DMZ configuring
-
Hi all,
Need a bit of advise here. I have the following setup:
ISP --> PFSense Firewall <---> (unifi - firewall/gateway/security device) USG-Pro4 <--> LAN, while this works for being able to browse etc I need the PFSense Firewall (lets use an ipaddy range which is not the original but for discussion purposes) to be able to get back into the LAN to ship logs to a server in the LAN
So lets say the PFSense is 10.0.0.1, the WAN port on the USG-Pro4 is 10.0.0.2 and then the LAN is 10.0.1.x
I have a log server sitting on the LAN 10.0.1.4 I need the firewall 10.0.0.1 to be able to push logs to that server on 10.0.1.4. Right now the firewall (10.0.0.1) can't even ping the USG-PRO4 IP 10.0.0.2. The USG-PRO4 can ping the firewall on address 10.0.0.1 but the Pfsense cant ping the USG-Pro4 on 10.0.0.2 . I would like some advise please on how I can get the firewall to ping (connect) to the log shipping server sitting at 10.0.1.4.
It use to work I am not sure what i broke :) but would appreciate the guidance.
-
Does the USG allow (respond to) pings on its WAN? Many routers do not by default.
It sounds to me like you need to set up port forwarding on the USG, so the pfSense connects to 10.0.0.2:1000 (whatever port your system uses) and the USG forwards that to 10.0.1.4:1000.
The pfSense isn't going to be able to ping 10.0.1.4 directly because using NAT in the USG is essentially blocking it.
-
@steveits said in DMZ configuring:
The pfSense isn't going to be able to ping 10.0.1.4 directly because using NAT in the USG is essentially blocking it.
Thank you for taking the time to respond. So the USG doesn't respond to any pings. I will check the settings on the USG, I dont see anywhere on the "GUI" will check on the Unifi forums how to enable this.
The thing is that the Pfsense can't even ping the WAN ip address (10.0.0.2) of the USG so pointing the Pfsense to that IP and Port in this case if I understand correctly, wouldnt make a difference. -
@carlos-magalhaes
Apart from the pinging the USG issue, you should be able to route the traffic to the network behind it by adding a static route to pfSense.
Add the USG WAN IP as gateway in System > Routing > Gateways. Then go the the Static routes tab and add a route for 10.0.1.0/24 (or only for 10.0.1.4/32 if you want it restrict to the server) and use the USG gateway.However, you might have add rules to the USG to pass the traffic.
-
@viragomann said in DMZ configuring:
However, you might
Thank you again for the help. So this is what I have (its not working so my config is wrong some how):
I have two gateways one on the WAN interface for internet and One on the LAN interface which is set to 10.0.0.2 (the USG).
Then on static routes I added:
Destination Network being 10.0.1.0/24
The GateWay is set to the USG 10.0.0.2 (which is the gateway I created for the USG).If I disable the WAN gateway (Just for testing) all is good Pfsense can ping through to 10.0.1.4, if I enable the WAN gateway and do a traceroute if I ping 10.0.1.4 it goes out to the internet to resolve.... even though the interface for the WAN Gateway is the WAN interface.
As soon as I disable the WAN Gateway then I can ping and traceroute back to the 10.0.1.x network.
This is probably obvious but getting confused right now would appreciate the insight.
Trying to get it to focus on anything for the internet uses the WAN Gateway anything looking for 10.0.x.x goes back to the USG Gateway.... -
@carlos-magalhaes
Seems as the static route does not work. Maybe it's set wrong.
Did you add the gateway in the interface settings instead in the routing settings?Post the routing tab, please, so that others can get a view of it.
There is no need to obscure your internal networks or use aliases, since they are not accessible from the internet anyway. -
@viragomann Thank you again,
Sure thing so let me post some screenshots:
I set the gateways and the static routes under > System > Routing > Gateways and also the Static Route Tab.
-
@carlos-magalhaes
The WAN GW is a public IP. This should be hidden though.The LAN gateway is disabled in this screenshot. I assume, you did it, cause it didn't work.
Apart from this and the new subnets all settings seems correct.Enable both gateways again. If it does not work, post the IPv4 routing table, please.
-
@viragomann said in DMZ configuring:
@carlos-magalhaes
The WAN GW is a public IP. This should be hidden though.The LAN gateway is disabled in this screenshot. I assume, you did it, cause it didn't work.
Apart from this and the new subnets all settings seems correct.Enable both gateways again. If it does not work, post the IPv4 routing table, please.
The WAN GW is a public IP. This should be hidden though.
Its a public gateway that is publicly accessible
-
@carlos-magalhaes said in DMZ configuring:
This is the default gateway setting. But good to see it. Here you have to select the WAN gateway.
In the settings of the LAN gateway (System > Routing > Gateways > edit gateway) you have to enable it at the top.
Hmm. The screen not showing something useable.
-
So there is the gateways showing and both the WAN and LAN gateways are showing as enabled (if that's what you meant)
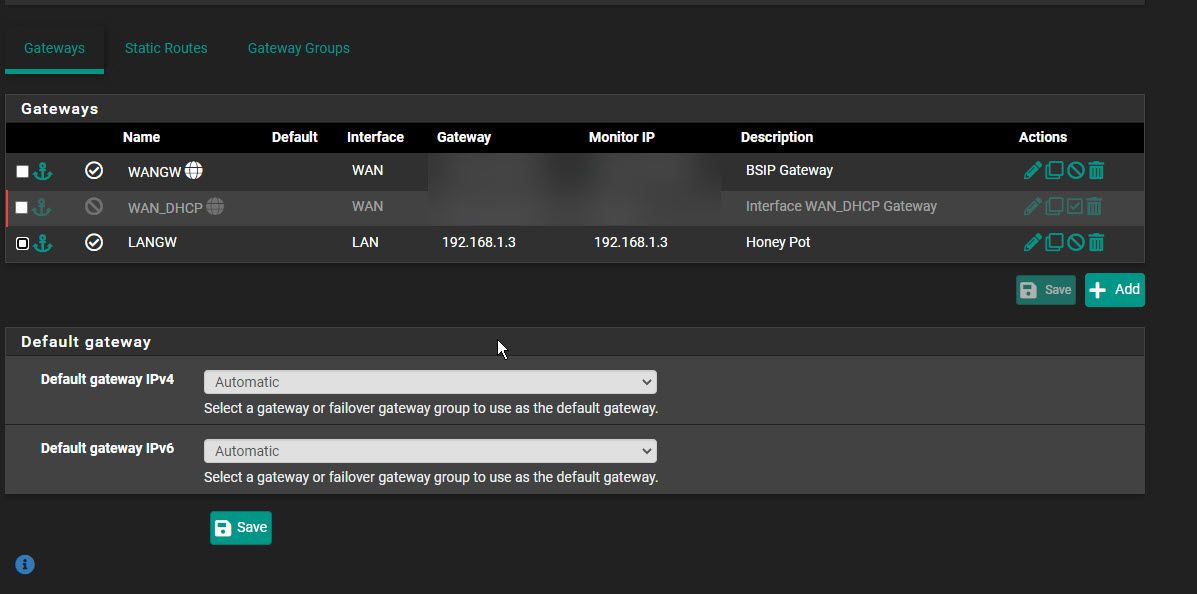
Hmm. The screen not showing something useable.
This was the routing under >Diagnostics > Routing
-
@carlos-magalhaes
Yes, seems ok.
In the gateway screenshot it looks like it was disabled. -
If I disable the WAN gateway (which I see is set as default), of course the internet drops but I can then ping the 192.168.9.x network via the USG on 192.168.1.3. As soon as I enable the WAN gateway and do a traceroute for 192.168.9.x it sends it out via the WAN gateway and tries to find that IP via the WAN Gateway
-
@mynetworkrocks
So again, the route might be not correct. So enable both gateways and the static route and check the routing table.The screenshout you've posted does not show a proper entry.
-
@viragomann said in DMZ configuring:
@mynetworkrocks
So again, the route might be not correct. So enable both gateways and the static route and check the routing table.The screenshout you've posted does not show a proper entry.
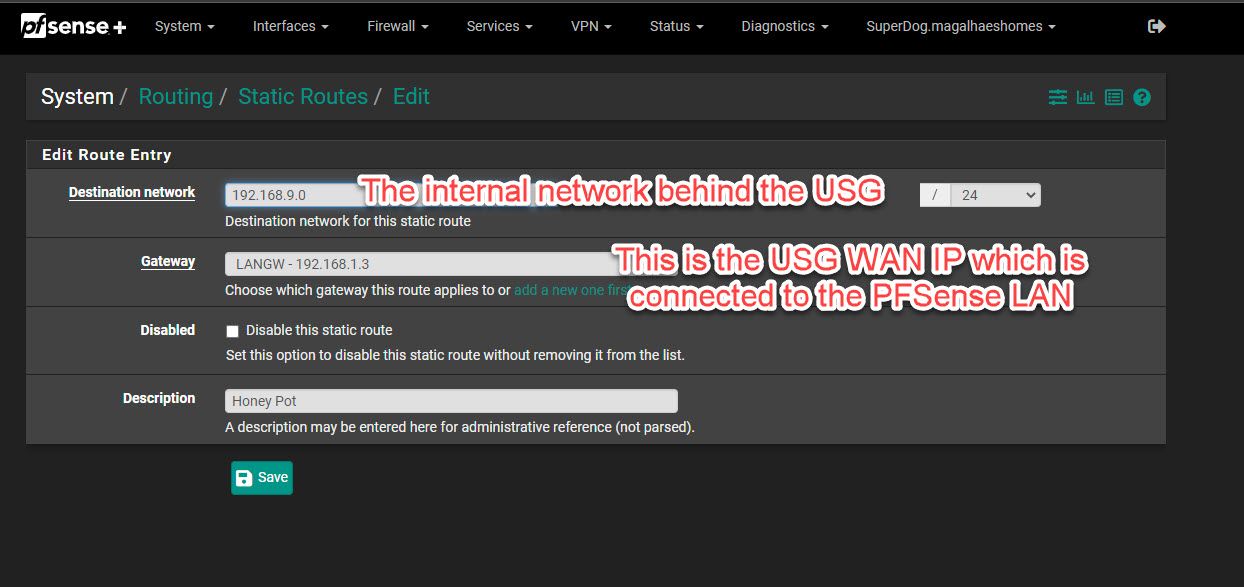
So here is the static route, the destination network is the LAN behind the USG, the USG is 192.168.1.3, the LAN behind the USG where the log server I am trying to get to is on 192.168.9.x.
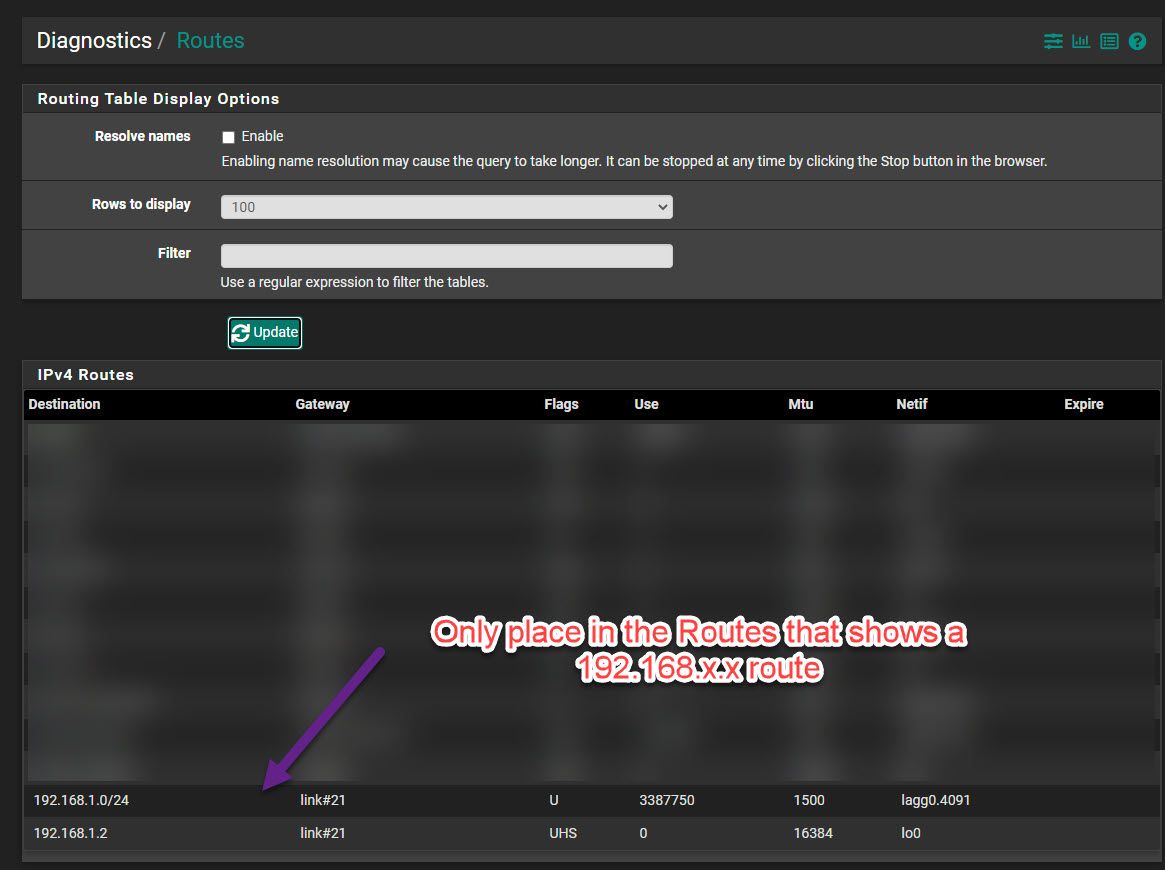
Then if I go to diagnostics > Routing, what I am trying to show here (the blurred part is other IP's i need to obscure but none are relevant to this discussion). Those two entries are te only two entries in Diagnostics > Routes under IPv4 Routes that have anything on the 192.168.x.x network. I don't see anything there for 192.168.9.x network as per the static route I created and is enabled?
-
@mynetworkrocks
Damn! You said, the USG does not respond to ping. So you cannont use it for gateway monitoring at all.
The gateway might get marked as down (check in Status > Gateways), hence pfSense ignores the route.So best to disable gateway monitoring here, since it is a local gateway anyway.
-
@viragomann said in DMZ configuring:
@mynetworkrocks
Damn! You said, the USG does not respond to ping. So you cannont use it for gateway monitoring at all.
The gateway might get marked as down (check in Status > Gateways), hence pfSense ignores the route.So best to disable gateway monitoring here, since it is a local gateway anyway.
Dam! that was it, the monitoring was disregarding the route ..... so I disabled the monitoring and disabled the monitoring actions and it worked straight away :)
The USG doesnt allow it to be "pinged" but the routing works now :) Thank you sir!




