How to tunnel VLANs over VPN
-
Hi,
I need to setup VPN tunnel to a remote office where main office has public static IP address while the branch (remote) office has dynamic address. Both offices have pfsense routers.
Through VPN I need to tunnel (currently) at least two different VLANs and keep them separated in the remote office. For one of those VLANs (i.e. VLAN 200)I don't have any control over and the only thing I can do is to tunnel it as layer 2 VLAN. At least one of the other VLANs (i.e. VLAN 150) can be normally routed through VPN tunnel (e.g. layer-3 tunnel).
And yes, I know that tunneling layer 2 is not the best idea, but I do need to do it anyway.
Here is a sketch:
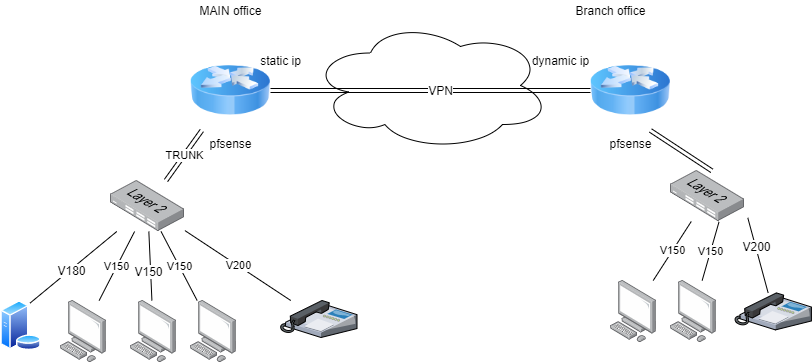
I could really get some help with directions .
- Is this possible with IPSEC?
- how do I bridge layer 2 VLAN traffic on server and on client side?
- how to tunnel VLANs separately?
- should I use GRE, GIF or l2tp for layer-2 traffic? Any hint is much appreciated.
- If I try to use OpenVPN I guess I need to establish one tunnel per one VLAN.
- Same question regarding bridging of layer 2 traffic - how to bridge it on server and on client side?
Sorry for a ton of questions, but I am still trying to grasp the optimal approach.
- Is this possible with IPSEC?
-
You can't pass VLANs through a L3 (tun) tunnel. That requires a L2 (TAP) tunnel. However, you can't use L2 if the 2 ends are in different subnets. The way to do what you want is to route the various subnets to the other end and create the appropriate VLANs. You can route as many as you want and they'll all go through the same tunnel.
-
Thanks for the comment. I am aware that I need to use L2 tunnel (like tap on openvpn).
I just managed to create OpenVPN tunnel successfully by creating server and client side tap interfaces, and then bridging interfaces on the both sides with the appropriate VLAN interface.
I don't know if there is a similar approach for ipsec (with l2tp or gre)?
-
Again, you don't have to pass VLANs through the tunnel. Just create the VLANs at each end and route the subnets appropriately.