on inverted match rules. I have a screenshot of the IOT rules in case it helps anyone else out who may be providing dns, dhcp or other services that are not running on their pfsense box.Merry Christmas everyone!
-
@aclouden Why do you think you need that dhcp rule at the top?? if you enable dhcp or dhcp relay on the interface the rules are put in place to allow for dhcp hidden, I don't see what the point of that dhcp rule is when there would be hidden rules to allow anyway.
And block works as well, but using reject on local is sometimes better because it can cut down on devices retrans, basically banging their head on the wall - hey I want to go here, I want to go here, I want go here.. With a reject when it tries to go - it will be told NO!! and wont send any retrans trying to get an answer.
-
@johnpoz
I seem to remember when I was setting up these interfaces that dhcp would not reach my internal servers without that rule. I'll test that again..I remember reading a long time ago that block is the best choice because the traffic is simply dropped with no reply. But.... Since these are internal interfaces and not public facing, I see what you mean.
-
@aclouden yeah reject would be a bad choice for external interface where your seeing noise from the internet, but internally its a better choice to be honest.
edit: you can view your hidden rules for dhcp like this
https://docs.netgate.com/pfsense/en/latest/firewall/pf-ruleset.html
[23.09.1-RELEASE][admin@sg4860.local.lan]/var/unbound: pfctl -sr | grep DHCP pass in quick on igb0 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server" ridentifier 1000002541 pass in quick on igb0 inet proto udp from any port = bootpc to 192.168.9.253 port = bootps keep state label "allow access to DHCP server" ridentifier 1000002542 pass out quick on igb0 inet proto udp from 192.168.9.253 port = bootps to any port = bootpc keep state label "allow access to DHCP server" ridentifier 1000002543 pass in quick on igb2 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server" ridentifier 1000003591 pass in quick on igb2 inet proto udp from any port = bootpc to 192.168.2.253 port = bootps keep state label "allow access to DHCP server" ridentifier 1000003592 pass out quick on igb2 inet proto udp from 192.168.2.253 port = bootps to any port = bootpc keep state label "allow access to DHCP server" ridentifier 1000003593 pass in quick on igb4 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server" ridentifier 1000004641 pass in quick on igb4 inet proto udp from any port = bootpc to 192.168.200.1 port = bootps keep state label "allow access to DHCP server" ridentifier 1000004642 pass out quick on igb4 inet proto udp from 192.168.200.1 port = bootps to any port = bootpc keep state label "allow access to DHCP server" ridentifier 1000004643 pass in quick on igb2.4 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server" ridentifier 1000007791 pass in quick on igb2.4 inet proto udp from any port = bootpc to 192.168.4.253 port = bootps keep state label "allow access to DHCP server" ridentifier 1000007792 pass out quick on igb2.4 inet proto udp from 192.168.4.253 port = bootps to any port = bootpc keep state label "allow access to DHCP server" ridentifier 1000007793 pass in quick on igb2.6 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server" ridentifier 1000008841 pass in quick on igb2.6 inet proto udp from any port = bootpc to 192.168.6.253 port = bootps keep state label "allow access to DHCP server" ridentifier 1000008842 pass out quick on igb2.6 inet proto udp from 192.168.6.253 port = bootps to any port = bootpc keep state label "allow access to DHCP server" ridentifier 1000008843 pass in quick on igb5 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server" ridentifier 1000009891 pass in quick on igb5 inet proto udp from any port = bootpc to 192.168.7.253 port = bootps keep state label "allow access to DHCP server" ridentifier 1000009892 pass out quick on igb5 inet proto udp from 192.168.7.253 port = bootps to any port = bootpc keep state label "allow access to DHCP server" ridentifier 1000009893 pass in quick on igb3 inet proto udp from any port = bootpc to 255.255.255.255 port = bootps keep state label "allow access to DHCP server" ridentifier 1000010941 pass in quick on igb3 inet proto udp from any port = bootpc to 192.168.3.253 port = bootps keep state label "allow access to DHCP server" ridentifier 1000010942 pass out quick on igb3 inet proto udp from 192.168.3.253 port = bootps to any port = bootpc keep state label "allow access to DHCP server" ridentifier 1000010943 [23.09.1-RELEASE][admin@sg4860.local.lan]/var/unbound:Those are all the interfaces I have dhcp enabled on, zero rules set on my gui - dhcp works on all interfaces.