Custom IP4 List
-
pfsense 2.4.5-RELEASE-p1
pfblockerng 2.1.4_23Years back, I wrote a program to scan the mail server log for failed login attempts and check the IP for country of origin and automatically block (windows firewall) any non USA attempts after a single bad login and any USA attempts after five bad login attempts. This has been working fine.
Now playing with pfblockerng I decided to take those IP and create a IP4 list that should be blocked. pfblockerng blocks most (4460ish out of 4468) of the ips in the list but several IPs that are on the list continue to get through and are re-blocked by my program again.
I verified that these IPs are in the firewall rules list so pfblocker and pfsense know about the IP.
I am curious what would cause this. Any help in figuring out how they get by the list.
Thanks Jon
-
@jmanatee said in Custom IP4 List:
Any help in figuring out how they get by the list.
Not everybody uses 2.4.5-p1 any more.
And pfBlocker "2.1.4_23" is way to old.
maybe it's time to update your script ?Btw : if an alias with an IP like 1.2.3.4 is blocked on "WAN", the 1.2.3.4 can't access anything.
Except if there is a "NAT" firewall above this block-alias rule .....
And other 'floating' rules aside. -
pfsense says I am on the latest version:
2.4.5-RELEASE-p1 (amd64)
built on Tue Jun 02 17:51:17 EDT 2020
FreeBSD 11.3-STABLE
The system is on the latest version.
Version information updated at Mon May 31 7:15:33 EDT 2021pfblocker offers a developer version but i only run releases not betas.
The IPs in question are in a WAN alias list created by pfblocker
There are no "NAT" firewall rules above this block-alias rule.
There are no floating rules.
I have confirmed multiple time the IP is in the list.It is strange
-
@jmanatee said in Custom IP4 List:
pfsense says I am on the latest version:
Netgate Site or Get pfSense or this forum ...
@jmanatee said in Custom IP4 List:
pfblocker offers a developer version but i only run releases not betas.
Only the "3" series is maintained by the author, and after 16 revisions ( 3.0.0_16 ) now stable - IMHO.
3.0.0_16 isn't beta. It's released. -
@gertjan said in Custom IP4 List:
Only the "3" series is maintained by the author, and after 16 revisions ( 3.0.0_16 ) now stable - IMHO.
3.0.0_16 isn't beta. It's released.I guess you are saying that the failure to block an IP in a alias list is caused by the version I am running?
This would be a pretty big bug and well documented wouldn't you think?
-
@jmanatee said in Custom IP4 List:
I guess you are saying that the failure to block an IP in a alias list is caused by the version I am running?
This would be a pretty big bug and well documented wouldn't you think?The latter : very true so no bug ;)
The first : I'm saying that er are very few that are working with the "2" series. So, the chance some answers is 'as big' .... ;)
But, the issue isn't "pfblocker" here, I guess.
pfblocker is huge, but actually nothing : it prepares lists with IPs, to be fed to the firewall 'pf' and DNSBL lists, to be used by the Resolver (unbound).For the rest of the time, "pfblocker" gathers some statistics to make nice pages
If you have no WAN rules ( == no NAT rules), the default 'block all' rules blocks everything and everybody. Why adding extra rules (with aliases) ?
But, how can the mail server be reached from the outside ? How do you receive mail ?edit : please, details all lists, rules etc.
-
@gertjan said in Custom IP4 List:
@jmanatee said in Custom IP4 List:
I guess you are saying that the failure to block an IP in a alias list is caused by the version I am running?
This would be a pretty big bug and well documented wouldn't you think?The latter : very true so no bug ;)
The first : I'm saying that er are very few that are working with the "2" series. So, the chance some answers is 'as big' .... ;)
But, the issue isn't "pfblocker" here, I guess.
pfblocker is huge, but actually nothing : it prepares lists with IPs, to be fed to the firewall 'pf' and DNSBL lists, to be used by the Resolver (unbound).For the rest of the time, "pfblocker" gathers some statistics to make nice pages
If you have no WAN rules ( == no NAT rules), the default 'block all' rules blocks everything and everybody. Why adding extra rules (with aliases) ?
But, how can the mail server be reached from the outside ? How do you receive mail ?edit : please, details all lists, rules etc.
I didn't say I had no rules, I said I had no rules above the pfblocker rules. I have many rules allowing for mail server access (pop3, smtp, imap, etc) but they are all below the pfblocker rules. My understanding on how rules worked were first match top to bottom an ip or port is accepted or rejected.
Is this wrong? Why would this work for the bulk of IPs in the pfblocker alias?
-
BTW I remember why I didn't update to pfsense 2.5 there was some problem with OpenVPN, I have not looked into it since then not sure if they fixed this problem yet
-
Like this :
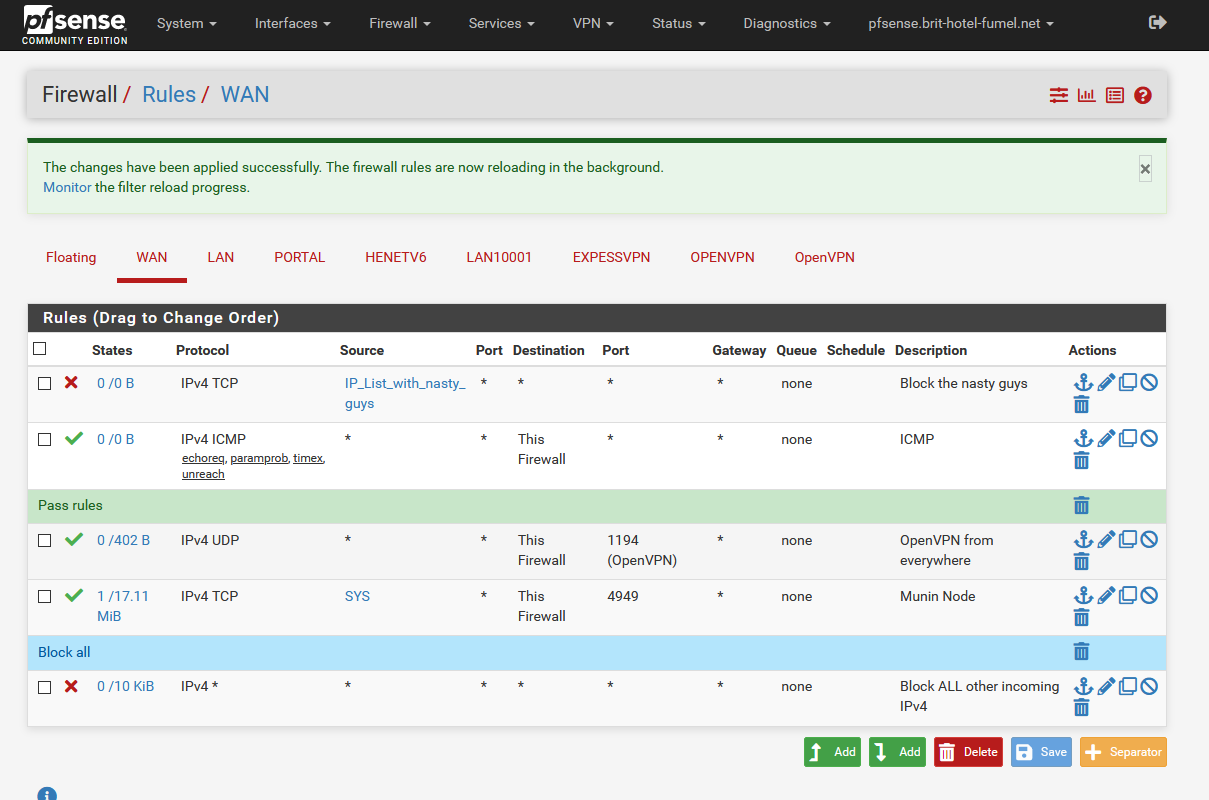
The first rule, using an Alias called "IP_List_with_nasty_guys", will block any TCP coming from the IP's present in the alias.
-
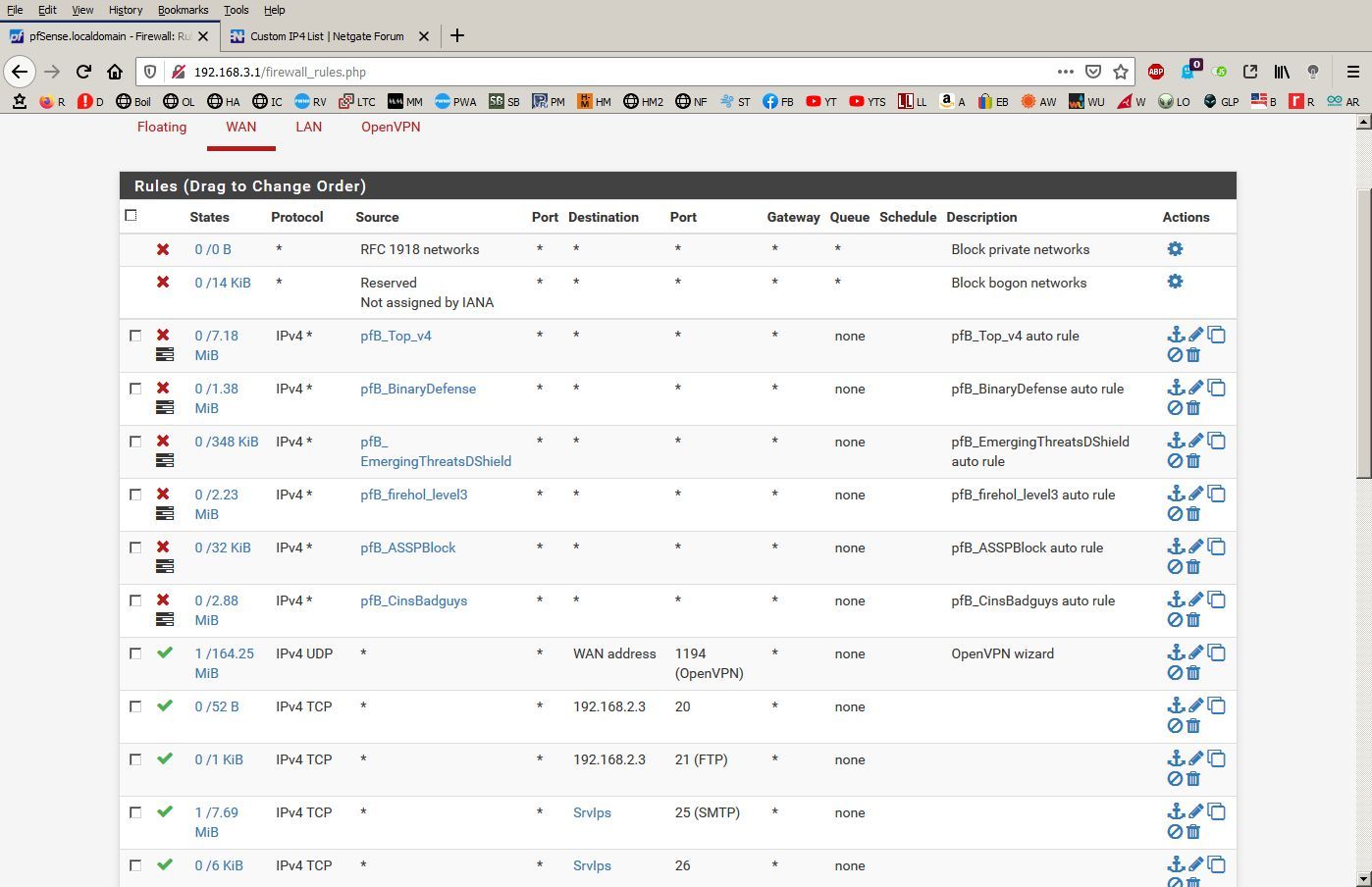
My list is the pfB_ASSPBlock, (there are several pfblocker ip4 lists) it contains the IPs in question and they still get through. Not all of them just a few of them.
-
@jmanatee said in Custom IP4 List:
My list is the pfB_ASSPBlock, (there are several pfblocker ip4 lists) it contains the IPs in question and they still get through. Not all of them just a few of them.
That screenshot shows hits for that rule with that alias. So what exactly is the problem?
-
There are like 4460 IPs on that list and some of the IPs (5-8) still get past pfsense to the server and continue attempts to login to the mail server
-
@jmanatee said in Custom IP4 List:
There are like 4460 IPs on that list and some of the IPs (5-8) still get past pfsense to the server and continue attempts to login to the mail server
Humm. That's scarry.
What if you take the IP you use when VPN-in - as I see you have the OpenVPN server.
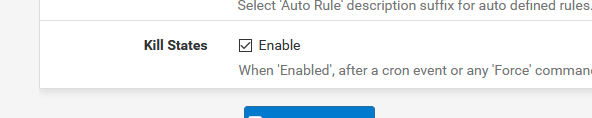
If you add your Client OpenVPN IP to the pfB_ASSPBlock, you couldn't enter anymore, right ?! The firewall wall log would show the hit.On the Firewall > pfBlockerNG > IP page, do you have this one activated :
?
Can't find another reasons ... and refuse to believe that pf, that is FreeBSD itself, is broken .... :(
-
@jmanatee said in Custom IP4 List:
There are like 4460 IPs on that list and some of the IPs (5-8) still get past pfsense to the server and continue attempts to login to the mail server
Did you actually check the content of the list IN pfsense or do you just assume it has to have 4460 IPs? Did you check the table pfblocker creates if those IPs that get past pfSense are actually in the table or somehow got filtered out?
Go to Diagnostics / Table and search your Table and check if there's the IPs/CIDR entries that went through or if they are missing. If they are missing either pfB didn't update the list or merged or optimized it with another list etc.
Also enable the logging for the pfB rules so you can better catch hits/misses of that IPs.
Cheers
\jens -
@gertjan said in Custom IP4 List:
@jmanatee said in Custom IP4 List:
There are like 4460 IPs on that list and some of the IPs (5-8) still get past pfsense to the server and continue attempts to login to the mail server
Humm. That's scarry.
What if you take the IP you use when VPN-in - as I see you have the OpenVPN server.
If you add your Client OpenVPN IP to the pfB_ASSPBlock, you couldn't enter anymore, right ?! The firewall wall log would show the hit.On the Firewall > pfBlockerNG > IP page, do you have this one activated :

?
Can't find another reasons ... and refuse to believe that pf, that is FreeBSD itself, is broken .... :(
Yes it will definitely block me on vpn I have done that accidentally a couple times.
Kill states was not enabled, I enabled it I will continue to watch it.
This was probably the problem.
Thanks