LAN net cannot ping through the tunnel, but OPT1 does
-
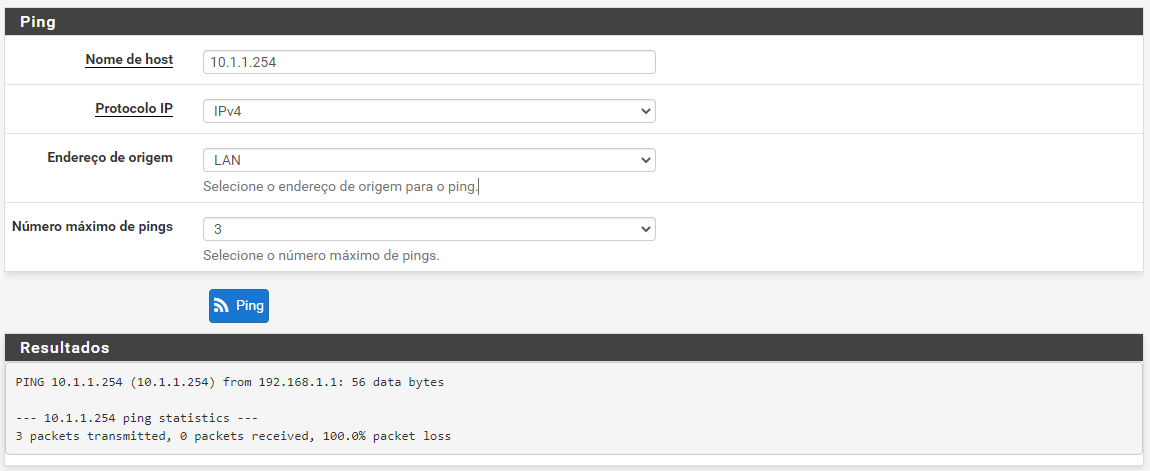
-
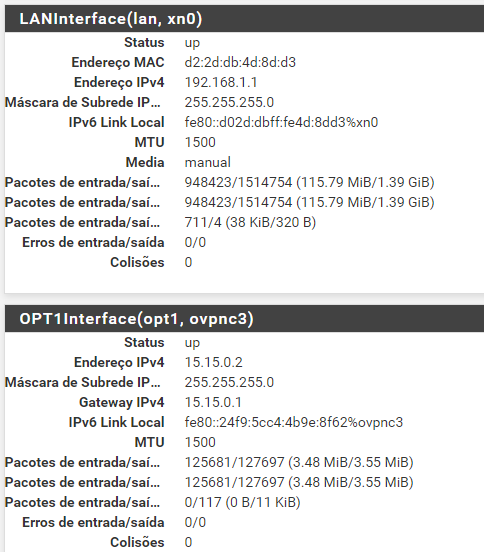
Too many unknowns. It would appear you're testing from the B side. Would need to see the config. What is the subnet assigned to the LAN interface vs OPT1? Considering pings are going thru from OPT1, are you sure 10.1.1.0/24 isn't assigned to OPT1?
This could be a simple misunderstanding or an issue with the subnet mask assigned to one of the interfaces.
I would start by revisiting the configuration on all your interfaces.
-
-
@dumpierre
I assume, 10.1.1.254 is the LAN address of pfSense at B.Possibly you're missing the route. Post the routing table, please.
Are both boxes the default gateway in their networks?
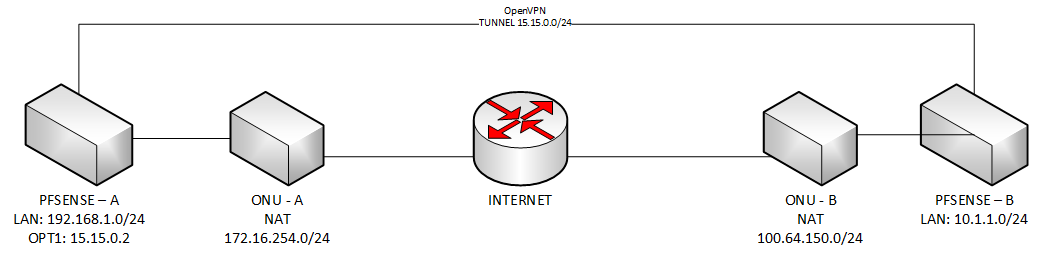
BTW: Why are you using a public address space for the VPN tunnel?
And why have you set a /24 mask for a site-to-site tunnel? You should better use a /30. -
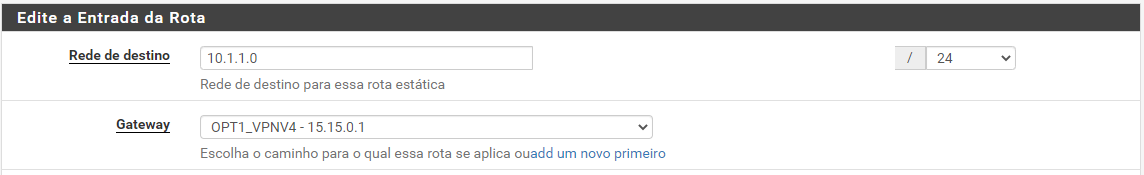
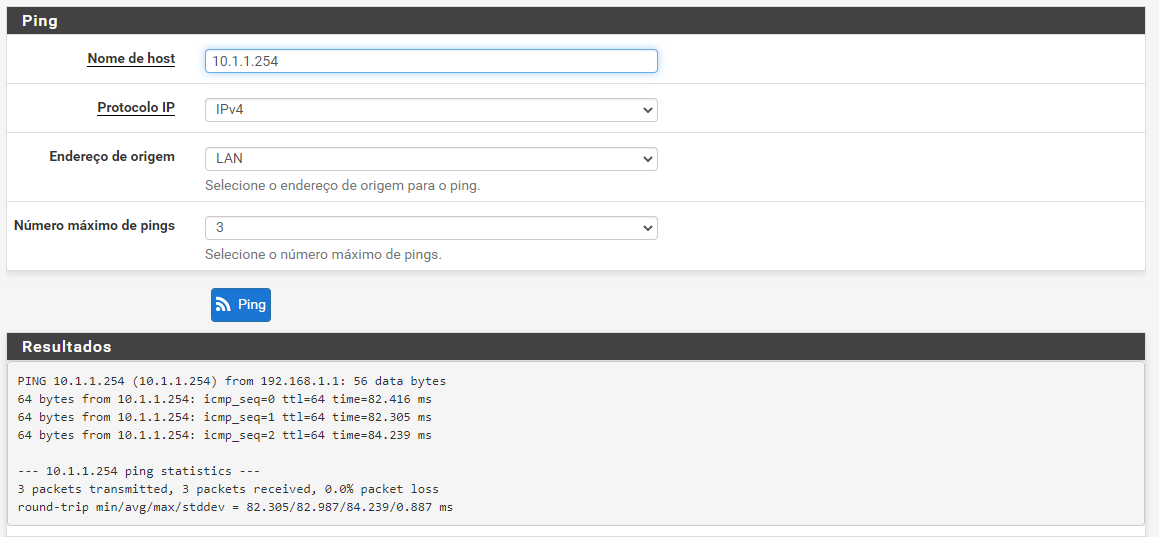
@viragomann exactly, the route was missing!
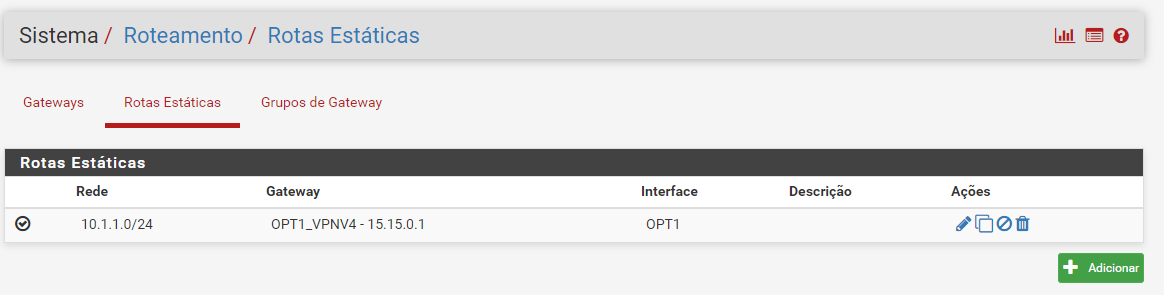
Now it's working
-
@dumpierre
You shouldn't set static routes to an VPN endpoint, even if will work.
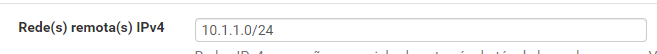
The routes should be managed by OpenVPN. So they are added properly when the connection is established.In the OpenVPN settings simply add the remote networks into the "IPv4 Remote Networks" box for adding the proper routes when connecting.
-
@viragomann hi, ivt is already configured, however, the local network cannot communicate with the remote network, only the firewall can communicate.
It worked after adding the route
No route:
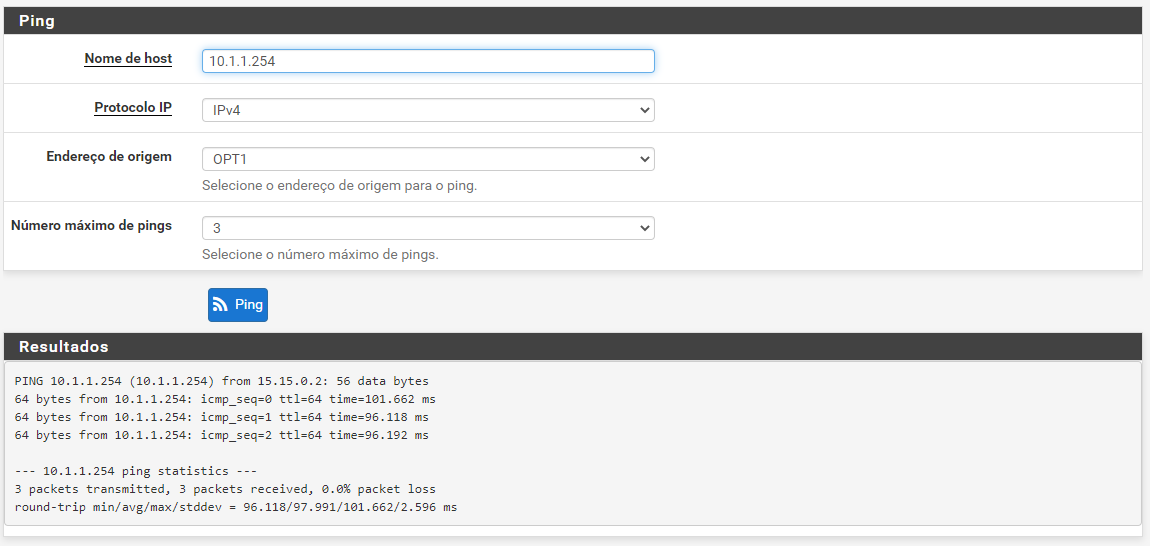
ping pfSense A to Host B: ok
ping Host A to Host B: failed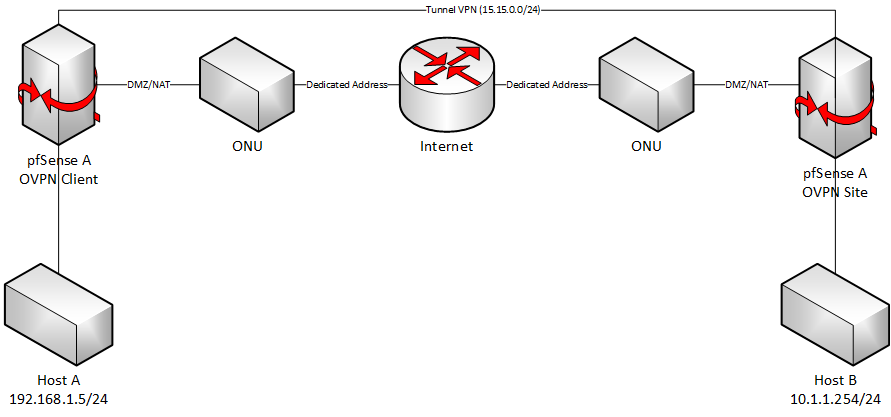
With route:
ping pfSense A to Host B: ok
ping Host A to Host B: ok