Unidirectional Firewall Rule?
-
Hello
I am trying to find a way to create a firewall rule that only allows UDP traffic within a session to flow in one direction (i.e. disallowing any return packets within the session).
I would like to replicate a similar action to a stateless firewall where if I have an allow rule, there isn't a silent secondary rule to allow return traffic within the same session (state).I am specifically trying to create this for UDP syslog traffic. Since the protocol itself never has return packets within a session, I would like to lock down the firewall rules even more by never allowing bidirectional traffic.
Does anyone know how to create such a rule in pfsense?
I have tried adding advanced options to my rules with states set to none and reply to set to no. I have also tried adding floating rules allowing WAN to LAN UDP syslog, then a rule before it blocking any packets flowing the other direction, but that still failed.
-
In case you never figured this out, or someone else stumbles across this on google.
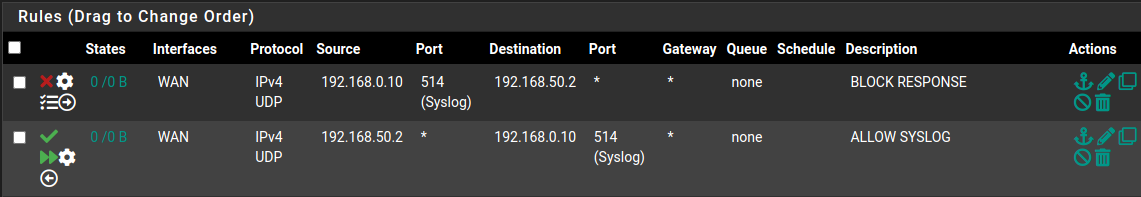
You will need 2 rules placed in the “Floating” Rules tab. The first will block return traffic, and the second will be the allow rule. Important note: Both firewall rules must be applied to the same interface. Specifically, they must be both applied to the interface where the traffic is originally coming from (source).
Example:
Lets say we have a Syslog server at the IP of 192.168.0.10 listening on port 514. And we also have a client that wants to send Syslog messages to the server, and their IP is the 192.168.50.2. So we must allow traffic to pass from the 192.168.50.2 to the 192.168.0.10 on port 514 without allowing return communication.
The options you will need set for each rule:
BLOCK RESPONSE:
Action: Block Interface: WAN #TrafficSourceInterface Direction: Out Protocol: UDP Source: 192.168.0.10 #syslog server Source Port: 514 Destination: 192.168.50.2 #syslog sender Destination Port: any Log: Log packets State type: NoneALLOW SYSLOG:
Action: Pass Quick: Apply the action immediately on match Interface: WAN #TrafficSourceInterface Direction: In Protocol: UDP Source: 192.168.50.2 #syslog sender Source Port: any Destination: 192.168.0.10 #syslog server Destination Port: 514 State type: noneShould look something like below. I have this all configured on an internal firewall, with syslog senders outside my "WAN" so that will differ with other peoples setups.
You can test this out using ncat in udp mode between two machines. Thats originally how I figured it out.