Firewall blocking internal traffic
-
Hi,
Please see traffic being blocked even though I have added a rule to pass all traffic.
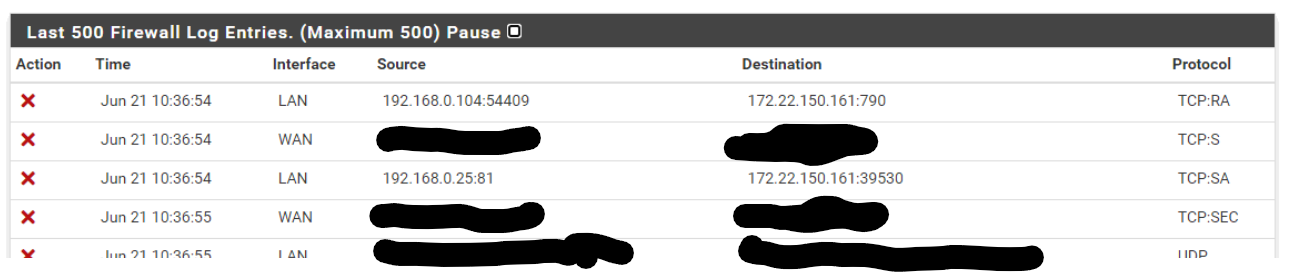
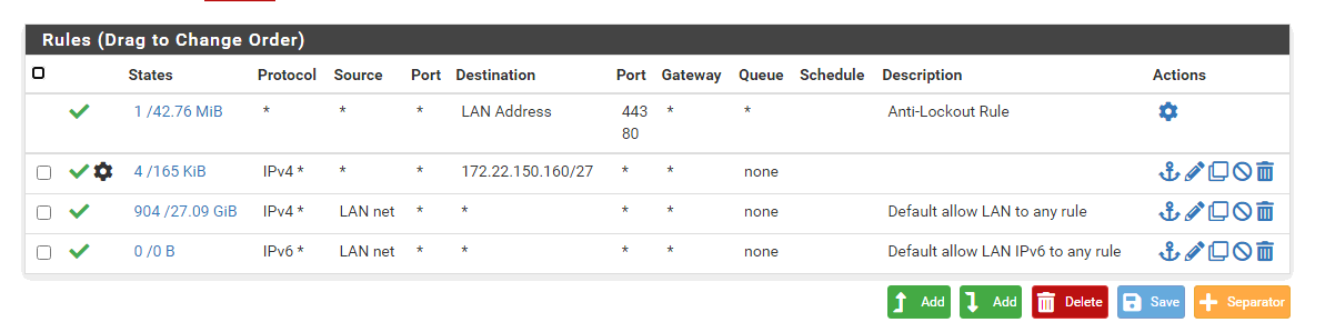
Does anyone know why its doing this? or if I've done something wrong?
Thanks
Dan -
@daniel_hyde
The blocked packets are out of state. The connection might either be already closed or you have an asymmetric routing issue.
Look here for details: https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html -
@viragomann Thanks for the reply.
I think the issue is related to the fact we are using High Availability Sync.Thanks
Dan -
@daniel_hyde Your second rule is unnecessary & redundant since the Default Allow rules right after it handle all outbound traffic for IPv4 and IPv6.
-
Yeah as already mentioned don't quite understand the point of the specific /27 destination rule unless your source would be something other than lan net? Do you have a downstream router on this lan? If so that is going to lead to most likely asymmetrical traffic flow, unless you have no hosts on "lan" and its just being used as a transit?
Only other reason for such a rule would be if you were wanting to log the traffic ? But I don't see the log icon on your rule. But you have done something else with the rule because you have the gear icon..
But yeah as already mentioned your block is because the traffic was out of state. the RA is common after states have been closed and something still sending RST for whatever reason. But your SA is normally a sign of asymmetrical for sure.. Because pfsense never saw the syn..
I guess a HA pair with traffic hitting the other device and states not in sync could be a reason for the block. But why would your traffic not being going to the device that holds the vip? In the middle of switch of the vip and states not sync could cause such blocks yeah..
-
Thanks everyone for the replies.
On this network they access some servers on 172.22.150.160/27 range.
They are accessible through a router that is 192.168.0.252
I have put a static route on the pfSense of 172.22.150.160/27 via 192.168.0.252
Just to add .252 is the HSRP address for actual routers on .17 (primary) and .18 (secondary)
In this configuration if the access to the servers is very slow and times out frequently.
If put a static route on the PC the issues disappear immediately.
Ideally I'd not like to do this on every PC.Thanks
Dan -
@daniel_hyde said in Firewall blocking internal traffic:
If put a static route on the PC the issues disappear immediately.
Ideally I'd not like to do this on every PC.Because your asymmetrical. If you going to have a downstream router, then you need a transit network.. Or you have to downstream nat, or you have yeah route on every host in the transit network (the network that connects routers).
Seem I go over this like every other day or so around here ;) hehehe
Any network that connects routers is a transit. There should be no hosts on this network.. If there are then yes your going to run into asymmetrical traffic flow when devices on downstream network and devices on the transit network talk to each other..
The correct solution if you want/need a downstream router setup a transit network to connect them (no hosts on this network).
edit: here is drawing showing how you would do a downstream router, 172.26.1.0/29 is the transit in this drawing.
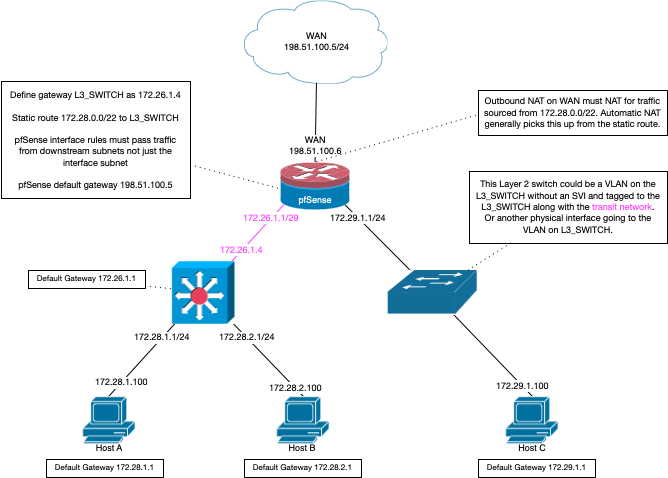
downstream in this context is any other router connected to your "transit" network that is not the default gateway of devices on the "transit" network.
-
@johnpoz Thanks for the reply.
I'll look into this, would I need to do the same to allow devices on the 172.22.150.160/27 range access the internet through the pfSense?
Thanks
Dan -
You would put the same sort of rule you have now allowing that /27 network, it would just be on your transit interface.
Yes you would need rules to allow any downstream network that you want to use the internet on your transit interface rules. Once you create a gateway, and routes in pfsense for what is connected downstream it would auto create outbound nats to nat the downstream network. Unless you have turned off auto nat, then yes you would need to make sure outbound nat is correct. But assume you already have that working if your internet is working fine currently for your downstream networks.
-
@johnpoz Thanks again for the reply, we do have support for the devices but the reseller hasn't registered them yet.
That is another issue we are having that the devices on the 172.22.150.160/27 network can't get to the internet.
Thanks
Dan -
@daniel_hyde said in Firewall blocking internal traffic:
172.22.150.160/27 network can't get to the internet.
Well if they are currently flowing over your "transit" - where you put that rule for the /27, and your not natting at this downstream device. You would have to make sure you have outbound nats for whatever downstream networks are flowing through pfsense to get to the internet.. Pfsense will only create auto outbound nats for networks directly attached to it. Or networks created via a route using some downstream gateway, etc
Validate your outbound nats list whatever downstream networks your using, and that your rules where these downstream networks come into pfsense are allowed.
Your lan rules are wrong for a downstream network, that is destination.. But this downstream network would be the source.. So your current lan rules wouldn't allow some source IP other than your lan net to get out to the internet etc.. no matter what your outbound nat rules are.
-
@johnpoz Thanks, that is where I'd gone wrong. I must have not saved the outbound NAT rules properly.
Thanks
Dan -
Your rules you shown would not allow that network as source for outbound to the internet either.
Unless you were natting - if that was the case then that rule is pointless, and outbound nat would of been fine with auto as well, etc. When you say saved, I take it you went manual mode with your outbound nats.
You really should set this up correctly if your going to run a downstream router. No devices on the transit network, etc.. And proper rules on the transit interface to allow for what you want.
-
As its setup in High Availability Sync the guide said to use manual outbound NAT
Thanks
Dan