firewall without NAT
-
@akegec
mmm, don't know what you are saying. I don't use any VLANs. Or is a bridge some kind of VLAN? -
You need to set the filtering sysctls before you create the bridge. So if you change them afterwards you need to re-create the bridge. A reboot does that.
Steve
-
@stephenw10
Thanks Steve. Was not sure if I was doing wrong. This explains it. -
@olivier-demoustier Lastly, existing firewall states are not affected by a rule addition or change. Those states need to be cleared via Diagnostics - States in order for the new/modified rule to take effect. This trips a lot of people up when they make a rule and it doesn't seem to do anything. Rebooting the firewall does the same thing as resetting states but in a brute-force way. Glad to hear you got it working.
-
@kom
Thank you for explaining. But would be nice if the software would do this automatically when you hit 'apply". Or at least a pop up saying that you need to do that......? -
@olivier-demoustier I hear you. After applying the rule, it should be possible to go through the state table and nuke any states that match a firewall rule. An option could be added to the rule list page to reset existing states on Apply after add/edit. There is likely a technical reason I'm ignorant of as to why this isn't done. Perhaps for performance reasons like having to wait another 5-10s more (depending on your CPU) than you already have to wait every time you modify the rules. Perhaps the dynamic nature of the table and how it works makes this difficult or impossible. I don't know. But I do know that this is fairly obvious and smarter people than I have been working on this for a long time so there must be a reason.
-
@kom
Or just add a second apply button. One without and one with the extra actions needed.... -
@olivier-demoustier how do you get different paths ie wifi and LAN into the lightbox sorta indicates having wifi and LAN NICS? therefore it should have 2 IP addresses how is it specificially set up lightbox connected to ? via a switch or ? as you are trying to isolate 2 different port ranges in one path or channel eg only one NIC, sorta pointless as that traffic needs to pass through a NIC to get to the light box and different ports if you are trying to isolate traffic need to travel through separate NICs to not conflict or congest said NIC, my thought to do this would be a NAT redirect for one port to go via one NIC and the other port to be redirected to the 2nd NIC but you have not been clear with your actual config, I could be wrong but its how I would do it 2 NIC in light box 2 IP addresses with a separate NAT redirect for each needed port or port range
-
@olivier-demoustier it was late and my eyes were half closed, sorry for confusion. Steve explained what I was trying to say. @stephenw10 thanks man.
-
@sundarnet-0
1 pictures speaks a 1000 words
This is the setup (simplefied) .
The lighting consoles have only 1 NIC for all types of communication like Artnet, sACN, OSC, Telnet, UDP remoting, TCp remoting..........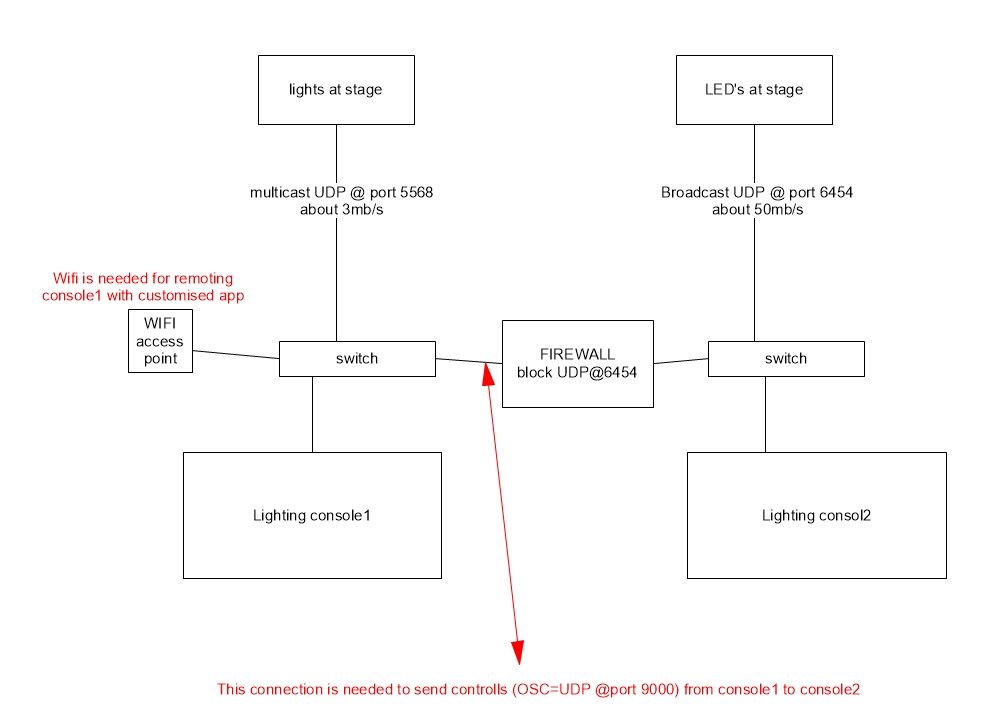
-
Just ran into another problem here. Maybe someone can help me out?
So I made a bridge and have only 1 firewall rule that passes all traffic.
Part of the traffic is "sACN" It is a multicast UDP E1.31based signal (more info here https://artisticlicence.com/WebSiteMaster/Publicity/HelpDesk18-sACN-in-large-systems-Part1-Nov2018.pdf)
After a few minutes (without any reason or changes) this part stops working. As far as I can see, all other protocols keep passing the firewall.
someone any idea why? -
You might need to check 'allow IP Options' on the pass rule there:
https://docs.netgate.com/pfsense/en/latest/firewall/configure.html?highlight=multicast#ip-optionsSteve