Simple IOT Network
-
Id like to make a simple IOT network and Guest network. I currently have a pfsense router with a quad NIC and a Ubiquiti AC Lite AP. I was thinking of getting another AC Lite AP and attaching it to a separate port on the NIC and creating a total separate network on that port with internet access.
This way guests and any IOT device I have would have there own WIFI to attached to.
My question is whether that separate port would be segregated from my other networks without any firewall rules. I'm trying to keep this simple.
Yes, I do have a VLAN aware switch but the additional AP seems very straight forward but does it provide good security? I want the IOT devices to call home as I want to use their services.
I also considered Steve Gibson's suggestion ( https://www.grc.com/nat/nat.htm) to put another router between pfsense and the AP/network. This just costs more as you need more routers.
boil it down.... does the AP attached to the seperate NIC interface protect the other interfaces from its traffic ie IOT/guest?
thanks,
Jay
-
@jay226 Separate interface or VLAN, it's the same thing. Security & access are controlled by firewall rules. Only LAN gets an Allow All rule. All other local interfaces have no rules until you add at least one. Rules are applied to traffic as it enters an interface so to control access for IoT and Guest networks, you add rules to the those interfaces respectively.
-
OK. So its not a one stop shop. I have to add firewall rules to that interface to allow outbound traffic to the internet and such.
does this method of the separate interface provide additional security to the other interfaces?
I suppose i could get them to talk if I created the correct forwarding rule?
Otherwise the are naturally separated?
I hope my question makes sense.
your thoughts on vlan? just was easy? That AP I have will do vlan tagging.
-
does this method of the separate interface provide additional security to the other interfaces?
Yes. That's what a firewall does. It manages traffic between networks.
I suppose i could get them to talk if I created the correct forwarding rule?
Not a forwarding rule, but yes you control access by adding rules to allow specific traffic to flow to specific destinations. A forwarding rule is a rule on WAN to allow inbound traffic that you want to forward to a local server.
Otherwise the are naturally separated?
Yes.
your thoughts on vlan? just was easy? That AP I have will do vlan tagging.
I personally would only use VLANs if I don't have physical interfaces available or if it's a complex setup.
-
@kom Thanks for you help. I'm still playing with this and wondering if the below statement is true.
-Firewall rules on the interface only control outbound traffic to other networks?
I say this because the below example does not block traffic to the LAN interface from the Printer VLAN.
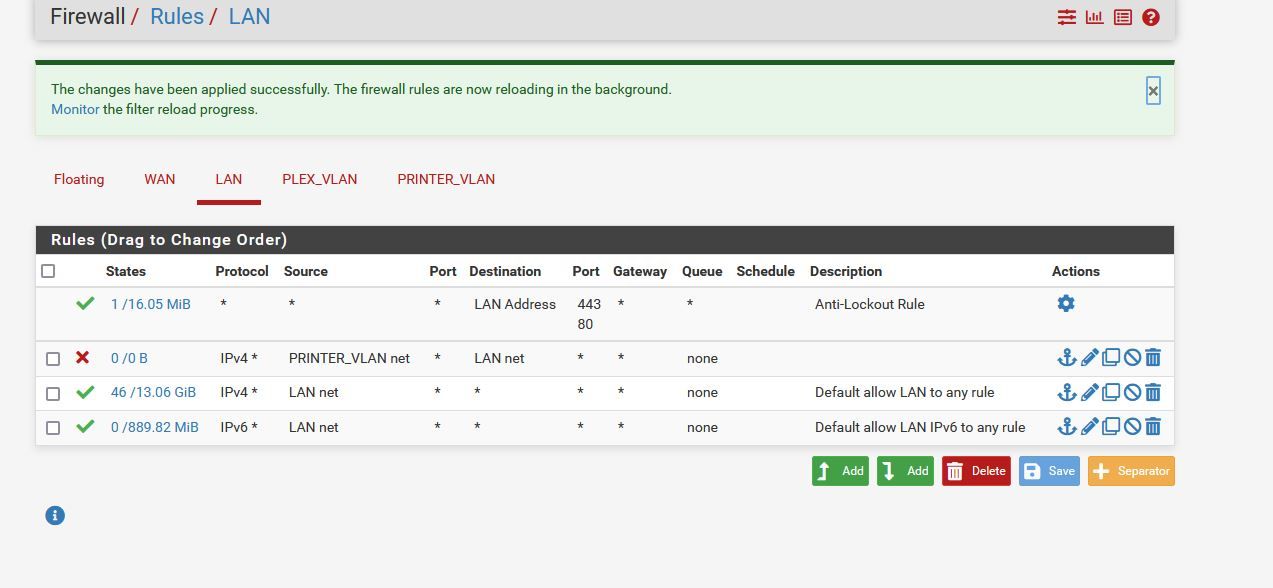
However, this does work
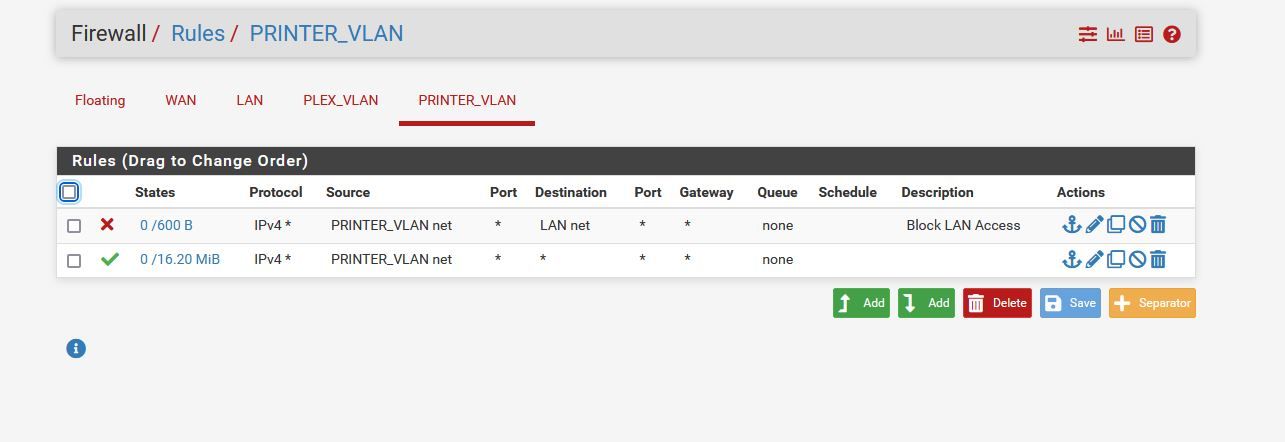
My conclusion is that I cant control with firewall rules traffic inbound to the LAN interface with rules on that interface. Even though it gives me the option to select other interfaces as the SOURCE network.
Hopefully that makes senses.
-
@jay226 said in Simple IOT Network:
wondering if the below statement is true.
-Firewall rules on the interface only control outbound traffic to other networks?No. The rule has to be set on that interface, where the traffic is coming into pfSense.
So the LAN rule with source PRINTER_VLAN net makes no sense at all.
That one on the PRINTER_VLAN is fine.However, to give devices only internet access I use to block anything but public address spaces. To do so I set up an alias of type networks and add all RFC 1918 networks to it. Then I use this in the rule as destination to allow or block traffic.
However, you will have to add additional rule to allow DNS access to pfSense, when needed.Consider that your PRINTER_VLAN rules allow any destination except LAN network, so it permits also access to pfSense web configurator.
-
All you need is VLANs and multiple SSIDs. Why would you want double NAT when single NAT is already one to many?
Here's my guest Wifi rules:
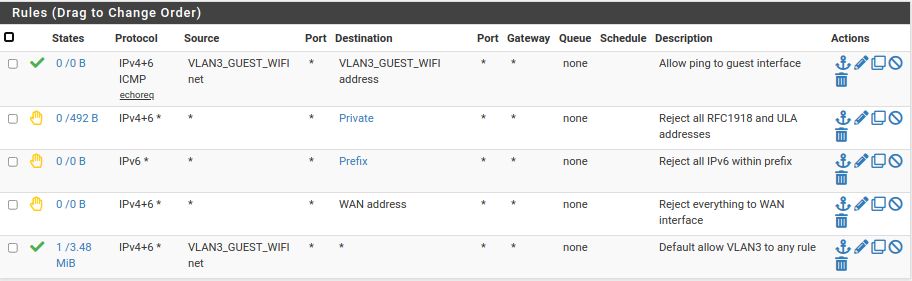
These rules allow guests access only to the Internet and to ping the interface. Nothing else.
-
@jknott sorry, i kind of added to a thread that had a different objective.
The other VLANs were to separate different resources from clients that didn't need them. I want to put all my IOT (Nivida Shield, Roku, TV etc) devices in vlan and only give them access to things they need. Like my TVs need Plex but they done need a printer.
I was hung up on how pfsense is processing packets on the interfaces but I think I'm clear now.
All I have not are VLANS and firewall rules. Not sure that is a doube NAT?
-
@viragomann Thanks for the input. I did not consider your last comment about webconfig access. Though I dont think i restricted it when everything was on the LAN.
So I should put a rule to drop traffic that goes to 192.168.1.1 or 192.168.20.1 for example on each interface? This will block access to the webconfig from that network?
-
@jay226 said in Simple IOT Network:
All I have not are VLANS and firewall rules. Not sure that is a doube NAT?
You said:
"I also considered Steve Gibson's suggestion ( https://www.grc.com/nat/nat.htm) to put another router between pfsense and the AP/network"If you have another consumer grade router, it will be doing NAT, in addition to pfsense doing it.
All I have not are VLANS and firewall rules.
What does that mean? If you have different classes of networks, such as guest Wifi and IoT, then VLANs are often the way to do it. It's certainly how you'd set up a guest Wifi, unless you want to buy APs you don't really need. On my network, both main and guest SSIDs are on the same AP, with a VLAN to carry the guest connection. IoT could be on a separate network, if you have a spare port on pfsense. Otherwise you can use a VLAN to a managed switch that's used for IoT. My guest rules would be a good place to start. You may want something similar for IoT, but I can't say without knowing more about your network and what the IoT connects to.
-
@jknott Thanks for the help. I'm just learning and trying to get a grasp on a good configuration. I appreciate guys on this forum taking time to address simple concepts as these are things I haven't spent time wrapping my head around. We are lucky these days with forums and YouTube to be able to learn without stepping into a class room.
-
This rule won't work, it needs to be on the printer_vlan net.
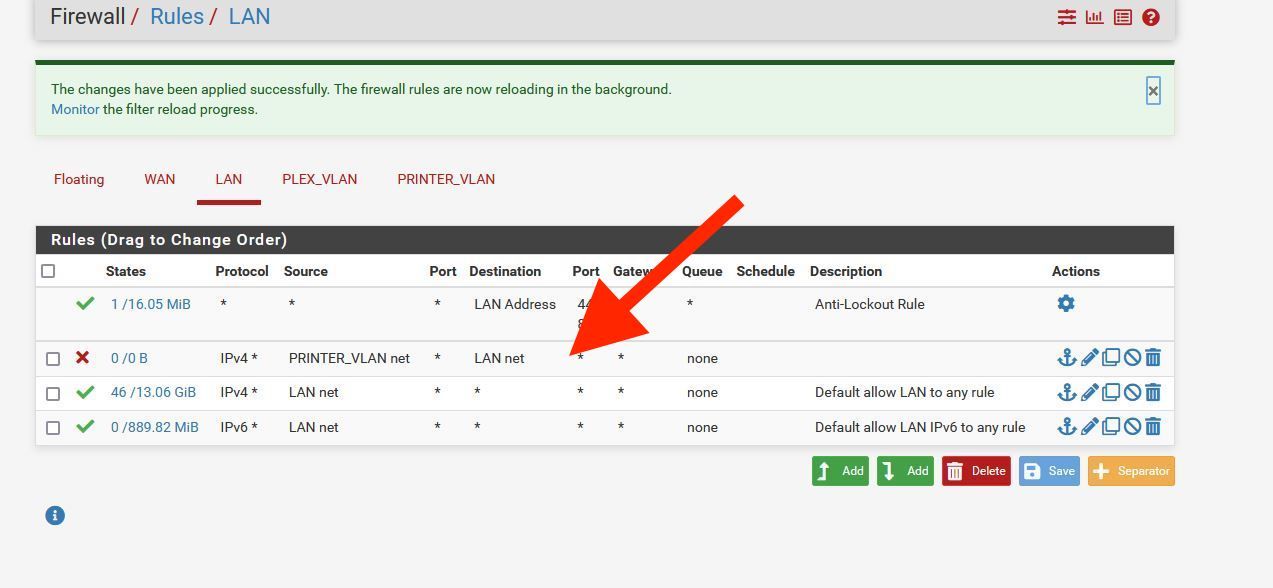
You want something like this that just allows traffic out from the netwotk to the Internet.
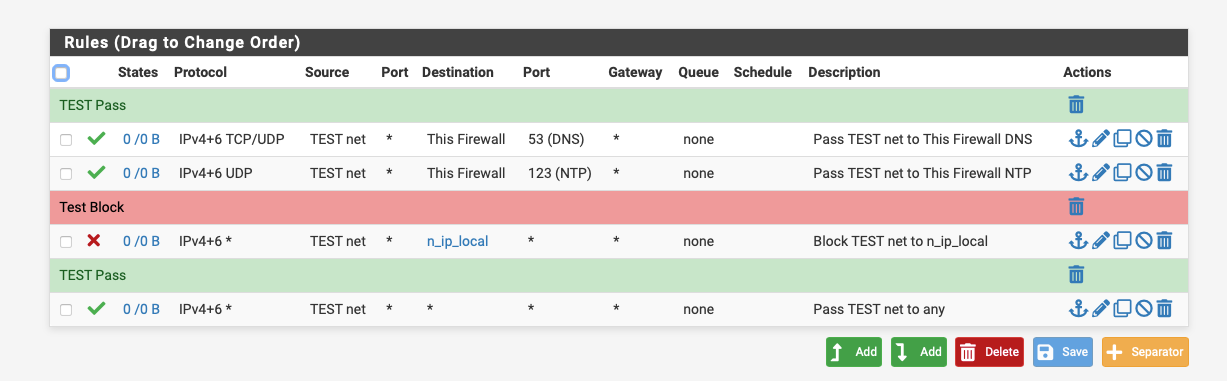
-
@jay226
My first suggestion with RFC 1918 alias does not allow access to the webGUI. My IoT rules look like this:
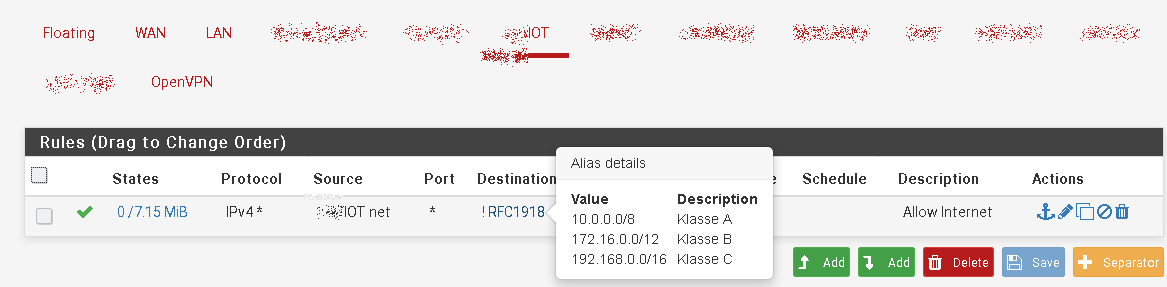
Additionally I have a floating rule in place allowing DNS access to pfSense (This firewall) for DNS resolution on all internal interfaces.
But if you still have an allow any rule on the IoT interface for whatever reason, block webGUI access for destination "this firewall". Otherwise the devices are permitted to access the pfSsense web interface by using its WAN IP for instance.
-
@nogbadthebad said in Simple IOT Network:
This rule won't work, it needs to be on the printer_vlan net.

You want something like this that just allows traffic out from the netwotk to the Internet.

@nogbadthebad your example makes perfect sense. Blocking all local addresses doesn't pass DNS and other services. Adding those pass rules at the top with a block rule at the bottom will block access to the Pfsense webconfigure page as well and other local networks VLANS etc.
-
@viragomann Ok.. found out the issue. Its something that I didn't know existed in Windows but I'm new to VLANs. Apparently, some security reason I guess, windows firewall will not accept IMCP packets from devices on different subnets. I finally after much headache found the below link.
The thing that threw me is that one of my linux machines was responding to pings on different subnets but others were not, so I thought there was a problem.
in the end, no problem, other than my ignorance.
Solved: VLANs and Windows Accepting Pings from Different Subents