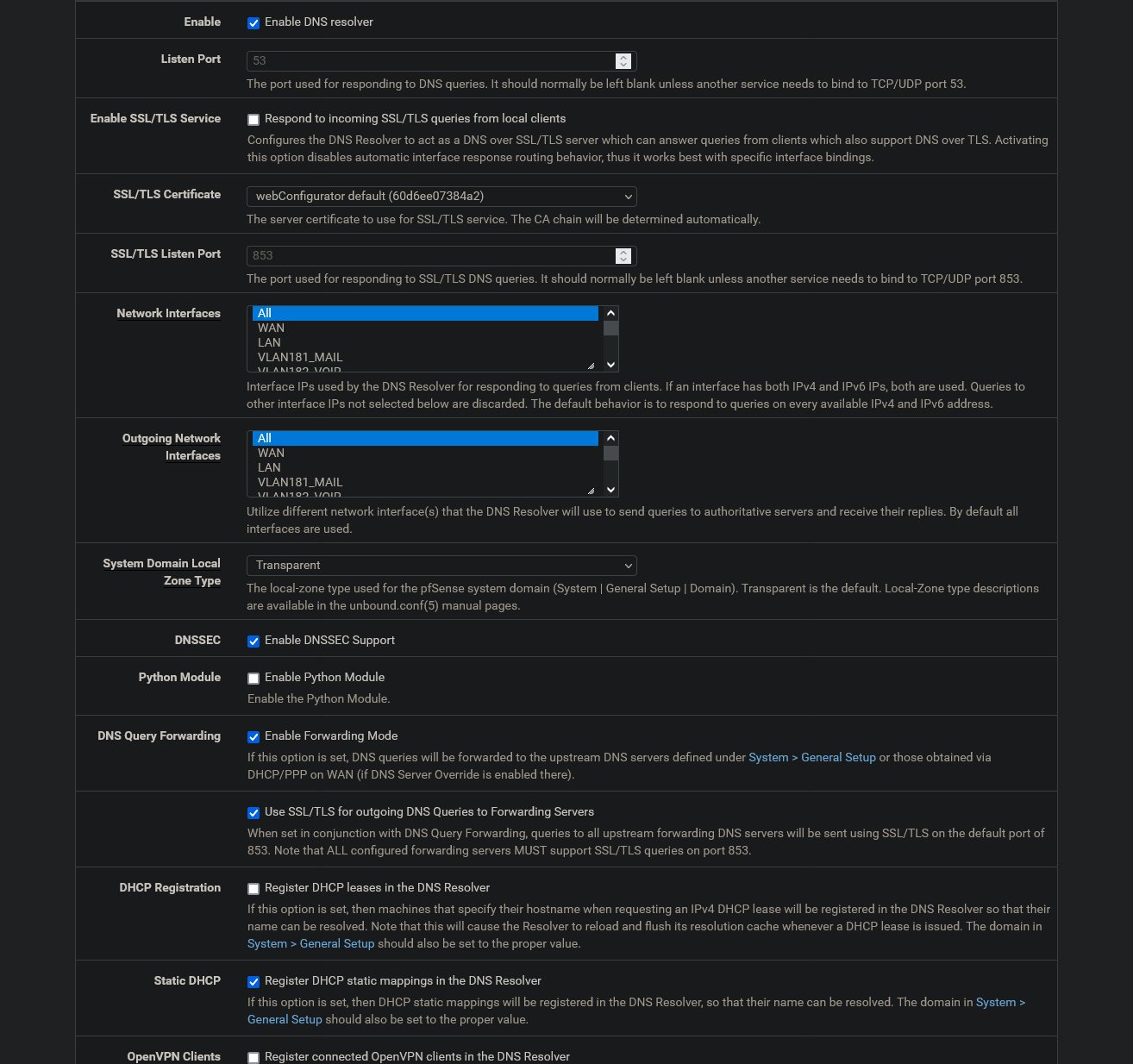
DNS over HTTPS/TLS Blocking & DNS Query Forwarding via SSL/TLS
-
Enabling DNS over HTTPS/TLS Blocking under DNSBL-SafeSearch will also cripple the DNS Lookup under Diagnostics. At least if you use DNS Query Forwarding together with Use SSL/TLS for outgoing DNS Queries to Forwarding Servers in the Resolver. Is this intended?
-
Back when I was forwarding instead of resolving, I didn't bother to block what I was using anyway, what's the point, I was forwarding to them. Once I determined I really didn't want to use any of these companies that were dangling 'free dns', encrypted or otherwise (they obviously wanted to gather market data they could sell) I realized I didn't want to be a part of it. Blocking them only makes sense if you don't then decide to use them anyway.
It sounds like PFSense is doing a resolve using what is on the general tab, which is being blocked, as opposed to forwarding. -
You are right. I would wish though the firewall itself would be excluded from this and still could use the resolver, but it seems to be no option.
-
It sounds like PFSense is doing a resolve using what is on the general tab, which is being blocked, as opposed to forwarding.
That sentence makes no sense to me. Either pfSense is resolving itself (via localhost and unbound as resolver), then it's using ROOT DNS servers. Or it is forwarding, then it is using those forwarders from the System/General page. There's no "resolving with those in general tab". Resolving is done via the Root DNS servers :)
-
@bob-dig said in (solved) DNS over HTTPS/TLS Blocking & DNS Query Forwarding via SSL/TLS:
You are right. I would wish though the firewall itself would be excluded from this and still could use the resolver, but it seems to be no option.
Also: can't reproduce the error myself. Just activated DNSBL, switched on all DoH/DoT blocking and ran a force update. Can't see that failing afterwards:
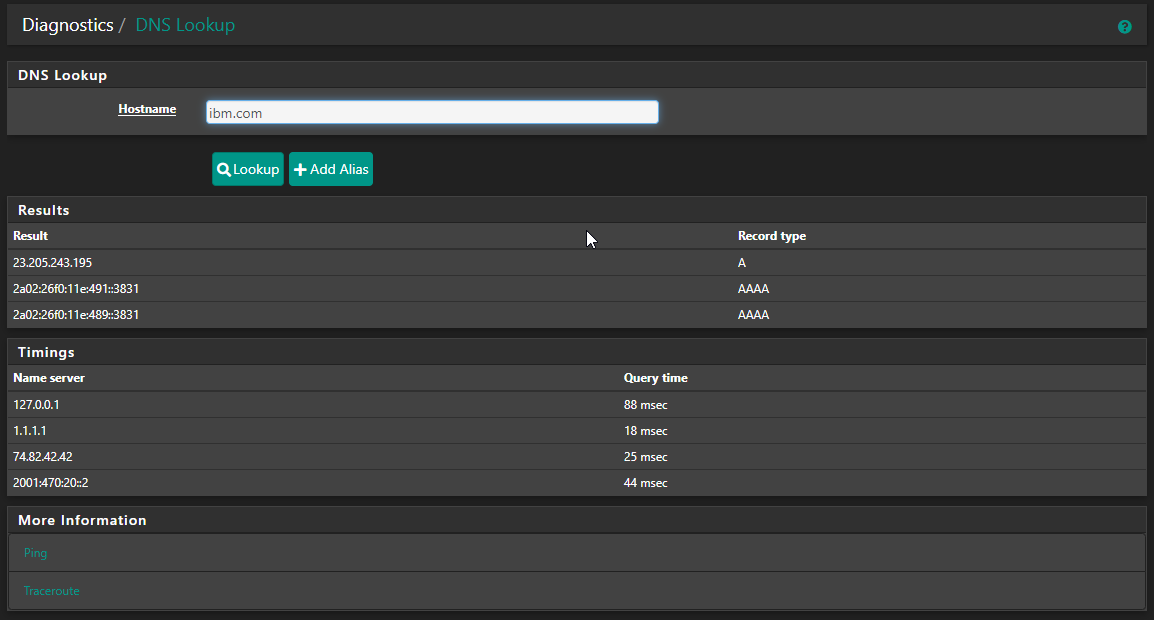
Used a domain that wasn't in the cache either. Resolver (locally) had no problem as did Cloudflare or he.net - all resolved the name without problems.
I also verified it is blocking DoH/DoT domains:
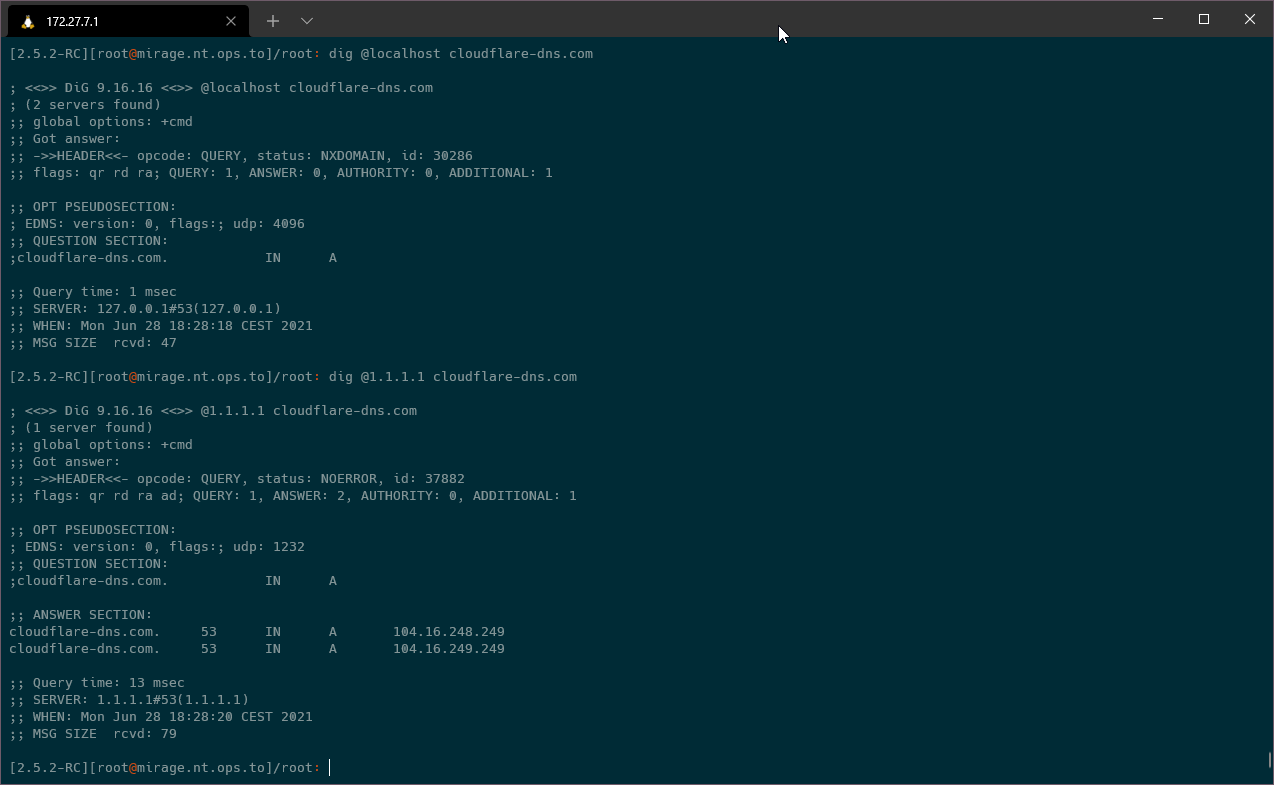
locally - NXdomain. Asking cloudflare directly: resolving. So everything running as it's supposed to. :)
-
@jegr said in (solved) DNS over HTTPS/TLS Blocking & DNS Query Forwarding via SSL/TLS:
So everything running as it's supposed to. :)
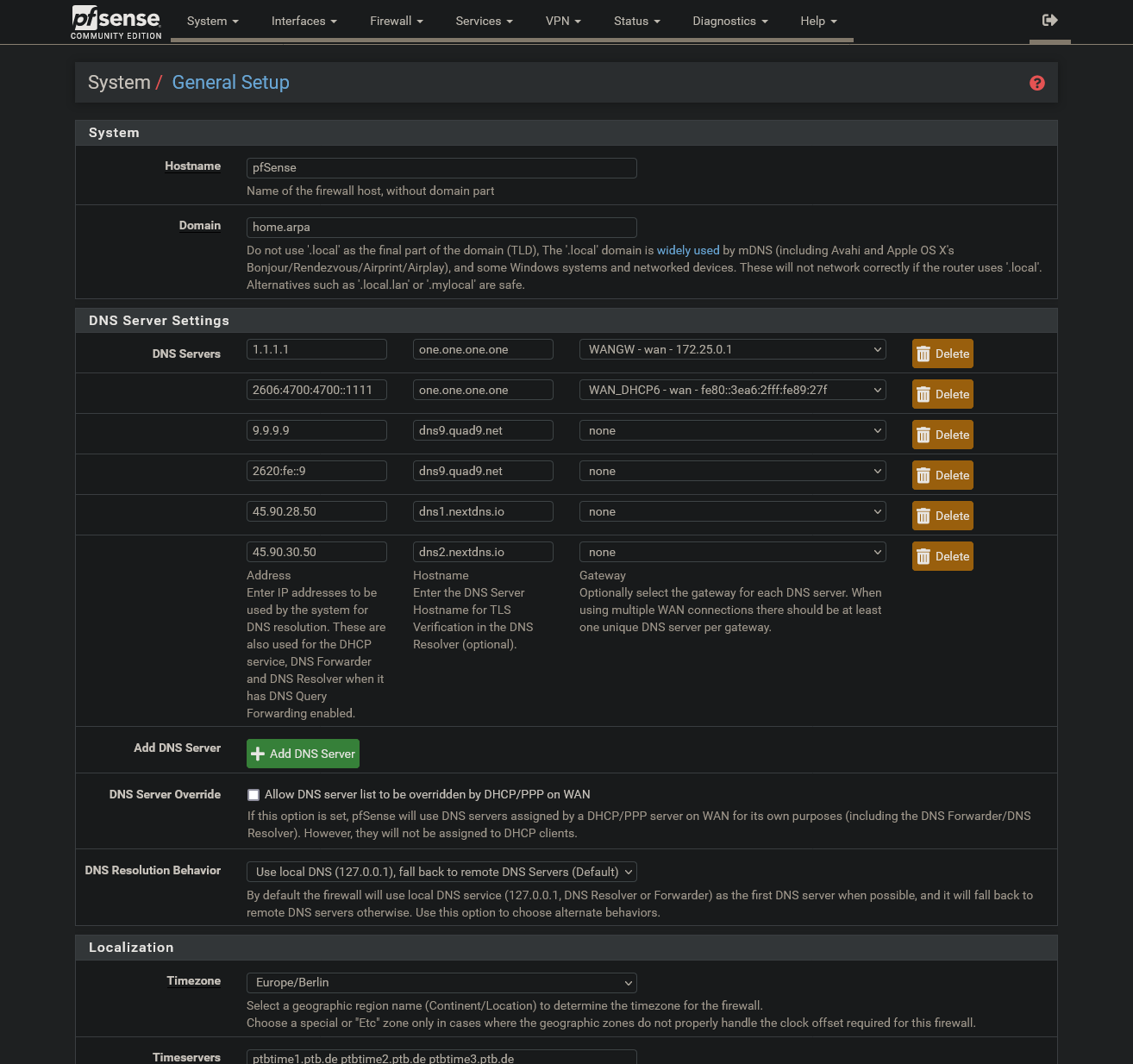
I use Enable Forwarding Mode and Use SSL/TLS for outgoing DNS Queries to Forwarding Servers.
1.1.1.1 is the DNS-Server in General Setup and I have disabled DNS Server Override there.
In the end the following dns lookups failed:
one.one.one.one
dns9.quad9.netWhat I wanted to do was putting in some other DNS-Servers in General Setup and for filling in the hostname field there I did the (failing) dns-lookups (or it was to find the corresponding IPv6 addresses).
Later I noticed that is was related to DNS over HTTPS/TLS Blocking in pfBlocker, although the resolver worked for me without a problem otherwise. -
@bob-dig said in DNS over HTTPS/TLS Blocking & DNS Query Forwarding via SSL/TLS:
I use Enable Forwarding Mode and Use SSL/TLS for outgoing DNS Queries to Forwarding Servers.
OK but then you're using the forwarder, not resolver. That's important. :)
Nevertheless for normal lookups that doesn't seem important as I switched to forwarding and it seemed to work. -
@jegr said in DNS over HTTPS/TLS Blocking & DNS Query Forwarding via SSL/TLS:
OK but then you're using the forwarder, not resolver.
I am using unbound. :)
Not watching the game or r u multitasking?

-
@bob-dig said in DNS over HTTPS/TLS Blocking & DNS Query Forwarding via SSL/TLS:
@jegr said in DNS over HTTPS/TLS Blocking & DNS Query Forwarding via SSL/TLS:
OK but then you're using the forwarder, not resolver.
I am using unbound. :)
Not watching the game or r u multitasking?

No, you don't understand what I'm talking about. Yes you may be using unbound, but you are NOT using the resolver, but the forwarding engine. That is a totally different procedure as I was already pointing out in my previous posting.
Besides that I couldn't reproduce pfBlocker somehow blocking IPs to DNS forwarders. Already wrote that above, too - perhaps you are multitasking? ;)
So either it's another setting interfering or some configuration of yours in pfBlocker but mine isn't misbehaving that way? :)
-
I can reproduce it by enabling this blocking in pfBlockerNG again, reloading or updating it and then rebooting pfSense: The problem (1. pic) occurred again.
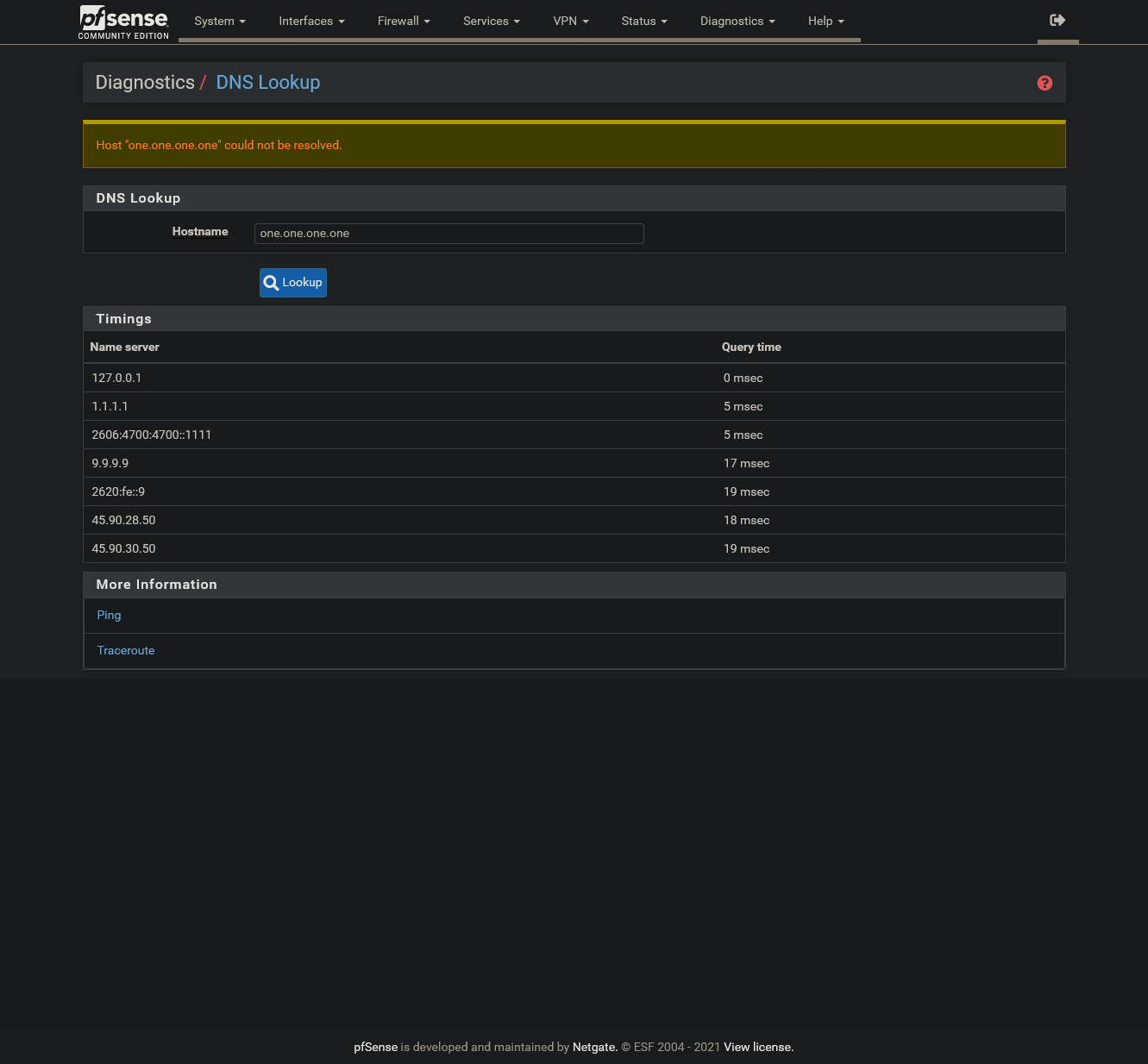
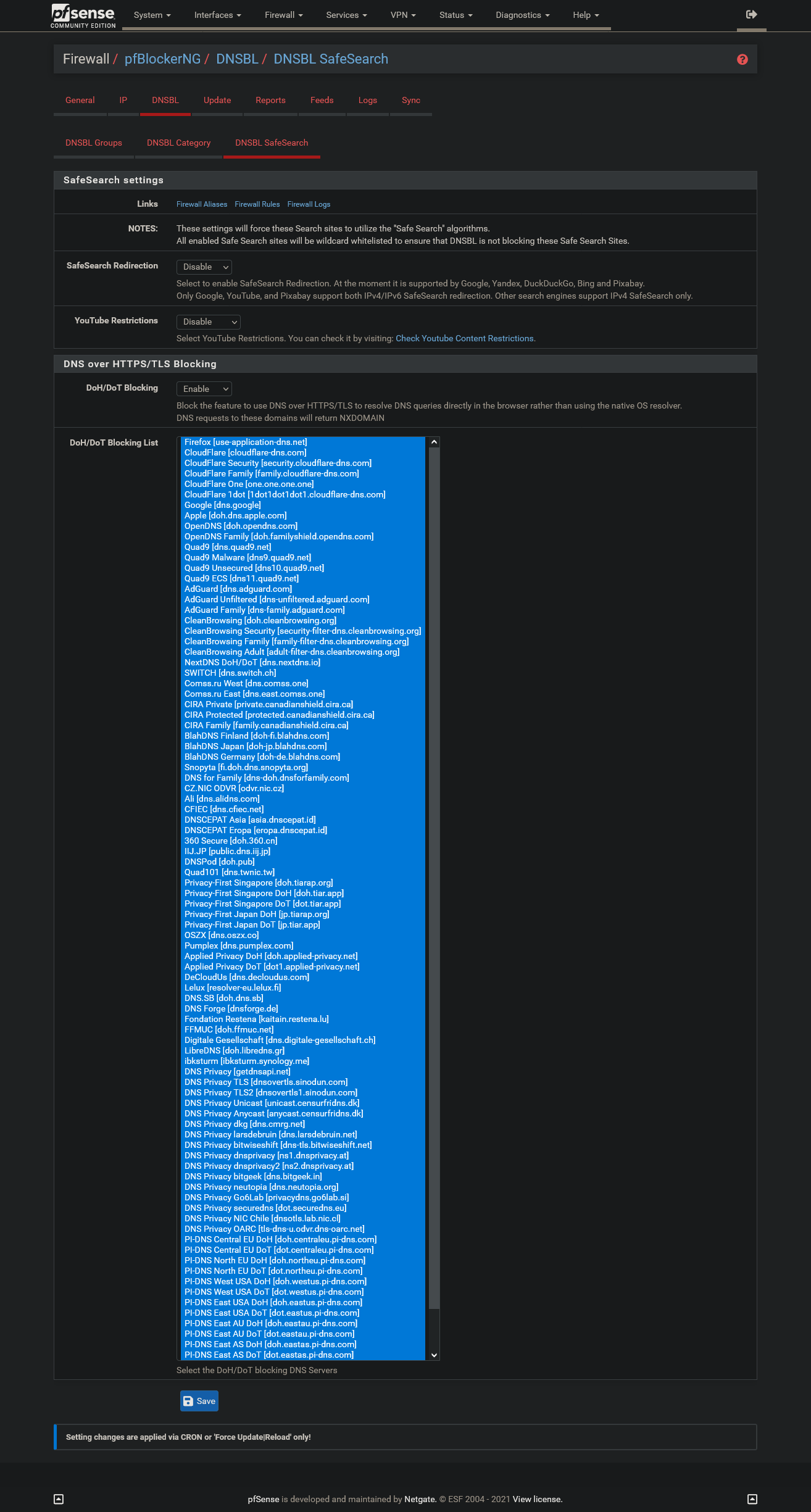
Same for: dns9.quad9.net
-
@bob-dig Where exactly is the sense in "blocking DoH/DoT" - then using exactly that in your unbound config? Don't understand that line of thought. Especially blocking my own forwarders in DoT section of pfBlockerNG and wondering why it wouldn't work ;)
Kinda biting your own tail :D
-
@jegr Yep, I thought whatever I do there in pfBlocker wouldn't affect my unbound config, but that is not the case. So it works as intended it seems. That was the question in my first post.