Snort-4.1.4 Update Package Release Notes
-
Snort-4.1.4
The Snort package has been updated to the latest version of the upstream 2.9.18 binary. A new rules package option has also been added, and two reported bugs fixed in the GUI code. Look for this Snort update on the pfSense-2.6 DEVEL branch and the upcoming 2.5.2 RELEASE branch.New Features:
- The FEODO Tracker Botnet C2 IP Tracker rules package from abuse.ch has been added as a selectable option on the GLOBAL SETTINGS tab. When enabled, Snort will check and download the FEODO Tracker Botnet C2 IP Tracker rules during the periodic rules updates. Additional details on using this new feature are available farther down below.
Bug Fixes:
- Fix issue with losing previously entered alias values when adding a new HTTP_INSPECT server engine on the PREPROCESSORS tab. Redmine Issue #11637.
- Make rules update process smarter about restarting running Snort interfaces at the end of the update cycle. See Redmine Issue #6235.
How to use the new FEODO Tracker Botnet C2 IP Tracker rules
Enable the download of the new rules package by opening the GLOBAL SETTINGS tab and clicking the checkbox to enable the rules download as shown in the screen capture below.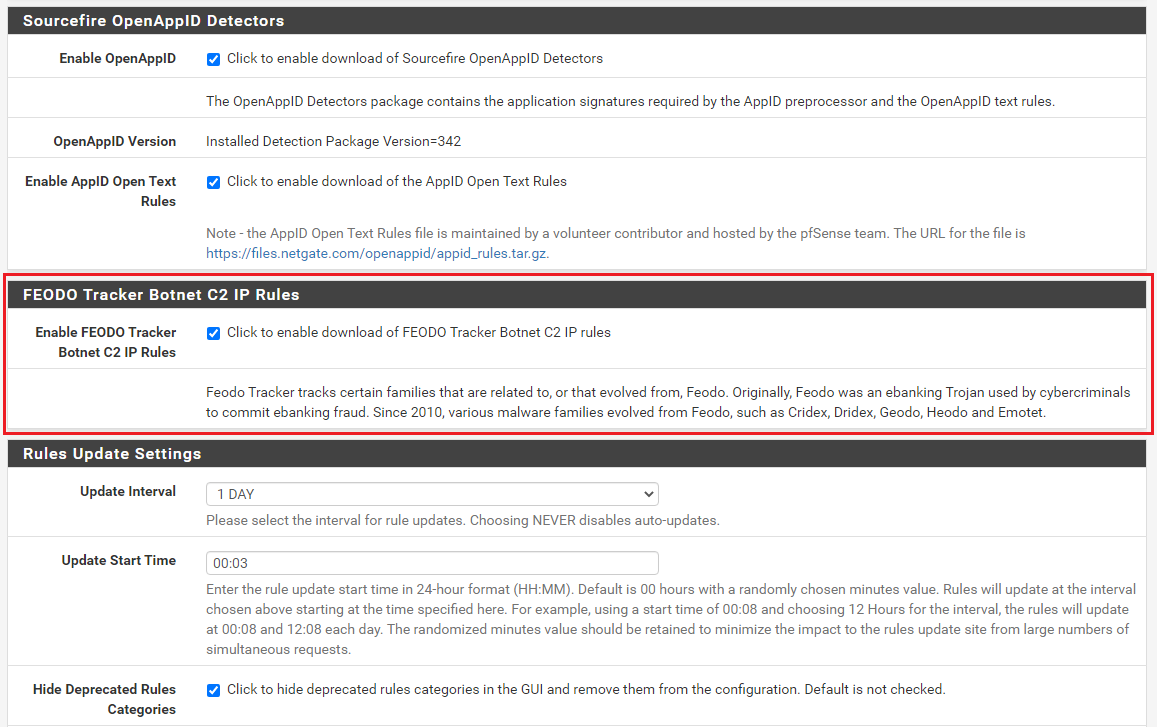
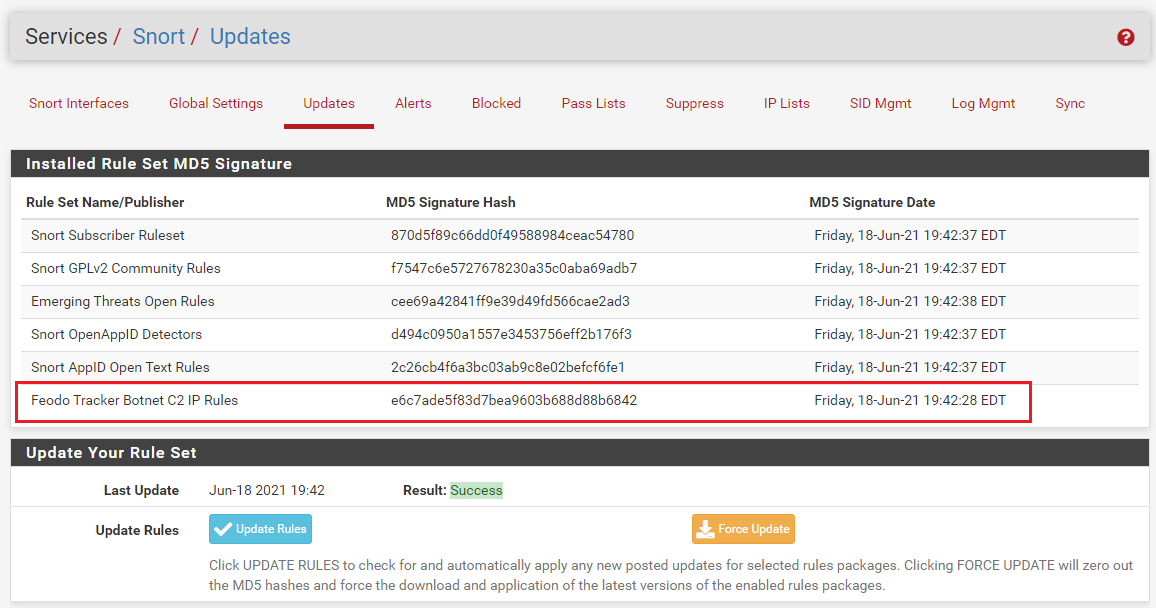
Next, go to the UPDATES tab and click the Update Rules button to trigger a rules update. After the update completes (the modal dialog will auto-close), you should see an MD5 signature hash and an MD5 signature date showing for the new rules package.
Finally, you need to click the CATEGORIES tab while editing the INTERFACE where you want to use the new rules. On that tab, click the checkbox to enable use of the FEODO Tracker rules as shown below.
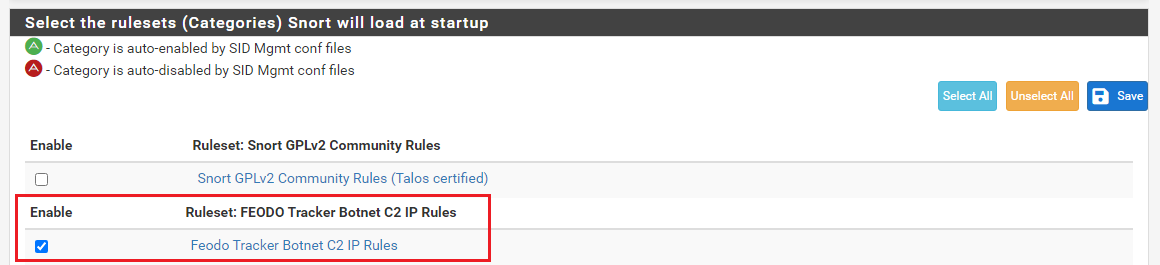
Save the change and then restart Snort on the interface. You can now manage these rules exactly as with the other rules packages (Snort Subscriber and Emerging Threats).
-
I'm looking forward to trying this out... a couple of questions, however.
-
Is there a chart somewhere showing how the new fork versions compare to the mainline release? I'm running 21.05-RELEASE and don't know what it means for my branch as to when the new Snort package will be available to me. I see this list here but I don't get any sense of feature parity unless I spend some time digging into the release notes for both branches.
-
Do you anticipate there being any work on getting more Netgate hardware interfaces to support inline blocking mode? I have an SG-1100 and would like to use inline instead of legacy but my adapters aren't on the list.
kind regards,
Gary -
-
@garyd said in Snort-4.1.4 Update Package Release Notes:
I'm looking forward to trying this out... a couple of questions, however.
-
Is there a chart somewhere showing how the new fork versions compare to the mainline release? I'm running 21.05-RELEASE and don't know what it means for my branch as to when the new Snort package will be available to me. I see this list here but I don't get any sense of feature parity unless I spend some time digging into the release notes for both branches.
-
Do you anticipate there being any work on getting more Netgate hardware interfaces to support inline blocking mode? I have an SG-1100 and would like to use inline instead of legacy but my adapters aren't on the list.
kind regards,
GaryI'm not sure I fully understand your question. There is no difference in package features in a given version of the Snort or Suricata package across platforms. So Snort-4.1.4 will be exactly the same on both pfSense+ and pfSense CE releases. The only difference is the timeline of when the package appears in a branch. If
you are asking for a chart showing which package version is "current" with a given pfSense version, then I don't know that one exists.Generally, new package updates are put in the DEVEL tree first to "cook" for a while to see if any major bugs show up. If not, the version is then ported over to the current RELEASE branches for both pfSense+ and pfSense CE.
So pfSense-2.6 DEVEL has the new package version now, and it should show up soon in the RELEASE versions. Packages are NEVER updated in deprecated versions of pfSense. So you will never see the 4.1.4 version of Snort show up for pfSense-2.4.5 or pfSense-2.5.0, for example.
-
-
@garyd If you're asking what version of Snort is included with pfSense, it isn't included, all packages are add-ons. If you left Snort and other packages installed when upgrading I think the process will upgrade packages to the latest version, but I've generally followed Netgate's advice to uninstall+reinstall (which of course will also install the current package version).
In System/Package Manager, if you click the version number it links to https://github.com/pfsense/FreeBSD-ports/commits/devel/security/pfSense-pkg-snort which gives a summary of all commits. Otherwise BMeeks is good about posting messages such as this one.
I don't see this new Snort for 21.05 yet either.
re: inline, I expect the answer is that it's up to the FreeBSD driver programmers, so who knows.
-
Look for this Snort update on the pfSense-2.6 DEVEL branch and the upcoming 2.5.2 RELEASE branch.I am familiar with the concept of dev/test/prod life cycles. I was merely asking what 2.5.2 would equal in the 21.X releases for Netgate hardware. I’m not the one that chose this ridiculous numbering scheme so perhaps someone that has could shed some light on the subject…? I’m not saying that’s you — I’m asking if you know who can.
Also, you got caught up in the excitement of mansplaining software development and completely ignored my second question about inline blocking mode. :-)
-
@garyd said in Snort-4.1.4 Update Package Release Notes:
asking what 2.5.2 would equal in the 21.X releases
Oh, I think we both assumed you were asking about Snort. 2.5.2 is comparable to 21.05.
-
@garyd said in Snort-4.1.4 Update Package Release Notes:
Look for this Snort update on the pfSense-2.6 DEVEL branch and the upcoming 2.5.2 RELEASE branch.I am familiar with the concept of dev/test/prod life cycles. I was merely asking what 2.5.2 would equal in the 21.X releases for Netgate hardware. I’m not the one that chose this ridiculous numbering scheme so perhaps someone that has could shed some light on the subject…? I’m not saying that’s you — I’m asking if you know who can.
Also, you got caught up in the excitement of mansplaining software development and completely ignored my second question about online blocking mode. :-)
Sorry about missing the second question. I am multitasking today working on a netmap problem in the Suricata 6.0.2 binary, and switch over to this forum for a second when I get a "ding".
The answer to your second question is "I don't know at this moment". FreeBSD-12 and higher switched over to a new scheme for NIC driver development. It's called iflib, and is a wrapper API for NIC vendors to use when writing a driver for FreeBSD. One positive thing about iflib is that it encompasses the use of netmap natively within the API. This theoretically leaves the NIC driver developer free to not worry about netmap. I think in actual practice, thus far, there are still some wrinkles (as in bugs) being worked out in the iflib code.
All that said, I do have an SG-1100 I can test with in the near future to see if Snort will actually run on it using Inline IPS Mode. Performance may not be optimum, though. If it does work now under FreeBSD-12.2/STABLE (which all of pfSense versions since 2.5.0 [and 21.02] are using), I can adapt the GUI code to allow that NIC as a choice.
As for version numbers in the main OS, anything starting with a year and a period such as "21." represents the new pfSense+ operating system that is currently only available for factory appliances. Sometime later this year pfSense+ will be available for third-party hardware with some conditions. The Netgate team is a better source for that info. Versions like 2.5.x or 2.6.x refer to the CE, or Community Edition. This is the free, open-source version. There is no necessary correlation between the 2.x CE editions and the 21.x (or future 22.x) pfSense+ versions. For now, there is very little difference in them. However, more divergence is expected by the community as time goes on.
At the moment, packages are compatible with either pfSense-2.5.x or 2.6.x CE versions, and the 21.x pfSense+ versions. So Snort-4.1.4 will work fine on either 2.5.2, 2.6.0 or 21.05 when it is posted into the respective packages tree. At some point in the more distant future, should critical parts of the underlying pfSense software diverge significantly between CE and pfSense+, then packages may become incompatible between the pfSense versions.
-
That's an interesting development re iflib. Let me know if you need any beta testers if it ends up in a future dev release.
-
Any assistance is appreciated.
Does Snort 4.1.3, in pFSense CE, support multithreading? -
@thesurge said in Snort-4.1.4 Update Package Release Notes:
Any assistance is appreciated.
Does Snort 4.1.3, in pFSense CE, support multithreading?No, the Snort binary used in pfSense is from the Snort 2.9.x branch. This is the old, legacy single-threaded code. The current binary in the package is 2.9.18.
-
@bmeeks I was always a little confused by the numbering scheme in pfSense -- it took me a moment to realize that it uses a release number for the package that does not necessarily reflect the version of Snort contained therein.
For the original question re multi-threading, there's a thorough comparison of the 2.x and 3.x branches over at snort.org.
-
@garyd said in Snort-4.1.4 Update Package Release Notes:
@bmeeks I was always a little confused by the numbering scheme in pfSense -- it took me a moment to realize that it uses a release number for the package that does not necessarily reflect the version of Snort contained therein.
For the original question re multi-threading, there's a thorough comparison of the 2.x and 3.x branches over at snort.org.
Snort on pfSense consists of two parts. There is, of course, an underlying binary component that runs as a daemon and does the actual traffic inspection. That is snort-2.9.18 as of today. The other component part is a PHP GUI piece that exposes the parameters used to build the
snort.conffile used by the binary to configure itself on each interface wheresnortis enabled. There were many more changes in the GUI's PHP code over the years than there were changes to the binary, thus the numbering scheme diverged. That means you can't equate the pfSense package version to the underlying binary version.If there is ever a Snort3 package created for pfSense, it will have "Snort3" in the package name to denote the underlying binary is from the 3.x branch of Snort. For the moment, nothing is planned in that area. I tried creating a Snort3 package a couple of years ago, but gave up in frustration. There was just no good way to import the existing configs. This is more to do with how the PHP GUI code works. Sure there is a configuration migration tool bundled with the Snort3 binary, but it does not work to migrate a pfSense configuration.
-
@bmeeks said in Snort-4.1.4 Update Package Release Notes:
Look for this Snort update on the pfSense-2.6 DEVEL branch and the upcoming 2.5.2 RELEASE branch.
Hi Bill,
may I kindly ask - is the 4.1.4 for shure to come in the 2.5.2? Or maybe I am too impacient ...

Regards,
fireodo -
@fireodo said in Snort-4.1.4 Update Package Release Notes:
@bmeeks said in Snort-4.1.4 Update Package Release Notes:
Look for this Snort update on the pfSense-2.6 DEVEL branch and the upcoming 2.5.2 RELEASE branch.
Hi Bill,
may I kindly ask - is the 4.1.4 for shure to come in the 2.5.2? Or maybe I am too impacient ...

Regards,
fireodoYes, it will be included in the current release (both CE and pfSense+) in the near future. I'm sure the team has been busy with the recent 2.5.2 version going RELEASE, and have not pulled over some package updates. I will drop the Netgate team an email asking them to move Snort-4.1.4 over to 2.5.2.
-
@bmeeks said in Snort-4.1.4 Update Package Release Notes:
Yes, it will be included in the current release (both CE and pfSense+) in the near future. I'm sure the team has been busy with the recent 2.5.2 version going RELEASE, and have not pulled over some package updates.
Good to hear!
I will drop the Netgate team an email asking them to move Snort-4.1.4 over to 2.5.2.
Thank you very much! And also THANK YOU for your work!
Nice Weekend, i wish,
fireodo