Why doesn't this rule work? Or are the logs going mad? Or ???
-
Today I'm seeing strange firewall log entries. Things which were previously not being blocked are today now getting blocked. It's really strange. Perhaps the logs are erroneous?
Here's a rule that worked for 1+ year. It's on my VPN interface. Basically, allow all traffic, right?
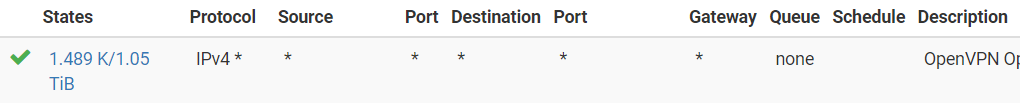
But today log entries showed things were being blocked and I decided to use the Easy Rule to add this entry (which I feel should be unnecessary)
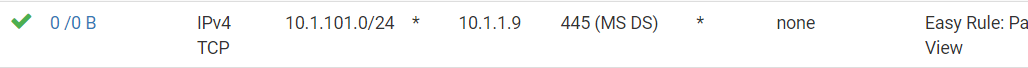
And more log entries of things being blocked on this interface started appearing too. Other destination IPs and ports. So I added more Easy Rules. But so far, none of those new entries show states or traffic counts.
So ... did some rule magically break? Are the logs going haywire?
-
@cfapress Maybe if you showed us what you're seeing in your logs, we might have an answer. Showing rules that used to work tells us nothing.
-
@kom here are two entries which, to me, shouldn't be here.
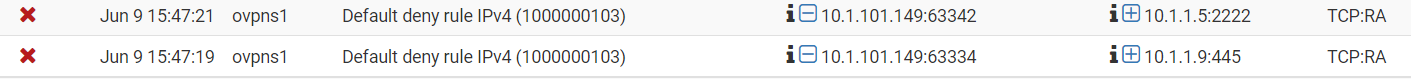
And I'm now noting the TCP flags. Admittedly I'm not too fluent on their significance. But I don't typically see TCP:RA
-
@cfapress Those are out of state packets being blocked. Nothing to be worried about.
-
@kom Thanks for clarifying.
I'm also noting that some of my staff who are connected to our LAN are also connected to the VPN. I figure that could be causing some of the odd log entries. I'll be reinforcing they don't need to use the VPN while being on-site at our offices.
-
@cfapress That specific entry shows a Reset-ACK being blocked. Looks like your end issued a reset, the far end replied back with an ACK, but since pfSense had already torn down the connection and deleted all established states with that end, the reply ACK was considered a new connection attempt and blocked.
-
@kom said in Why doesn't this rule work? Or are the logs going mad? Or ???:
Nothing to be worried about.
Not sure I would say that.. A few here or there than yeah prob not.. But if your seeing a lot of them - prob a good idea to track down that is causing them.
Could be your states are being reset, wan going down can do that if you set pfsense to do that - which I believe is default.. IP change on wan another thing that could reset the states.
If a lot of them - could be asymmetrical traffic flow, etc.
A few here or there are normal with how tcp works and especially wifi devices trying to leverage an existing state after switching from cell to wifi, etc.
But if seeing a lot of them - I would investigate to why vs just blowing it off.