firewall without NAT
-
Hi, is it possible to create a firewall without NAT? I would like to make something that blocks a range of ports, but all other traffic should pass unchanged. This system has no internet and no need of DHCP. Everything is on static IP's and 99% of the traffic is UDP.
Any suggestions are more than welcome. Thx in advance -
@olivier-demoustier I've never tried it but turning off outbound NAT would do it? Firewall - NAT - Outbound. Set it to Disable Outbound NAT rule generation. I don't know if that removes or disables the existing rules or not.
-
Yes, that would remove all outbound NAT rules.
https://docs.netgate.com/pfsense/en/latest/nat/outbound.html#disabling-outbound-nat
Steve
-
@stephenw10 Thanks for all the quick responses. unfortunately it does not work for me.
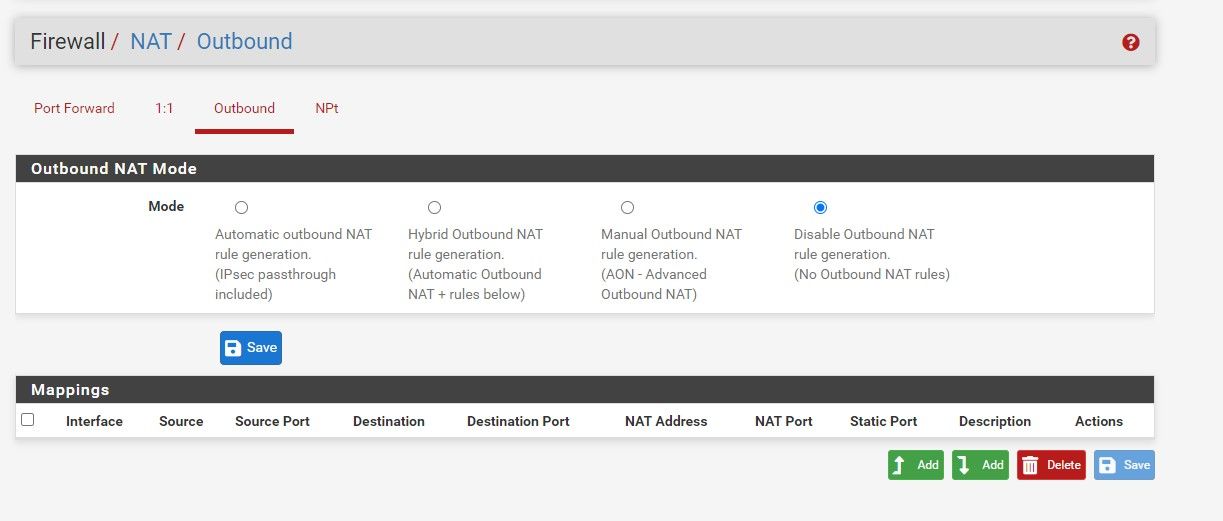
Attached some screenshots: NAT disabled and No firewall rules. And still no UDP traffic passing tru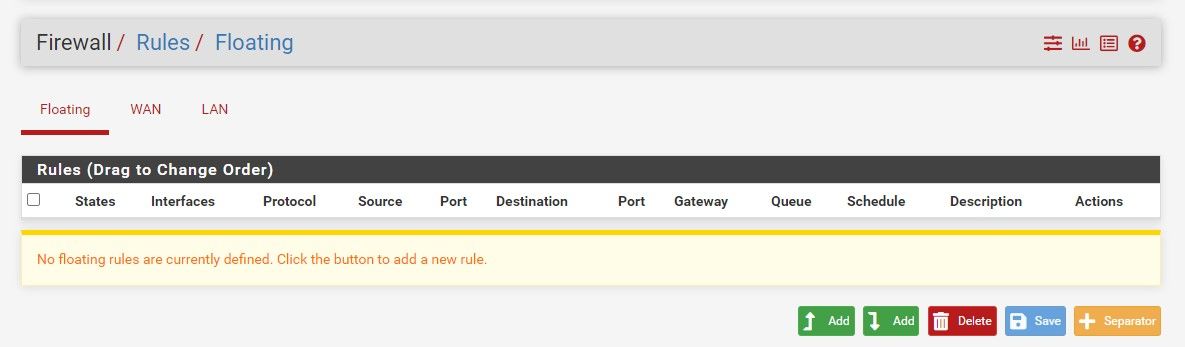
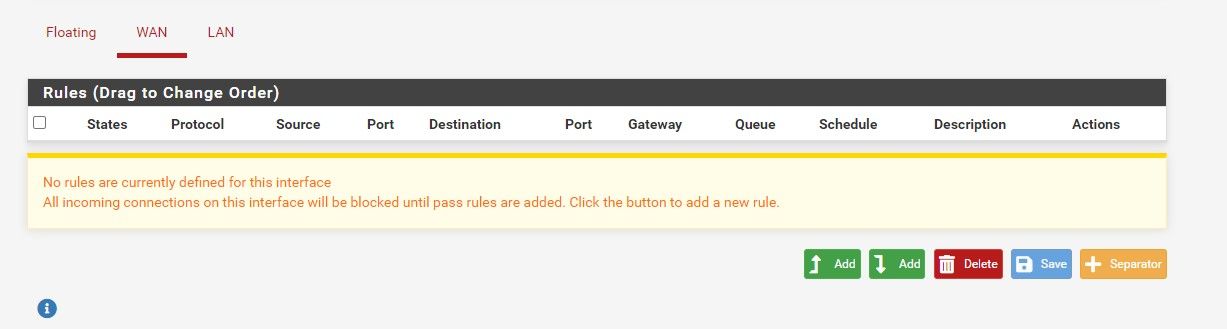
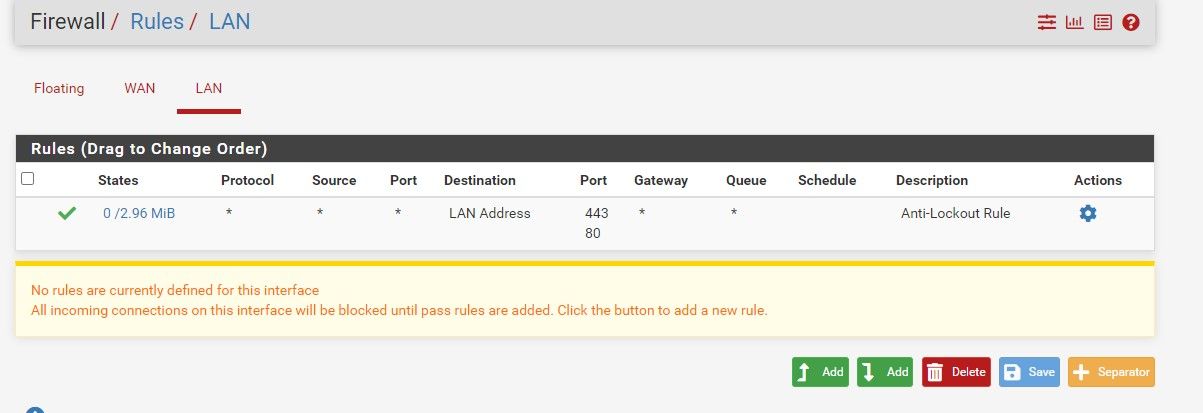
I'm probably missing some more? I started with a fresh install, no VLANs
I left the IP address for LAN at 192.168.1.1 (DHCP disabled)
But what IP address should I set for WAN? Like I mentioned, in this system everything is on static addresses.
Thanks in advance. -
@olivier-demoustier You need at least one Allow rule on any interface whose clients need to go through that interface. Right now, you have it configured to block all traffic to WAN and LAN.
-
@kom
No luck :)
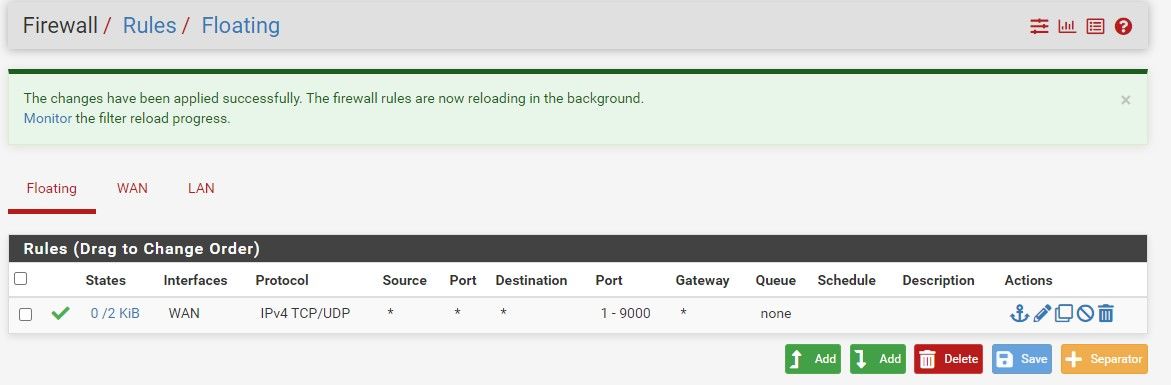
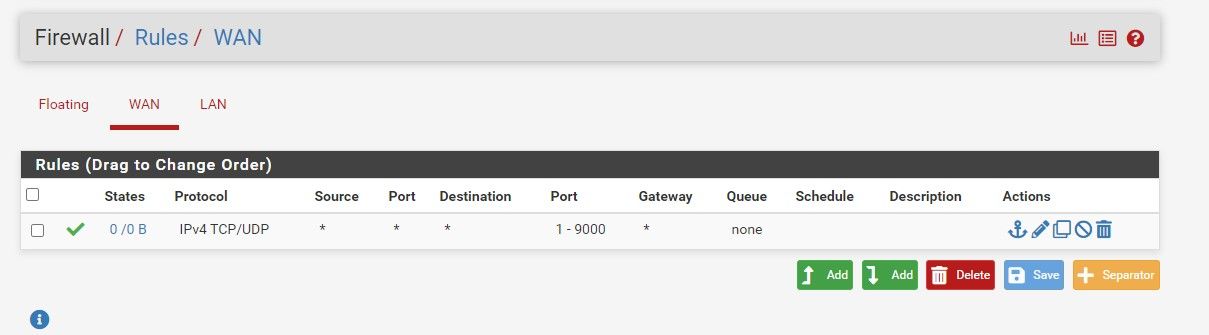
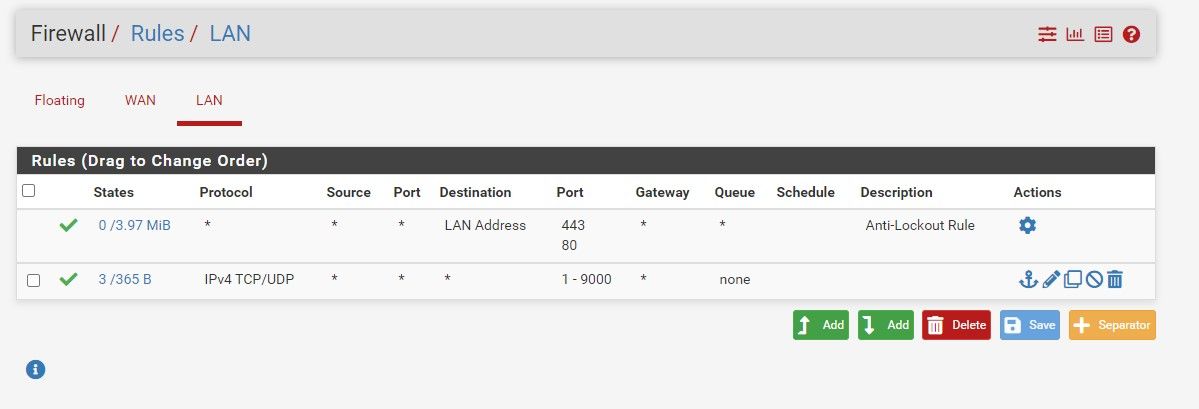
-
@olivier-demoustier I have no idea what you're trying to do with which clients on whatever network so I can't really comment further other than to say that you need to do some reading on pfSense and how it works. Perhaps if you explained what you have and what you are trying to do, it would be more clear. In a lot of cases, new users decide on a course of action which is either wrong or sub-optimal and then ask specific questions when they should be describing what they want to achieve and then asking for suggestions on how to best do it.
-
@kom
Hi Kom, I understand what you are saying. And indeed I'm not familiar with firewalls and NAT's.
In short the situation. Lighting desk that sends (a lot ) of UDP on port 6454 (artnet, broadcast) and some other UDP on port 9000 (OSC). I would like to split up this traffic with 2 firewall's. So I have 2 UTP cables. One with only the UDP on port 6454 and another with only the UDP on port 9000. -
@olivier-demoustier What network is on WAN, and on LAN? How are these devices (I have no idea what a lighting desk is) connected to pfSense? IS this UDP traffic coming from one client or multiple clients? Why do you want to split that UDP traffic in the first place?
I have to leave until tomorrow so post your answers and maybe someone else can help you with this.
-
@kom
A lighting desk is a console that controls lights for TV/rock shows....
It broadcasts "ARTNET" this is a UDP signal on port 6454. In large show's it reaches up to 80mb/sec. At the same time it receives other controls on port 9000 (called OSC). Sometimes the OSC gets lost by all the broadcast or/and the osc needs to be wireless via WIFI. If we don't split the ARTNET from The OSC, all the artnet slows down the wifi.
In real life it is a bit more complicated and also more different protocols involved. But if the simple setup works, I can adjust further. -
@olivier-demoustier
Does all communication devices have fix IPs or do they use UPnP to connect to the other? -
@viragomann
All fixed IP's -
@olivier-demoustier
I can imagine that you get an asymmetric routing in this setup. If that's the case, it possibly helps to enable sloppy state handling.
You can do this in the firewall rules in the advanced options. -
@viragomann
For the moment, I don't get any UDP packet true the firewall. -
pfSense will route between the WAN and LAN interfaces. Traffic coming into the LAN will be routed out to the WAN as long as firewall rules pass it and a route exists. That could be the default route or between the WAN and LAN subnets directly.
However, you're taking about broadcast traffic that will not be routed. That is always inside one subnet.
What subnets do you have on WAN and LAN?
What IPs are you testing between?
It sounds a lot like you might actually want a bridge here with both interfaces in the same subnet.
Steve
-
@olivier-demoustier if you are trying to isolate traffic by having 2 nics in the lightbox then you need to isolate those IP addresses and use direct IP address rules in your firewall but possibly going to need to use NAT redirects for that
I say this assuming you are trying to isolate one ports traffic through one NIC and the other via the second to stop overloads? -
Some people are still believing that NAT is evil. Just because some people don't like entering their home through a door instead a wide gate. By default a door denies all inbound.
-
If it is broadcast, use only a managed switch with different VLANs, then you got 2 broadcast domains and no interaction betwen this.
One VLAN is used for WiFi and the other dont flod the WiFi anymore. You want now to route betwen this VLANs, you neet different IP Subnets and then you can use an Firewall between.
-
@sundarnet-0
Hi SundarNet, The lighting console has only 1 nic. So all this broadcast ( on port 6454 and 9000) passes in/out 1 nic on that end. This meaning , only 1 IP adress. -
@stephenw10 IP range is 2.x.x.x subnet 255.0.0.0