Cast to YouTube across VLANs not working on Fire TV Stick
-
I've read countless posts on this topic and nothing has resolved this for me. In particular, the majority of posts have been focusing on Chromecasts (and a few on Roku), I haven't seen anything for Amazon's Fire TV.
What I'm trying to do is use the YouTube app on my phone (on the "HOME" VLAN + subnet) and use the "cast to device" feature to cast to my TV (on the "IOT" VLAN + subnet). This works just when I connect my cellphone to the IoT VLAN -- the "Fire TV" option is right at the very top. But when I try with my cellphone in the HOME subnet it's a no-go.
This is what I've tried so far:
-
Install and enable Avahi on pfSense. Select both the HOME and IoT interfaces in the "allow interfaces" section. Check the "Repeat mdns packets across subnets" option. Check "Disable support for IPv6".
-
In firewall rules, allow both HOME and IoT VLANs to hit IPv4 UDP 224.0.0.251:5353 and 239.255.255.250:1900
-
Set up and enable PIMD as per the instructions here (although I don't really follow part 3 of step 3 in their instructions -- is it : or something else for destination address:port?)
-
Give full access (all destinations:ports) from HOME -> IoT and IoT -> HOME
-
Enable IGMP snooping on my switch (unrelated, but thought it was worth a shot because I've read IGMP snooping or setting up IGMP proxy in pfSense helped resolve some of these issues for some people). Although this doesn't make sense as from my understanding, IGMP snooping only optimizes network traffic with a lot of broadcasts, doesn't necessarily enable additional features. And I'm not really sure if IGMP proxying is the same or not.
Nothing has worked so far. The only thing I've noticed on my HOME network after enabling #1 above (avahi + mdns repeater) is a mDNS/Bonjour service titled _amzn-wplay._tcp. which doesn't show up without avahi + mdns repeater. But cast to YouTube does not show the correct option.
I've also tried inspecting packets via tcpdump and sniffing packets via wireshark to no avail. I was hoping to contrast/compare the cases where phone + Fire TV are on same VLANs vs different VLANs but nothing of note there either.
Any help would be much appreciated as I don't want to connect the wife's phone (and my phone) to the IoT network. (She also hasn't been happy with semi-frequent outages as I move over the network from old router to pfSense
 )
)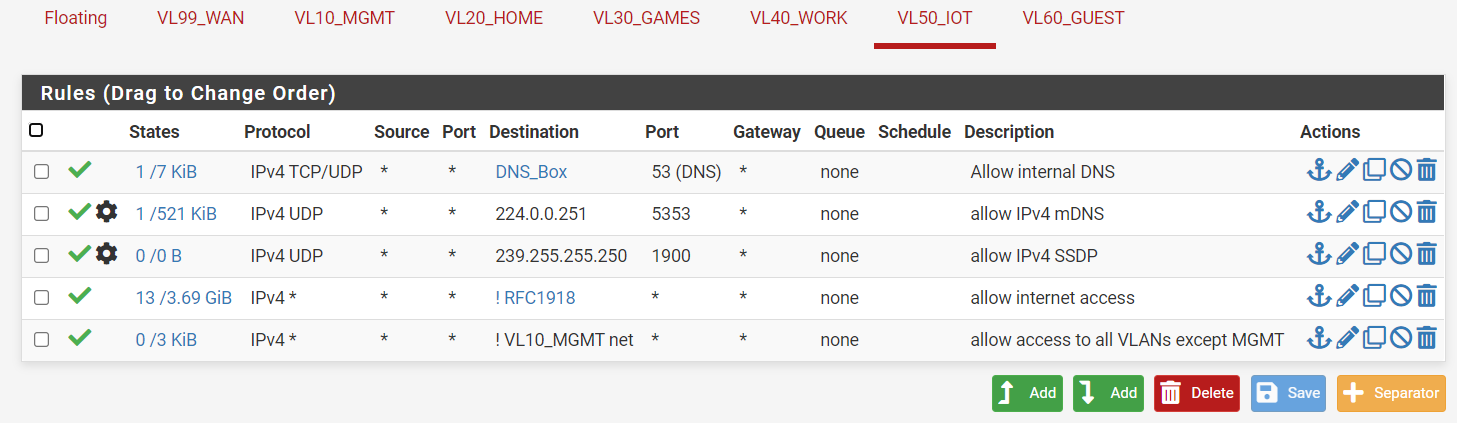
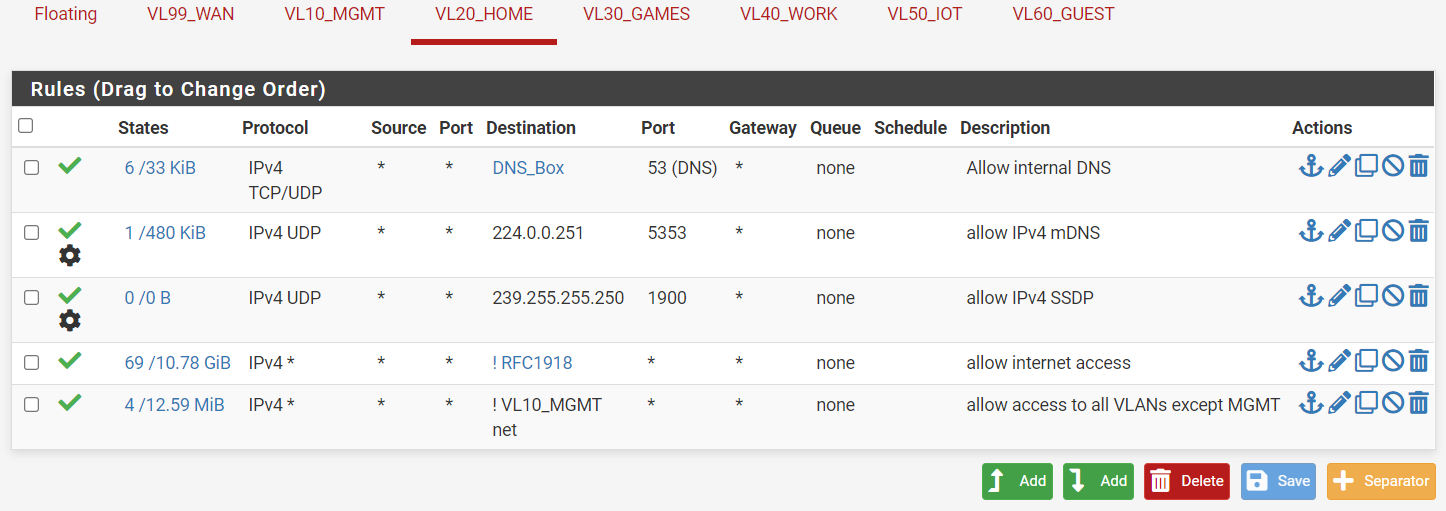
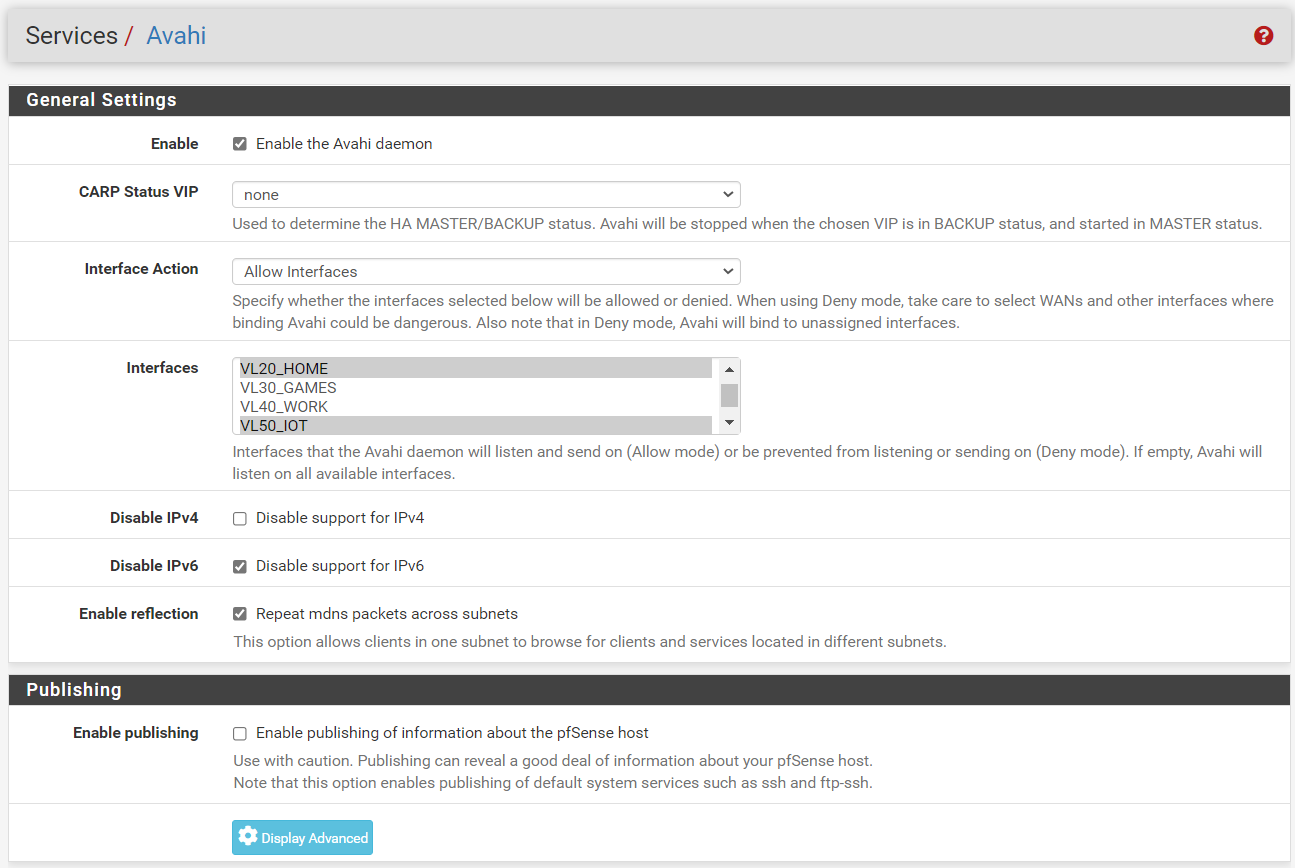
Please note in the above images my firewall settings are extremely relaxed (HOME and IOT VLANs can access everything except management VLAN) -- the reason is that I'm just trying to get this to work, and I will lock down access on the IoT VLAN when I finally get it to work.
Any help/advice would be much appreciated! And if I'm missing any configuration screenshots or details please let me know and I will provide that as quickly as I can.
-
-
@althemal I'm with you. I tried everything to get this working and failed. In the end I put them on the same vlan and controlled with firewall rules instead. Works perfectly now with firewall rules and aliases but not the solution I wanted (or the answer your looking for).
The only thing I got down to was if my switch actually supported mdns over clan but after so ended weeks trying everything I gave in and put them on the same vlan lol.
-
@althemal
I know this is not exactly the same. But it sound like Google is still involved via YouTube so it may be helpful. I fought this for a while with trying to cast from my phone on one VLAN to the chromecast on different VLAN. Eventually I came across a post suggesting to do a NAT redirect on pings to Google's DNS addresses.Firewall > NAT > Port Forward > Create A New Rule
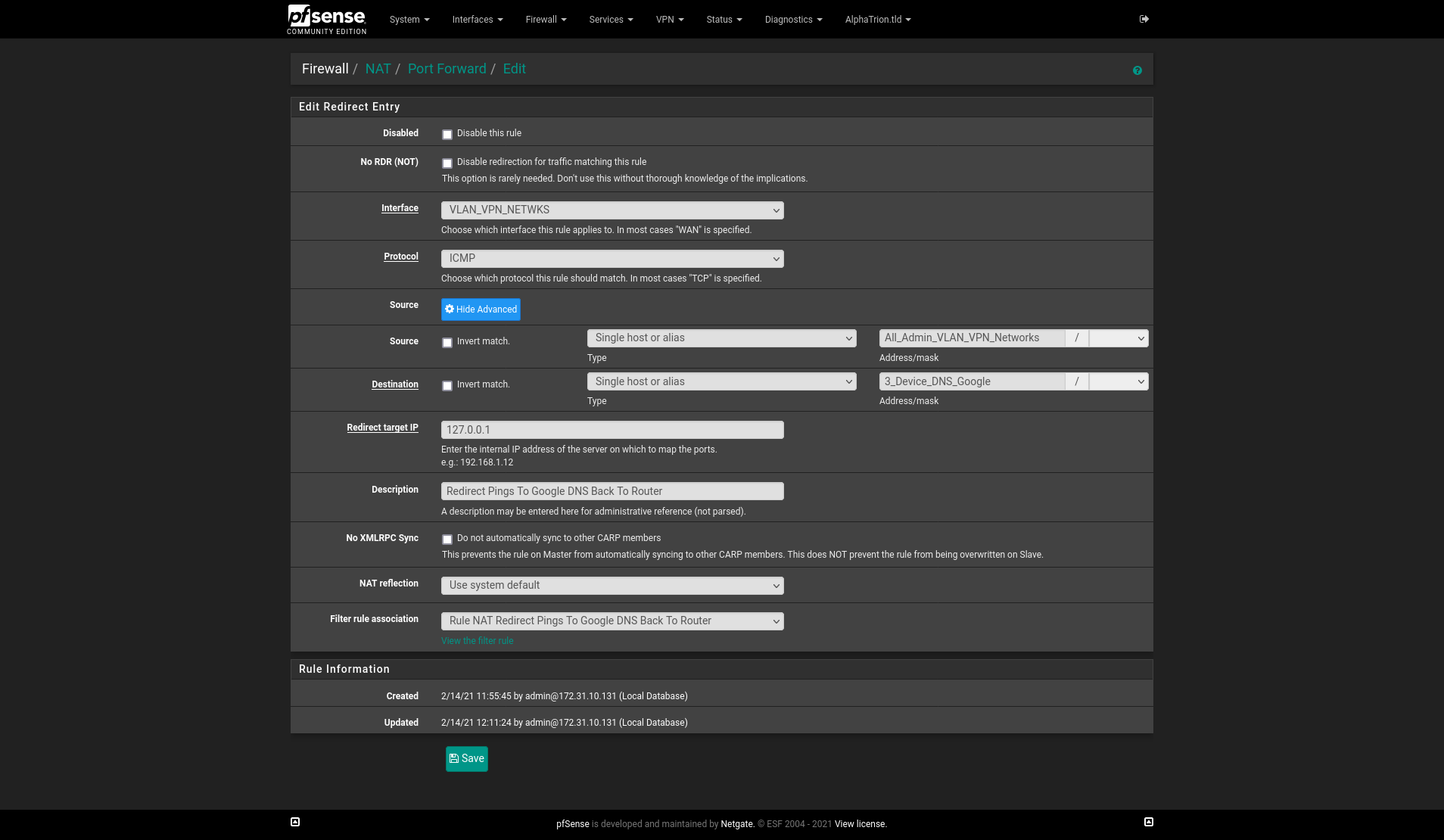
My Aliases:
- All_Admin_VLAN_VPN_Networks = My VLAN IP ranges (i.e. 192.168.1.0/24, 10.20.30.0/24, etc...)
- 3_Device_DNS_Google = dns.google (For this, I only care about IPv4 so this is basically 8.8.8.8 and 8.8.4.4)
This will create a Port Forwarding rule on the NAT > Port Forward tab. AND...
It will create a firewall rule called "NAT Redirect Pings To Google DNS Back To Router" on the interface tab selected in the image above.You will want to go to that firewall tab and drag the new rule to the correct place.
After you have saved the rule.
Now when you ping 8.8.8.8 or 8.8.4.4 pfsense should respond back and not Google's servers.For good measure I also made sure to allow access to the chomecast discovery ports (8008, 8009, and 8443). FireTV may have different ports.
Restarted my phone and chromecast; then things started working.