Traceroute on nested VPNs
-
Hi
I've been experimenting with the full tinfoil hat for some weeks now, trying various nested VPN setups, mostly because I can really. I have a generally stable connection as it stands, latency isnt as bad as I thought but I have a question. Actually I have two but I'll save the MTU can of worms for another day.
If you run a traceroute over a nested vpn connection, will it show hops across both of the vpns or just the second (outside?) one? I think I can see the 'nest' in OpenVPN, all traffic in my network is sent out over the AirVPN gateway which uses NordVPN as its interface, but if I run a tracetoute from inside the network I can only see traffic going into the AirVPN servers, I see no hint of NordVPN. Do I actually have a nested VPN or am I sadly deluded, or even worse, am I actually sending traffic out over both VPNs in a sad mockery of my intentions?
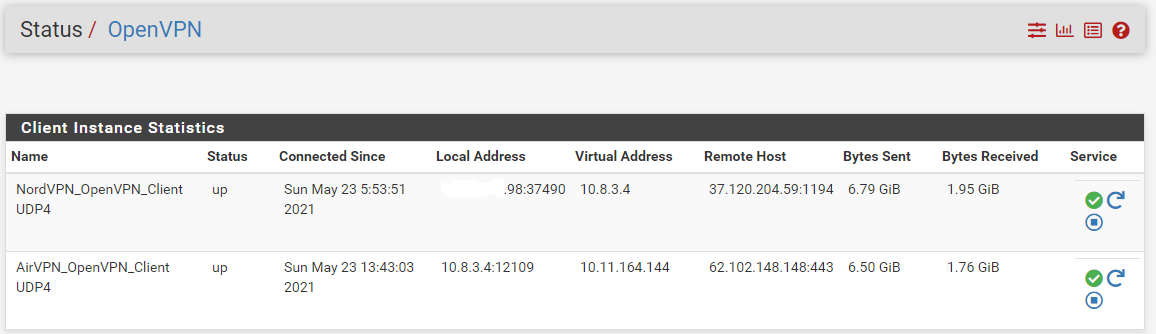
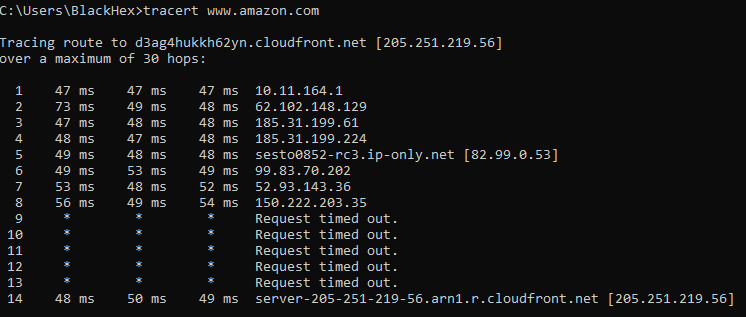
Cheers for your thoughts here, I'm operating waaaaay above my networking comfort level here and for no good reason really, its not like im running Silkroad or anything but sod it, them snoopers are going to work for their money.
-
It will only show hops on the "inside" VPN. It can't see any others.
-
This post is deleted! -
Do I actually have a nested VPN or am I sadly deluded, or even worse, am I actually sending traffic out over both VPNs in a sad mockery of my intentions?
There is already a package for nested VPN. You can check your setup/theory with it.
https://forum.netgate.com/topic/161162/openvpn-multihop-package
-
Thanks JKnott, thats what I was hoping.
John, this is very cool, im using it now and I have a connection, no fuss no muss. What I dont understand though is what this is doing compared to what I was doing before.
I can see this adds a route to the first VPN to send traffic through the second VPN, but when i look under status the local address for VPN 2 remains my WAN address, not VPN1, is it all handled in the routing table? This might be one of those maddening questions from someone over his head but what is the difference between:
Original:
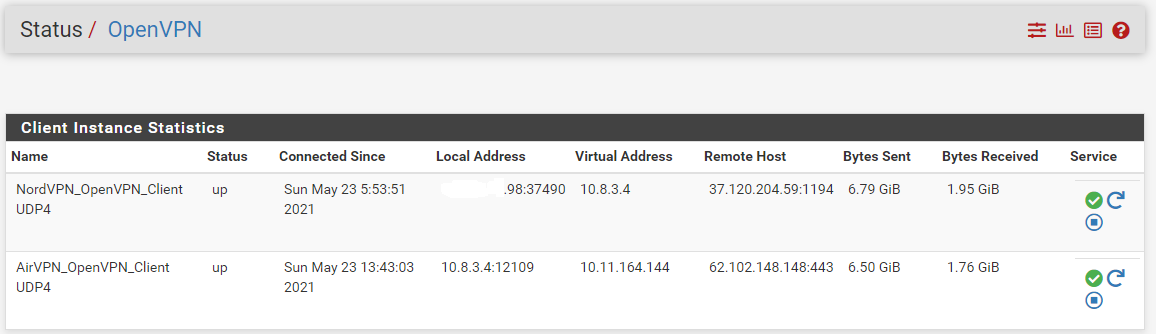
which I got by setting the interface for VPN 2 to VPN1, you can see the source for the one is the virtual address of the other.and
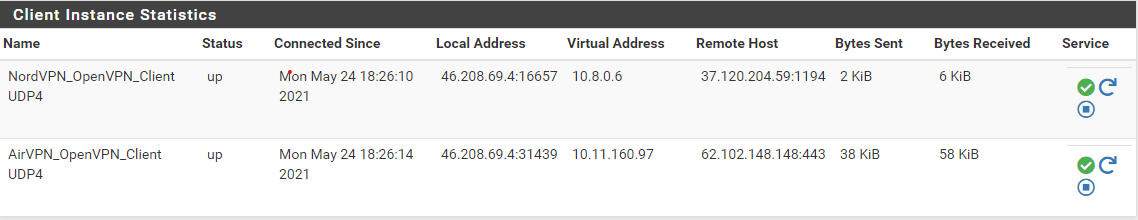
with "route-up "/usr/local/etc/openvpn-multihop/addroute.sh 62.102.148.148"If that first setup is wrong, what was it actually doing with the traffic or is this just two roads to the same destination? Thanks again,
-
There are still a few things to consider:
- OpenVPN Client:
- Set "Interface" to -> any
- "Don't add/remove routes" are set automatically by the package.
- "route-up" command is automatically set by the package
-
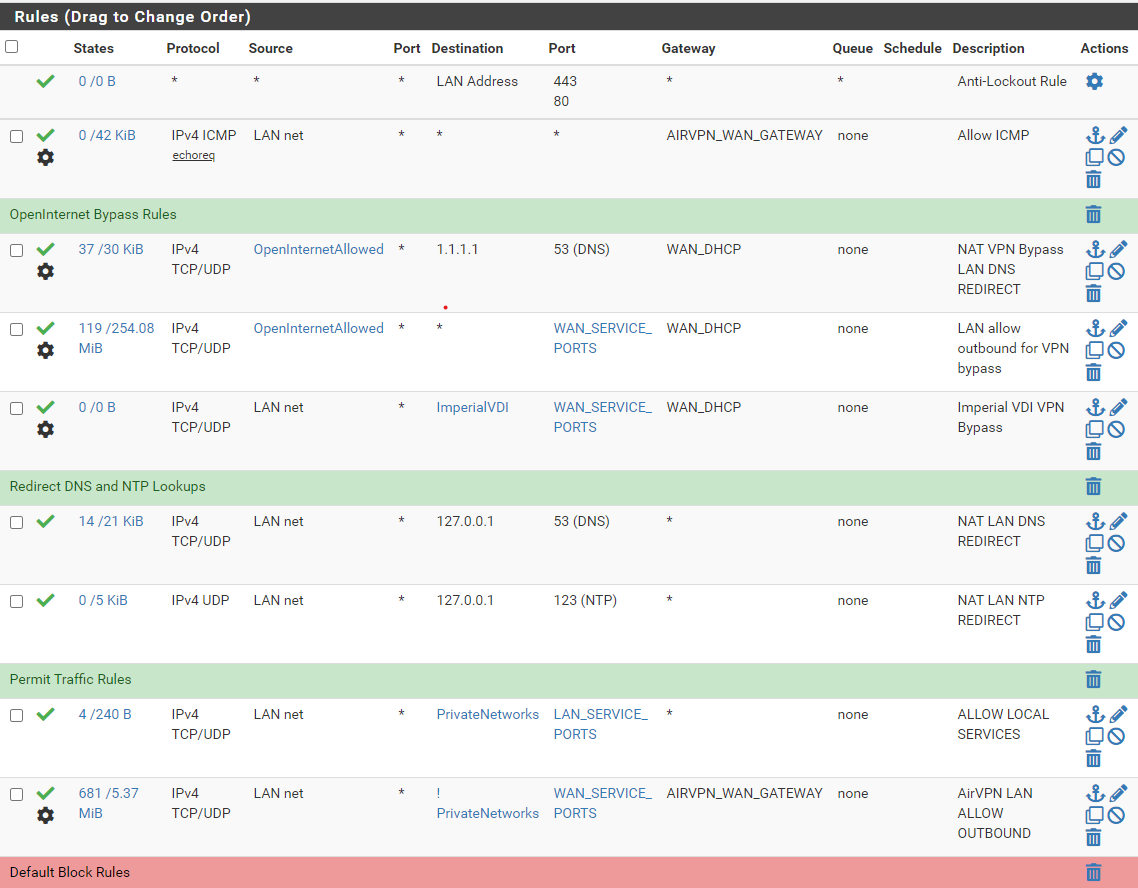
NAT rules must be present
-
Gateway for firewall LAN does not have to be set
Everything else is done by the package.
Example when AirVPN is Hop1 and NorthVPN is Hop2.
You can check the route under Diagnostics-> States.
Hop1:
Interface: WAN
Filter expression: 443Output: "WAN udp XXXXXXXXXXXXXXXX -> 62.102.148.148:443 MULTIPLE:MULTIPLE 9.23 K / 4.975 K 1.87 MiB / 2.04 MiB"Hop2:
Interface: Hop2InterfacefromNordVPN
Filter expression: 1194Output: "Hop2InterfacefromNordVPN udp XXXXXXXXXXXXXXXX -> 37.120.204.59:1194 MULTIPLE:MULTIPLE 9.23 K / 4.975 K 1.87 MiB / 2.04 MiB"Edit: The OpenVPN connection always goes via the last hop
-
Hi John
Nice one, thanks. Im still curious as to how these two methods differ, did the old method of setting VPN 2 to use VPN1 as the interface work or was it always balls? Does this package also ensure hop 2 never sees my source IP, it seems to but I just want to check.
When you say firewall rules on LAN arent needed any more, if I'm selectively routing some clients out on the clearnet, can i just deactivate "Add default route" and still use LAN rules as normal? If i do so, do I still set the VPN gateway to go out over VPN2 or is there some new nested gateway to use, would the below still work?
Your a good man John, I've found very surprisingly few good resources for doing this on Pfsense, this package seems to be a godsend...
-
I'm not an expert in this configuration myself and I don't know if I understood you correctly. English is not my first language.
If you fear IP leakage, then again there are different methods to secure that.
For example, you can add kill switch.
Another possibility would be to activate only the last hop in NAT Outbound. There are enough examples here in the forum.If you remove "Add default route" from the last hop, then selective routing is possible. Then you can use any VPN gateway in LAN->Gateway.
If you leave "Add default route" activated, then you don't have to enter anything under LAN-> Gateway.The last hop always remains the default route everywhere.
-
Hi John
Thanks again for your help here, I have found your older thread where you were discussing this and developing your ideas for this script, that is a damn fine thread btw and I'm a bit embarassed I didnt find it before... https://forum.netgate.com/topic/157520/openvpn-client-cascade/46 for anyone else reading (who is also an idiot who cant use search), its a very solid description of the process for manually setting up a nested VPN.
I will have to look into this script a bit more, it seems to automate the later steps nicely but im not sure I understand all the details, especially the "Don't pull routes" settings, more research required. All the best mate