Portforwarding on WAN next to VPN configuration
-
Hi all,
Summary of my situation:
2.5.1-RELEASE (amd64)
virtual dedicated machine (VM ware)
running pfsense ~3 years
pfsense serve as primary router with no ISP router in between (only dumb 'modem')
~50 clients
DHCP working correctly
dynamic DDNs setup (dynDNS and duckDNS)
DNS resolver going out through VPN tunnel (all traffic) while using pfsense internal DNSCurrently all of my traffic is tunneled through VPN (Nordvpn) with LOAD BALANCING ACROSS MULTIPLE VPN’S (round-robin) through a gateway group. This works quite nice (the 2.5 update broke all TCP VPN connections and i cannot resolve this with all possible solutions found on this forum as well as the 2.5 nordvpn guide, but hey, i am fine with UDP for now and this is not the core of my question).
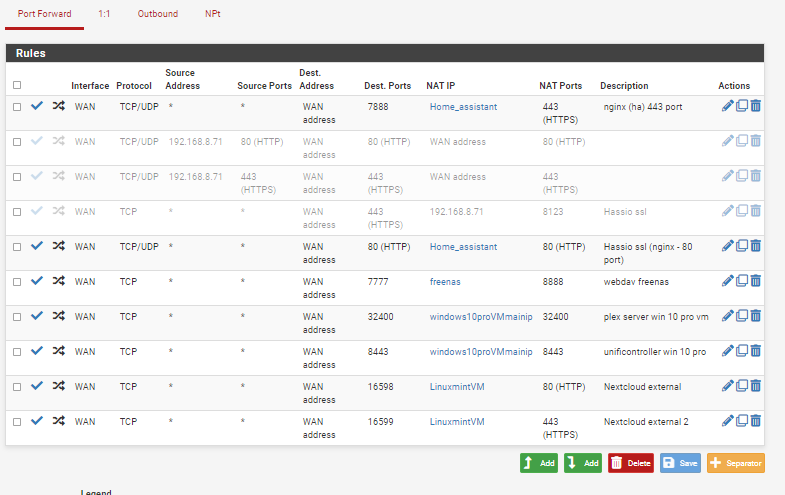
screenshot of NAT - PF:
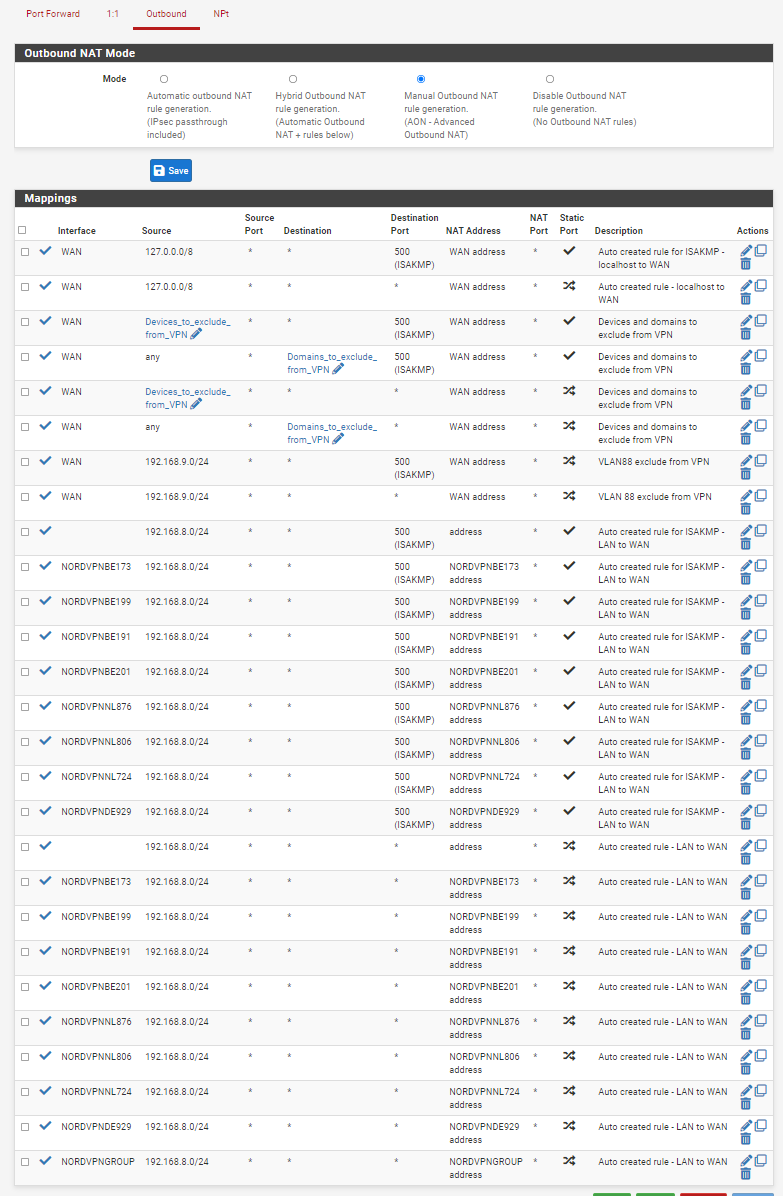
screenshot of NAT outbound:
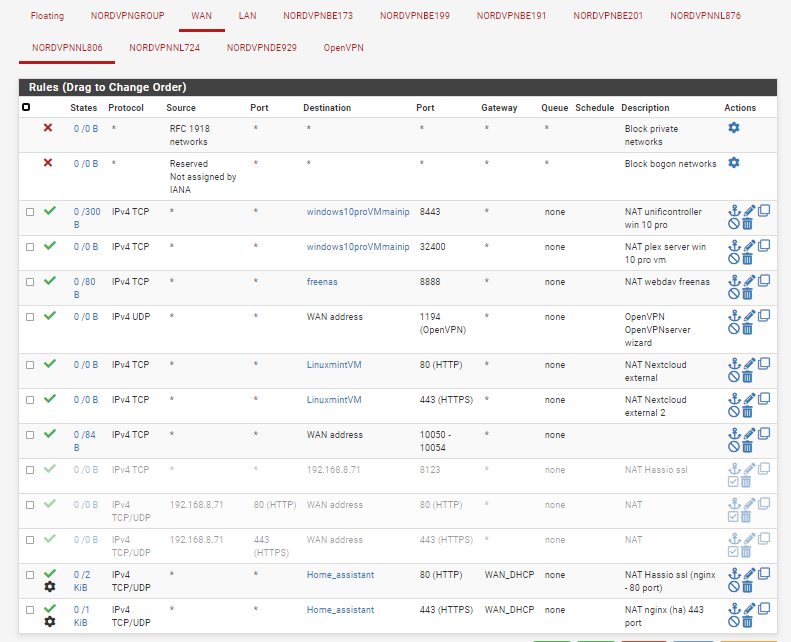
screenshot of firewall rules - WAN
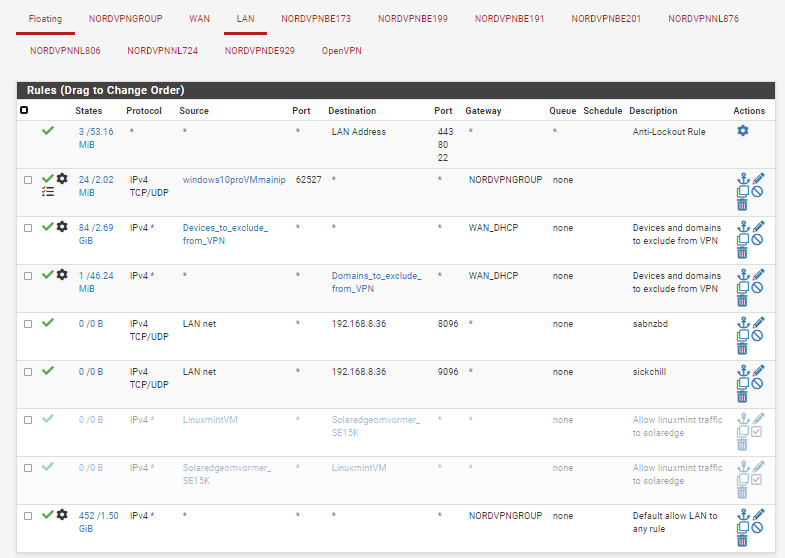
screenshot of firewall rules - LAN
To configure everything I based myself mostly on the following 2 guides (link and link2)
To access my home assistant virtual machine i need to open two external ports (7888 and 80) on the WAN (with nordvpn it is not possible to open ports over their vpn connection), which i thought is no problem as i can easily exclude certain hosts from the VPN, ergo i added my home assistant VM to the devices to exclude from VPN (this works flawlessy for all machines in there) and then i added the port forward rules for the home assistant instance, but helas, none of the forwarded ports are open (checked with online port checker as well as with the program that should gain access through this port). It is simpy not opened. Upon deeper inspection, none of the ports that are port forwarded on the WAN are forwarded.
Per the troubleshooting guide i checked several things (i made sure everything was correctly set, including the gateway) but nothing worked for me (several restarts etc).
One last thing I can think off is that this simply does not work when having the VPN tunnel as the default gateway, would there be a way around that (besides specifying the gateway under the fw rule)?
Any help would be greatly appreciated!
Thank you and kind regards,
Ben
ps, first post so please forgive any faults in this post.
-
@blvermeu said in Portforwarding on WAN next to VPN configuration:
One last thing I can think off is that this simply does not work when having the VPN tunnel as the default gateway, would there be a way around that (besides specifying the gateway under the fw rule)?
It doesn't work on 2.5.1 due to this bug: https://redmine.pfsense.org/issues/11805
But it should work well on 2.5.0 and 2.4.5.
However, why do you need the VPN as default gateway, since you policy route the VPN traffic anyway?
Simply check "Don't pull routes" in the VPN client settings and modify your firewall rules if needed. -
@blvermeu said in Portforwarding on WAN next to VPN configuration:
round-robin
This will be fixed on version 2.5.2. Maybe there are some patches to fix it by now. Did you check this?
-
@viragomann said in Portforwarding on WAN next to VPN configuration:
@blvermeu said in Portforwarding on WAN next to VPN configuration:
One last thing I can think off is that this simply does not work when having the VPN tunnel as the default gateway, would there be a way around that (besides specifying the gateway under the fw rule)?
It doesn't work on 2.5.1 due to this bug: https://redmine.pfsense.org/issues/11805
But it should work well on 2.5.0 and 2.4.5.
However, why do you need the VPN as default gateway, since you policy route the VPN traffic anyway?
Simply check "Don't pull routes" in the VPN client settings and modify your firewall rules if needed.Thank you, that is indeed a good remark, i'll try and play with this go get the WAN as default. I guess in the past I wanted all traffic to go by default on the VPN and only by exception via WAN, but i might rethink this strategy. On a different note, i was not fully aware that the default gateway for VPN was not required (when doing policy routing), i'll also try to take a look at this.
@viniciusmerlim said in Portforwarding on WAN next to VPN configuration:
@blvermeu said in Portforwarding on WAN next to VPN configuration:
round-robin
This will be fixed on version 2.5.2. Maybe there are some patches to fix it by now. Did you check this?
Thanks so much both for the feedback. It's good to hear it is going to fix itself eventually, i will nurture some patience meanwhile. Do you have any idea when the next updates that will address these issues will be 'public' and by public i mean not in Beta... :-)?
Thank you and kind regards!
Ben