Unifi Controller behind pfsense
-
Hi,
I'm new to pfsense, try to learn more about it.
But I'm a little stuck here.I have set up a pfsens that will be in front of all my servers, where among other things the unifi controller is. have tried to load all the ports that unifi uses against the server. But unable to get in touch with the unifi equipment, ran a test on an edgrouter. And got it right there without any problem. Anyone done anything like that before or can help me here?
port for unifi:
UDP
3478UDP
5514TCP
8080TCP
8443TCP
8880TCP
8843TCP
6789TCP
27117UDP
5656-5699UDP
10001UDP
1900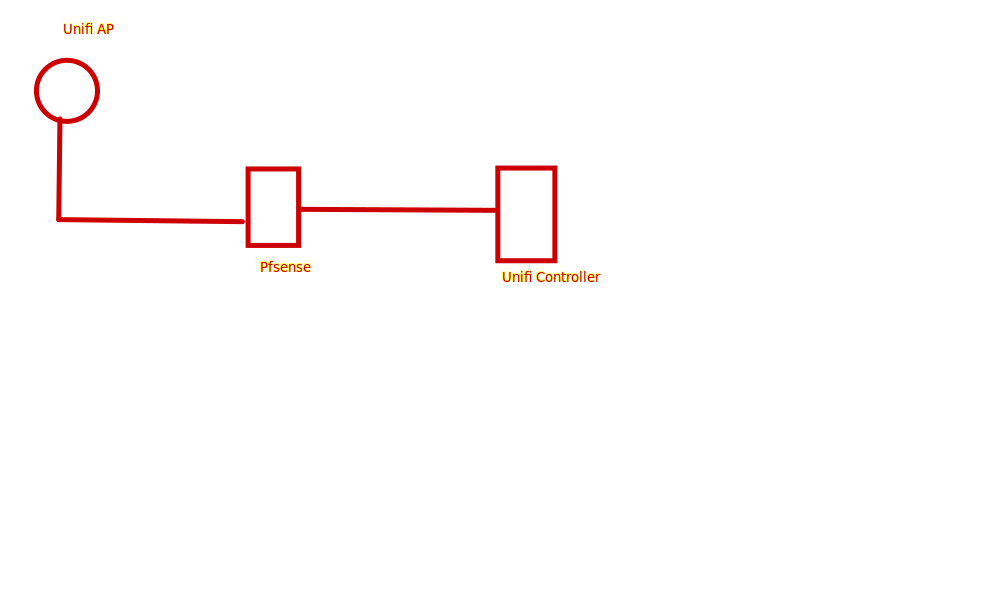
-
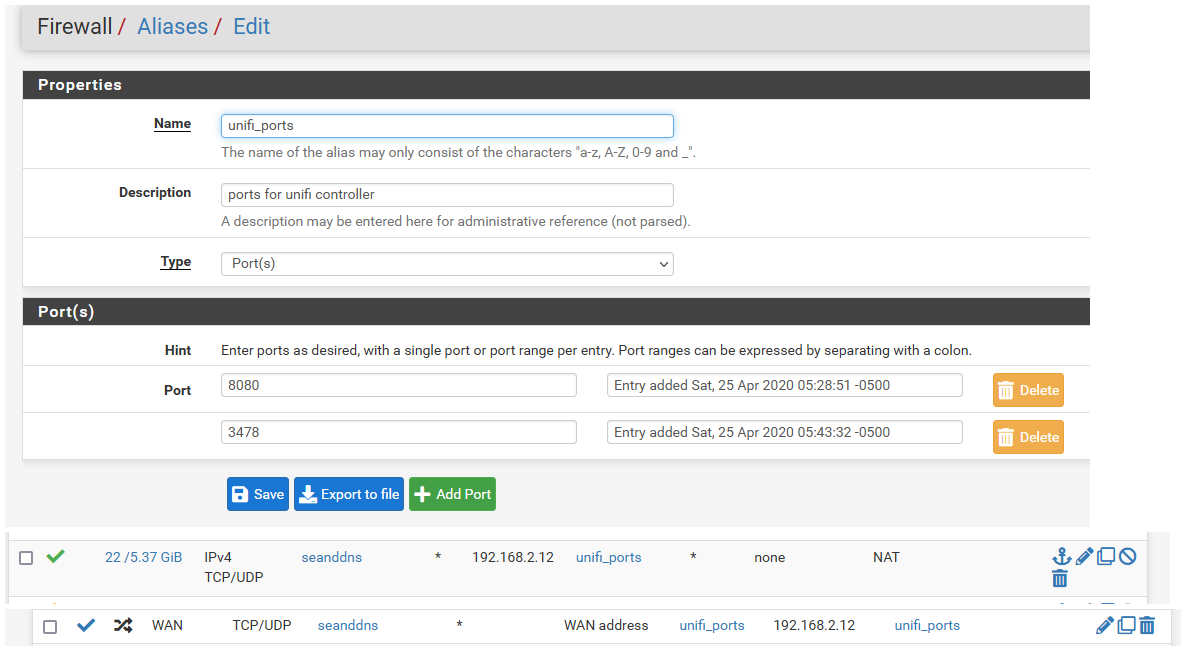
I manage my sons setup with my controller behind pfsense. These are the only 2 ports that are needed..
And the portforward and firewall rule.
If your controller is on a different L2 than your unifi devices - you do have to do L3 adoption for them to show up in the controller.
Why would you not just put the AP management network on the same L2 as your servers - behind pfsense. That is has nothing to do with the vlans your wireless network (ssid) would be on - this makes it much easier to manage. Or just put your unifi devices and controller on their own vlan, different than your servers vlan and other networks/vlans. Your controller likes to be on the same L2 to find devices and adopt them.. If not you need to look into the unifi L3 adoption docs.
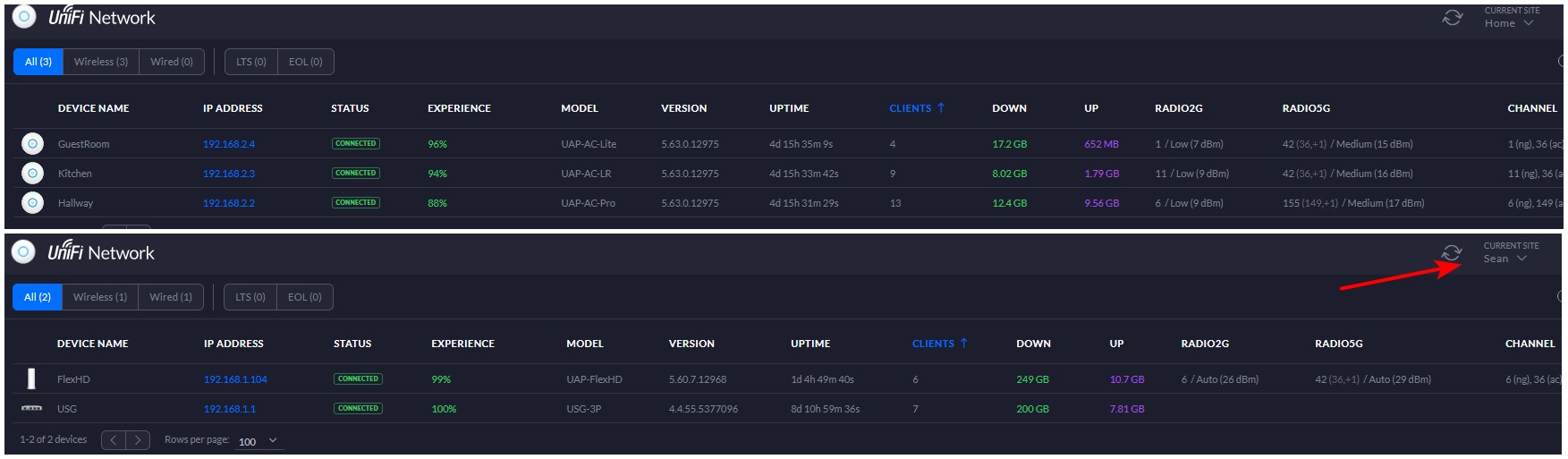
https://help.ui.com/hc/en-us/articles/204909754-UniFi-Layer-3-Adoption-for-Remote-UniFi-Network-ApplicationsI have those rules setup on mine because my sons unifi device his usg and is flexHD are it his house.. On his own internet connection..
So to be complete - here is my devices (home site) and then my son's site in same controller
-
because I'm on a network where we are 6 other households on a fiber link, each with its own vlan and firewall rules so we do not see each other or can talk between the networks. but want to get my server equipment separate from them, the reason why I want to put the unifi controller there is because it runs on a proxmox server.
is a bit because it becomes easier for me to test new things without it taking everything down -
None which has anything to do with what I said..
Put your controller and your AP on the same L2.. Zero to do with how many other vlans might in the building or make up some local network.. Nor does your controller running on a proxmox have anything to do with what vlan you put the controller on..
I would suggest the best learning/testing you could do would be just that.. Putting the AP and Controller on their same L2 network - so you don't have to worry about L3 adoption or firewall rules or port forwards that allow for that.
But if you insist on putting the AP and Unifi controller on different L2 networks, the follow the guide I linked to for L3 adoption, it also lists the firewall rules you would have to allow for. Which would be the 2 I showed, nothing more.
Also you don't show in your diagram.. This network that the AP is on, will your AP point back to pfsense IP on the network as its gateway? Or is there dhcp on that network pointing to something else as the gateway.
Your diagram as drawn, since you don't show internet anywhere - has me assume that the AP is on the wan of pfsense, and your servers are behind pfsense (since you want to isolate them).. This leads to the assumption that there is something else providing dhcp to those devices and pfsense wan.. If that pfsense wan network is rfc1918, and AP is on this wan network your going to have to turn off the block rfc1918 rule as well on the wan. And your L3 adoption IP/FQDN you use will have to point to the pfsense wan IP. If you do not control the dhcp server that provides IP to the network your AP will sit on - then the dhcp method of L3 adoption would be out, etc.
This assumes your pfsense is doing nat, and you will have to setup port forwards for the L3 adoption ports as well.. You listed out some ports, but zero details of interfaces or rules or port forwards you have created, etc.
-
sorry for a bad explanation
but thank you for everything you have explained so far. Is a little longer on the road now than before, not thinking about everything you have written down here. so have some to look through now
-
I thought the Unifi controller was on port 8443.
-
L3 adoption can be a PITA.. And if there is no actual reason for it - like my example where my sons unifi stuff is remote and on some other network across the internet. I would highly suggest use the same L2 for your controller and AP.
This management network for the controller and ap does not need to be the same as either wan of pfsense or your server network you want to create if you do not want it to be.
But L2 adoption is way easier to setup.. How hard is it to put a VM and AP on the same network ;) You can then put learning L3 adoption down for a different day. But if you are new to pfsense this not where I would suggest anyone start..
If this AP is just yours - and not shared for the rest of the building etc.. I can see no reason why you don't just connect it to the same network your servers behind pfsense. And even put off learning how to do vlans for another day after you have gotten your feet wetter with pfsense.
-
@jknott said in Unifi Controller behind pfsense:
I thought the Unifi controller was on port 8443.
Not for management of clients.. That is the gui port.. Completely different than the port used for AP talking to the controller - while you can change that from the 8080 if need be via the system.properties file.
Here the default ports.
https://help.ui.com/hc/en-us/articles/218506997You will notice
TCP 8080 Port used for device and application communication.The articles can be a bit misleading - pretty much like all of these sorts of any articles.. The only 2 ports needed for a device sitting on different L2 are the stun and the 8080 port. edit: Shoot you might even be able to get away without the stun port. But then it pops up lots of errors about no stun communication and make your controller dashboard and info about the devices look shitty with ! in triangles all over it ;) I have not played with running the remote site without stun, since it was just 1 more port to forward and I lock down the inbound traffic to only my son's IP anyway.. So doesn't really matter if 2 ports or 200 ports.. But why open up stuff that serves no use.. But the stun port is prob not needed for actual adoption and management - but since there will be errors all over your controller dashboard - makes it hard to tell if actually working ;) heheh
I can tell you for fact those are the only ports the AP needs to be able to talk to the controller on for adoption and managment. Now if you also want to access the gui and etc from the same network your AP is on different from the controller - you might want/need other ports as well to be forwarded/allowed. But for just management/adoption of devices via L3 methods is the 2 ports I listed.
-
nice for everything you can learn, thank you very much for the info, it's a bit easier and faster to play and learn now to make it happen.