PfSense behind ISP modem/router combo
-
Not sure if this is the correct area to post. I’m having issues with some of my features such as my VPN and port forwards getting through to the public internet.
My setup has the ISP combo connected to the WAN port on the pfSense box and then the 4 ports on my pfSense are all slotted for my 2 EoP adapters. Notninf super complex.
The VPN uses the outbound WAN address given by the ISP combo. I know it’s properly setup as I can connect at the house but when I’m out on public WiFi I still seem to have issues. I’ve set the firewall rules to allow inbound traffic of any type for the VPN and I also port forwarded the correct ports for the VPN on the pfSense box and my ISP combo.
-
@cmos_battery said in PfSense behind ISP modem/router combo:
are all slotted for my 2 EoP adapters
 End of production? End of page, ...?
End of production? End of page, ...?Is pfSene the default gateway in your LAN?
@cmos_battery said in PfSense behind ISP modem/router combo:
I also port forwarded the correct ports for the VPN on the pfSense box and my ISP combo.
If pfSense is your main firewall, forward the whole traffic to it.
Then check if you get the packets on pfSense WAN interface. To investigate you can use Diagnostic > Packet Capture.
-
@viragomann
Ethernet over Power adapters. It is my main firewall, I’ve been turned my ISPs combo firewall off but still seem to have issues.I will try and see where the packets end up with wire shark.
-
@cmos_battery
You mean PoE (power over Ethernet).Just check if the expected packets arrive on the WAN interface using Packet Capture. Possibly they are blocked by the ISP or you are within a CGN.
-
@viragomann
No I meant exactly what I said, Ethernet over Power is provided by adapters translating the ethernet over bare copper in the house from one module to the other. Another name is Powerline Adapters, good stuff, my adapters do 1GB.I'm getting the packets like expected, I'm mostly like going to work with an experienced network admin I know and ditch OpenVPN. Its never worked for me and feels like a hassle. I'm mainly aiming to tunnel to my house from college to access my hypervisor cluster and my windows 10 PC's on the domain. An IPsec & L2TP would be better for my use case, though I know they are another world of pain at least I'd get better transfer rates and the admins at my college use them so I'd be able to get their support.
-
@cmos_battery said in PfSense behind ISP modem/router combo:
I know it’s properly setup as I can connect at the house
From where exactly? What subnet?
If you can connect from the LAN side of pfSense to the OpenVPN server then the client is probably using the local WAN IP rather than the external address which is why it fails in other locations.
Though if though was the case you would not see openvpn packets arrive on the pfSense WAN.OpenVPN is generally far more flexible. If you can't get that to connect using L2TP over IPSec is only going to be more difficult. It may well ultimately be faster though as you say.
Steve
-
Here is my topology. My combo sits in front with the 192.168.1.1 as the LAN address, 192.168.1.94 is the outgoing WAN for the pfSense and uses the combo as the gateway. The pfSense has 192.168.2.1 as the LAN and then branches off throughout the house by means of switches in different rooms and powerline adapters. The combo unfortunately has to stay at the front and cant be replaced since it uses ethernet as the WAN and the ISP configured the TV set boxes to only accept MoCa signals through additional MocA adapters they gave us. The pfSense box has its DHCP server turned on so all the computers and servers I have are connected under that as well as my google mesh WiFi. Should I disable DHCP and should I be looking to disable NAT so I don't have a double NAT situation. As it is I'm not even able to port forward my PC's for certain services and games.
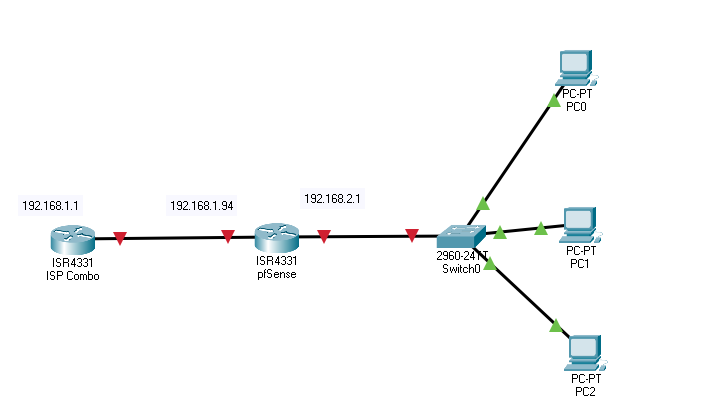
-
Uggh! Double NAT. Put your ISP's device in bridge mode if you can.
-
@jknott
The dreaded recommendation. This ISP device has me scratching my skin looking at it. SOOOO I cant put it in bridge mode. Honestly there's not a terrible amount this thing even does and my ISP hasn't blocked off any features.EDIT: ok, ok so its not a combo. My provider uses only fiber when doing installs. It looks like the modem is mounted outside and clearly its going be way above what I've learned in my CIS classes. "Dual-Band Wireless AC/N VDSL2 Bonding Gateway" is the exact description of the device. Its NAT has no option to turn that off. Probably out of luck
-
@cmos_battery
The double NAT is not an obstacle for running OpenVPN behind, as long as you get the packets forwarded properly.Did you allow the VPN access on the WAN interface?
Assuming, your combo does masquerading on inbound traffic (some crappy consumer routers do this perilous operation by default, maybe it's possible to disable it), you have to go into the WAN interface settings and remove the check from "Block private networks".
If you still have trouble, please provide details about you OpenVPN configuration, your WAN rules, NAT rules and a capture of the WAN traffic when you try to connect from outside.
-
@viragomann said in PfSense behind ISP modem/router combo:
The double NAT is not an obstacle for running OpenVPN behind
Very true - but users have issues with configuring their isp device doing nat in front of pfsense, and with the export of config where it gives the wan rfc1918 address vs the actual public IP.
-
@cmos_battery said in PfSense behind ISP modem/router combo:
I'm getting the packets like expected
What packets are you getting exactly?
What I would do here is run a packet capture on the pfSense WAN for the port you have OpenVPN running on (1194 by default). Then try to connect to it via some external network, using your phone as a hotspot for example. Make sure you see that traffic arriving on WAN from the expected external IP.
If you don't then the ISP device is not correctly setup.Switching to L2TP over IPSec is not going to help here IMO.
Double NAT will work fine for almost everything. One thing that will fail is UPnP and many games are unfortunately (and inexplicably!) completely reliant on it. It's a significant security risk anyway which is why UPnP is disabled by default.
Steve
-
I’ve set in the OpenVPN wizard the two checked boxes at the end to enable it for the firewall and WAN. In addition, I did go ahead and removed the checked boxes for Bogon networks and private networks. My virtual network is 10.2.0.0/24. I’ll have to get off work and provide some more details and look through all the info and get pictures.
-
Block bogon or private networks should not normally make any difference. It would only change anything if the ISP device was source NATing forwarded traffic which is unlikely.
If the ISP devic has ever forwarded any OpenVPN traffic you should see state creation on the firewall rule on WAN. That gets cleared if you rebooted though.
-
@cmos_battery said in PfSense behind ISP modem/router combo:
I did go ahead and removed the checked boxes for Bogon networks and private networks
With @stephenw10 - why? So amounts to randomly clicking shit, in a hope to get something work ;)
In what scenario would you hitting your wan for vpn access via a bogon or rfc1918 address?
-
I’ll probably just have to drop attempting the VPN, I’m stuck in a bit loop of being able to access the it from the ISP router but nothing seems to be able to ever get outside when I’m on the public networks.
I’ve created a port forward on the ISP device but lately it seems I can never get ports to open or get my port checkers to see them. Probably just a shit should we of a network I.
-
This isn't rocket science... You have a public IP on your isp router 1.2.3.4 lets say, you forward UDP 1194 to your pfsense wan IP.. 192.168.1.50 for example.
Now you hit 1.2.3.4 from your client on 1194...
-
Well if that was the case I wouldn’t be in said position. I’ve used the wizard to create the OpenVPN, I’ve allowed bogon and private networks. I’ve used the pre done firewall and NAT rules, port forwarded the OpenVPN port to the WAN.
The main issue is that neither the ISP device nor the pfSense will open ports.
-
If you can hit the OpenVPN server and connect when you client is in the 192.168.1.X subnet then pfSense is configured correctly.
Either the ISP device is not setup to forward the traffic to pfSense or the client is using the pfSense WAN IP to try to connect, 192.168.1.94. Obviously that won't work externally.
If you used the OpenVPN client export package what did you set 'Host Name Resolution' as?
By default it will use the WAN IP directly which would fail in your case.
Check the client connection logs. Be sure it's connecting to the real public IP.It should definitely be possible to get this to work with a little troubleshooting.
Steve
-
@stephenw10
Currently its using the interface IP address which would probably be the WAN. There are 3 other options; Multi-WAN IPs, Multi-WAN DDNS, and then installation hostname. Which should be used? Is there a way to specify my publics IP address rather?