no communication between VPN and Client LAN
-
@viragomann said in no communication between VPN and Client LAN:
What are your concerns on running multiple OpenVPN servers?
this whole setup will be much bigger in the future, i will explain what is planned in the future.
right now we have a Router at our local office that manages the local network as well as providing an openVPN server for all remote sites over the first internet connection. this is working fine.
Now my boss wants a second path for communication in case something happens to the first path like a power outage (we have emergency power but in case of a local power outage we would still have no internet).Now my boss read something about pfSense and was excited and bought a starlink dish and a super expensive server for the second VPN server.
The problem now is, that starlink cannot provide a static IP-adress and my boss don't want any dynDNS services. So we cannot run a Server at this location over Starlink because of the changing IP-adress.
But we have another server somewhere else with a static IP and pfSense installed so the idea is to set up the OpenVPN server there and tunnel from here to the server as well as from all other locations to that same server so we could establish a static connection this way over that server.
And it's my task to realize this

-
@knausepeter
Ok, but this long story doesn't bring any change to the conditions. You have multiple sites, one of them is the main location, the others I'll call branches. All branches should be able to access services in the main location, but don't need to talk to each other.Since the main location has a dynamic IP and hence cannot run the server, you want to set up a central VPN server, where the main and all branches should connect to via OpenVPN to enable the desired communication.
This is the server we're talking about.And now my question again is, why do you want run multiple VPN servers to realize this?
It doensn't matter if this is an expensive hardware or not at all. An OpenVPN server doesn't need much resources, so you can also run multiple instances on a small hardware, but easier to set up the routing between the connected clients.
Your option is to go with CSO as I mentioned in my first post here, but that doesn't seem to be familiar to your. -
@viragomann said in no communication between VPN and Client LAN:
Ok, but this long story doesn't bring any change to the conditions. You have multiple sites, one of them is the main location, the others I'll call branches. All branches should be able to access services in the main location, but don't need to talk to each other.
Since the main location has a dynamic IP and hence cannot run the server, you want to set up a central VPN server, where the main and all branches should connect to via OpenVPN to enable the desired communication.
This is the server we're talking about.
Exactly!
And now my question again is, why do you want run multiple VPN servers to realize this?
The new machine runs the pfSense among other things that should replace the "old" Router that is hosting the present VPN Server. In the future the pfSense machine should run 1 server, that connects to the main Internet and the client that connects to the remote server (what i'm trying to realise right now). Then the old router goes somewhere else.
As soon as my setup works, all the other locations will be moved to the pfsense.
to get back on topic, I think I'm close to a breakthrough, I just think I entered something wrong in the CSO, it can't be that much now.
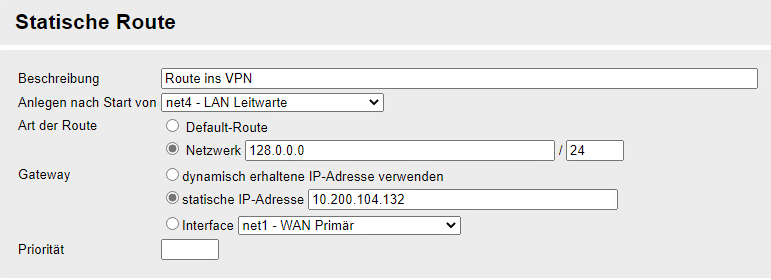
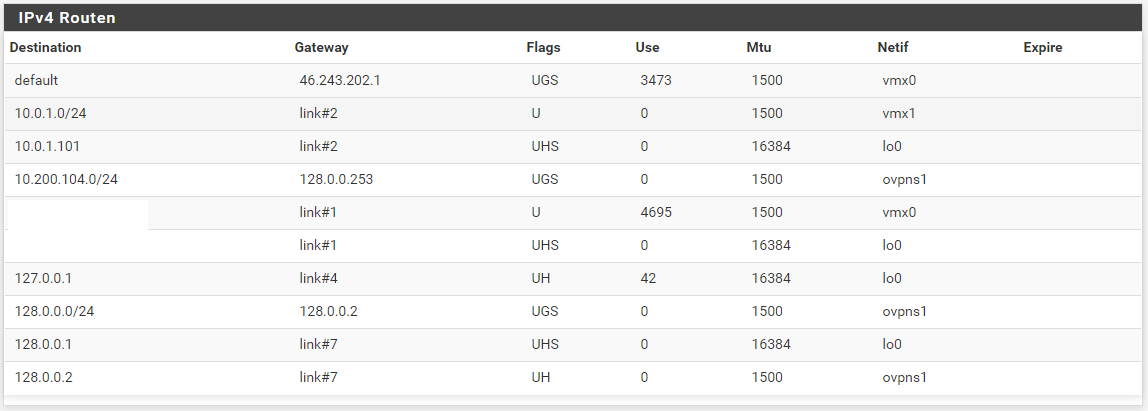
do i have to enter something at the clientside pfSense openVPN config?
-
@knausepeter
Okay, however why do you still not respond to my question which I asked three times already?And why put you as much time in a mediocre solution and ignoring all drawbacks?
-
@viragomann said in no communication between VPN and Client LAN:
Okay, however why do you still not respond to my question which I asked three times already?
why do you want run multiple VPN servers to realize this?
because we need a guaranteed connection and if the first internet connection fails the remote sites must fall back to the second VPN connection, this would be a lesser problem, if our second internet connection had a static ip, but since starlink hasn't a static ip, this was our solution. This whole mess what i'm trying to do here is just for the emergency case. But i think i also answered this already (no offense)
And why put you as much time in a mediocre solution and ignoring all drawbacks?
good question, i keep asking this myself for days... because i try to realise what my managing director wants... do you have a better idea? i need to utilize the new fancy hardware and starlink...
-
@knausepeter
In order not to be misunderstood, I'm talking about running two OpenVPN servers on a unique pfSense box. This one which has a static public IP.
For instance you run one OpenVPN server on port 1194 for the branches and a second one as site-to-site on port 1195 for the client in the main location.This way you can properly route the traffic from one VPN server to the other one as well as to the client in main location and you are able to control the traffic by filter rules.
-
In order not to be misunderstood, I'm talking about running two OpenVPN servers on a unique pfSense box. This one which has a static public IP.
For instance you run one OpenVPN server on port 1194 for the branches and a second one as site-to-site on port 1195 for the client in the main location.
Why didn't i think of this?! Didn't know, that this works that easy but it's a good point, thank you.