Cannot Renew LetsEncrypt Cert
-
I have had a LetsEncrypt cert for the pfSense WebGUI running fine for the past 3 months, but when I tried to Issue/Renew (configured as Standalone HTTP Server), it times out, and suggests my firewall is blocking access. I have port 80 forwarded to 8080 on the firewall. Not sure how to fix this...
I've tried going to DNS manual, and it seems like that part works OK, but now it says I need to add TXT value (which is provided in the output)...how/where do I do that?
In short, I would like to know what I am doing wrong with the first method, and if there is something fundamental for why that combo can't work, how do I make the second method work. First method is also preferred as I can automate it via cron.
Anyone have any thoughts on how I can get this renewd?
-
I'm not sure what method your using.
You saw the 'must see this first' ? At that moment in the video, you were strongly advised not to use the GUI as a http-01 web server. Don't stop there, do look at the entire video.
You have (rent) a domain name and thus access to the registrar's control panel to 'manage' the domain name. The registrar normally also gives you some access to at least 2 DNS servers, a master is one of them.
This master should be accessible using the DNS-01 method. That's the method you should prefer, by far.
The registrar doesn't offer DNS-01 access , Leave them, go some where else.
Or pick a registrar that has a method listed here : https://github.com/acmesh-official/acme.sh/tree/master/dnsapiThe video mentions a plan B or C using internal (LAN based !)web server to make http-01 possible, or a solution with the HA-Proxy.
-
If what your using for dns does not support api that acme support.. Cloudflare for example works here, using it for a couple of different certs.
Then your dns would need to atleast support the adding of a TXT record where you could manually create the record with the value given in the output.
But I would suggest better option. I personally would never use acme for pfsense web gui cert. How many users would be accessing this - you? from how many different devices?
Why not just create cert via a CA your browser can be set to trust.. Pfsense can do this all with a couple of clicks. Now you will only have to renew this cert ever say 398 some days - which seems to be the new sort of length limit browsers won't complain about. Now you can even add rfc1918 address for SAN and can access pfsense via fqdn or ip and your browser will not complain.
acme is great when you need a cert that lots of people and devices will trust that you have no control over.. Something exposed to the public for example - now sure why this would ever be something you would do with pfsense web gui. Only admins should ever be using that..
example - I created mine well before the age limits kicked in, so still valid by browsers. Mine is good for 10 years.. So never really have to mess with it. I have CA on pfsense that I can create many certs my browser trusts that really only I ever access. My switches, my printer, unifi controller gui, my nas gui, etc. etc..
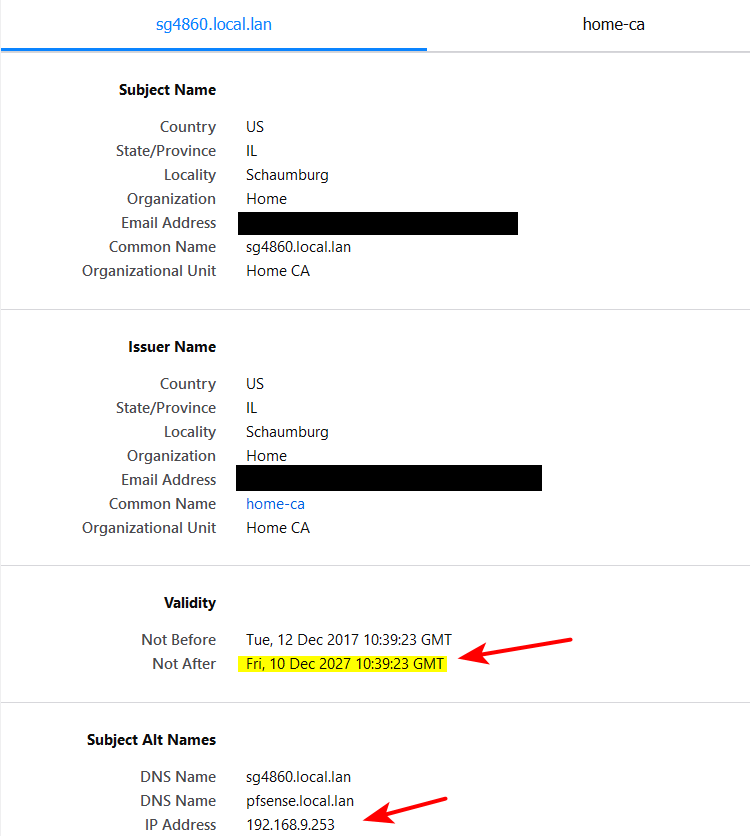
And I have rfc1918 ip of pfsense in there as well - so even if my local dns fails - I can access the web gui without my browser complaining..
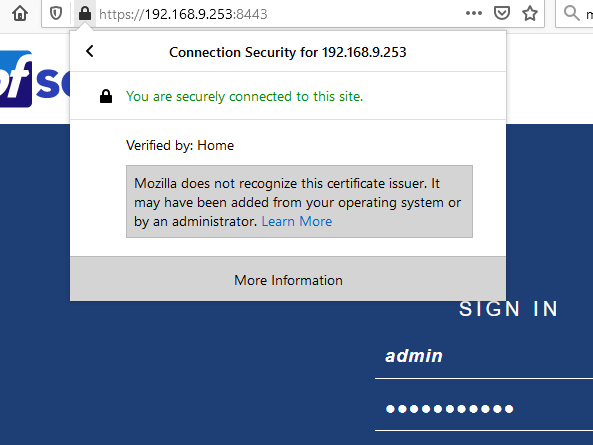
While acme is great and all - it just doesn't make sense to use it for something like your firewall web gui access. Other advantage is you can just use any domain you want, doesn't have to be a public domain. Notice my local.lan - at some point will be changing over to using the recommended home.arpa domain - but will loose my 10 year long cert ;)
-
OK, so...some good ideas, and yes, LetsEncrypt for my pfSense Webgui is overkill. Ack (watched the whole 1 hour video).
A lot of this is me trying to understand how to use this functionality and in general, how to work with automating cert renewal, and working with LetsEncrypt, etc. So, having said that, I would like to sort out how to do it, regardless if its a good idea. To be honest, in future I like the pfSense as CA idea and will likely pursue that, but for the moment...
So, my domain is with Google Domains, which has the functionality to add TXT records (my correct usage of this function is TBD). From watching the video, it seems like the easiest way to accomplish all this is by using DNS-manual.
When I do this, I first click 'Issue'
...and then get this output:
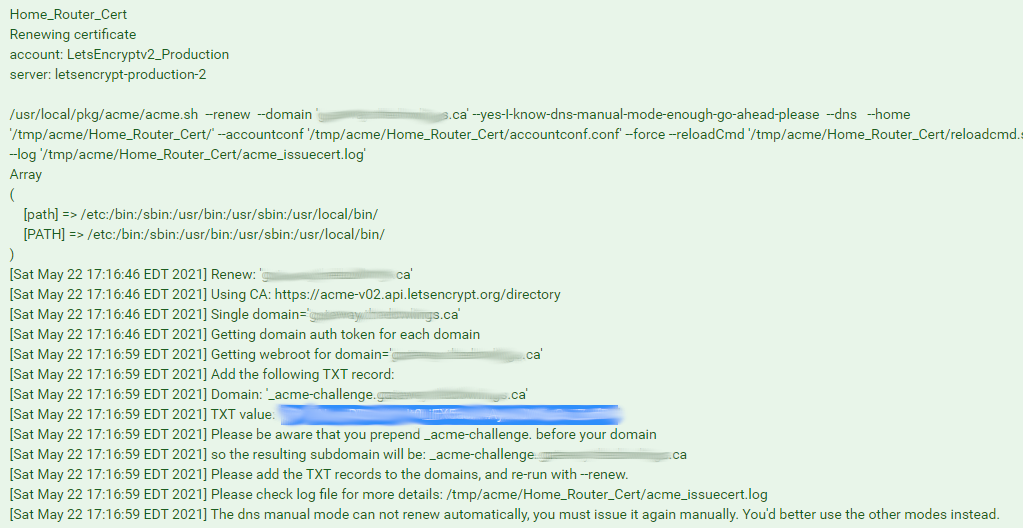
I take the TXT value and add it to my google domain record:
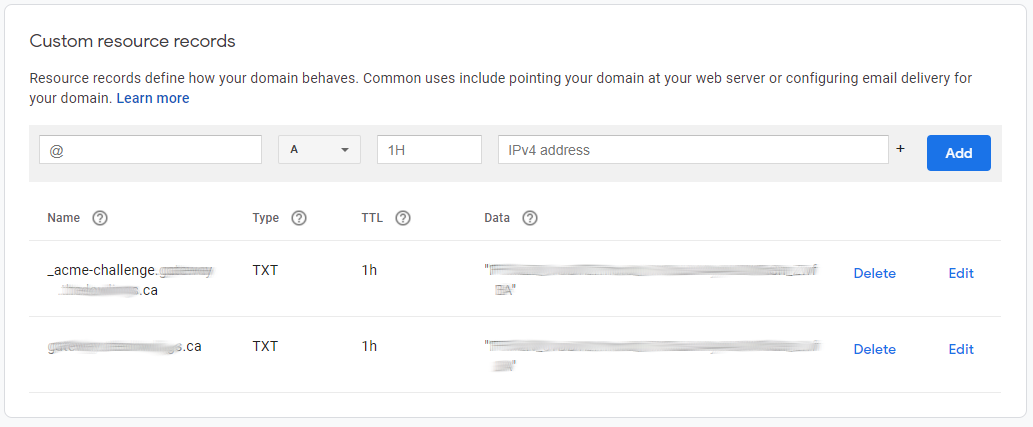
Wait a bit of time (5 mins), then hit the 'Renew' button and...no joy.
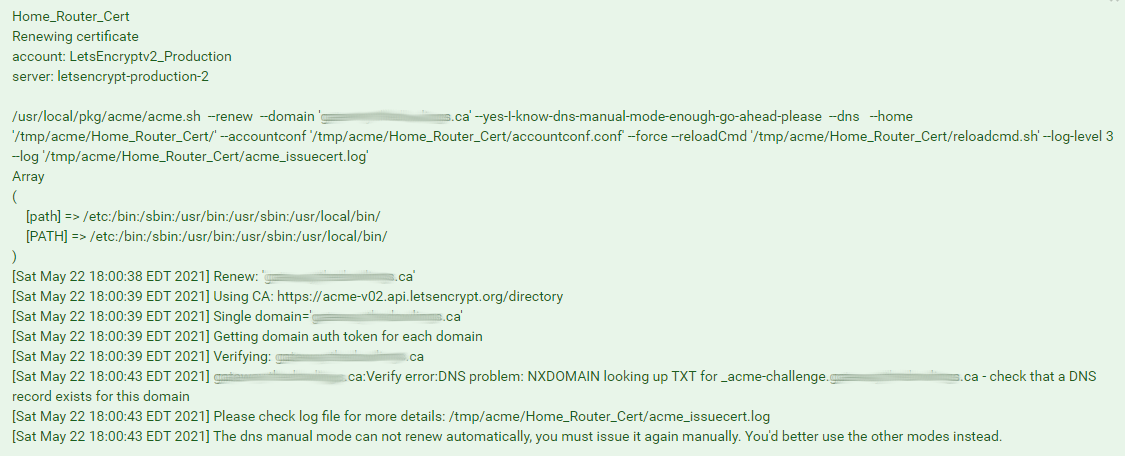
So...given this additional info, what do folks think. Thoughts on next steps?
-
Well your getting a NX for looking up that record.. Doesn't matter what value put in there for TXT, it needs to be resolvable.
I mean it does matter.. But for testing make sure you can actually resolve that record before you hit renew.
Do a simple dig or nslookup... PM me your domain and I will see if TXT resolves.
-
@sdowling said in Cannot Renew LetsEncrypt Cert:
Wait a bit of time (5 mins), then hit the 'Renew' button and
..... wrong ^^
Why passively wait ?
Make it an active wait.You add the TXT record with the google domain record GUI.
Now, start polling it : have pfSense ask for that TXT record :
dig @127.0.0.1 _acme-challenge.your-domain.tld TXTand repeat this until you get your -correct - TXT record back.
Now you know the TXT is valid for you, and also for Letsenscrypt.
This is the moment you can proceed.Btw : the DNS propagation time is somewhat random.
Do the check yourself :
As for all the DNS name servers of your domain :dig @127.0.0.1 your-domain.tld NSYou get a list back with all the DNS servers for your domain.
dig @ns1.your-domain.tld _acme-challenge.your-domain.tld TXT dig @ns2.your-domain.tld _acme-challenge.your-domain.tld TXT dig @ns3.your-domain.tld _acme-challenge.your-domain.tld TXTetc. (there should be at least two NS servers)
They all have to return the valid TXT record.Btw : the acme DNSAPI automates this adding (and deleting !) of these records. Authentication will be needed of course, as you have to ID yourself to get access to the GUI to modify a DNS record yourself, and when that's done, it's a pretty straightforward process.